XenMobile
Netskope supports XenMobile on-demand VPN for iOS devices that allow users' devices to connect securely to corporate resources. Configuring XenMobile for iOS on-demand VPN consists of these primary tasks:
Add a PKI Entity.
Add a Credential Provider.
Add a Credential Policy.
Add a VPN Policy.
Install the Citrix Secure Hub iOS app on the mobile device and register the device. This task is not covered in this document. Refer to the Citrix product documentation for more information.
Prerequisites
Before you begin, open the Netskope UI, go to Settings > Security Cloud Platform > Netskope Client > MDM Distribution, and then scroll down to the Create VPN Configuration section.
Copy these code strings from this section:
Organization ID. You need this for the OU entry on the XenMobile Certificate Signing Request page.
VPN Server Name. You need this for the Server Name entry on the XenMobile VPN Policy Information page.
PAC URL: You need this for the Proxy Server URL on the XenMobile VPN Policy Proxy page.
You also need a CA certificate to import on the XenMobile Credential Providers Distribution page.
For information about iOS VPN fail-open, refer to iOS VPN Fail Open.
To configure XenMobile for iOS on-demand VPN:
Log in to your XenMobile account (https://xms.bowlins.com:4443). Under Certificate Management, go to Settings > PKI Entities, click Add, and then select Microsoft Certificate Services Entity. This will be used during the new Credential Provider setup later in this procedure.
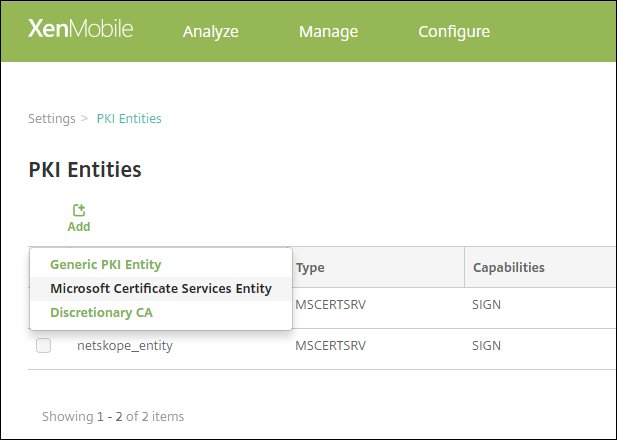
For General Information, enter these parameters:
Name: Enter a unique name for this entity.
Web enrollment service root URL: Enter the Root URL for your account. For example,
https://RootCA-URL/certsrv.certnew.cer Page Name: Leave the default setting.
certfnsh.asp: Leave the default setting.
Authentication type:
Client Certificate.SSL client certificate: Import the user certificate that will be used to issue the XenMobile client certificate.
When finished, click Next.
For Templates, click Add, enter the name of the template created when configuring the Microsoft certificate, and then click Save. When finished click Next.
Skip the HTTP Parameters and click Next.
For CA Certificates, select the root CA that corresponds to your environment, which is part of the chain imported from the XenMobile client certificate. If no certificate is present, click Import certificate to add the CA certificate, and then select it. When finished, click Save.
After creating a PKI entity, you need to add a credential provider. Under Certificate Management, go to Settings > Certificate Management > Credentials Providers and click Add to create a new credential provider.

On the General page, enter these parameters:
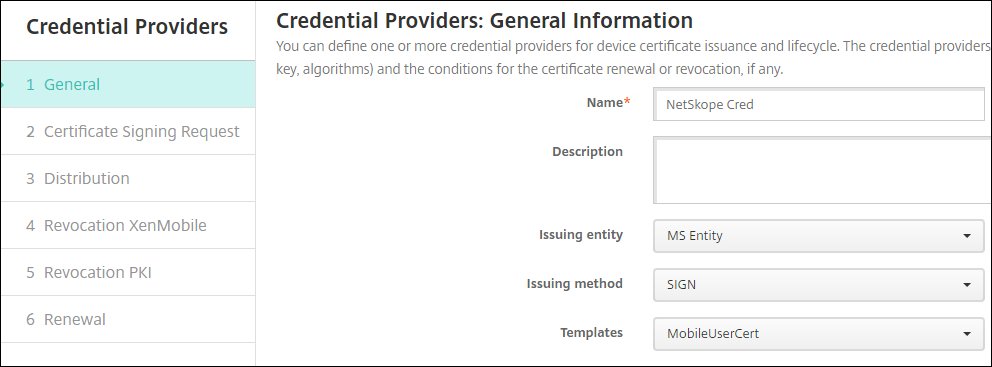
Name: Enter a unique credential provider name.
