Cloud Exchange Feature Lists
To stay up to date on all new features, ensure you configure your platform to notify you whenever there is an update to Cloud Exchange by enabling the "check for updates" button under Settings > General as shown here.
Setup script to streamline installation
Selective module enablement (one, two, or more)
Multi-instance/tenant support (more than one Netskope platform can be connected to CE, for example).
Automated checks for updated code in Docker-hub and automatic or manual enablement of updates.
Automated checks for updated or newly published plugins.
Support for additional plugin repositories.
Proxy support.
Support for high-availability clustering using Dockerswarm.
Validated workflows for running on RHEL 8.0 (running podman) and Ubuntu 18.04 or newer
Support for APIv2 endpoints (where there is an alternative to v1).
Support for User Confidence Index scores.
Support for customer-generated/provided SSL certificates.
Clone, edit, delete workflows for all rules.
Sort on all indicators, actions.
Role Based Access Controls (superuser, admin, read-only, and module-specific read/write access) in GUI and for API tokens.
All plugins API communications to 3rd parties include a user-agent string in the HTTP header identifying the source as Netskope Cloud Exchange and the version (netskope-ce-3.0.0).
Supports configuring the number of workers via changes to an environment variable if the default number (six) is insufficient.
Local login or Single sign-on support for IdPs supporting SAML
GUI and API access to all commands via TLS1.3 SSL.
Onboard help documentation, including links to Swagger for API commands
In UI system notifications (queued and able to be acknowledged) reflecting audit and system logs.
On UI system notifications for disconnected or malfunctioning plugins.
On UI system showing tasks completed or in queue to enable troubleshooting.
Diagnose script to streamline log and system collection for troubleshooting.
The "is empty" operator has been added to filter out Netskope fields that are empty or null.
Introduction to Horizontal Scaling
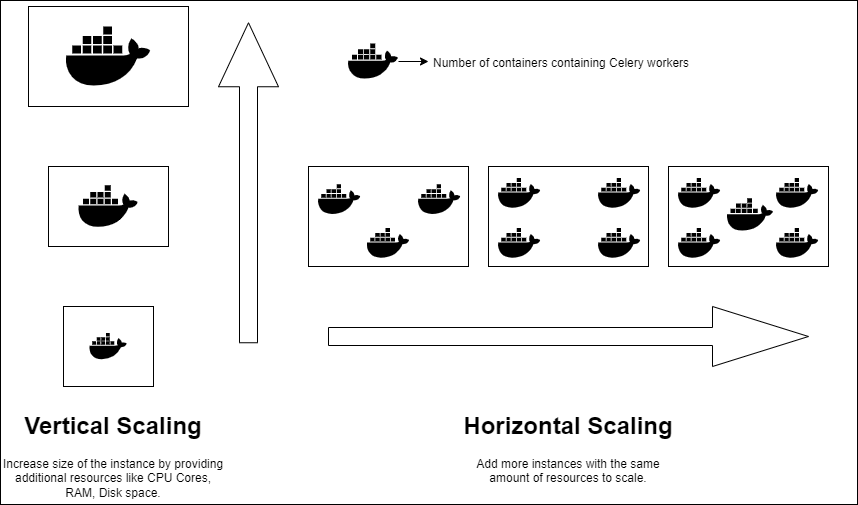 |
Implementing horizontal scaling in Kubernetes and OpenShift deployments of cloud exchanges is an effective approach that allows organizations to minimize infrastructure expenses while attaining excellent availability and resilience.
By horizontally scaling, the system distributes the workload across multiple instances or nodes instead of relying on a single, resource-intensive machine.
This approach not only optimizes resource utilization but also ensures that the system can handle increased traffic or demands by adding more nodes to the cluster.
As a result, cloud exchange can dynamically scale their applications based on demand, effectively reducing infrastructure expenses by allocating resources efficiently.
Furthermore, horizontal scaling enhances fault tolerance as multiple instances of the cloud exchange are running simultaneously.
If one instance of cloud exchange fails or experiences issues, the remaining instances can seamlessly handle the load, maintaining uninterrupted service availability.
