Microsoft Azure Sentinel Plugin for Log Shipper
This document explains how to configure your Azure Sentinel integration with the Log Shipper module of the Netskope Cloud Exchange platform. This integration allows ingestion of Netskope events and alerts into an Azure Sentinel tenant. The Azure Sentinel plugin support is:
Event Support | Yes |
Alert Support | Yes |
WebTx Support | Yes |
A Netskope Tenant (or multiple, for example, production and development/test instances).
A Netskope Cloud Exchange tenant with the Log Shipper module already configured.
An Azure Sentinel instance.
Note
Verify your Azure Sentinel instance permissions are secure and not set up for open public access. Only allow access to your cloud storage instance from your Cloud Exchange Host and any other addresses that need access.
Get your Azure Sentinel Workspace ID and Primary Key.
Configure the Azure Sentinel plugin.
Configure Log Shipper Business Rules.
Create Log Shipper SIEM mappings.
Validate the plugin.
Click play to watch a video.
Go to your Azure Sentinel instance https://portal.azure.com/.
Log in to your Sentinel instance.
Under the Azure Services section click More Services.
Find and click Azure Sentinel.
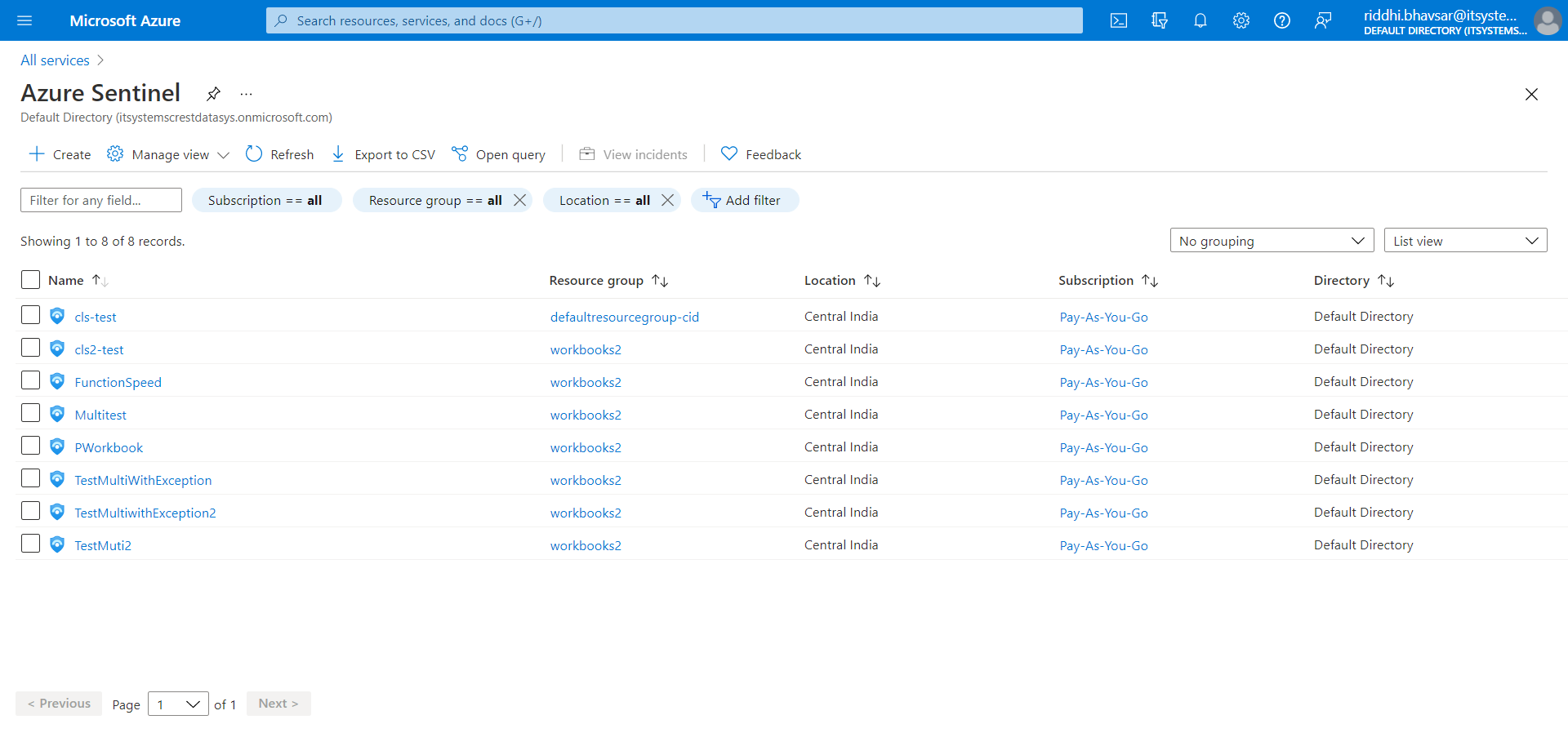
Click Create.
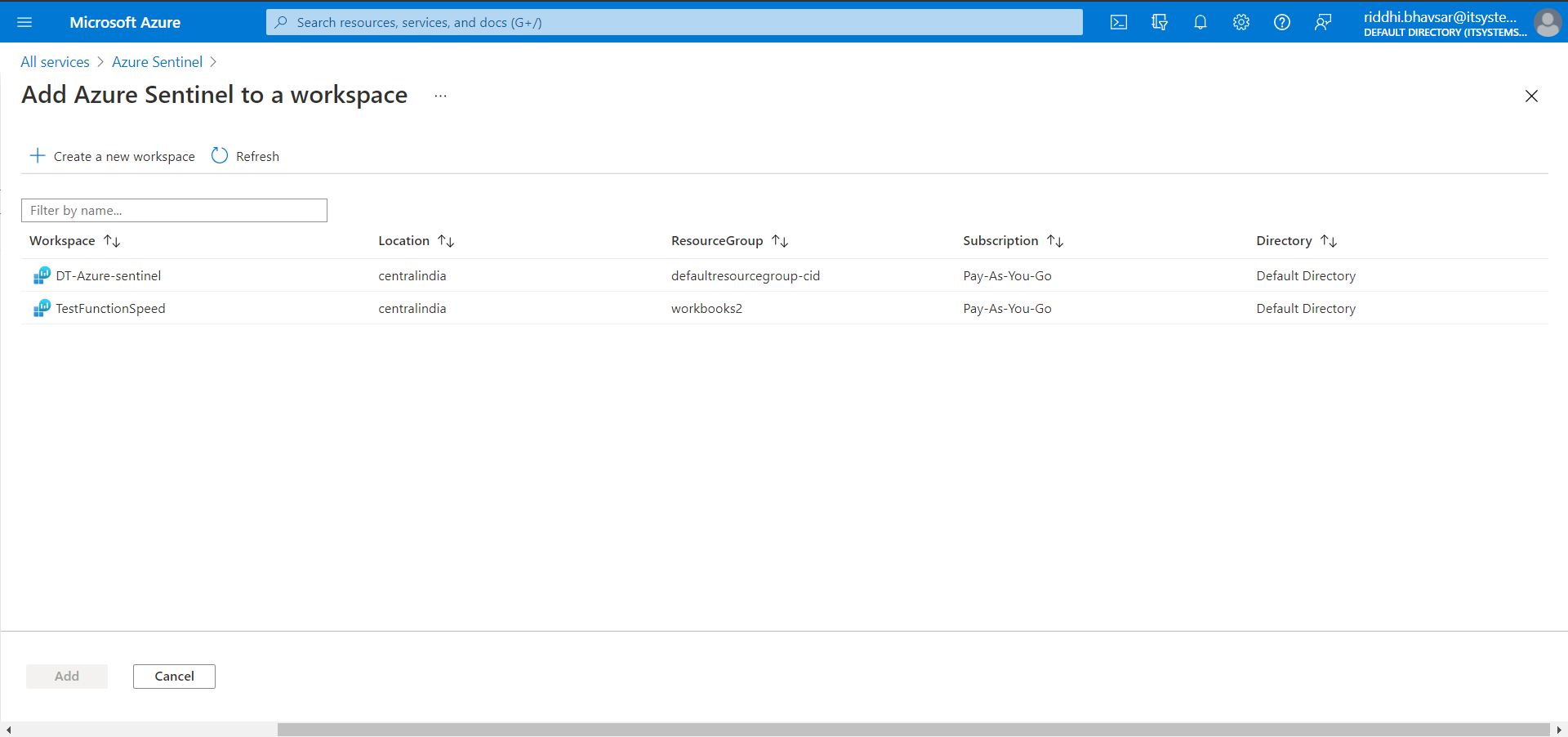
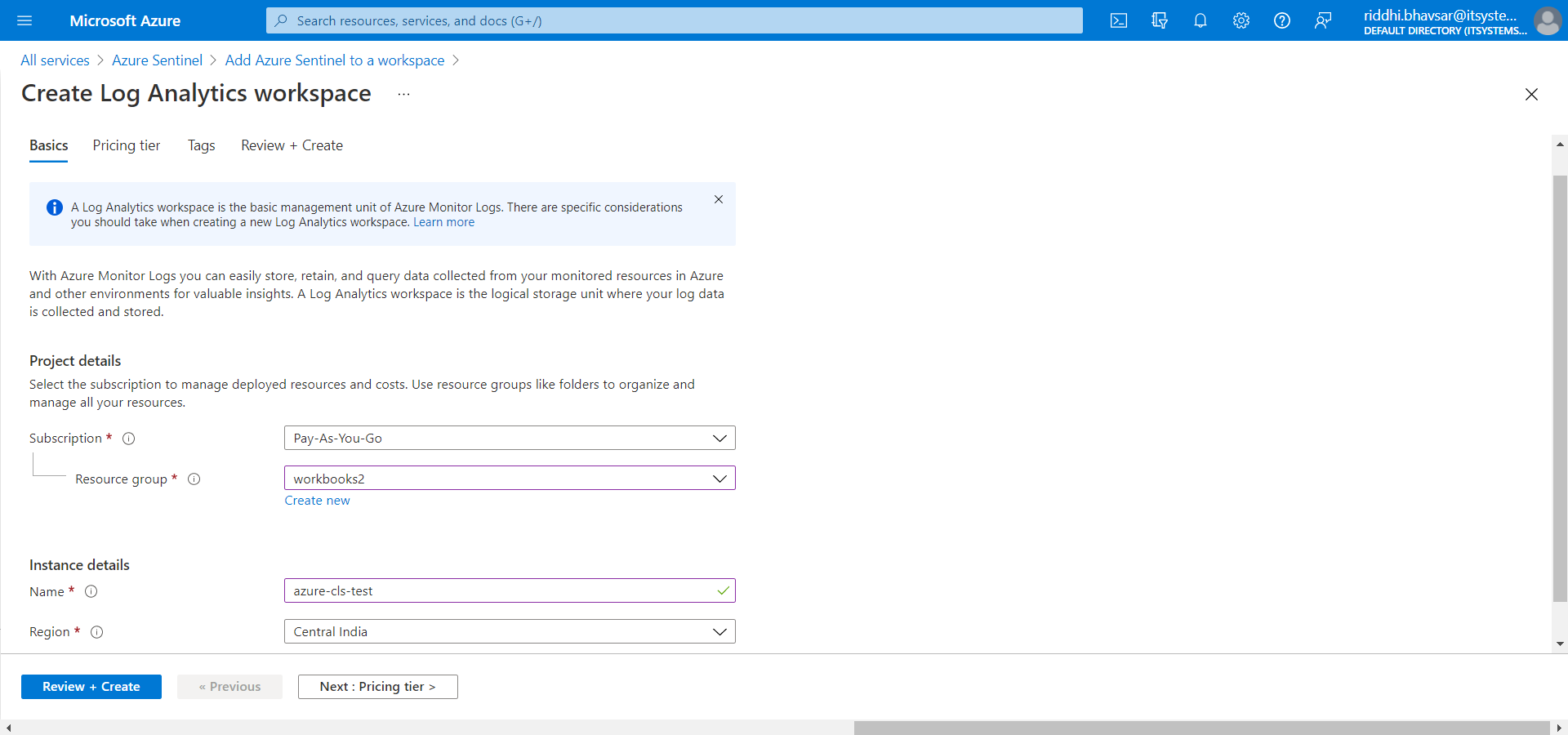
Click Create a new workspace. Select Resource Group, enter a name, and select your Region. Click Review + Create.
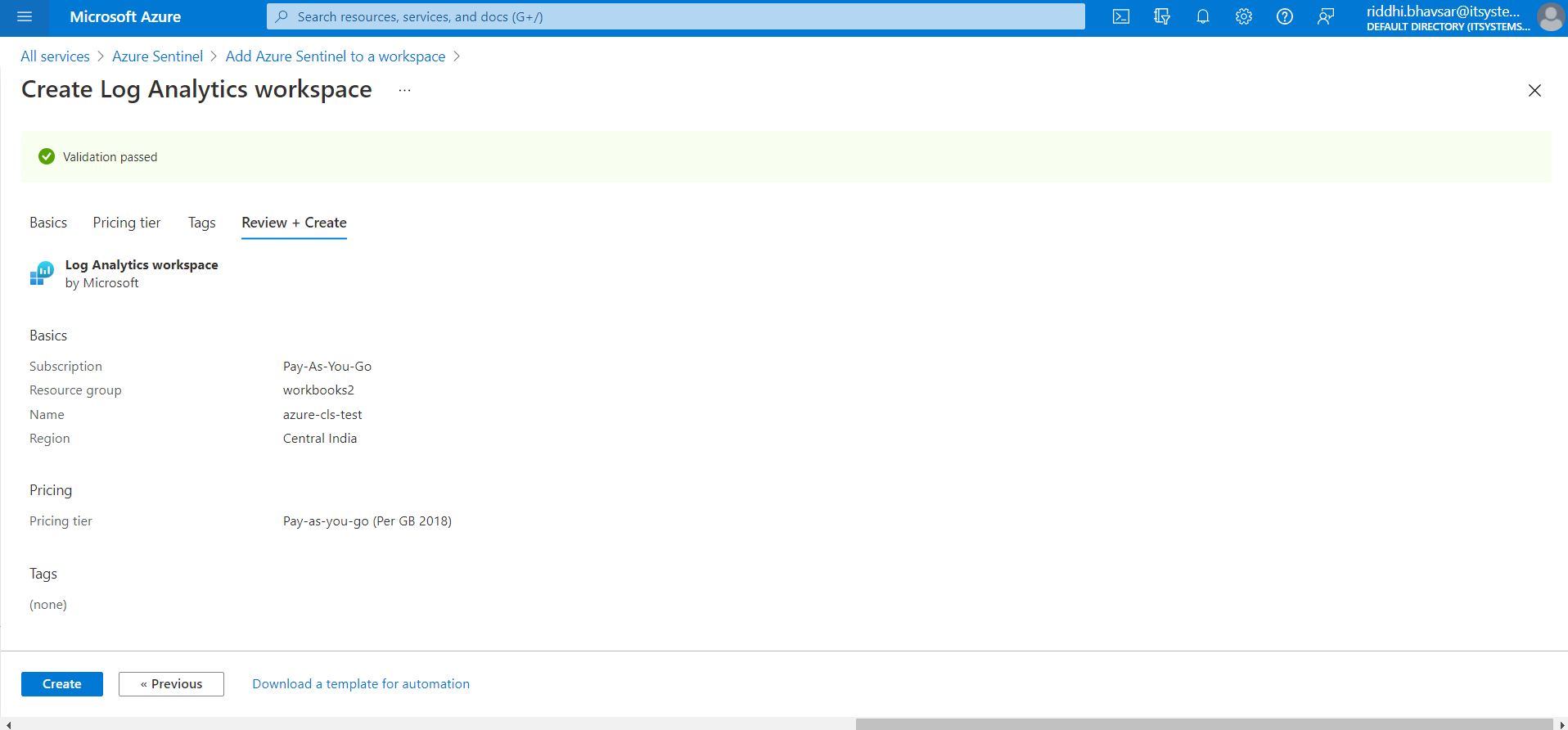
Click Create.
It will take a few seconds to deploy. After deployment succeeds, click Refresh. Click on the Workspace that you created and click Add.
