Compromised Credentials
Most users never change their passwords and use the same password in several applications. When unsanctioned apps are hacked, the compromised accounts in these apps can expose accounts in your sanctioned apps. The Netskope Compromised Credentials dashboard informs you about known compromised credentials for the accounts used by your employees.
You can use the Compromised Credentials page to build awareness around the number of compromised credentials in your company. If you have risk officers, they can use this information to assess the need for SSO and 2-factor authentication in sanctioned cloud apps. Using this feature as input, it is possible to setup a workflow to automate remediation actions such as resetting a user’s AD account. Passwords are never checked. To access the Compromised Credentials page, go to Incidents > Compromised Credentials.
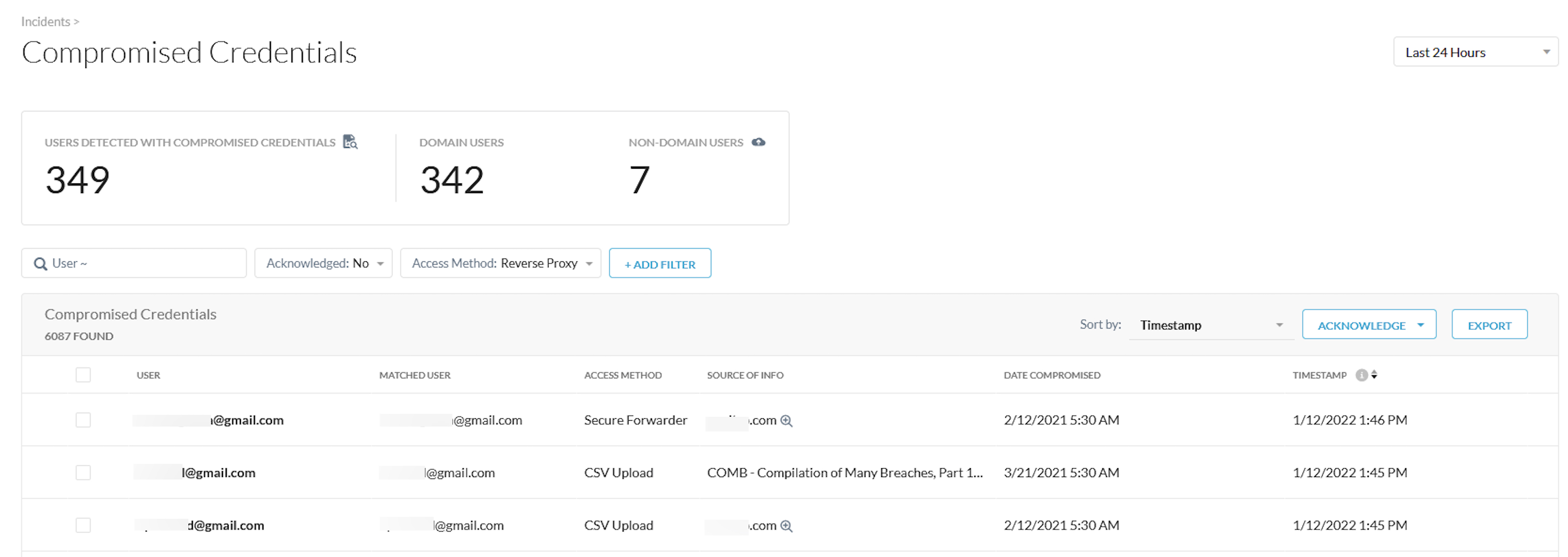
Use the Compromised Credentials page to view:
Total number of users with compromised credentials. Click the link here to view and edit the domains tracked. This number is the total of domain users + non-domain users.
Total number of domain users.
Total number of non-domain users. Click the link here to upload a file with user names.
User - Compromised user's email address associated with the Netskope account.
Matched User - email address associated with the breached access method.
A Matched User email may differ from a User email address. For example, smith@netskope.com is the User email associated with Netskope account. But smith@netskope.com is the same person as smith@gmail.com or smith@hotmail.com, the Matched User email associated with the breach.
Access Method - the named user used one of these access methods: Explicit Proxy, Secure Forwarder, Mobile Profile, Client, Reverse Proxy, DPOP inline, TAP, AD Importer, CSV Upload, API Connector, and Log when the breach was detected.
Source of info.
Date compromised.
Timestamp when the breach was detected.
You can customize the information shown by clicking +Add Filter and selecting specific types of information, plus switch between all acknowledged compromised credentials or just the unacknowledged ones.
Click on a user's email address to go to the Skope IT page for more details. To export the Compromised Credentials page information to a spreadsheet, click Export and choose the desired options. To remove one or more of the compromised credentials, enable the checkbox next to an item and click Acknowledge, or click Acknowledge All.