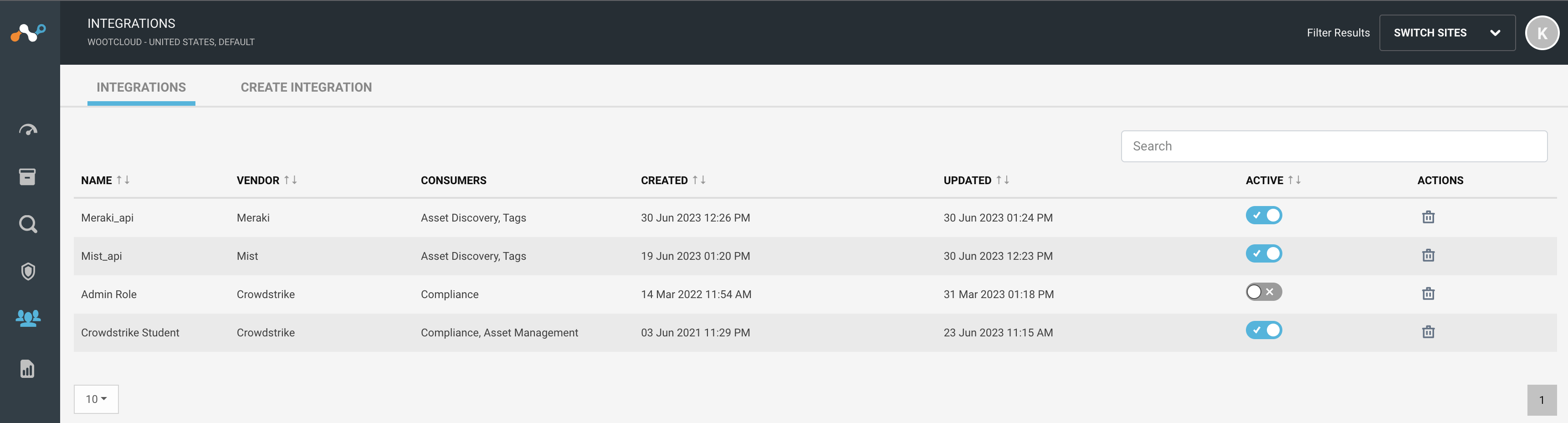
Integrations
Netskope supports third party integration through Netskope IoT Security UI.
 |
Integrate CrowdStrike with Netskope IoT Security
Follow the procedure to integrate CrowdStrike:
Navigate to the Manage > Integrations menu. Select Create Integration tab. You will see a Create New Integration window.
Set active or inactive state of the integration on creation.
Give a unique name to the integration.
Select the type as CrowdStrike from the dropdown list.
Provide the CrowdStrike Client ID and Client Secret key for CrowdStrike.