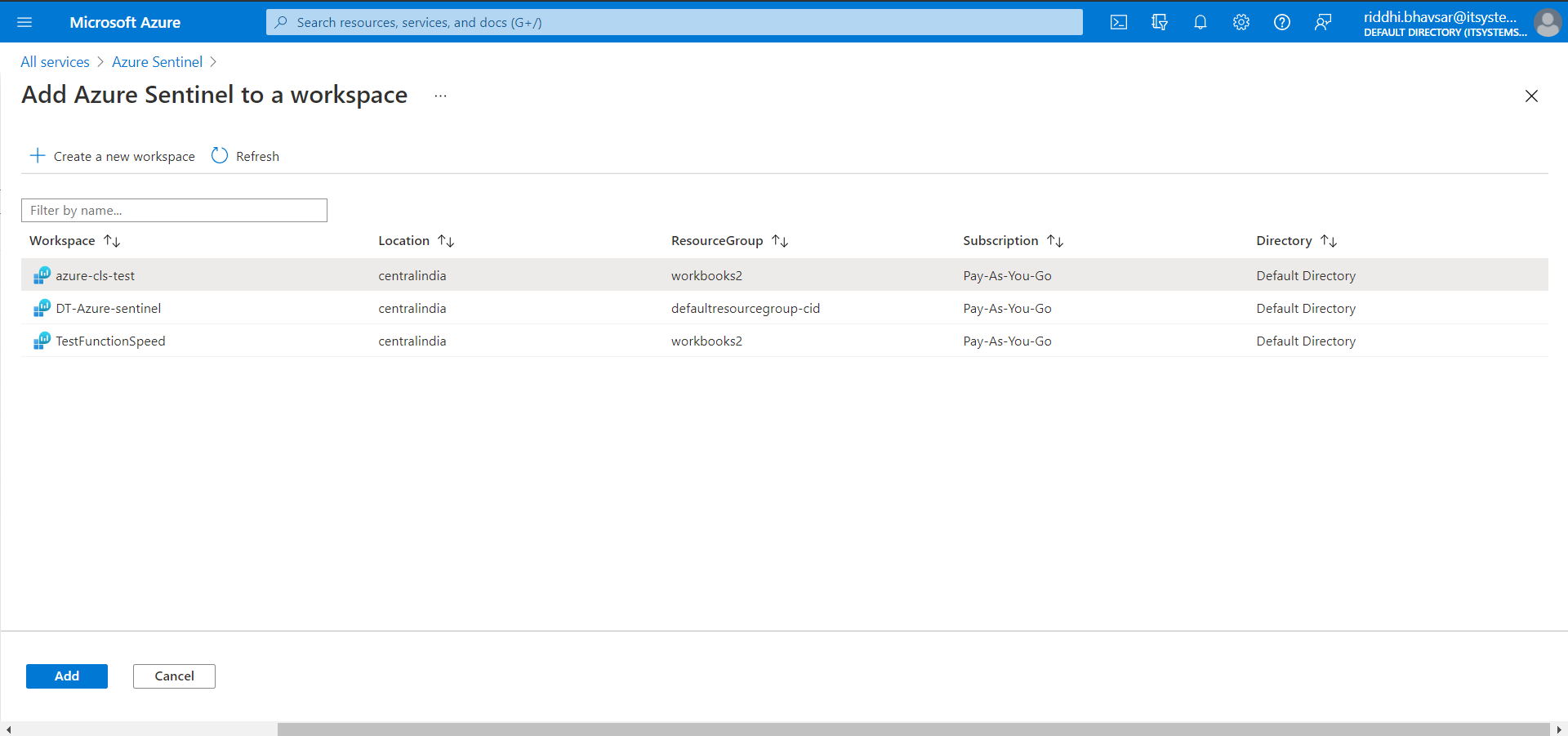
It will take a few seconds to add a workspace.
After successfully adding a workspace, go to Home All Services Log Analytics workspaces.
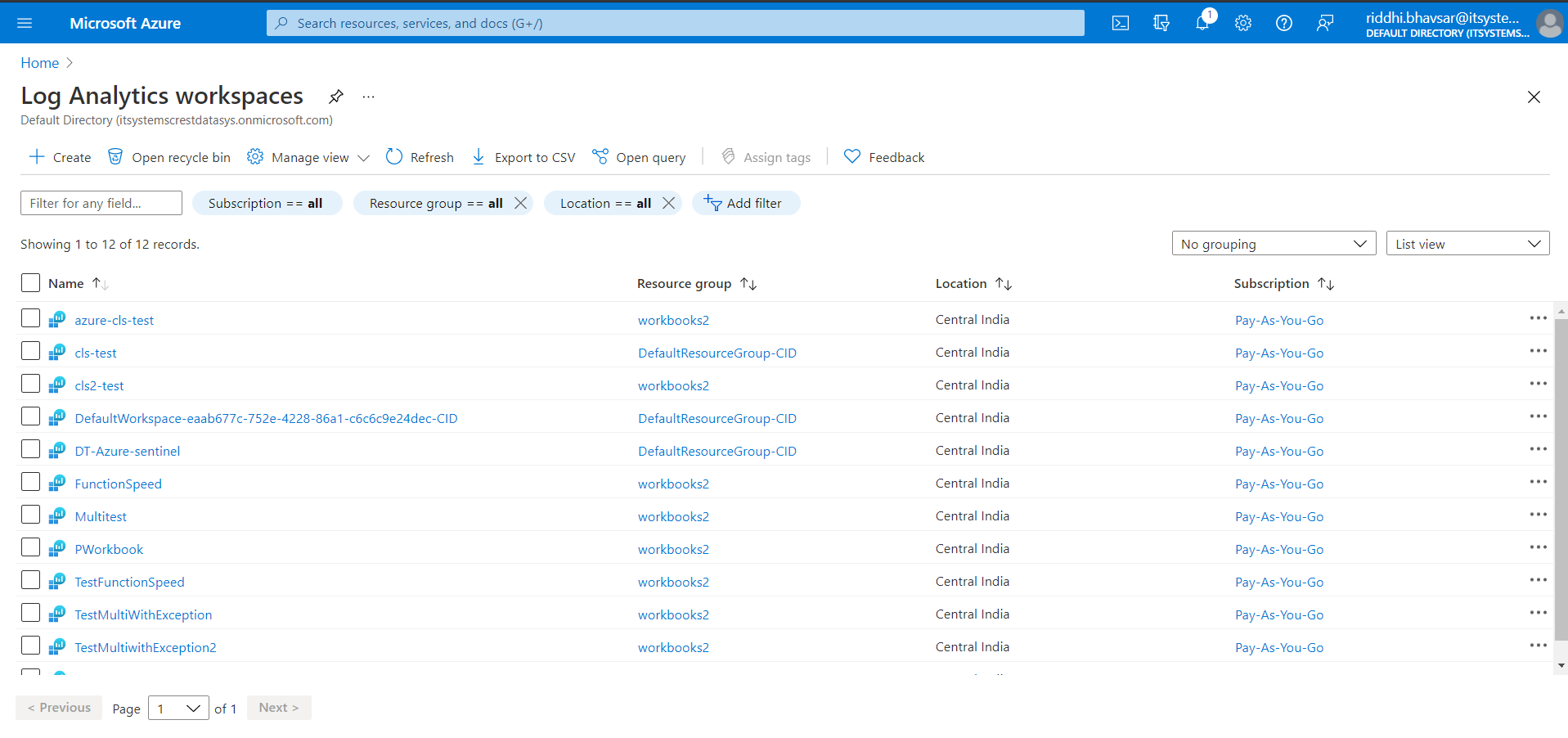
Click on the workspace name that you created.
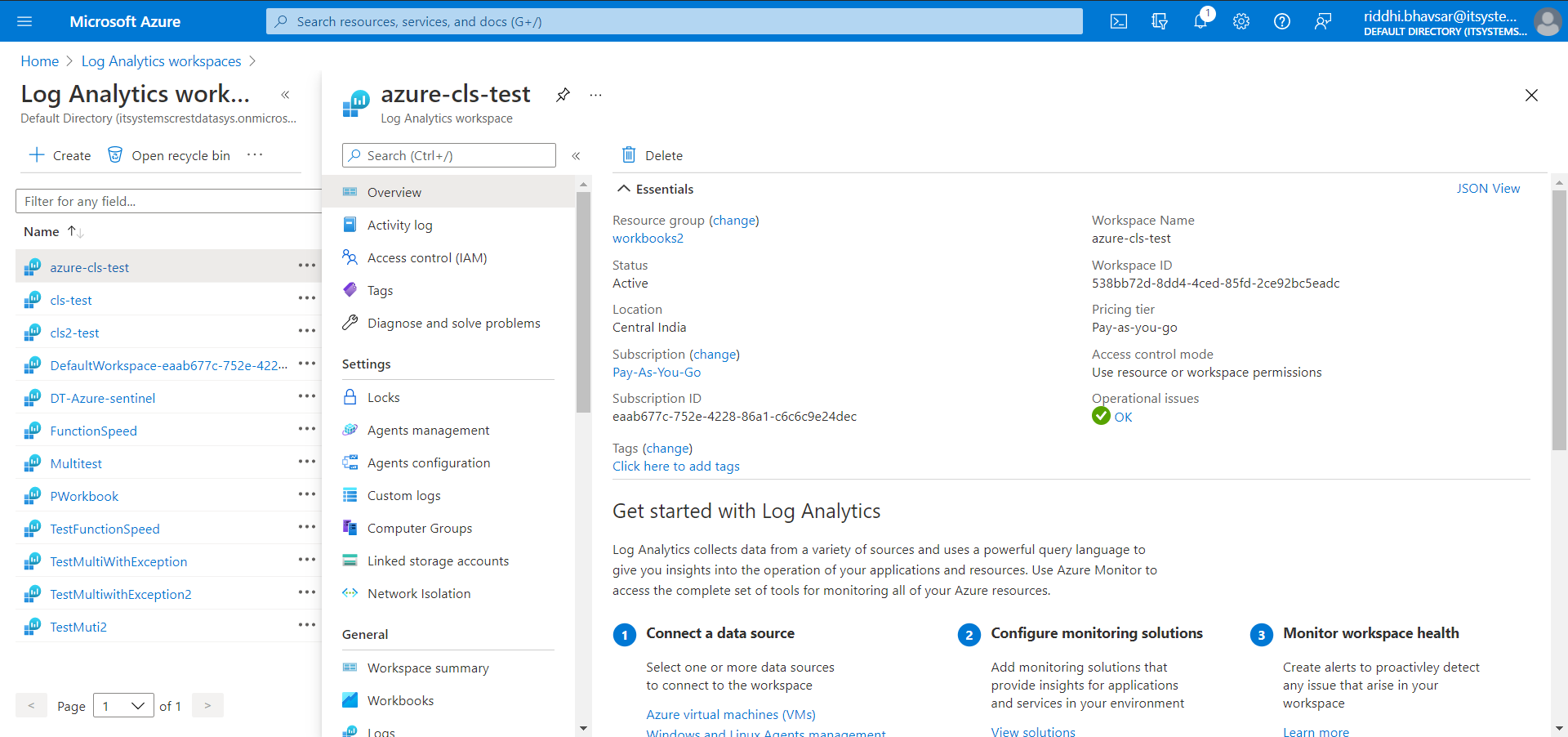
Click Agent Management.
