Devices
The Devices page focuses on monitoring the Client's status of all the devices in your tenant. You can export your entire device list to CSV file. To open the Devices page, go to Settings > Security Cloud Platform > Netskope Client > Devices.
Enable and Disable Device(s)
To enable or disable the Netskope client, or collect logs from a device, click the checkbox next to the hostname and click Enable or Disable. These buttons remain grayed out until you select a hostname.
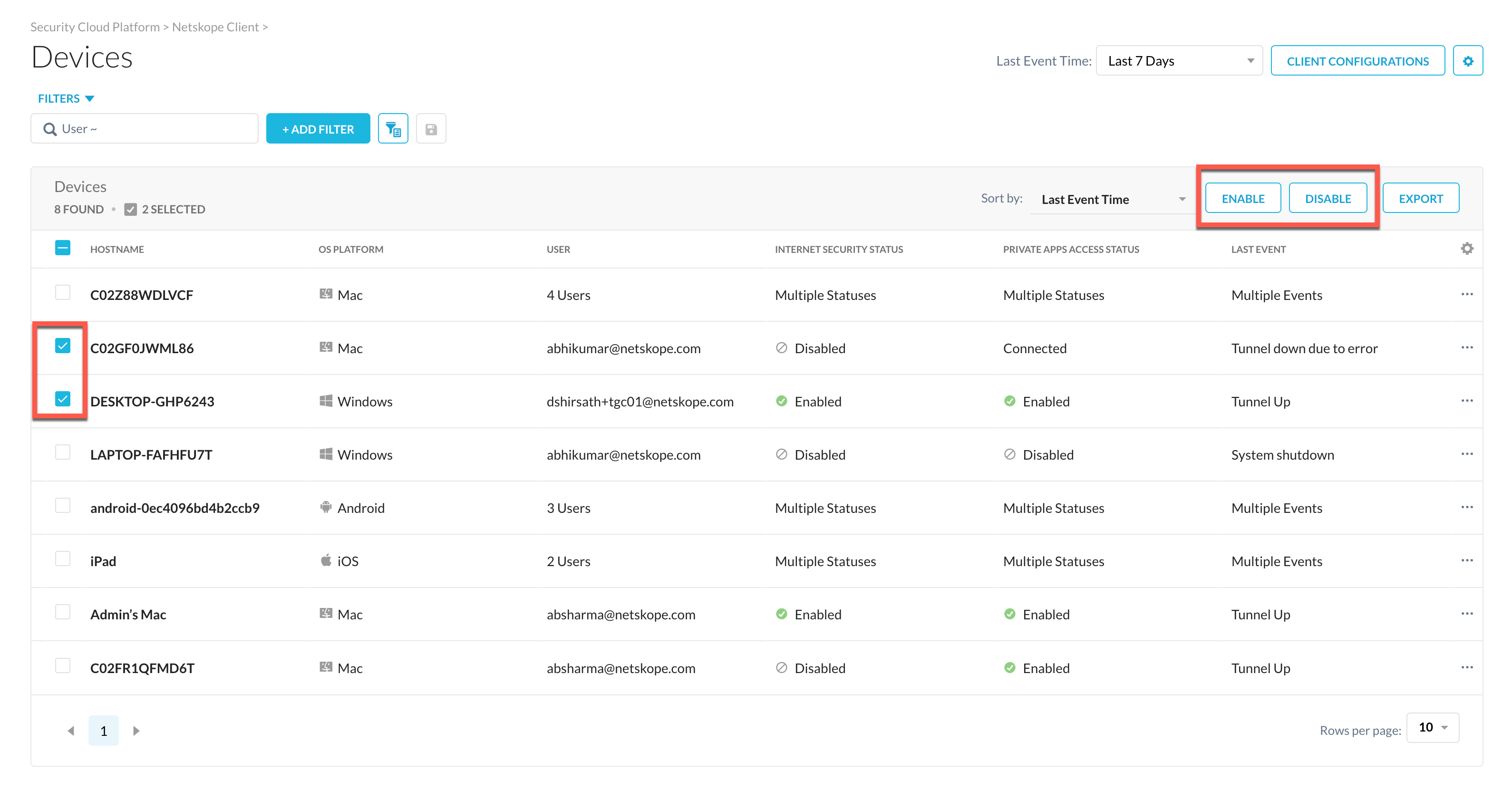 |
Logs can only be collected from individual devices, but you can enable and disable the Netskope Client on multiple devices at one time.
