Data Protection for Amazon Web Services S3
Netskope provides data protection to secure your data in AWS S3 buckets. Netskope uses DLP and Threat Protection policies to perform scans on objects in your S3 buckets. You must configure the DLP policies so that Netskope can scan your buckets. If you have Threat Protection enabled in your Netskope tenant and have defined policies, then Netskope performs Malware scans on your S3 buckets.
The following workflow diagram provides a visual representation of the steps required to configure your AWS accounts for DLP Scan and Threat Protection (Malware Scan).
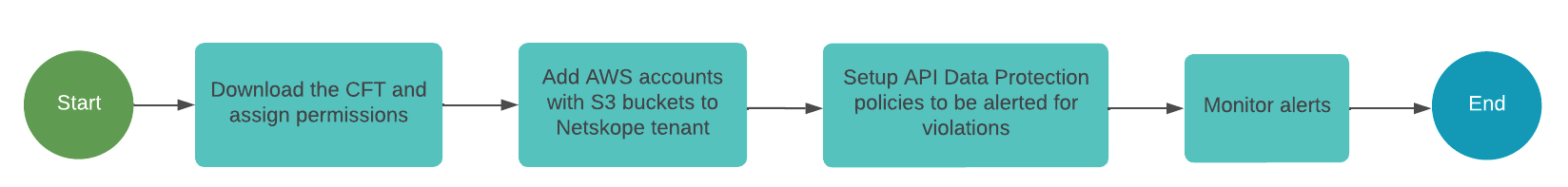
Netskope scans the buckets for DLP violations and malware with improved efficiency using CloudWatch events.
The set up uses a Cloud Formation Template (CFT), aws-instance-setup.yml that is customized with permissions required for Netskope for IaaS to create an IAM cross-account role. The role provides Netskope access to create a CloudWatch event stack called NetskopeStack in all regions of every AWS account added to the Netskope tenant. This stack subscribes the AWS accounts to Netskope's notification receiver to receive CloudWatch events generated from write, update, and delete operations performed on S3 buckets in your AWS accounts.
To learn more, see "What happens in the process?" section in Step 2/2: Configure AWS Permissions for Data Protection.
Important
Data Protection for AWS S3 does not support quarantine and legal hold functionalities. If you have configured a DLP or Malware quarantine profile with an external storage provider such as OneDrive, the file would be copied to that location. However, the file would not be removed from its original location in the public cloud storage, AWS S3.
Netskope Public Cloud Security enables you to simultaneously configure multiple AWS accounts in a single region for DLP Scan and Threat Protection (Malware Scan). To learn more: Enabling Data Protection for AWS S3.