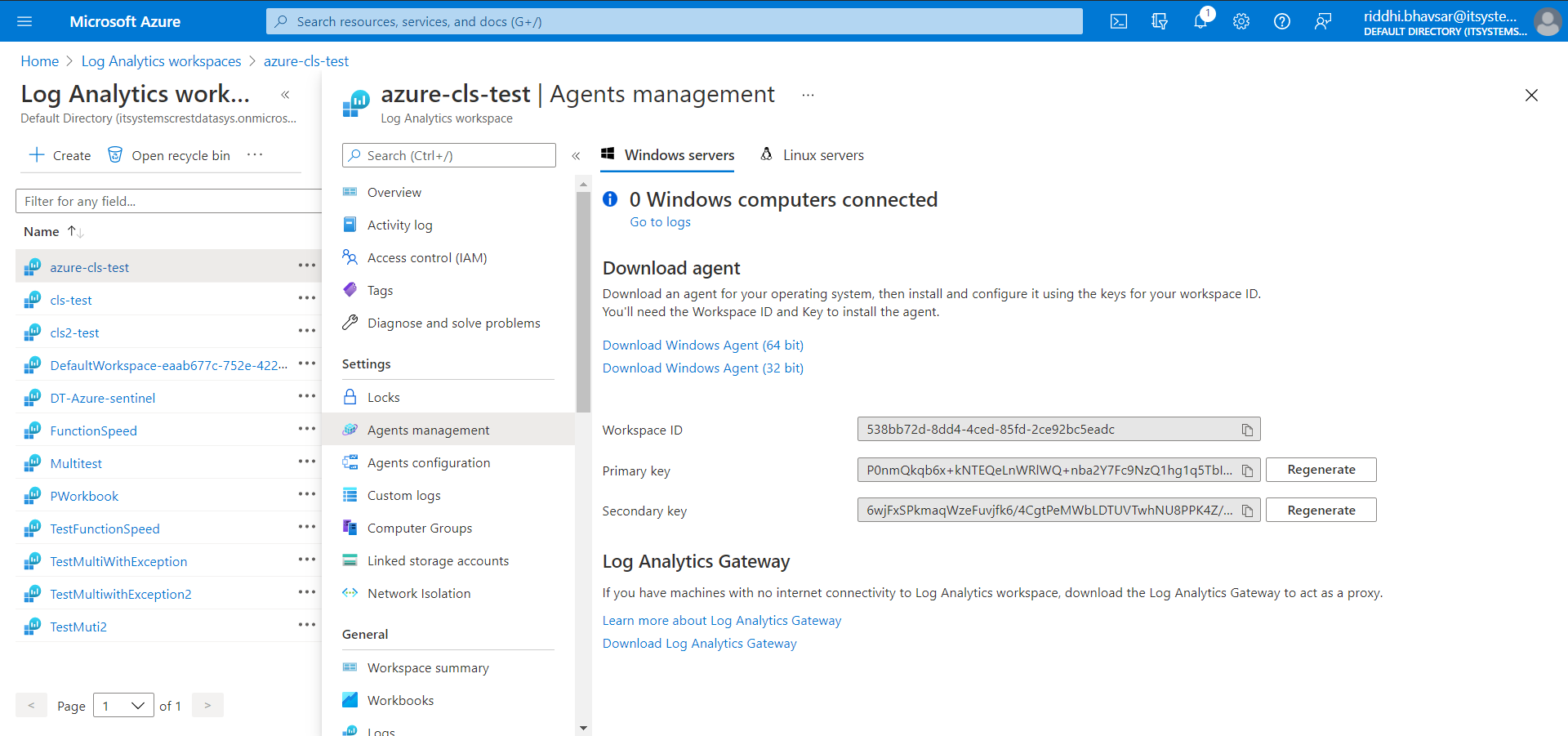
Copy and save the Workspace ID and Primary Key.
In Cloud Exchange, go to Settings > Plugins.
Search for and select the Azure Sentinel v2.0.2 (CLS) box to open the plugin creation pages.
Enter these parameters:
Configuration Name: Create a unique name for the configuration.
Mapping: Select the valid Mapping. (Default Mapping for all plugins are available. If you want to Create New Mapping, follow the CLS guide to Create New Mapping.)
Use System Proxy: Enable if the proxy is required for communication.
Transform the raw logs: Disable if need to send Raw Data. (Default: It will be enabled and send Transformed data)
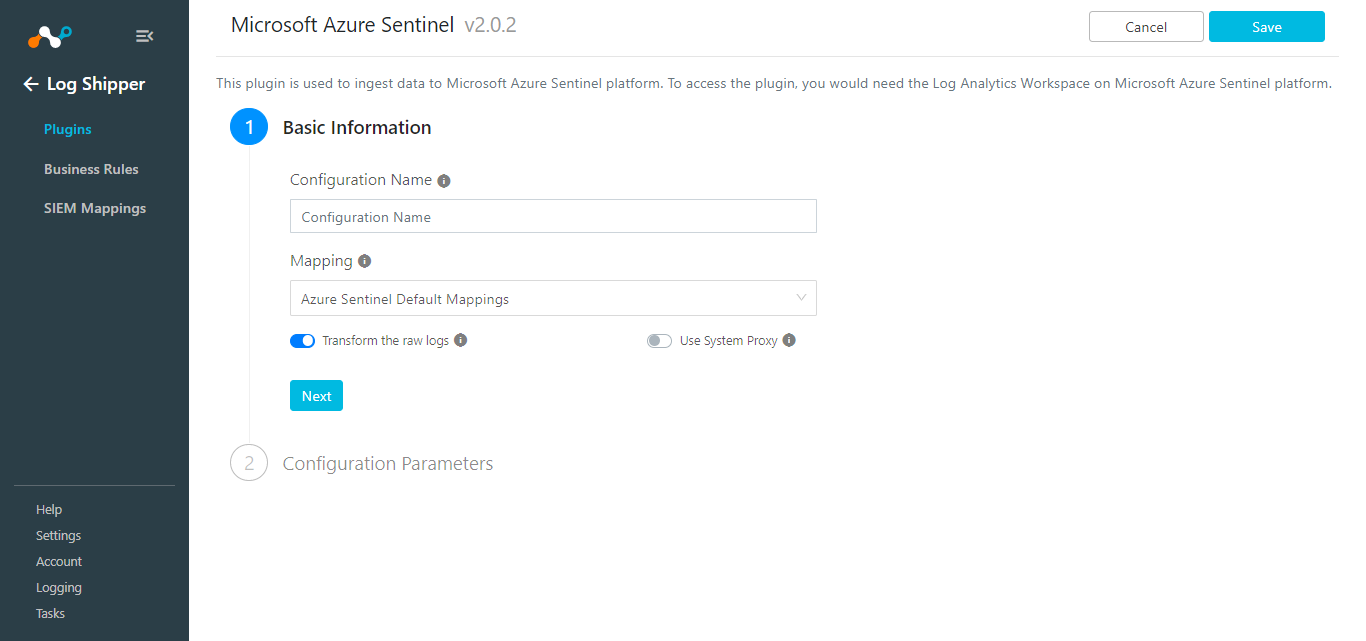
Click Next.