Search Functionality
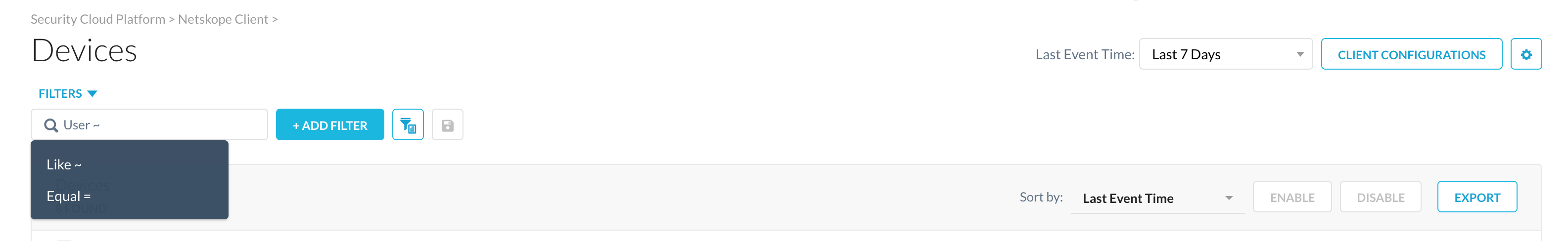
You can use the Search functionality to look for a specific device added in the tenant. To search for a device, enter the username in the search field. The search is not case-sensitive and you can get search results that are Like ~ or Equal = to the text entered in the text box.
 |
Filters
The Devices page displays information based on the selected filter.
Default Filter
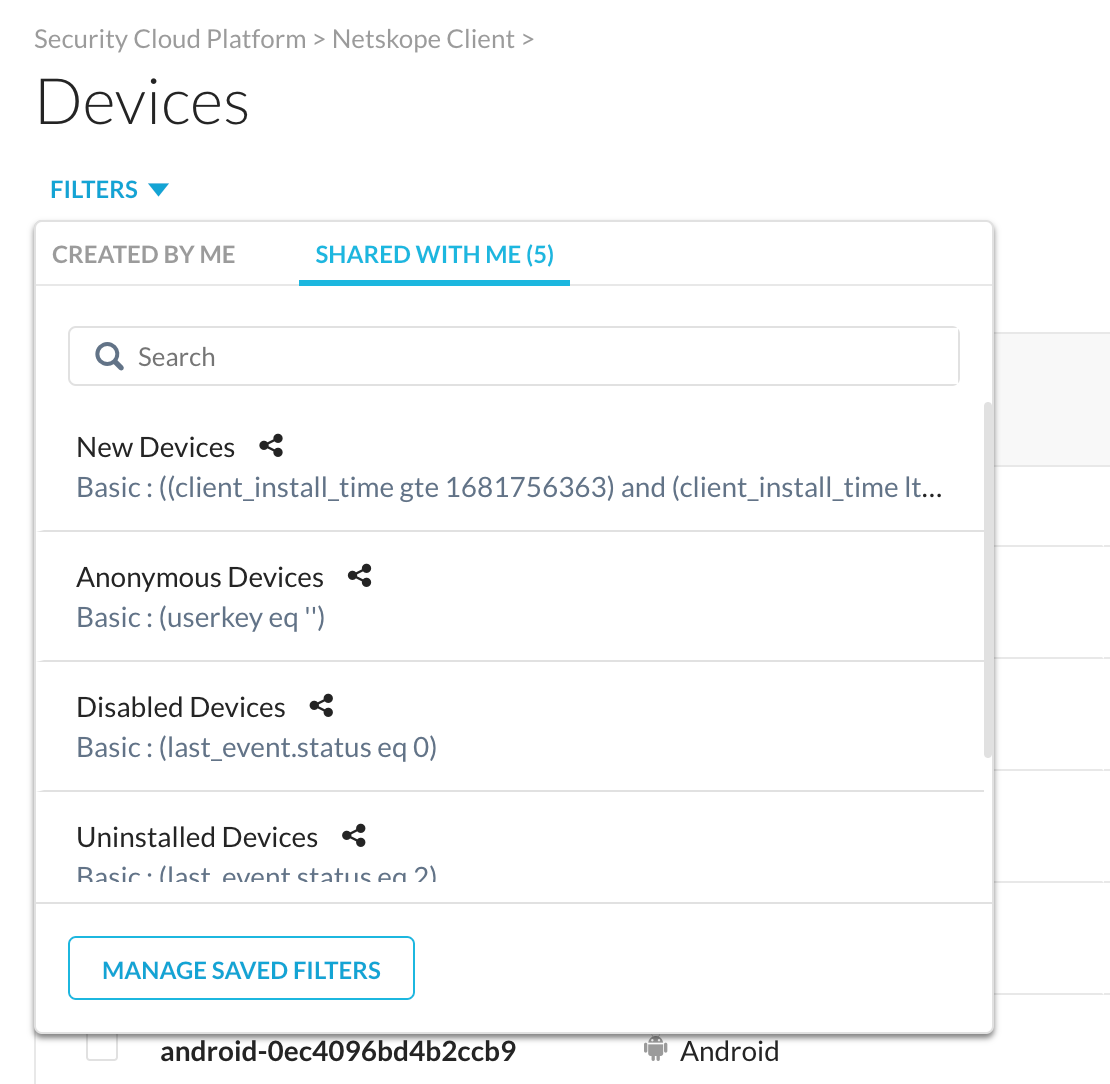
You can click FILTERS above the Search text box to select the default filter. The filters are either created by you or shared with you. The following are the default filters:
All Devices: Displays all devices within your tenant where the Netskope client is installed.