Issuing entity: Select the Microsoft Certificate Services Entity you created in step 2.
Issuing method:
Sign.Templates: Select the template you created in step 3.
When finished, click Next.
On the Certificate Signing Request page, enter these parameters:
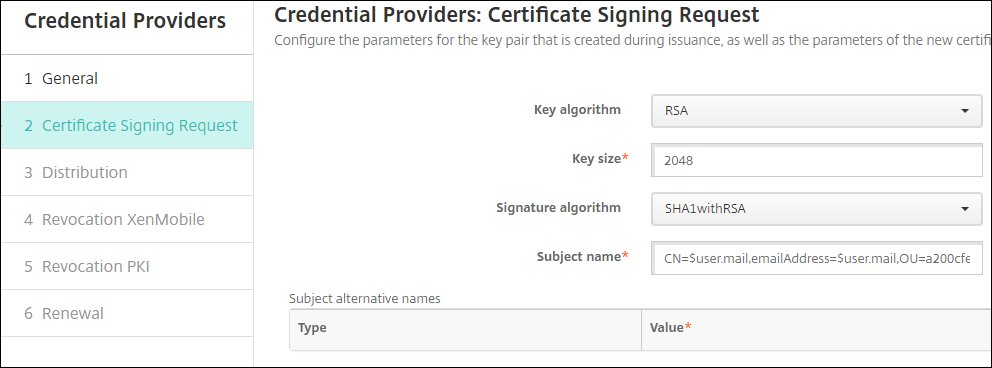
Key algorithm:
RSAKey size:
2048Signature algorithm:
SHA1withRSASubject name: Enter
CN=$user.mail,emailAddress=$user.mail,OU=<Organization ID from the Netskope UI>,O=Citrix Systems.
When finished, click Next.
On the Distribution page, enter these parameters:
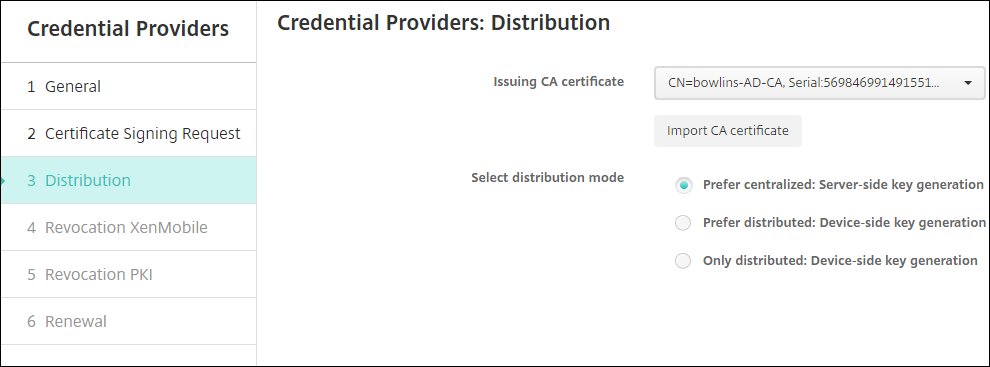
Issuing CA certificate: Select your certificate from the dropdown list. To import your certificate, click Import CA certificate.
Select distribution mode: Select
Prefer centralized: Server-side key generation.
When finished, click Next.
