Azure Virtual Desktop
This document contains the best practices around steering bypasses when deploying the Netskope Endpoint on Azure Virtual Desktop (AVD). You can install Netskope Client in Azure Virtual Desktop using the deployment options supported by Netskope.
Supporting Operating systems: Windows 10 and 11.
Configuration Requirements
Specific configurations in Netskope webUI ensures processes or traffic from either of the applications are not blocked or directed to the Netskope Cloud.
Configurations In Netskope Client
While installing the Netskope Client in Azure Virtual Desktop, configure the following exceptions in the steering configuration to ensure proper functioning of the virtual desktop.
Destination Location - For Azure Virtual Desktop network locations.
Certificate Pinned Application - For Azure Virtual Desktop agents running on virtual desktop (Optional).
Configure Destination Location Exception
Destination Location exception bypasses traffic sent to specific destinations as defined in the network location profile.
Microsoft provides a JSON file with Azure destinations in https://www.microsoft.com. However, the list contains all destinations used by the Azure Infrastructure divided by Service Tags (Services). To avoid excluding all Azure destinations from the steering, you can include destinations involved with the Virtual Desktop Infrastructure.
Consider the following Service Tags for steering exclusions:
The IP addresses of the Virtual Desktop Gateways under the WindowsVirtuallDesktop Service tag.
Additionally, add the traffic destined to the following IP addresses:
169.254.169.254/32
168.63.129.16/32
IP addresses of the monitoring traffic under AzureMonitor service tag.
To learn more, view Required URLs for Azure Virtual Desktop.
It is difficult to manually extract IP addresses from the Microsoft Service Tag document. You can convert Microsoft JSON file to a simple .csv using a Python script and then upload them in the exceptions. Download the Python script from the Support portal.
To use the Python script:
Download the latest JSON file from the Microsoft Website: Azure IP Ranges and Service Tags – Public Cloud.
Save the JSON file and the Python script under the same folder. Rename the JSON file as AzureIPs.json.
Run the Python script from a command prompt.
Verify the contents of AzureWVD.csv created in the same folder. This contains two lines where the first line starts with AzureWVD and second with AzureMonitor.
Once you gather the CSV file, configure the Network Location Object through Policies > Network Location.
To create a Network Location object:
Login to your Netskope webUI and go to Policies > Network Location (under Profiles).
In the Network Location page, click New Network Location and select Multiple Objects.
In the Upload Network Locations pop-up window, select the, csv file (max size 8 MB) with the list of destination addresses. The .csv file must have entries in the following format: [Net Location Name], [IP Address 1], [IP Address 2], , , For example, Location1, 11.2.3.4, 12.3.5.125/16. For example, upload AzureWVD.csv file.