New Devices: Displays all devices with Netskope Client added within the last 24 hours. You can change the filter to search using options from the Last Event Time dropdown menu. For example, Last 7 days, Last 30 days, and so on.
Anonymous Devices: Displays devices where the the user has not logged after installing the Netskope client.
Disabled Devices: Displays devices where the Netskope client is disabled. Devices can end up in this state when an admin has taken through the admin console, or when an end user (if allowed) has client from the device.
Uninstalled Devices: Displays devices where the Netskope Client is uninstalled.
Installation Failure: Displays devices where the Netskope Client installation failed.
 |
Custom Filter
To use custom filters, click +Add Filter and select a filter. Enter text in the search field to display devices on the Devices webUI.
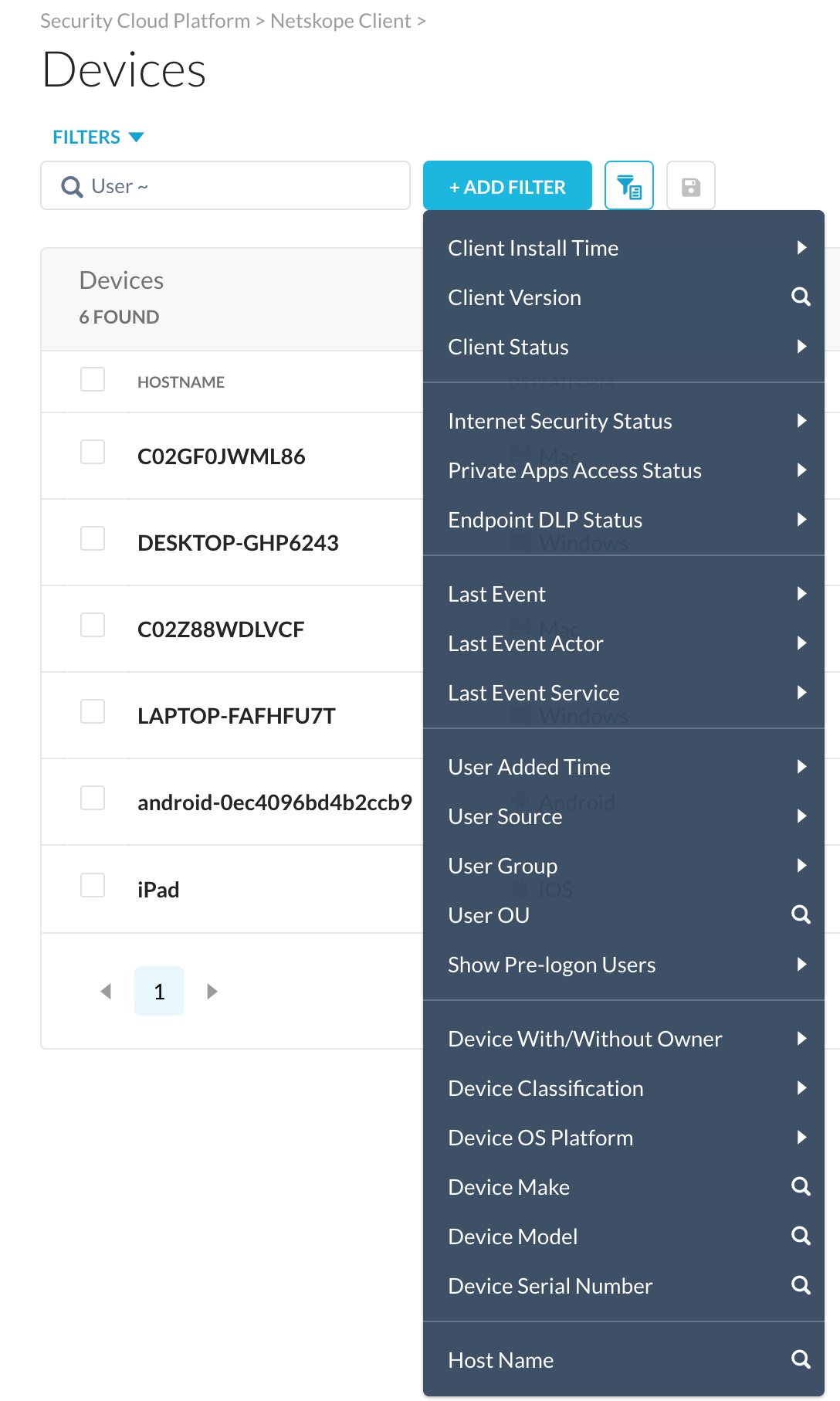 |
The following table refers to the filters that you can use to refine your search results:
Filter Option | Description |
|---|---|
Client Install Time | The time taken to install the client in a device. |
Client Version | You can view devices tagged to a specific version. |
Client Status | Filter devices according to the current client status. |
Internet Security Status | Display devices with respect to the internet security status such as Enabled, Disabled, Errored, Fail Closed, and Backed Off. |