On the Revocation XenMobile page, enter these parameters:
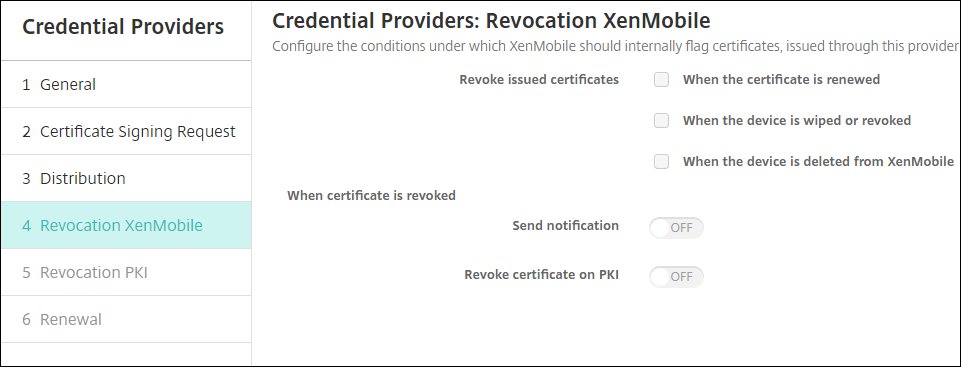
Revoke issued certificates: None of these options should be enabled.
Send notification:
Off.Revoke certification on PKI:
Off.
When finished, click Next.
On the Revocation PKI page, make sure Enable external revocation checks is
Off.
When finished, click Next.
On the Renewal page, enter these parameters:
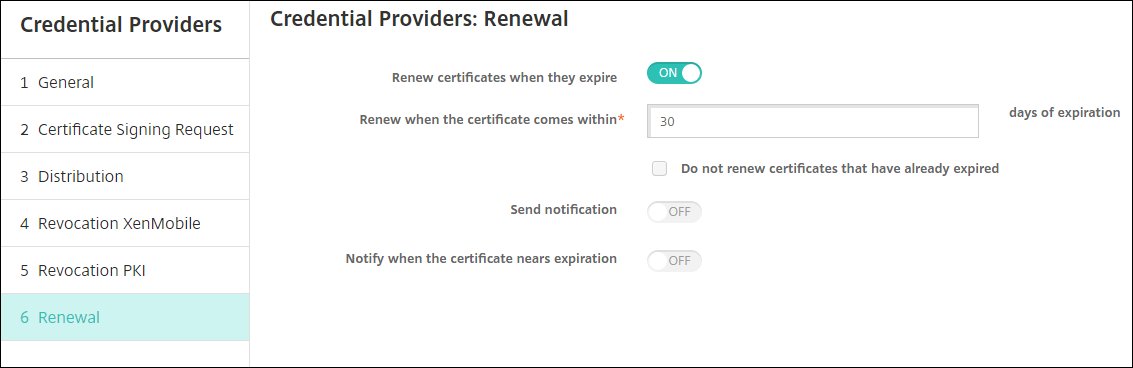
Renew certificates when they expire:
On.Renew when the certificate comes within:
30(days of expiration).Send notification:
Off.Notify when the certificate nears expiration:
Off.
When finished, click Save.
Now configure your credentials for Device Policies. Go to Configure > Device Policies and click More to expand the options. Under Security, click Credentials.
Make sure iOS is the only platform selected, and then enter a unique Policy Name.
When finished, click Next.