Provide CrowdStrike base URL.
The default consumer is compliance to calculate the compliance of the devices. Optionally you can use CrowdStrike for Asset Management.
Click the Create Integration button.
Note
Click the Cancel button to forbid the action.
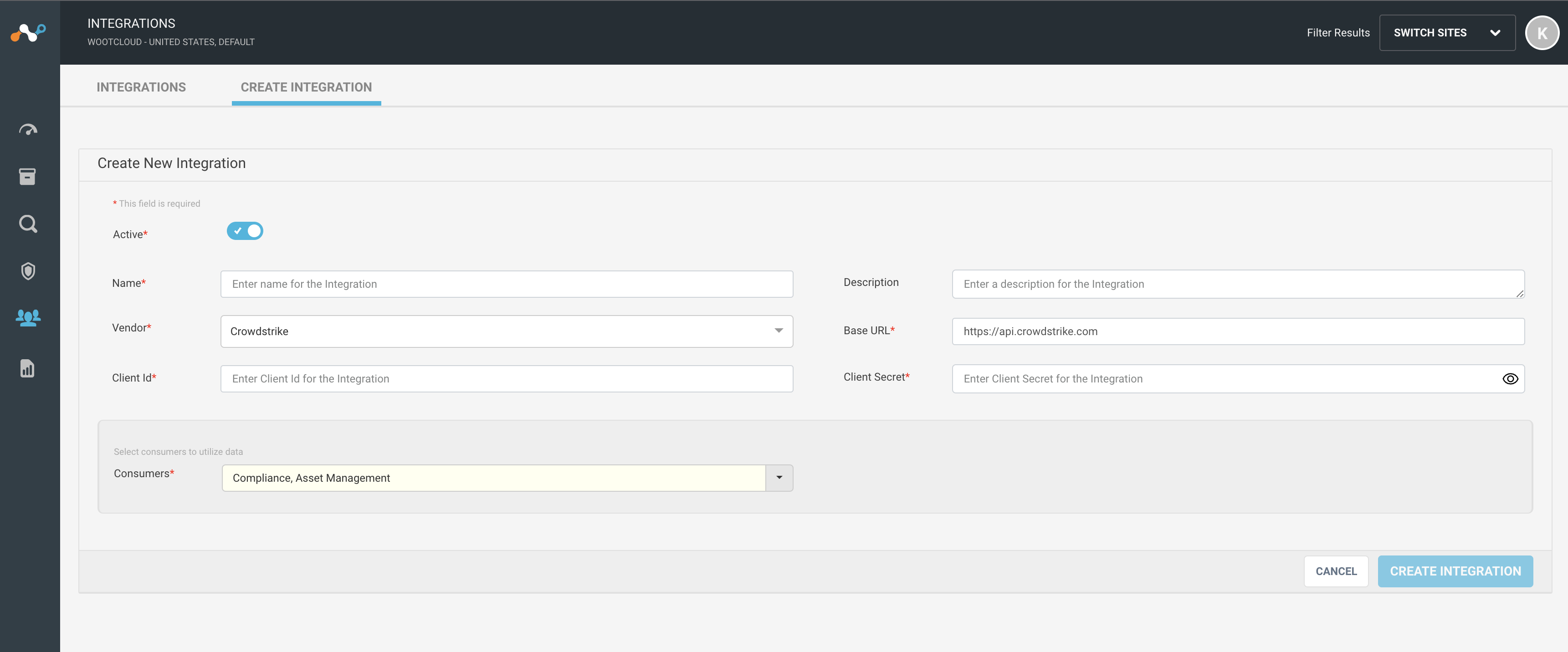
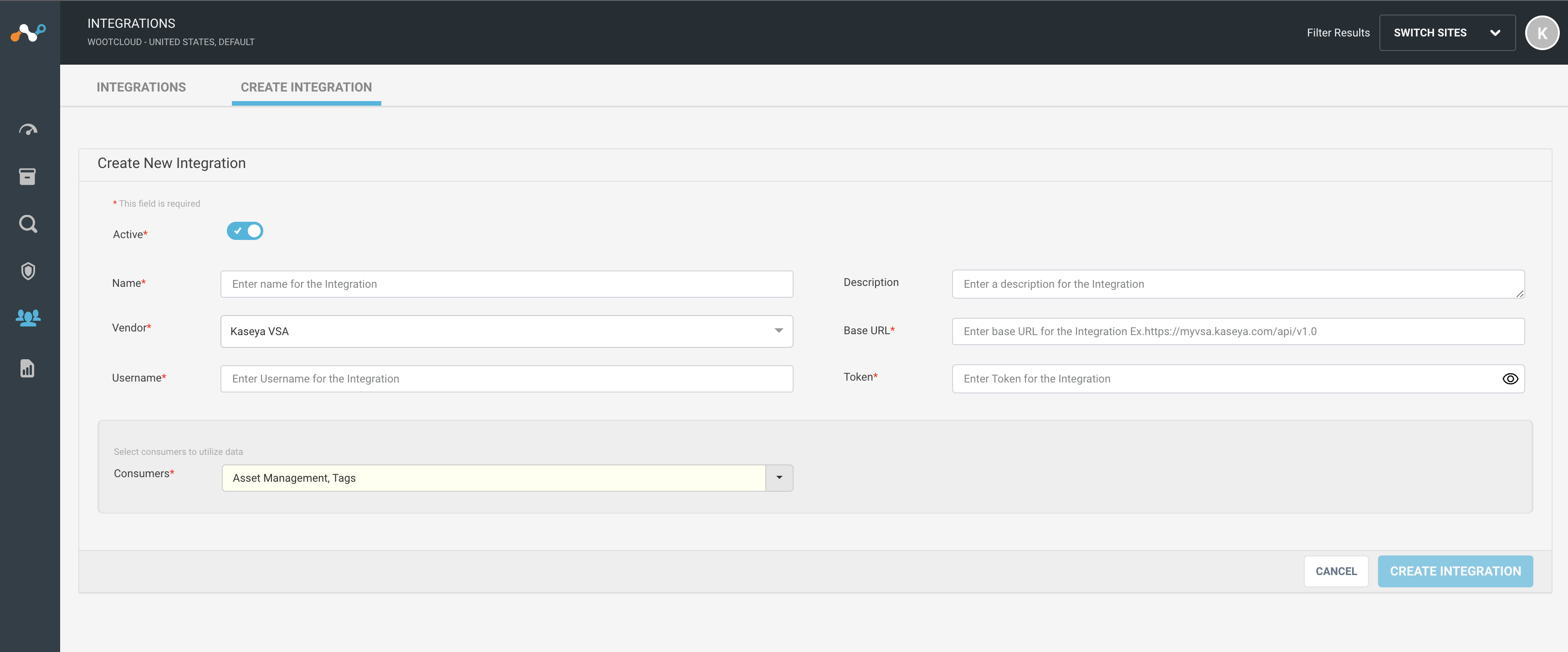
Integrate Kaseya VSA with Netskope IoT Security
Follow the procedure to integrate Kaseya VSA:
Navigate to the Manage > Integrations menu. Select Create Integration tab. You will see a Create New Integration window.
Set active or inactive state of the integration on creation.
Give a unique name to the integration.
Select the vendor as Kaseya VSA from the dropdown list.
Provide Kaseya VSA Username and Token to connect from Netskope IoT Security.
Provide Kaseya VSA base URL.
The default consumer is Asset Management to pull assets from Kaseya VSA to Netskope IoT Security. Optionally you can use Kaseya VSA for Tag consumption.
Click the Create Integration button.
 |
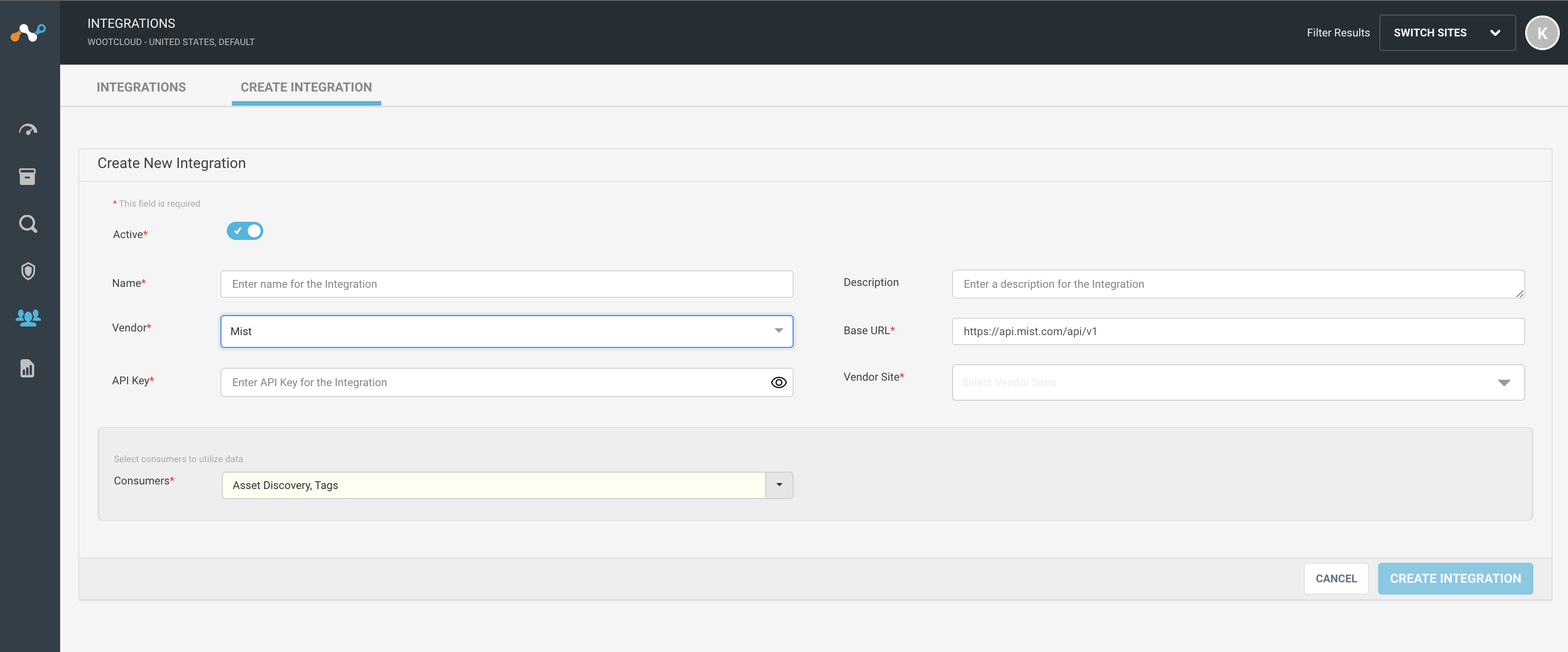
Integrate Mist with Netskope IoT Security
Follow the procedure to integrate Mist:
Navigate to the Manage > Integrations menu. Select Create Integration tab. You will see a Create New Integration window.