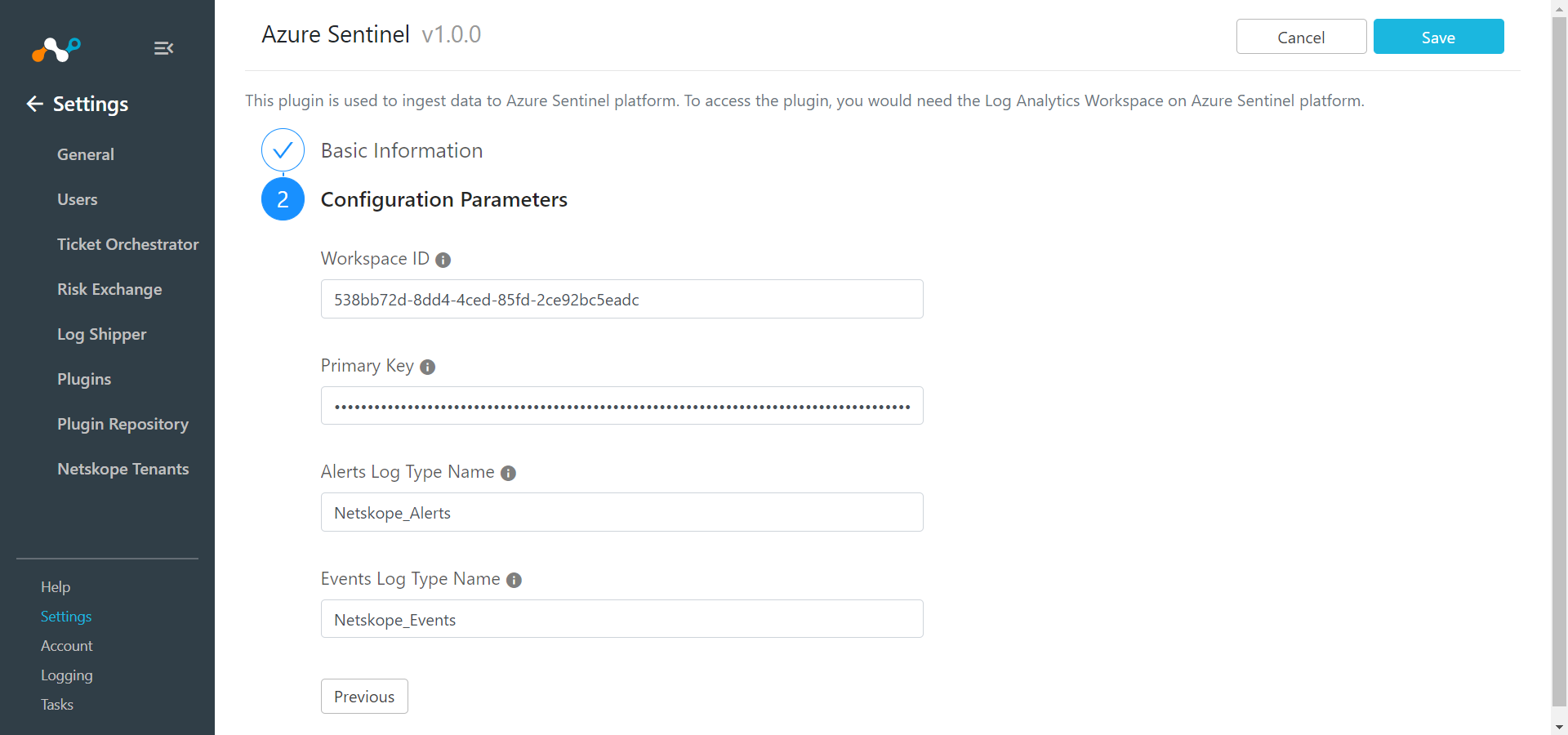
Enter these parameters:
Workspace ID: The unique identifier of your Microsoft Azure Sentinel Workspace.
Primary Key: The authentication key for your Microsoft Azure Sentinel Workspace.
Alerts Log Type Name: Custom Log Type name for alerts. Based on this name, schema for alerts will be created in Log Analytics Workspace with suffix
_CL. Note that the valueNetskope_AlertsorNetskope_Alerts_CLfor this parameter matches the Netskope published playbooks in the Azure marketplace.Events Log Type Name: Custom Log Type name for events. Based on this name, schema for events will be created in Log Analytics Workspace with suffix
_CL. Note that the valueNetskope_EventsorNetskope_Events_CLfor this parameter matches the Netskope published playbooks in the Azure marketplace.WebTX Log Type Name: Custom Log Type name for web transactions. Based on this name, schema for web transactions will be created in Log Analytics Workspace with suffix
_CL. Note that the valueNetskope_WebTxorNetskope_WebTX_CLfor this parameter matches the Netskope published playbooks in the Azure marketplace.
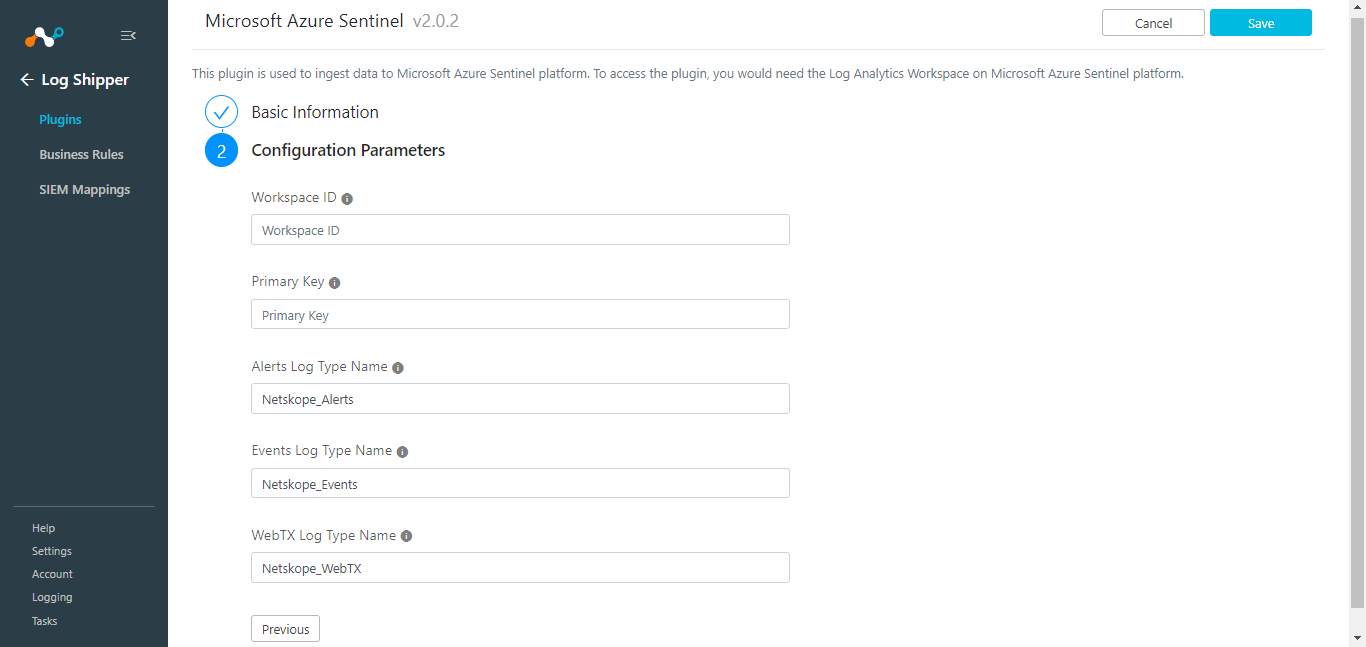
Click Save.
Skip this step if you do not want to filter out alerts or events before ingestion.
Go to Log Shipper > Business Rules.