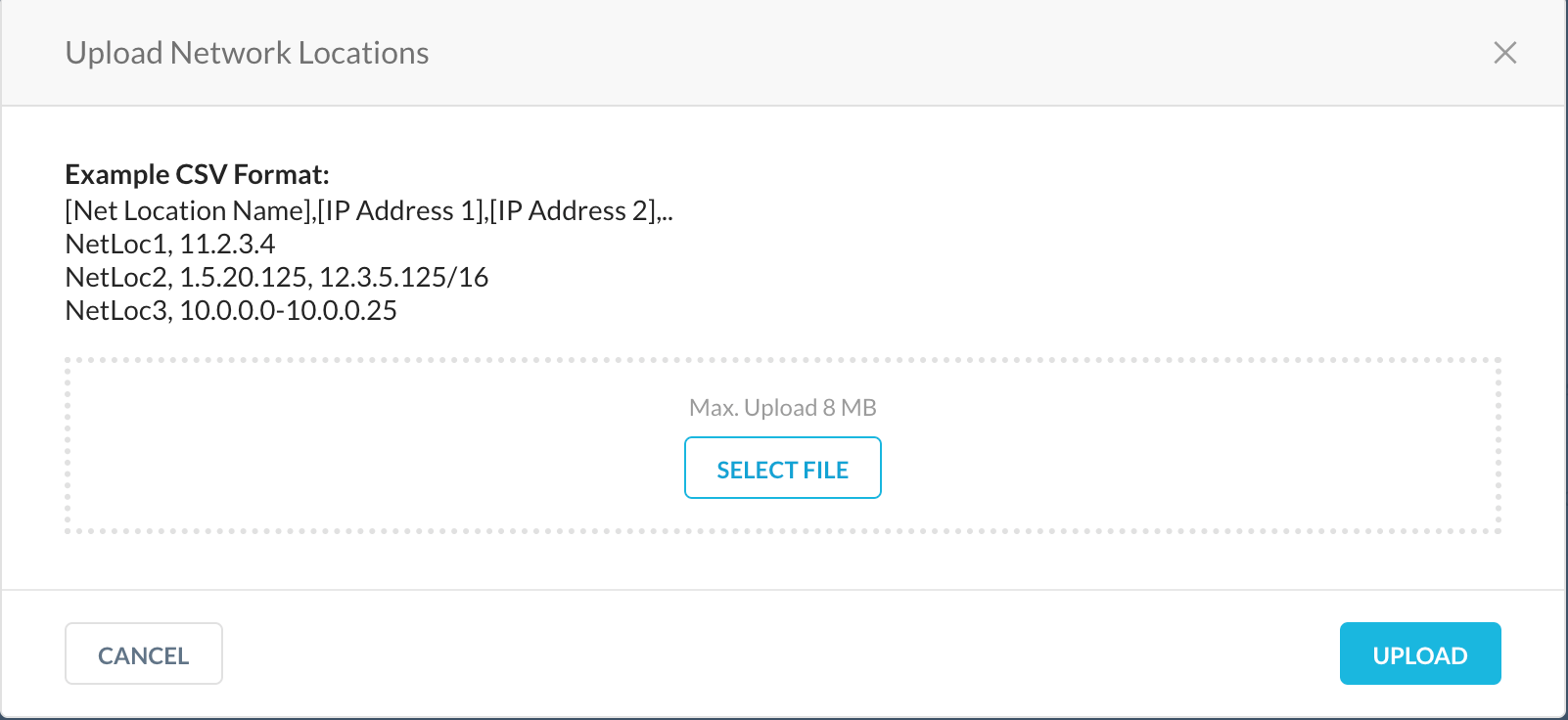
Click Upload to complete the process.
Verify the newly created AzureWVD and AzureMonitor network location to see if they contain the imported IPs.
Click Apply Changes.
To create Destination Location exception:
Go to Steering Configuration and select a configuration.
In the EXCEPTIONS tab, click NEW EXCEPTION drop down list and select Destination Location.
In the New Exception pop-up window, select the Network Location profile from the list. Select AzureWVD and optionally select AzureMonitor if you want to exclude the monitoring traffic.
Select Treat like local IP address.
Click ADD to complete the process.
Note
Microsoft updates the list of destinations in their Service Tags file and publishes a new version. Since the IP addresses of the Remote Desktop Gateways changes less frequently, Netskope recommends updating the exclusion list if you encounter disconnections with the virtual desktop upon login. In this case, you must re-create a new steering exception as the current exceptions are deleted upon the destination Location overwrite.
In order to update the AzureWVD and AzureMonitor Network Destination lists, you can repeat the steps to convert the JSON file to a .csv file. Once you have the .csv file, create a steering exception. While uploading AzureWVD.csv in Policies > Network Location > New Network Location > Multiple Objects, the user interface (UI) displays duplicate entries for AzureWVD and AzureMonitor. The old entries gets removed once you Apply Changes.
Configure Certificate Pinned App Exception (Optional)
You can add the Certificate Pinned App exception if you want to bypass all traffic performed by the Azure Endpoints installed on the device.
To add Azure Virtual Desktop as a Certificate Pinned Application on the Netskope UI:
Go to Settings > Security Cloud Platform > Steering Configuration.
Click Default tenant config to levarage the default configurations or you can click NEW CONFIGURATIONS to create a new steering configuration.
On the configuration page, click EXCEPTION > NEW EXCEPTION > Certificate Pinned Applications.
In the New Exception window, do the following:
From Certificate Pinned App, select the application. To add a new certificate pinned application in the New Certificate Pinned Application window, do the following:
Application Name: Enter the name of the application.
Platform: Select the operating system where the application is managed.
Definition: Provide the processes and .exe(s) list that you want to bypass. Here, add the following processes:
WindowsAzureGuestAgent.exe: Azure VM Agent service
WaAppAgent.exe: Azure RD Agent service
WindowsAzureNetAgent.exe: Azure Network Agent service
WindowsAzureTelemetryService.exe: Azure Telemetry Service
metricsextension.native.exe: Azure Monitor Agent
rdagentbootloader.exe: Azure Agent Bootloader
From Custom App Domains, add * to bypass all the domains.
From Actions, select Bypass for Windows.
Click ADD.