Set active or inactive state of the integration on creation.
Give a unique name to the integration.
Select the vendor as Mist from the dropdown list.
Provide Mist API Key to connect from Netskope IoT Security.
Provide Mist base URL.
On correct API Key validation, the Netskope IoT Security will fetch the vendor sites.
The default consumer is Asset Discovery to discover devices from Mist to Netskope IoT Security. Optionally you can use Mist for Tag consumption.
Click the Create Integration button.
 |
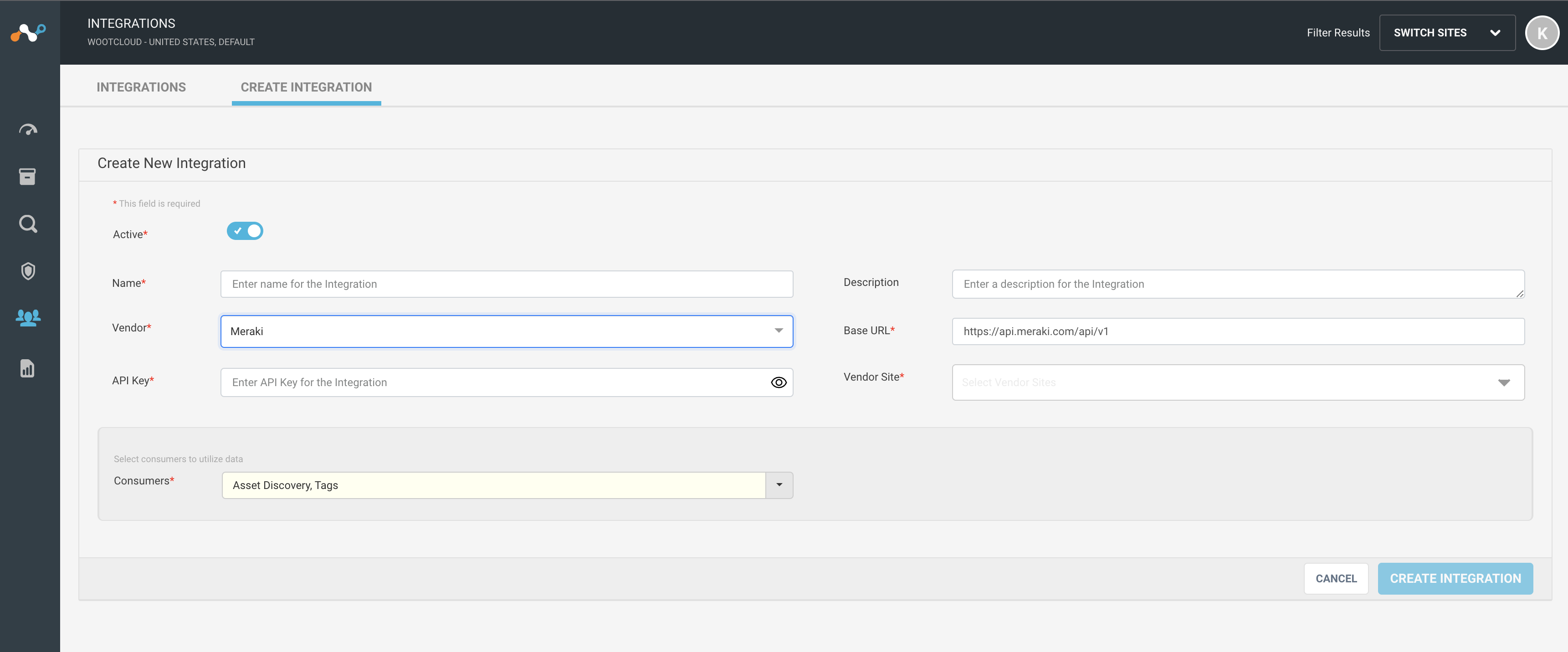
Integrate Meraki with Netskope IoT Security
Follow the procedure to integrate Meraki:
Navigate to the Manage > Integrations menu. Select Create Integration tab. You will see a Create New Integration window.