Enter these parameters:
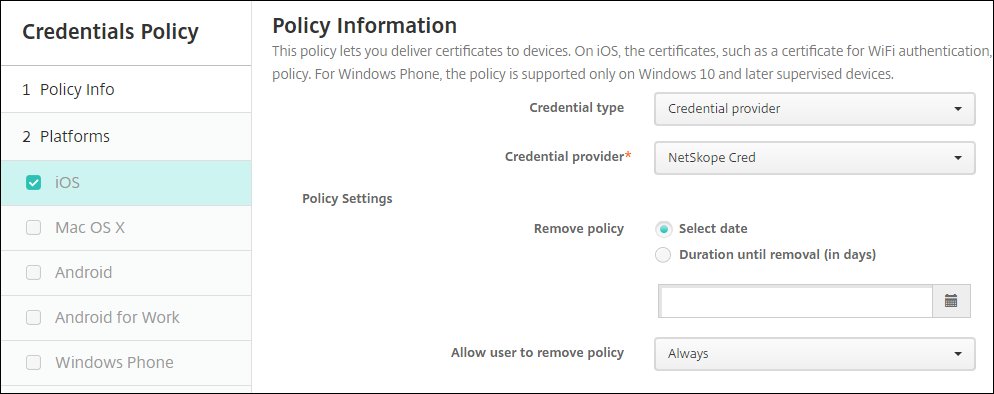
Credential type:
Credential Provider.Credential provider: Select the Netskope credential provider (you created in step 3 above).
Remove policy:
Select date.Allow user to remove policy:
Always.
When finished, click Assignment in the left panel.
For Choose delivery groups, select
AllUsers.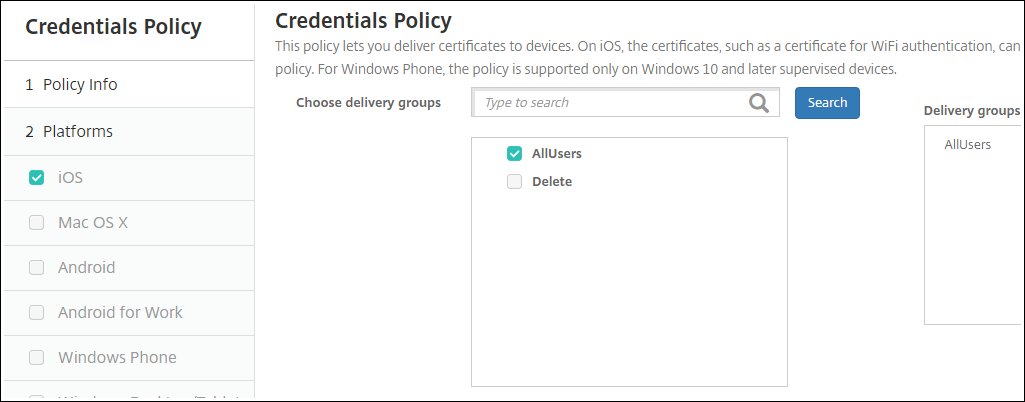
When finished, click Save.
Now create a VPN policy. Go to Configure > Device Policies, click Add, and then click VPN.
Make sure iOS is the only platform selected, and then enter a unique VPN policy name.
When finished, click Next.
Make sure iOS is the only platform selected, and then enter these parameters:
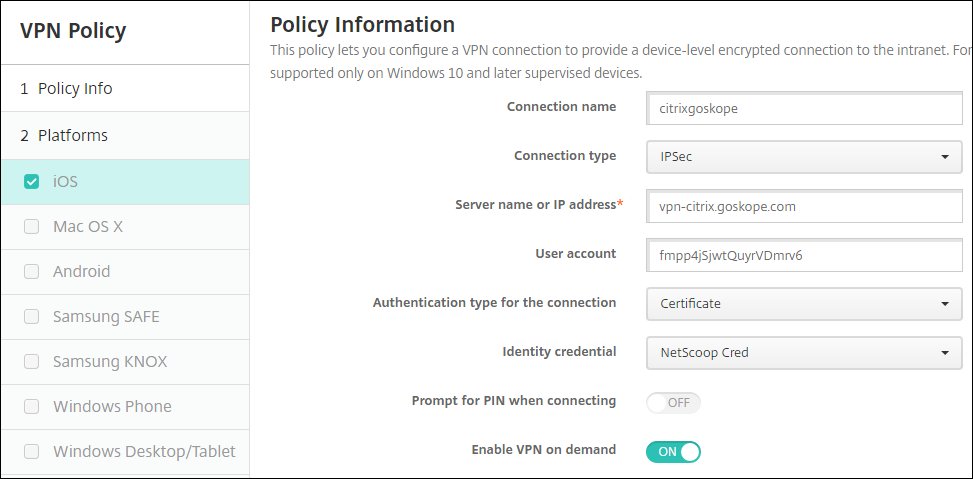
Connection name: Enter a unique connection name.
Connection type:
IPSecServer name or IP address: Enter the VPN Server Name from the Create VPN Configuration section in the Netskope UI (Settings > Security Cloud Platform > Netskope Client > MDM Distribution).
User account: Enter an optional user account name.
Authentication type for the connection:
Certificate.Identity credential: Select the Credentials Policy (you created in step 11 above).
Prompt for PIN when connecting:
Off.Enable VPN on demand:
On.Next, enter the On-Demand Rules parameters:
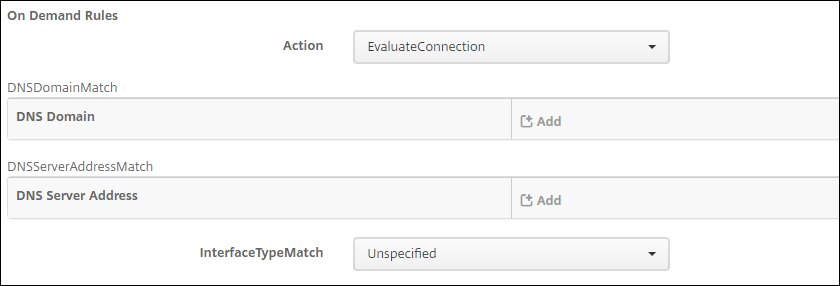
On-Demand Rules:
EvaluateConnection.InterfaceTypeMatch:
Unspecified.
Next, enter the Action Parameters:
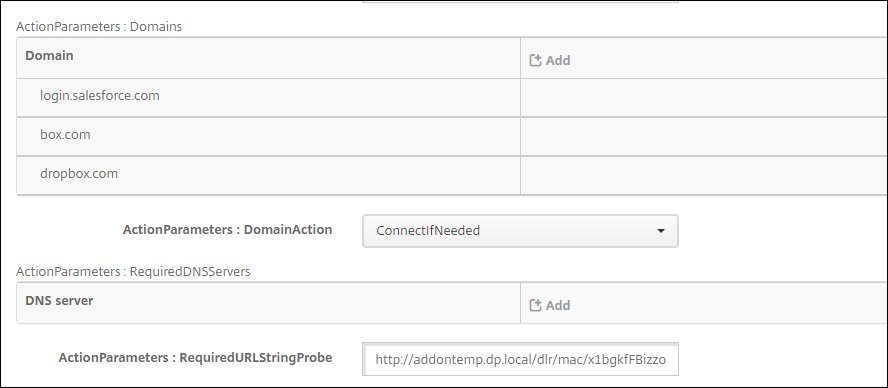
ActionParameters:Domains: Add on-demand domains (like
app.box.com).Tip
If you want to add multiple on-demand domains at once instead of adding them one by one, create an XML file with on-demand domains as shown below, and then paste the code in the OnDemandRules:XML content field.
<array> <dict> <key>Action</key> <string>EvaluateConnection</string> <key>ActionParameters</key> <array> <dict> <key>Domains</key> <array> <string>.salesforce.com</string> <string>login.salesforce.com</string> <string>app.box.com</string> </array> <key>RequiredURLStringProbe</key> <string>http://addontemp.dp.local/dlr/mac/x1bgjyzwNbwo2u</string> <key>DomainAction</key> <string>ConnectIfNeeded</string> </dict> </array> </dict> </array>ActionParameters:DomainAction:
ConnectIfNeeded.RequiredURLStringProbe: Enter an HTTP or HTTPS URL to probe.