Private Apps Access Status | Display devices with respect to the private app access status such as Enabled, Disabled, and Errored. |
Endpoint DLP Status | Display devices with respect to the private app access status such as Enabled, Disabled, and Paused. |
Last Event | Display those devices where the client last event posted was installed, enabled, or disabled by the admin or user. |
Last Event Actor | Displays those devices where the events are created by user, admin, or system. |
Last Event Service | Displays devices where the event service is either Internet Security or Private Apps Access. |
User Source | Displays devices where the users are sourced from AD or local. |
User Group | Displays devices where the users added in that device is also a part of the listed user groups. |
User OU | Displays devices based on the organizational units. |
Show Pre-logon Users | Displays devices where the Pre-logon users options are added or not. |
Device Classification | Displays devices according to their status like managed, unmanaged, unknown, not configured. |
Device OS Platform | Displays devices according to the operating system. |
Client Configuration
You can configure system-wide settings using the Client Configuration dialog box. Click Client Configurations displayed at the top right corner of the Devices page to open Client Configuration. To learn more, view Client Configuration.
Device Information
The following lists the various components to display the Device information on this page:
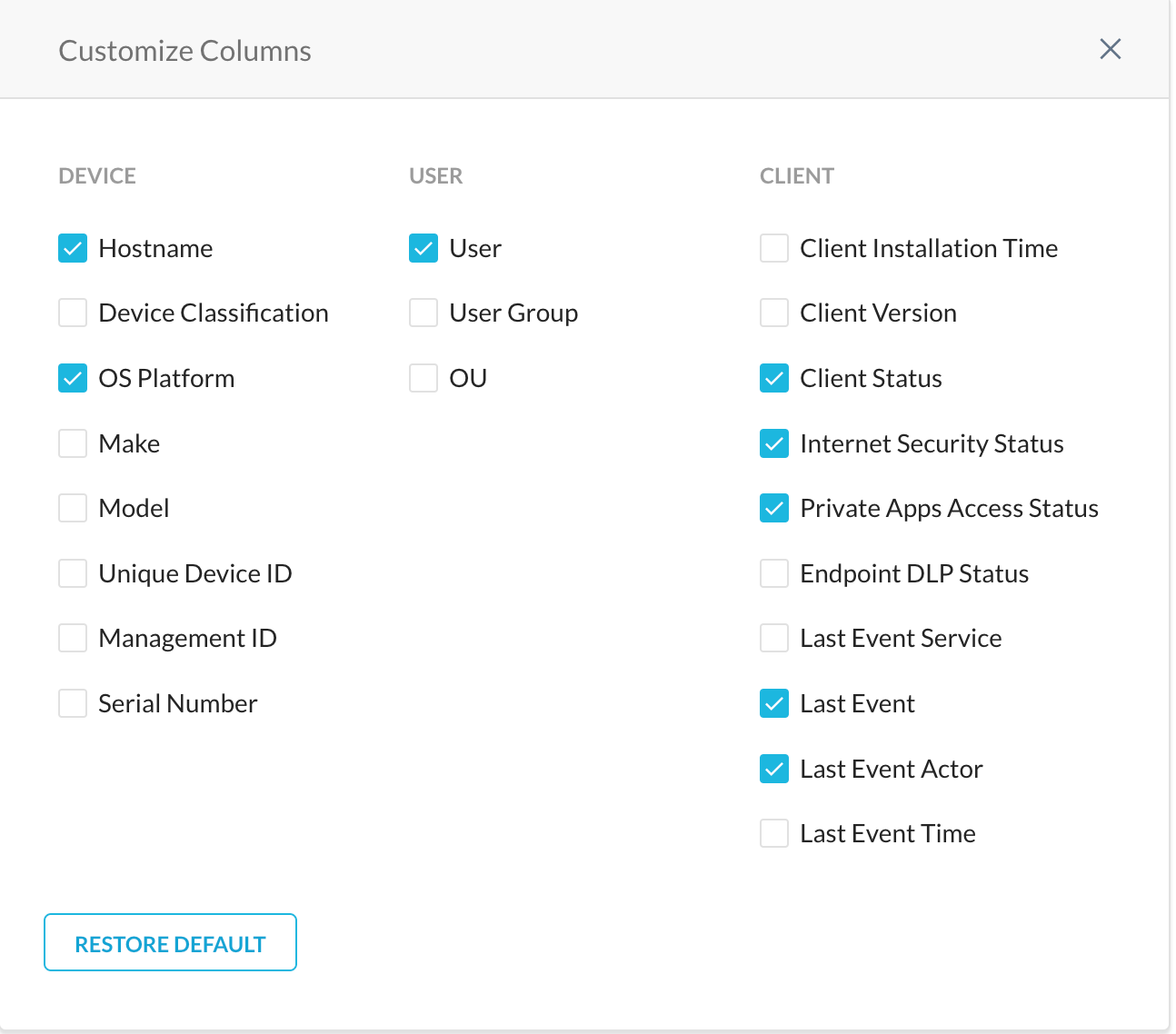 |
Hostname
Note
For Android and iOS devices, the device serial number is displayed as NA.
Device Classification
OS platform
Make
Model
Unique Device ID
Management ID
Serial Number
User (displays user email address)
User GroupOU
Client Installation Time
Client Version
Client Status
Internet Security Status
Private Apps Access Status
Endpoint DLP Status
Last Event Service
Last Event
Last Event Actor
Last Event Time
Important
For Netskope Clients with version older than 104.0.0, the webUI does not display the following statuses and the respective columns appear blank:
Client Status
Serial Number
Last Event Service
 |
Additional Information
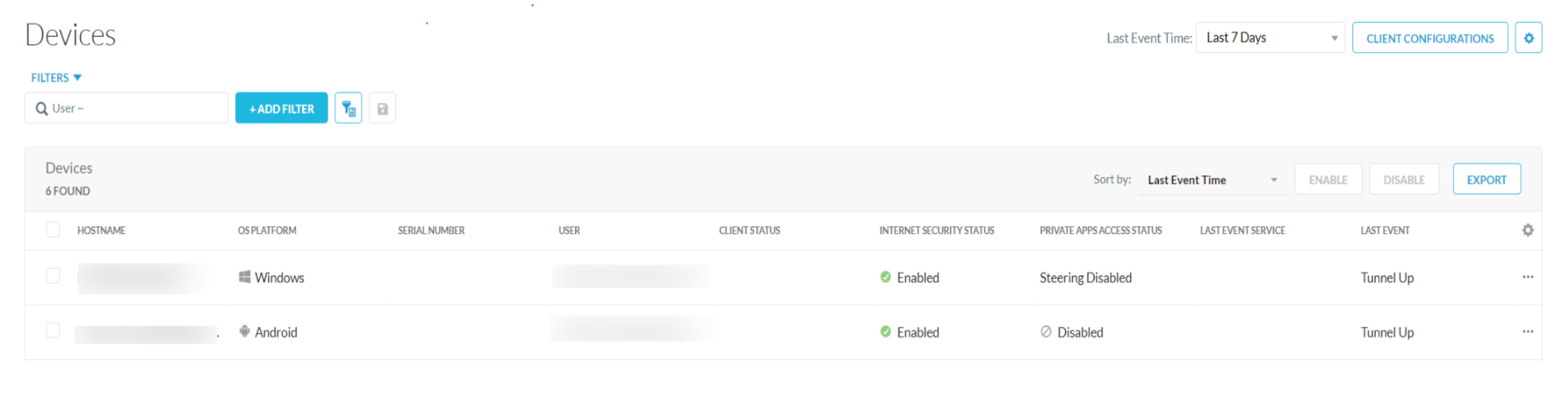
To display additional information such as Make, Model, Last Event Actor on the Devices webUI, click
 displayed on the devices list table and select options according to your requirement.
displayed on the devices list table and select options according to your requirement.If the device includes more than one user:
The Users column displays the total number of users.
The Internet Security Status, Private Apps Access Status columns displays Multiple Statuses and Last Event displays Multiple Events.
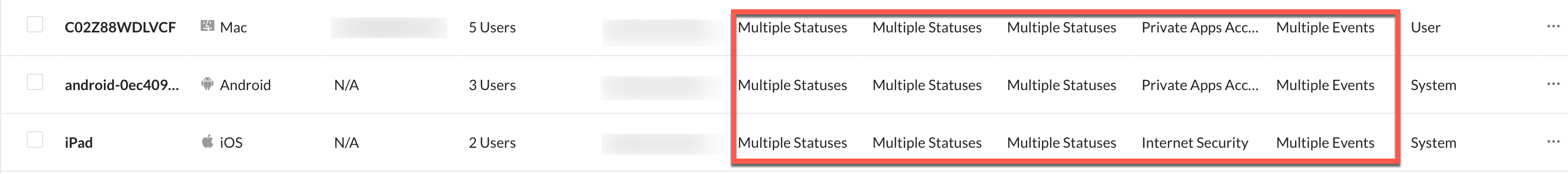
Click the hostname to select the user from the list of users added to that device.
Click the checkbox in the Hostname column to select all deployed devices. You can select only up to 10,000 devices at a time. If there are more than 10,000 devices, make your selection in batches.
Note
For iOS devices, the hostname, model, version, and check-in are not shown, and only devices that are installed using MDM managed devices with the VPN profile with the Email listed.
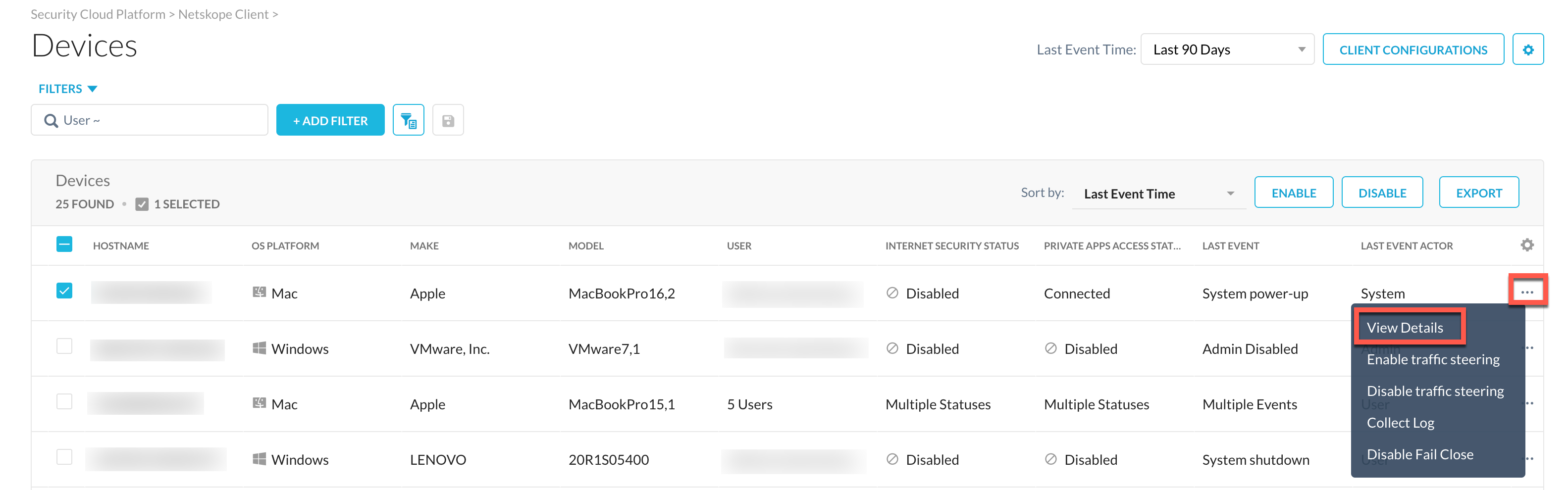
View Device Details
To view the details of an individual device, select the hostname or click the ellipsis(...) and select View Details to open the device details page.
 |
The device details page displays device, and client information. To view event history, group membership, or organization unit information, click the appropriate tab.
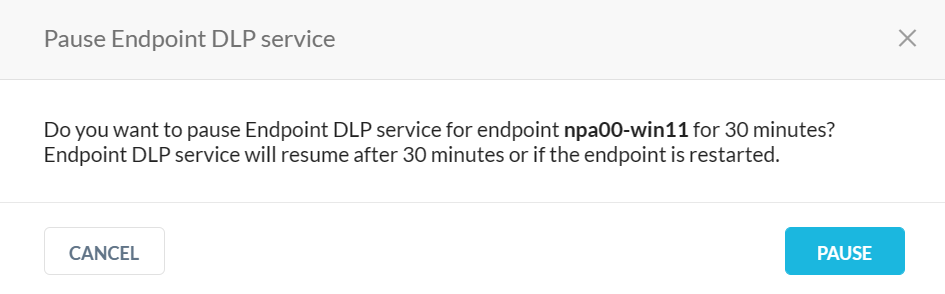
If Endpoint DLP is enabled, you can pause or resume the service from the detail view. The default pause time is 30 minutes.
Netskope Client creates Unique Device Identifier at the time of enrollment. Prior to the version 105.0.0, the Unique Device ID was created based on the hostname and few other parameters. As the hostname is no longer maintained unique in the organizations, with 105.0.0, Netskope Client is enhanced to use the hardware parameters such as Windows GUID for creating Unique Device ID.
Previously, whenever there were devices with the same hostname, it shared the same Unique Device ID. From version 105.0.0, different Unique Device IDs are assigned to each device and no two devices share the same ID. With the new Unique Device ID, whenever the administrator tries to query based on the Client Data, the value for nsdeviceuid.
Note
This feature will be enabled in a phased manner by Netskope that would take a couple of months. No action required by the user for this roll-out.
Manage Client
The admin can control the user access to enable or disable the Client. The admin can select one of the following options:
Enable Traffic Steering - The admin enables Client for the selected device and restricts the user from disabling the Client.
Disable Traffic Steering - The admin disables Client for the selected device and restricts the user from enabling the Client.
Export Device Information
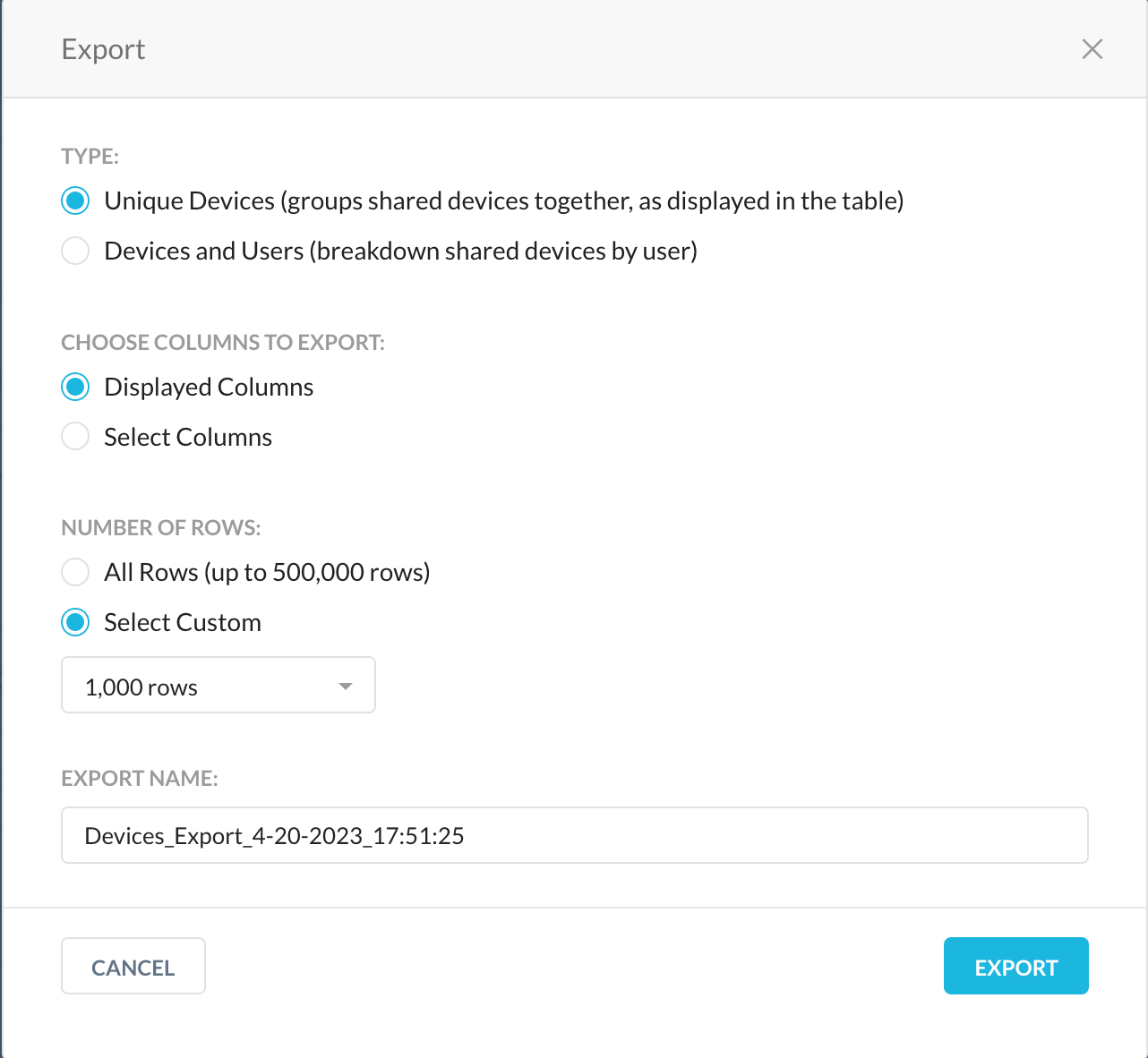
To export the contents in the Device UI to a CSV file, select the hostnames and click Export. The details displayed in the exported file depends on the options that you choose on the Export webUI. When there are multiple users added to a device and you choose Unique Devices in the Type field on the Export webUI, the CSV will only display the total number of users added to that device. To view each username added to a device, choose the option Devices and Users in the Type field.
 |
Client Status
The following table lists various client statuses according to Internet Security and Private Access Apps services and their meaning. You can also query client status via the Get Client Data REST API.
Internet Security Service Status
Event | Actor | Status | Meaning |
|---|---|---|---|
Installed | System | Disabled | Via email invitation, distribution tool (i.e. SCCM, Altiris, JAMF etc) |
Tunnel Up | System | Enabled | 'Auto' enabled just after install, upgrade or later |
Tunnel Down | System | Disabled | disabled - default startup state of client i.e. after installation/upgrade/restart |