Set active or inactive state of the integration on creation.
Give a unique name to the integration.
Select the vendor as Meraki from the dropdown list.
Provide Meraki API Key to connect from Netskope IoT Security.
Provide Meraki base URL.
On correct API Key validation, the Netskope IoT Security will fetch the vendor sites.
The default consumer is Asset Discovery to discover devices from Meraki to Netskope IoT Security. Optionally you can use Meraki for Tag consumption.
Click the Create Integration button.
 |
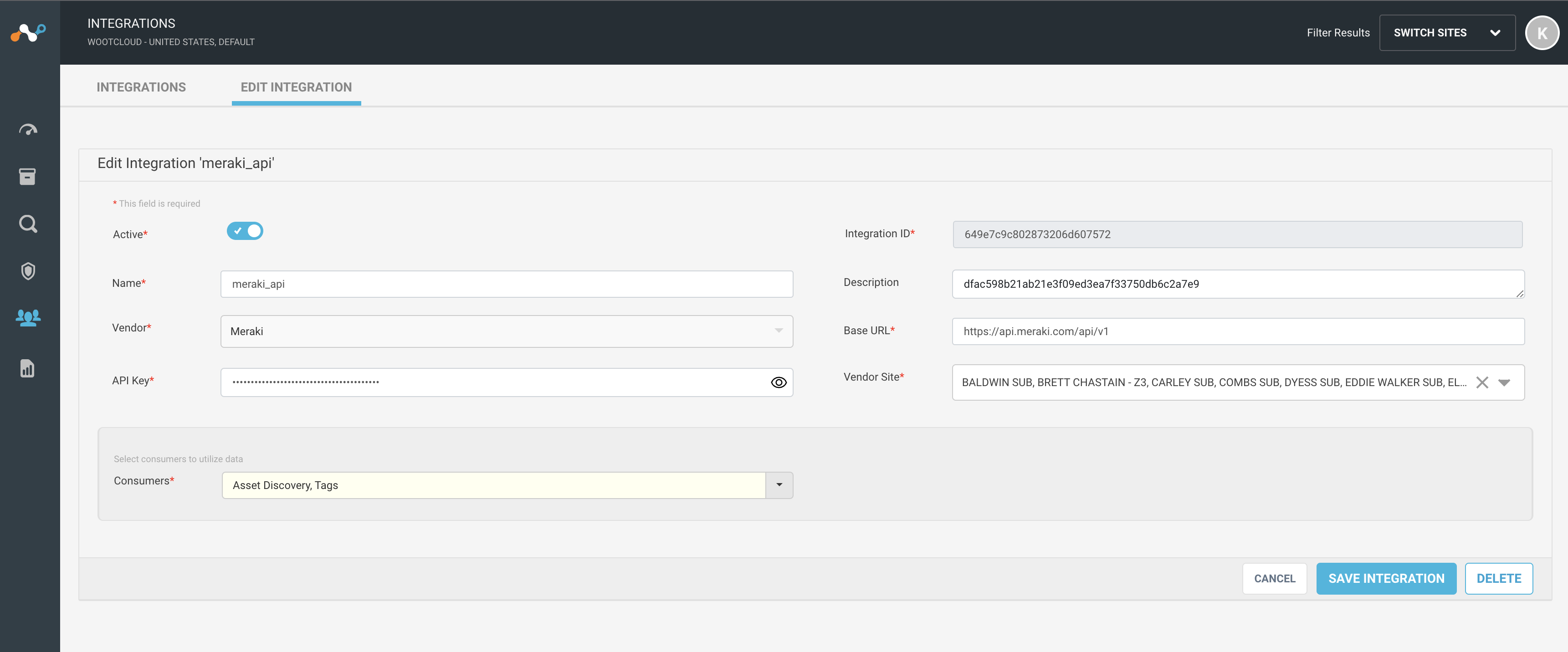
Edit Existing Integration Configuration
You can edit, enable, disable and delete the existing integrations. Follow the procedure to edit the integration:
Navigate to the Manage > Integrations menu.
Select an integration from the list. You will see an Edit Integration <name> window.
You can activate or deactivate the integration configuration.
You can edit the integration name, base URL and consumer fields.
You can update the credentials, base URL, API key, and vendor sites for Mist and Meraki .
You can update the consumers.
Click the Save Integrations” button.
Note
Click the Cancel button to forbid the action. Click the Delete button to delete the selected integration. You can not delete the integration when it is connected to the integration based compliance configuration.