Next, add the Proxy parameters:
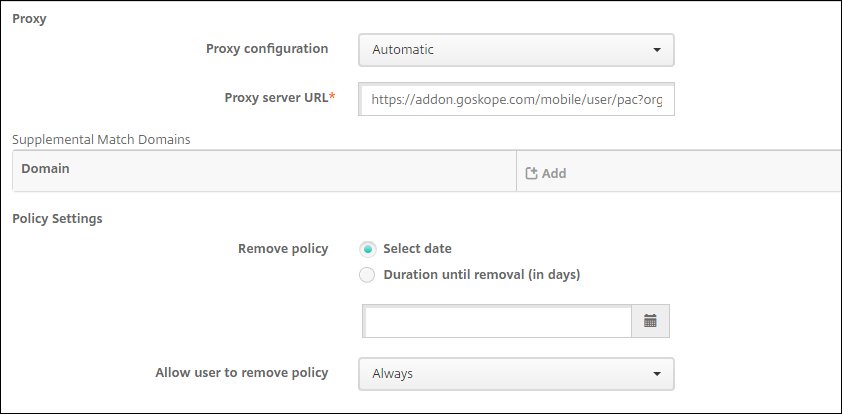
Proxy configuration:
Automatic.Proxy server URL: Enter the PAC URL from the Create VPN Configuration section in the Netskope UI (Settings > Security Cloud Platform > Netskope Client > MDM Distribution).
Remove policy:
Select date.Allow user to remove policy:
Always.
Click Assignment in the left panel, and enter these parameters:
Choose delivery groups:
AllUsers.Expand the Deployment Schedule section to see these options.
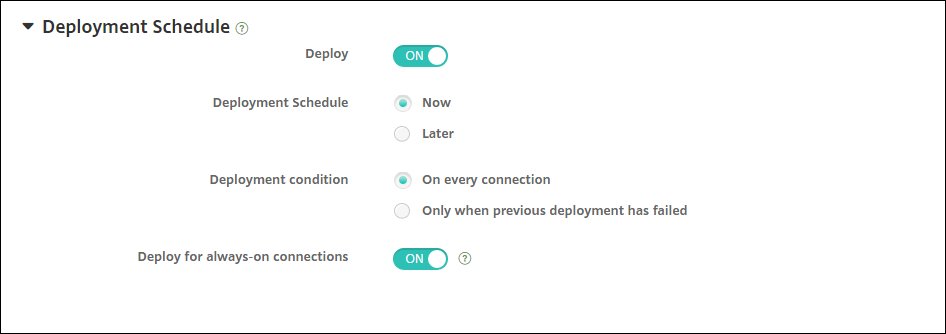
Deploy:
OnDeployment schedule:
Now.Deployment condition:
On every connection.Deploy for always-on connections:
On.
When finished, click Save.
The configuration for XenMobile on-demand VPN is complete. Install the Citrix Secure Hub iOS App on your device, and then after that you can perform the server login, user login, and so on to register the device. Refer to the Citrix product documentation for more information.
By default all Netskope tenants are set to On-Demand iOS VPN. If you want to use the Per-App iOS VPN profile, contact your sales rep, professional services rep, customer success manager, or Support to have Per-App VPN enabled.
To configure XenMobile for iOS per-app VPN:
Log in to your XenMobile account (https://xms.bowlins.com:4443). Go to Configure > Apps, click Add, and then select Public Store App.
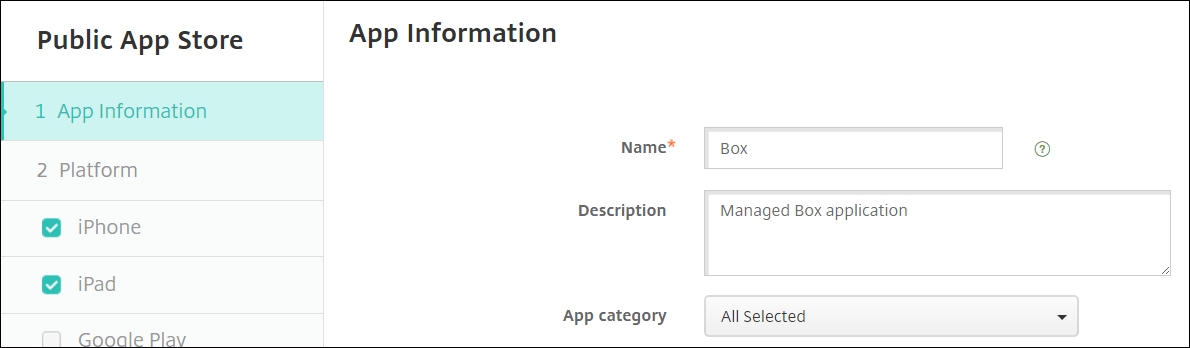
Enter the name of the app and a description.
Important
iPhone and iPad should be the only platforms selected.
When finished, click Next.
Search for the app you entered in step 1.
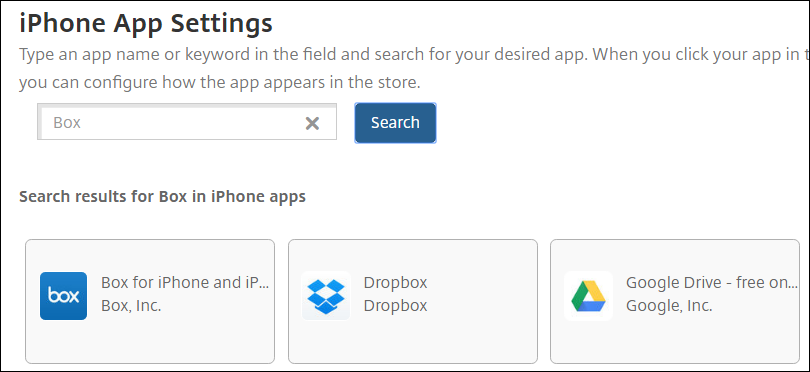
Select the app, enter these parameters:
Name: Leave as is or enter a new name.
Description: Leave as is or enter a new description.
Pad app:
OFF.Remove app if MDM profile is removed:
ON.Prevent app data backup:
ON.Force app to be managed:
ON.Force license association to device:
ON.
When finished, click Next.
Repeat steps 3 and 4 for iPad.
Select Delivery Groups Assignment in the left panel, select AllUsers, and click Save
Now configure an App Inventory policy. Go to Configure > Device Policies and click Add. Click More to expand the options, and under Apps select App Inventory.
Enter a policy name, and then click Next.
Make sure iOS is the only platform selected, and the iOS Policy is ON. When finished, click Next.
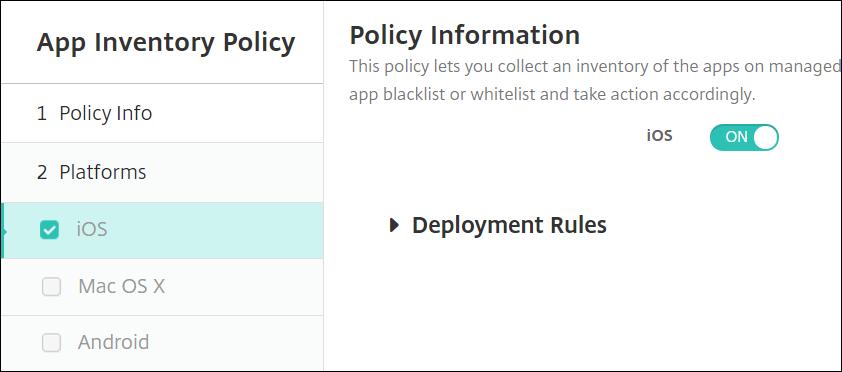
On the Assignment page, choose the Delivery Groups, like AllUsers, and then click Save.
Now configure your credentials for Device Policies. Go to Configure > Device Policies and click More to expand the options. Under Security, click Credentials.
Enter a unique Policy Name and click Next.