The combination of cost reduction, high availability, and fault tolerance makes horizontal scaling in Kubernetes and OpenShift deployment of Cloud Exchange a highly advantageous technique for modern, scalable infrastructure management.
Log Shipper regularly and persistently executes polls against the Netskope REST API gateway to extract raw JSON formatted event and alert logs and push a newly formatted version out to one or more receivers, configured as a plug-in. It does this using a sophisticated algorithm to use a multi-threaded query engine, working within rate limits (4 queries/second), and handling error responses and datasets larger than its pagination limit (10,000 logs per response) in order to deliver all requested logs during initial seeding and near-real time activities.
Configure the frequency of polling.
Filter queries to the exact types of events and alerts desired to be retrieved.
Use business logic to further refine the exact data to be sent to one or more receivers.
Use and configure SIEM mapping files to add, modify, and delete fields and field data to create custom formats that deliver field data in a desired, deterministic order .
Designate, during plugin configuration, the SYSLOG protocol (UDP, TCP, or TLS).
Designate the UDP/TCP port.
Provide a dashboard to see total logs ingested, connector state, and breakdown of log destinations.
Plugins that are ready include: Rapid7, Azure Sentinel, LogRhythm, IBM Qradar, Google Cloud Security Command Center, Microsoft Cloud Application Security, Google Chronicle, Elastic (agent), generic (configurable) SYSLOG CEF (usable by AlienVault, Solarwinds, Devo), and Netskope Web Transactions storage in AWS, GCP, and Azure.
Support for Event streaming (aka web transaction logs using v2 endpoint) logs as part of each plugin feed in uncompressed format - does not apply to AWS S3, GCP, and Azure Blob plugins
Ticket Orchestrator extracts alerts, and the fields in those alerts, generated by Netskope in response to user and system behaviors/discoveries, and creates tickets and/or notifications in 3rd-party ITSM/IR/collaboration systems to streamline incident response.
Configure the frequency of polling of Netskope tenant for new customer alerts.
Creation and management of tickets inside attached ITSM systems based on filtered alerts raised by a customer Netskope Security Cloud, including Jira and ServiceNow.
Facilitate the creation of notifications based on filtered alerts in configured sub/pub systems (including Slack, Twilio, PagerDuty) as well as by sending custom-formatted email.
Supports filtering of alerts to query to focus on a key subset.
Sophisticated filtering includes business rule logic, complete with deduplication and muting of tickets to prevent noise.
List alerts and their associated metadata that have been surfaced by Netskope and polled by Ticket Orchestrator and search within these.
Copy these search queries to business rules to streamline rule creation.
Supports filtering of obtained alerts to match ticket creation workflow queue(s).
Obtain ticket queues from Jira and ServiceNow (ITSM SecOps) and surface those to streamline the destination choice for created tickets related to matching business rules.
Validate number of tickets that would be created if a rule was implemented prior to enabling.
Display list of tickets created with the associated and configured plug-in, including metadata and a link to take the user to the ticket within the associated ITSM system.
Acknowledge Netskope sourced alerts inside ServiceNow ITSM or SecOps (requires installing ServiceNow approved and hosted helper application).
Mute Netskope sourced alerts inside ServiceNow ITSM or SecOps (requires installing ServiceNow approved and hosted helper application).
Mute Netskope ticket workflows from within the Ticket Orchestrator business rule menu.
Invoke deduplication on business rules to prevent multiple alerts from being created from multiple matching alerts (only the first rule match results in a ticket).
Capture differential for de-duplicated tickets and append to existing tickets or send via notifications
Plugins that are ready include: Atlassian Jira, ServiceNow (ITSM and SecOps), Slack, PagerDuty, Twilio, and generic email plus other pub/sub compliant notification systems.
Threat Exchange is designed to streamline and automated the sharing of indicators found/blocked/sourced by one security or IT platform in defense of a specific customer to every other connected platform owned or used by the same customer that can leverage that data, to reduce the likelihood of success of an attack.
Supports connected plugins to multiple instances/tenants (one plug-in configured to work with Netskope production tenant, another for Netskope development tenant, for example).
Supports multiple configuration destinations per vendor solution (push different information to different parts of vendor systems for different uses).
