Integrating Palo Alto Networks WildFire for Cloud Sandbox
Note
You must have the Advanced Threat Protection license to integrate Palo Alto Networks WildFire with Netskope Cloud Sandbox.
To integrate Cloud Sanbox with Palo Alto Networks WildFire, go to Settings > Threat Protection > Integration. There are two integration modes:
You can send all files supported by WildFire, which is the default mode.
You can send only the files Netskope detects as malicious to WildFire, which occurs when you select Limit Files.
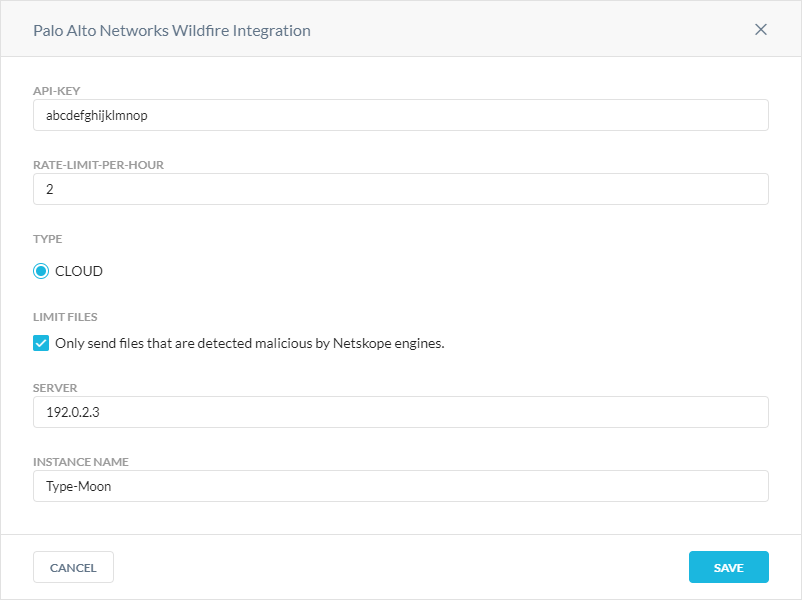
Choosing whether to send all files or only malicious ones can depend on the rate limits imposed by your third-party threat engine license (e.g., WildFire, Sky ATP, Check Point, etc.). If you only send malicious files to WildFire, the Netskope threat detection engine essentially functions as an initial filter for malicious files.
To learn more on how to get a WildFire API token with read and write permissions so you can provide it to Netskope: Palo Alto Networks WildFire documentation.
Sending All Files to WildFire
After undergoing Netskope fast scan, the file is sent for Netskope deep scan.
Netskope deep scan checks the file type and then the rate limit for each third-party threat engine (e.g., WildFire, Sky ATP, Check Point, etc.), whichever your organization has integrated with. For Wildfire integrations, the API query allows Netskope to confirm the number of files and rate limits for file submission.
Netskope deep scan sends the file to the third-party threat engine (e.g., WildFire) and generates an alert in Skope IT if the third-party engine detects any malware. The alert appears as a Malware alert type in RESTful API logs and Skope IT. The third-party service also reports on all files and file hashes that are shared, regardless whether or not there was a malicious object detected.
Sending Only Malicious Files to WildFire
After undergoing Netskope fast scan, the file is sent for Netskope deep scan.
If any of the Netskope deep scanning engines (e.g., Cloud Sandbox, Advanced Heuristic Analysis, etc.) detect the file as malicious then:
Netskope deep scan checks the file type and then the rate limit for each third-party threat engine (e.g., WildFire, Sky ATP, Check Point, etc.), whichever your organization has integrated with.
Netskope deep scan sends the file to the third-party threat engine (e.g., WildFire) and generates an alert in Skope IT if the third-party engine detects it as malicious as well.
Note
If a third-party threat detection engine detects any file as malicious, then Netskope deep scan raises the alert in both modes.
Netskope also queries if the MD5 is classified as a known malicious file and obtains the WildFire report, so you can view it in Netskope.