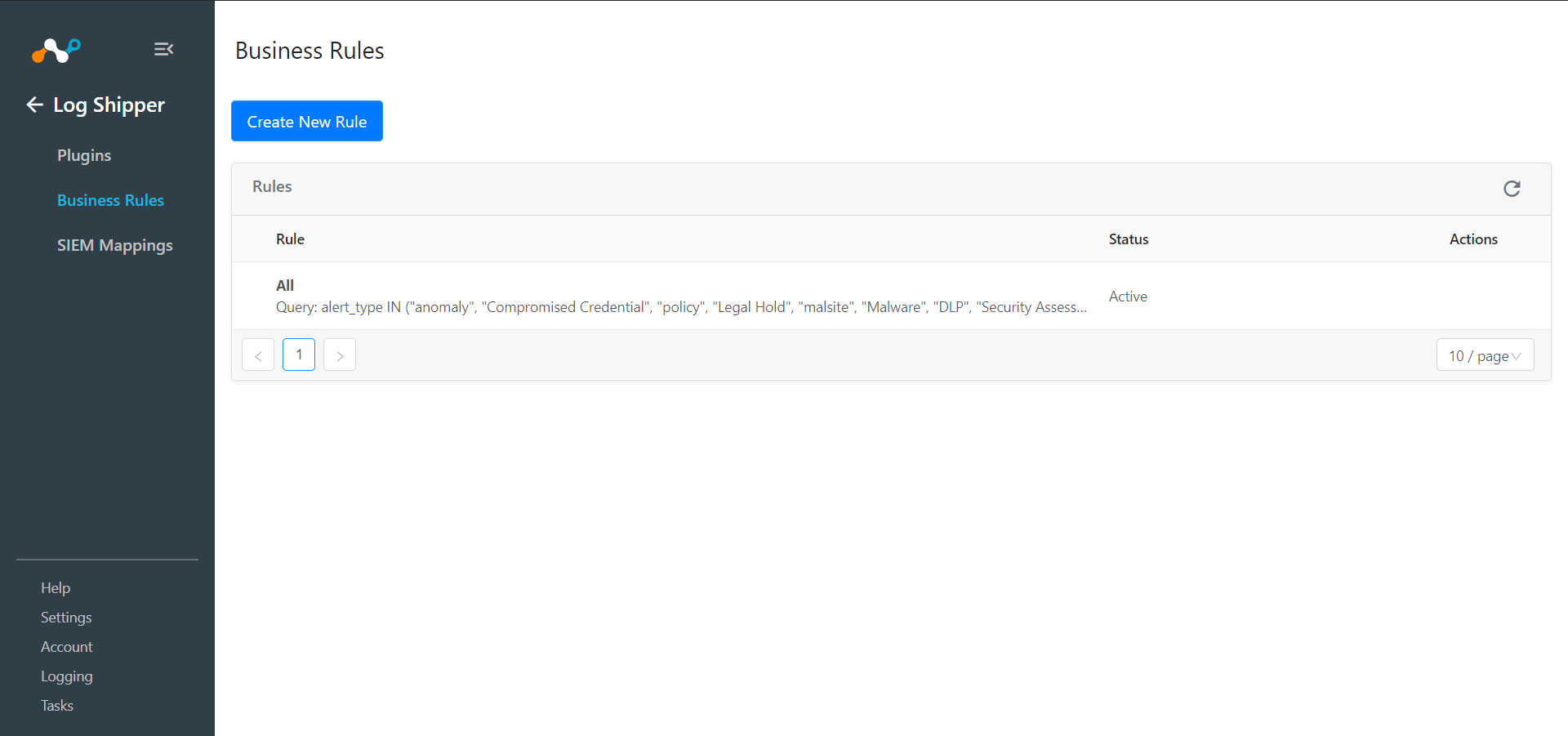
Click Create New Rule.
Note
If you want all the events and alerts ingested into your SIEM Mapping, you can use the default ALL rule.
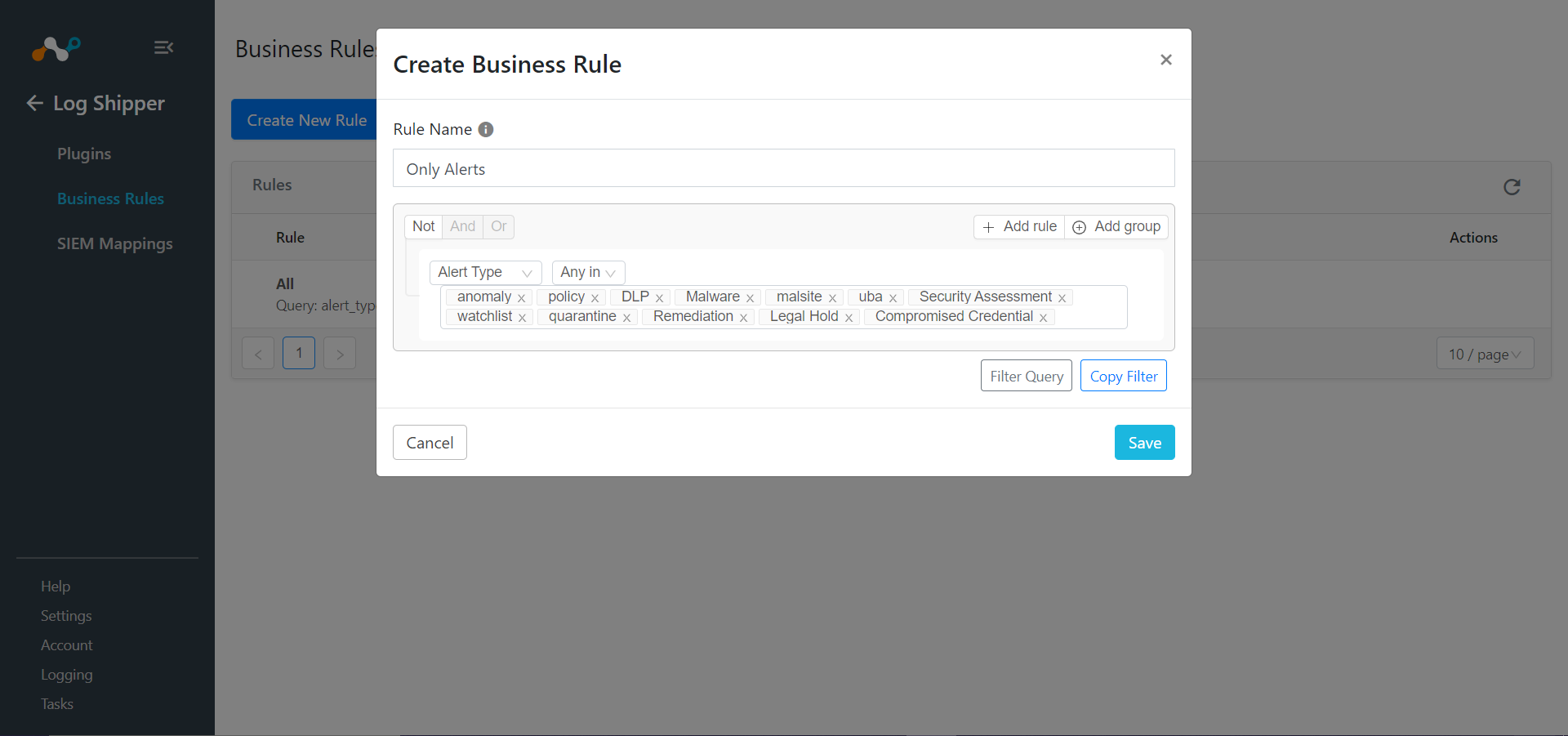
If creating a new rule, enter a Rule Name and select the filters to use.
Click Save.
Go to Log Shipper > SIEM Mappings and click Add SIEM Mapping.
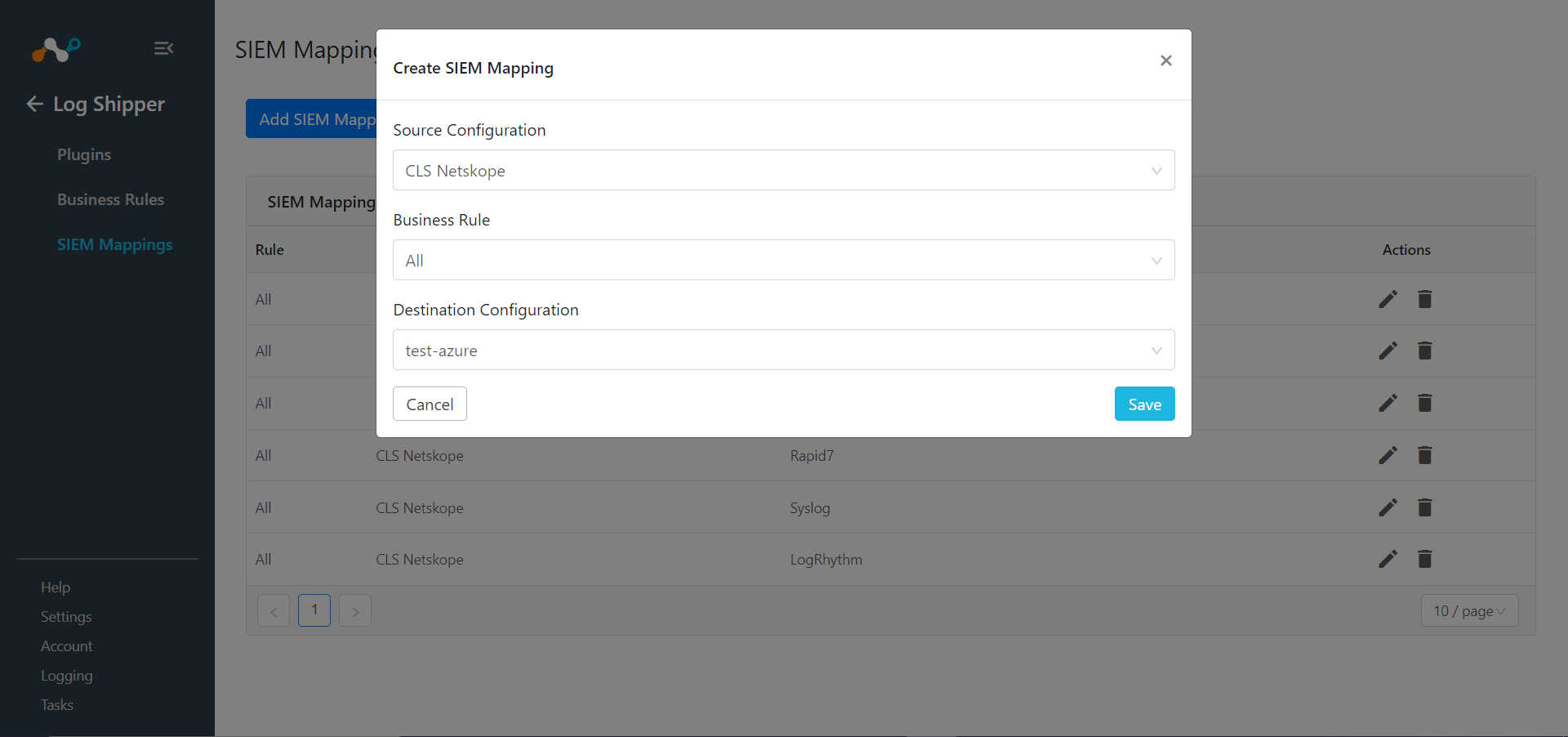
For Source, select the Netskope CLS plugin configuration, select a Business Rule, and for Destination, select the Azure Sentinel plugin configuration.
Click on Save.
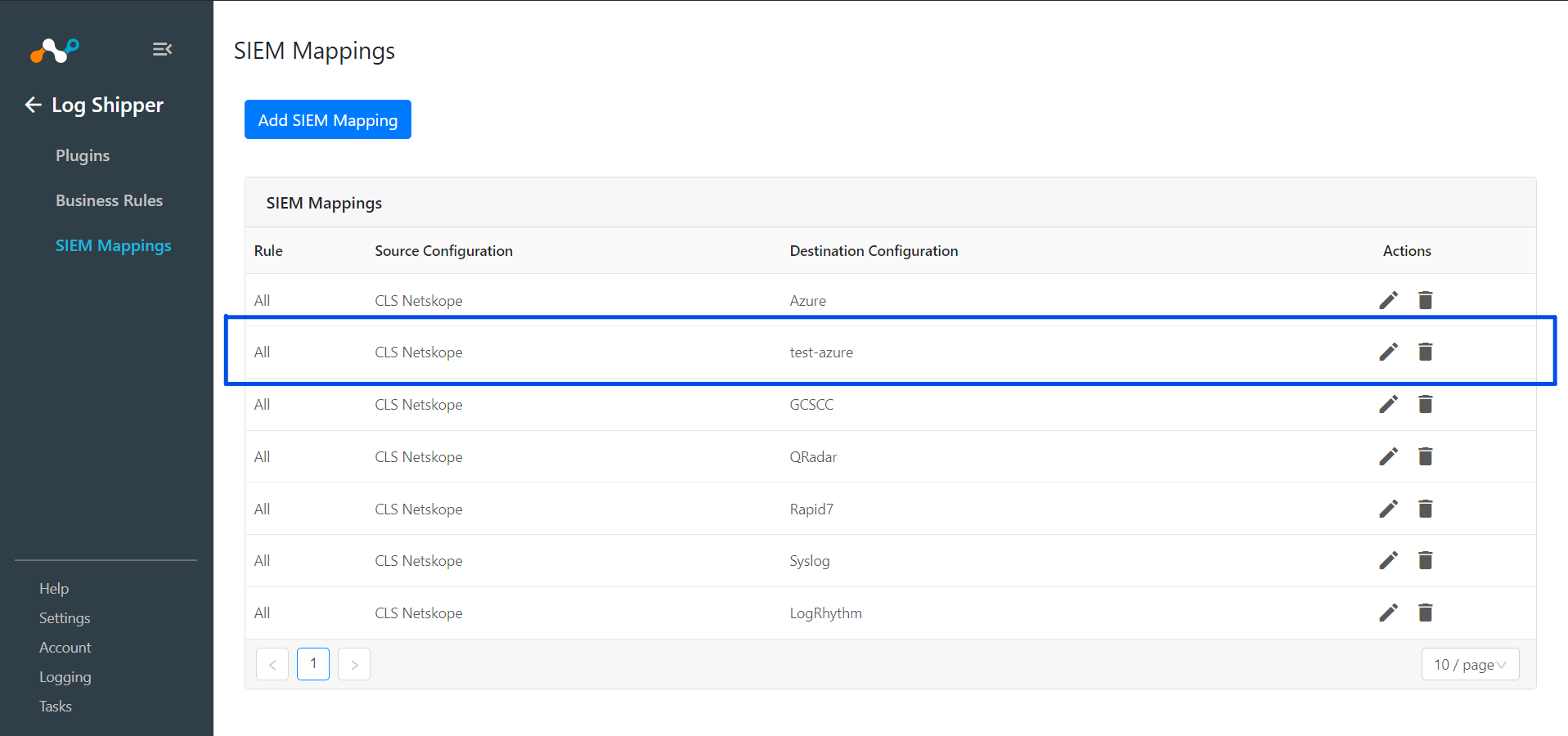
To validate the plugin workflow, you can check from Netskope Cloud Exchange and from Azure Sentinel instance.
To validate from Netskope Cloud Exchange:
Go to Logging, and . check to see if the Logs are getting ingested. Filter using message contains
<plugin_configuration_name>.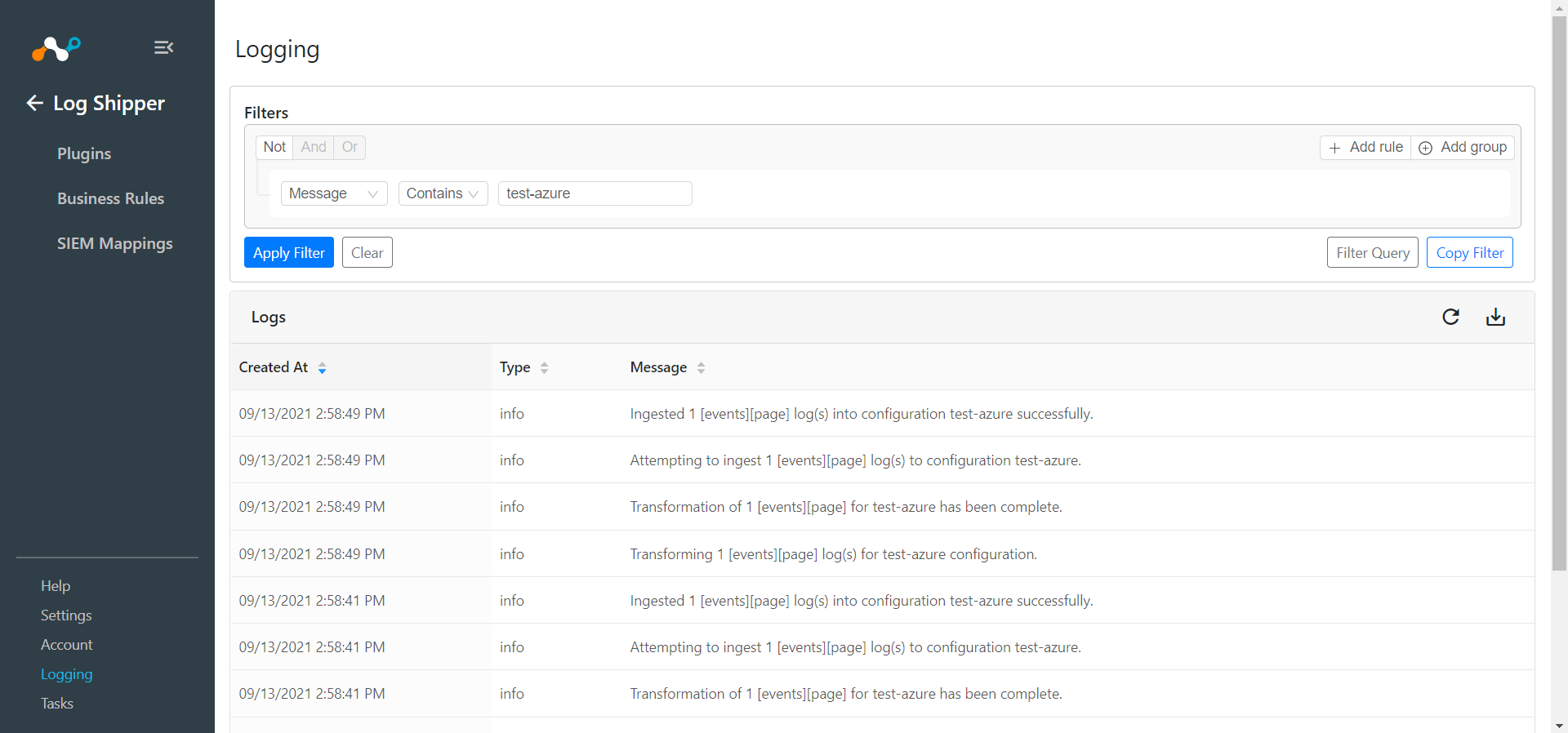
To validate from the Azure Sentinel instance:
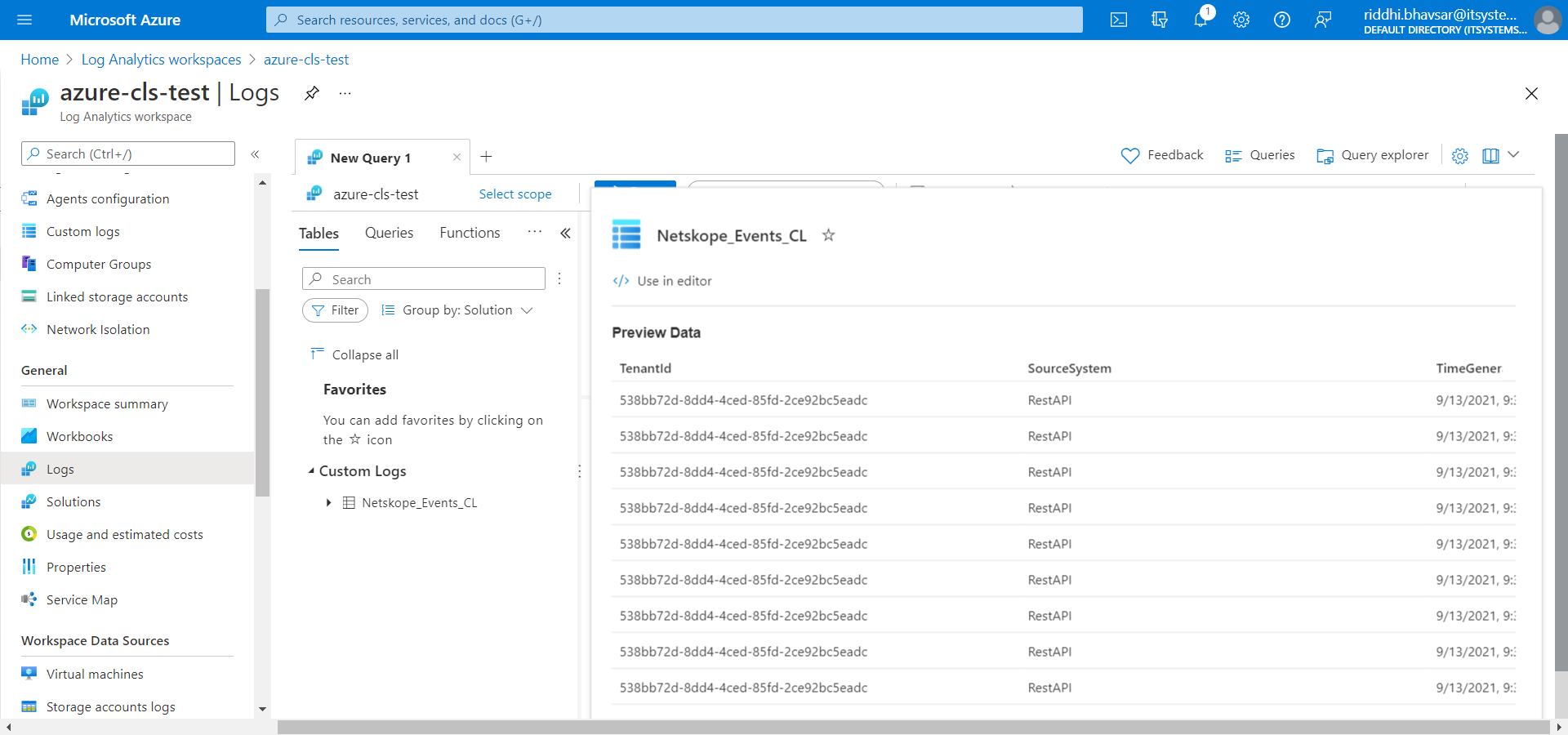
Go to Home All Services Log Analytics workspaces.

Click on the workspace name that you created.

Click Logs.
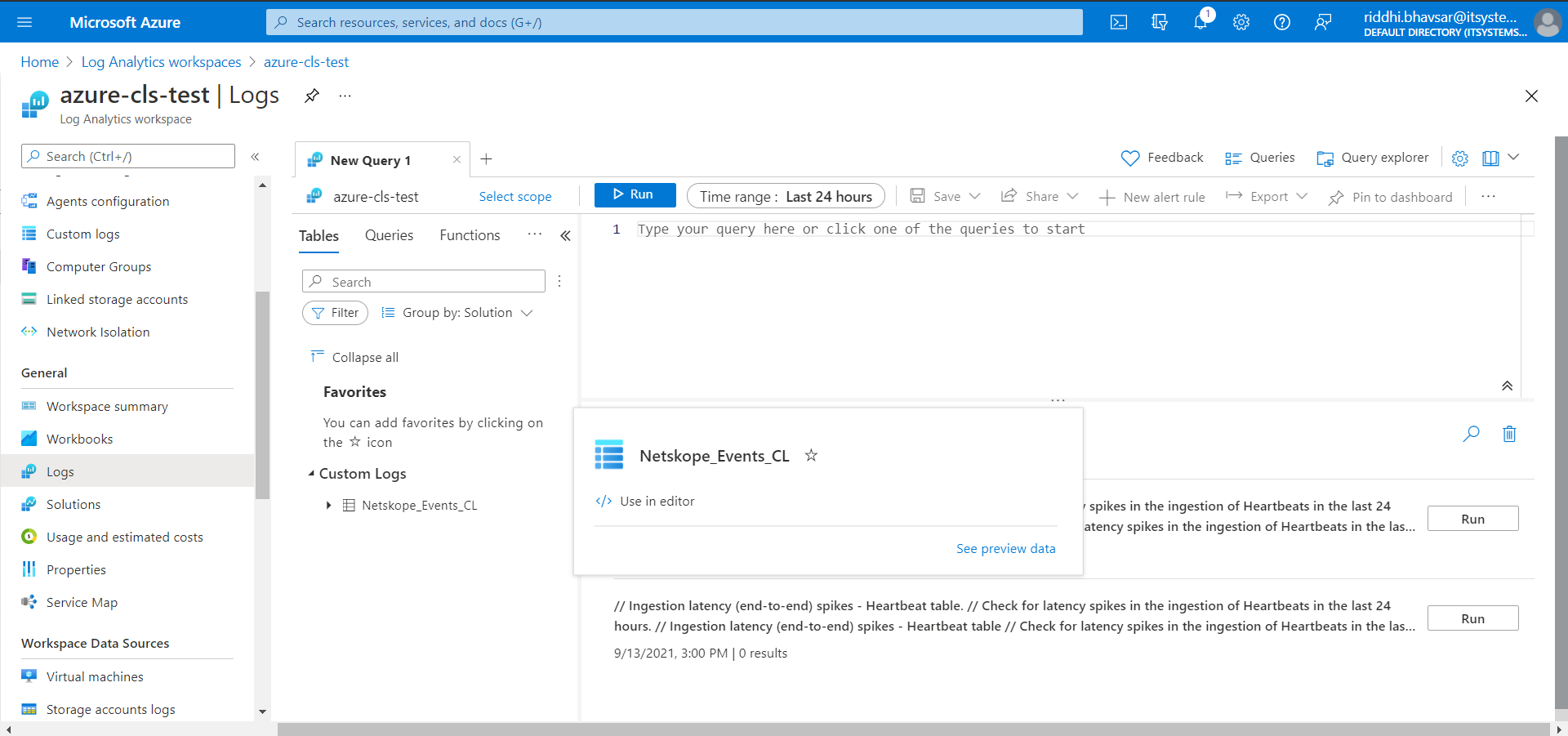
Hover over Custom Logs Netskope_Events_CL and click See preview data, or you can write your query to filter data.