Supports upload and installation of customer/partner-created plug-ins leveraging the sample scripts provided (enabling additional systems to be added on a per-customer basis).
Extracting customer-specific malicious IP/URL when detected (as configured and as supported).
Sharing customer-specific malURL/IP with other IT/Security systems (as configured and as supported, unilateral).
Sharing workflows between configured integrated systems are configurable using business rules.
Automatically tags and excludes invalid URLs that were unsuccessfully shared with Netskope as reported in the API response(s) from the REST API gateway.
Extract customer-specific malicious file hashes when detected and as supported in SHA256 or MD5 format.
Sharing customer-specific malicious file hashes with other IT/Security systems (as configured and as supported, unilateral).
Extract customer-specific malicious IPv4 addresses when detected in SHA256 or MD5 format (when configured and as supported).
Sharing customer-specific malicious IP addresses with other IT/Security systems (as configured and as supported, unilateral).
Extract customer-specific file file hashes, when scanned, for use by other plugins for DLP protection in SHA256 or MD5 format (when configured and as supported).
Facilitate the ongoing configuration of custom URL files for use in restrict or allow secure web gateway policies inside Netskope.
Lists metadata for all obtained IOC, including first seen/last seen (by Threat Exchange), internal hits (seen by Netskope)/external hits reported (by other Threat Exchange integrations), reputation, number of times IoC reported, which system/plug-in reported, additional data as supported/provided by each vendor (URL string to a deeper dive into the original detection event, for example).
Reports plug-in working (up arrow) or not (down).
Tagging of indicators in support of manual curation and to enable staging of indicators for sharing (share IOC tagged with ‘validated’ for example).
Management of global tag dictionary.
Search support within Threat Exchange database.
Ability to copy Threat Exchange search string into plug-in(s) for use in sharing.
Sophisticated filtering includes nesting multiple filters using Boolean logic, including NOT.
Filtering of indicators pulled by respective plug-ins (by timeframe, severity, type, etc.).
Filtering of indicators pushed by respective plugins to 3rd-party systems (by timeframe, severity, type, tag).
Configuration of polling interval (from seconds, minutes, hours, days).
API commands to modify, add, disable indicators or their metadata (change severity, add tags).
Support for overwriting default reputation of IoC sources per configured plug-in for use in sharing rules.
Theoretically infinite retention of disabled IoC (expired IoC are not deleted from database, but disabled for purposes of sharing).
Plugins are ready for use: ServiceNow, Mimecast, ProofPoint, Cybereason, Crowdstrike, Microsoft Defender, Microsoft MCAS, SentinelOne, VMware Carbon Black, ThreatQuotient, STIX/TAXII, MISP, FireEye (using API module from Helix), Github (for DLP prevention), and the sample plugin.
CrowdStrike reported severity is now mapped as received into severity in the Threat Exchange database.
Risk Exchange includes two workflows, User Risk Exchange, and Application Risk Exchange. Value ranges can be weighted as needed to create a single score per user, and a daily average across all users/devices/applications. By leveraging business logic, you can match individual scores, score combinations, or weighted scores as nested, ordered triggers to send notifications via CTO plugins, and/or trigger one or more preconfigured orchestrated actions as made available in individual plugins.
Configure the frequency of polling.
Filter queries to the exact types of scores desired to be retrieved.
Use business logic to further refine permutations of scores of concern.
Designate actions to take when those business logic rules are matched.
See in the dashboard average score of all tracked users or devices, the score of yesterday and today, the delta between those scores, and the score trend over a configurable timeframe.
Dashboard displays top 10 riskiest users/applications (with the lowest weighted score).
See all and filter to find individual users or device weighted scores and modify if needed.
Set and modify weights of individual plugin scores.
Validate/test effect of changing individual plugin score weights by observing predicted new percentage of each risk category.
See log of all actions taken.
See log of all normalized data received from plugins.
Plugins that are ready include: Netskope (user), CrowdStrike (device), KnowBe4 (SecurityAdvisor) (user), Okta (user), Mimecast (user), Microsoft Azure AD (user), Google BeyondCorp Enterprise (host), ProofPoint (user), SecurityScorecard (Applications), ServiceNow (Applications), and ThirdPartyTrust (Applications).