Tunnel down due to secure forwarder | System | Disabled | 'Auto' disabled due to Netskope Secure Forwarder found |
Tunnel down due to GRE | System | Disabled | 'Auto' Disabled due to GRE |
Tunnel down due to IPSec | System | Disabled | 'Auto' Disabled due to IPSec |
Tunnel down due to Data Plane on-premises | System | Disabled | 'Auto' Disabled due to on-premises DP |
Tunnel down due to config error | System | Disabled | 'Auto' disabled due to config errors/missing config |
Tunnel down due to error in Modern Standby mode | System | Disabled | Auto' disabled due to device in modern standby mode (AOAC) |
Tunnel down due to error | System | Disabled | 'Auto' disabled due to (any other) error |
Change in network | System | Disabled | 'Auto' disabled due to change in network |
System shutdown | System | Disabled | 'Auto' disabled due to system restart/ power down |
System powerup | System | Disabled/Enabled | 'Auto' Tunnel status will be as per actual status |
Enrollment Token Error | System | Errored | Displayed when an invalid enrollment authentication token is used |
User Disabled | User | Disabled | User disabled the client from the system tray |
User Enabled | User | Enabled | User enabled the client from the system tray |
Admin Disabled | Admin | Disabled | Tenant admin disabled the client from the system tray |
Admin Enabled | Admin | Enabled | Tenant admin enabled the client from the webUI |
Uninstalled | System | Uninstalled | Uninstalled by end user, admin, SCCM admin etc |
Installation Failure | System | Disabled | Installation failed |
Uninstallation Failure | System | Disabled | Disabled Failed to uninstall the Client |
Upgrade Success | System | Disabled | Client upgraded successfully |
Upgrade Failure | System | Disabled | Client failed to upgrade |
Private Access Apps Status
Event | Actor | Status | Meaning |
|---|---|---|---|
Disabled | System | Disabled | NPA is not available for the customer. NPA status code is 0. |
Disabled | System | Disabled | NPA is available for the tenant but tunnel is not yet established. It should be transient state. NPA status code is 0. |
Disabled | System | Disabled | NPA is avaiable, but not enabled from the tenant UI. NPA status code is 0. |
Enabled | System | Enabled | NPA tunnel is connected. NPA status code is 2. |
Disabled | System | Disabled | User disables the NPA Client. NPA status code is 0. |
Disabled | System | Disabled | Admin disables the NPA Client from the tenant UI. NPA status code is 0. |
Errored | System | Disabled | NPA tunnel is disconnected due to error. NPA status code is 11. |