Make sure iOS is the only platform selected, and then enter these parameters:

Credential type:
Credential Provider.Credential provider: Select the Netskope credential provider (If you do not see a Netskope Credential Provider in the dropdown list, refer to steps 1-9 in Configure XenMobile for iOS On-Demand VPN to create a Netskope Credential Provider).
Remove policy:
Select date.Allow user to remove policy:
Always.
When finished, click Assignment in the left panel.
For Choose delivery groups, select AllUsers.

When finished, click Save.
Now create a VPN policy. Go to Configure > Device Policies, click Add, and then click VPN.
Make sure iOS is the only platform selected, and then enter a unique VPN policy name.

When finished, click Next.
Make sure iOS is the only platform selected, and then enter these parameters:
Connection name: Enter a unique connection name.
Connection type: Select a type that you want to apply for this connection.
Server name or IP address: Enter the VPN Server Name from the Netskope UI (Settings > Security Cloud Platform > Netskope Client > MDM Distribution > Create VPN Configuration.
User account: Enter an optional user account name.
Authentication type for the connection:
CertificateIdentity credential: Select the Credentials Policy (you created in step 12 above).
Prompt for PIN when connecting:
OFFEnable VPN on demand:
OFFEnable per-app VPN:
ONOn-demand match app enabled:
ONActionParameters:DomainAction:
ConnectIfNeeded.RequiredURLStringProbe: Enter an HTTP or HTTPS URL to probe.
Next, add the Proxy parameters:

Proxy configuration:
Automatic.Proxy server URL: Enter the PAC URL from the Netskope UI Settings > Security Cloud Platform > Netskope Client > MDM Distribution > Create VPN Configuration.
Remove policy:
Select date.Allow user to remove policy:
Always.
Click Assignment in the left panel, and enter these parameters:
Choose delivery groups:
AllUsersExpand the Deployment Schedule section to see these options.

Deploy:
OnDeployment schedule:
NowDeployment condition:
On every connectionDeploy for always-on connections:
On
When finished, click Save.
Now create an App Attribute policy. Go to Configure > Device Policies and click Add. Click More to expand the options, and under Apps select App Attributes.
Enter a unique App Attributes policy name and click Next.
Enter these parameters:
Managed app bundle ID: Select the app ID for the app you selected in step 2. If it's not in the dropdown list, click Add New and enter it.
Per-App VPN Identifier: Select the VPN policy name you created in step 16.
When finished, click Next.
Select the delivery groups and click Save.
The configuration for the XenMobile per-app VPN is complete. Install the Citrix Secure Hub iOS App on your device, and then after that you can perform the server login, user login, and so on to register the device. Refer to the Citrix product documentation for more information.
Fail open function allows traffic from a device using iOS VPN to bypass Netskope and directly go to an app or service. When fail open is enabled, all iOS devices will no longer steer traffic to Netskope. Fail open occurs when Netskope initiates it due to a service interruption and when an admin enables it in the Netskope UI.
To enable fail open for iOS VPN:
In the Netskope UI, go to Settings > Security Cloud Platform > MDM Distribution.
In the Create VPN Configuration section, confirm that your iOS VPN is operational. If so, click the
 icon to open the Advanced Configuration dialog box.
icon to open the Advanced Configuration dialog box.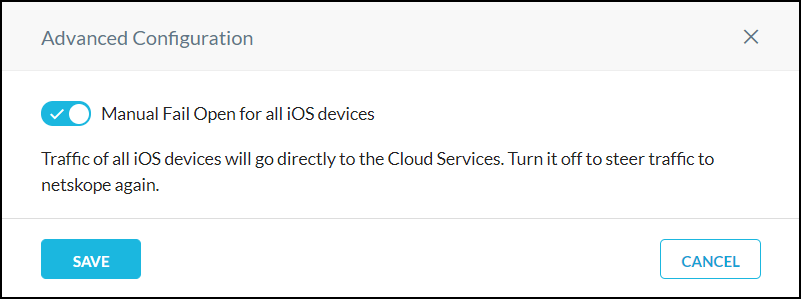
Enable the toggle and then click Save.