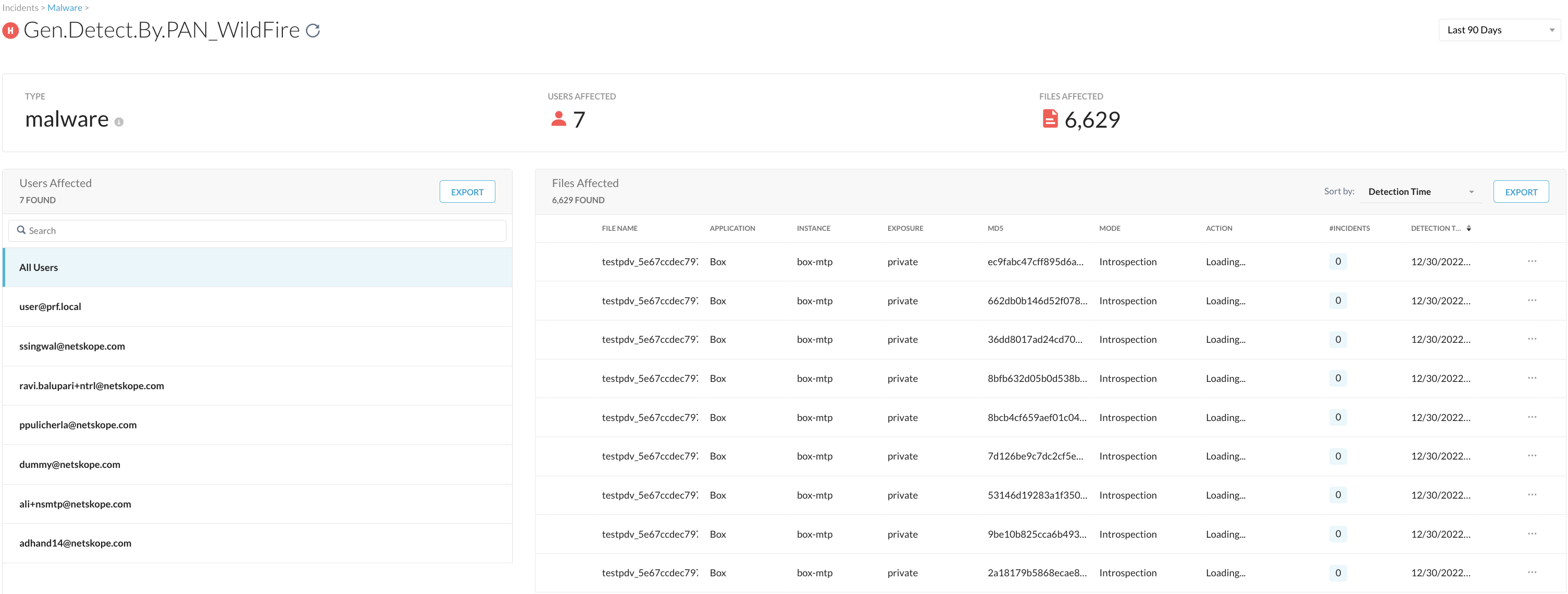
Viewing the Malware Incidents
On the Malware page, you can see the detection name called “Gen.Detect.By.PAN_Widfire”.
In Skope IT Alerts, you can see the Alert Type as Malware.
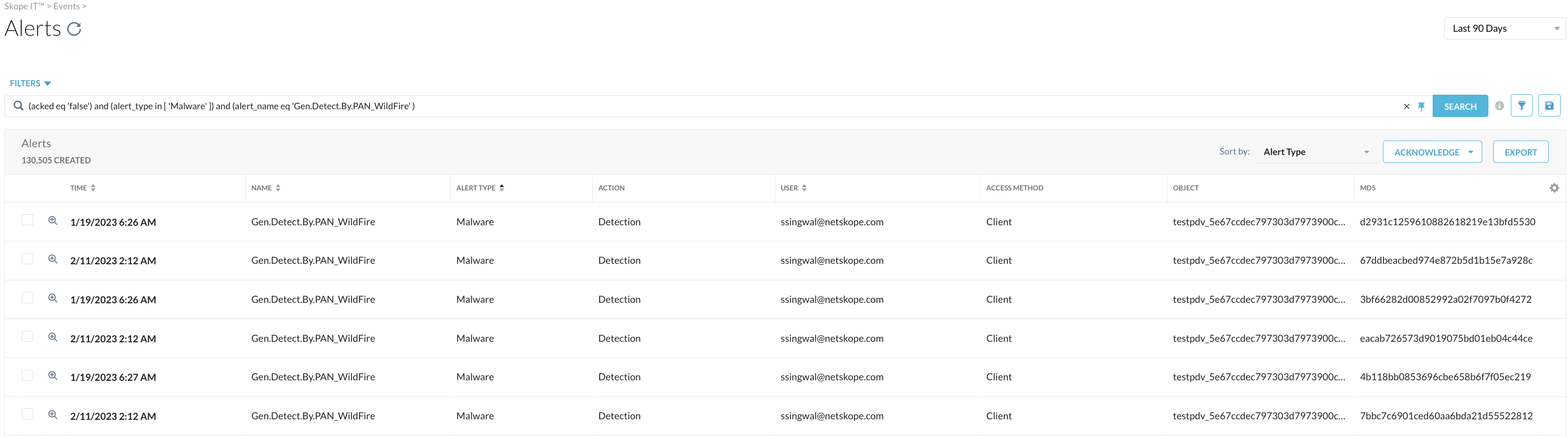
In the Alert Details, you can see the following information: