Steering Configuration
A steering configuration controls what kind of traffic gets steered to Netskope for real-time deep analysis and what kind of traffic gets bypassed. It's for endpoints using the Netskope Client and directs traffic from end users to the Netskope Cloud. A Netskope account steers thousands of apps by default, but to ensure the correct type of traffic is steered, you can modify the default steering configuration or create a new steering configuration. You can assign these configurations to either user groups or Organizational Units (OUs) for granular steering within your organization. Steering configurations apply to all platforms, but OU and Group settings are applied to the Netskope Client only.
Caution
For Netskope Client version 87.0.0, Netskope enhanced the steering configuration download limit to 1 MB. If you are running a Netskope Client version older than 87.0.0, you will see a configuration update failure if you have added a large number of cloud apps to the steering configuration. To avoid configuration download or update issues, Netskope recommends you upgrade your Netskope Client to the latest release. To learn more about Netskope Client: Netskope Client Overview.
The Netskope Client offers comprehensive coverage when installed on managed devices and provides visibility and policy enforcement for devices that are both on- and off-premises (remote). The Netskope Client:
Performs posture checks to classify devices as managed or unmanaged based on admin-defined configurations.
Detects if a user is on-premises or remote and applies different steering configurations based on the location.
Provisions certificates to help with user identification when used with other traffic steering methods, such as GRE or IPSec.
Detects the presence of other traffic steering methods.
Generates user-facing notifications for security policy violations.
General Guidelines
When creating or editing steering configurations, consider the following:
When creating a custom steering configuration, you can enable Dynamic Steering, and the default exceptions are populated in both on- and off-premise steering configurations.
When editing the default steering configuration (i.e., Default tenant config), there is no restore defaults functionality, so you must create or remove exceptions in on- or off-premises mode based on where you left off before enabling Dynamic Steering.
If you're editing a configuration that steers All Traffic, note the following:
When you enable Dynamic Steering, the off-premises configuration, which steers All Traffic by default, inherits the exceptions.
When you enable Dynamic Steering, the on-premises configuration, which steers Cloud Apps Only by default, doesn't inherit the exceptions. Netskope assumes you create exceptions differently when a user is on-premises.
When you disable Dynamic Steering, Netskope preserves the steering configuration based on the traffic type.
If you're editing a configuration that steers Cloud Apps Only, note the following:
When you enable Dynamic Steering, the on-premises configuration, which steers Cloud Apps Only by default, inherits the exceptions.
When you enable Dynamic Steering, the off-premises configuration, which is All Traffic by default, doesn't inherit the exceptions. Netskope assumes you create exceptions differently when a user is off-premises.
When you disable Dynamic Steering, Netskope preserves the steering configuration based on the traffic type.
About the Steering Configuration Page
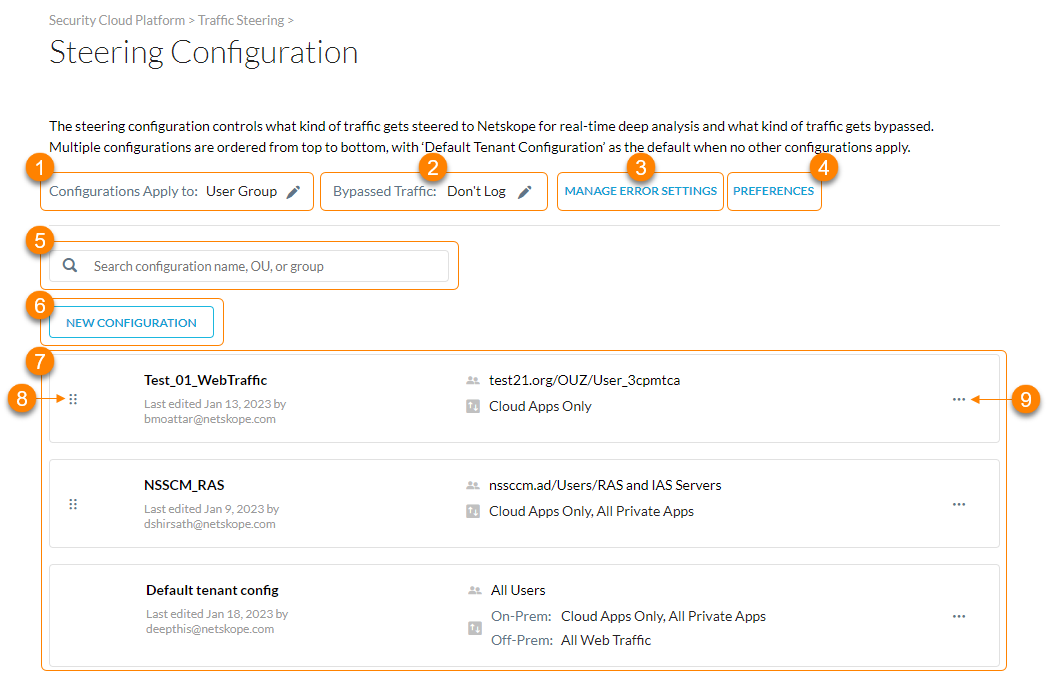
On the Steering Configuration page (Settings > Security Cloud Platform > Steering Configuration), you can:
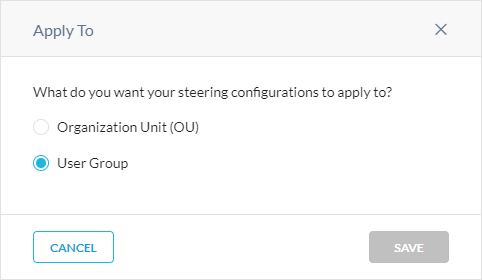
Choose whether all traffic steering configurations must apply to Organizational Units (OUs) or user groups. When configuring OUs and user groups, consider the following:
If a user is a member of multiple groups, the order placement of User Group steering configurations determines what's used to resolve conflicts. The first group determines which group steering configuration Netskope uses when there is a group conflict. Conflict resolution is only applicable to User Groups.
In a multi-user deployment mode, if the logged in users belongs to different OUs or user groups, the Netskope Client applies the steering configuration corresponding to the user most recently logged. Ensure all the users belong to a single OU or User Group for a multi-user machine.
For users in OUs or user groups that aren't included in a custom steering configuration, Netskope applies the default steering configuration (i.e., Default tenant config). If you want to steer different types of traffic for different OUs or User Groups, create multiple custom steering configurations.
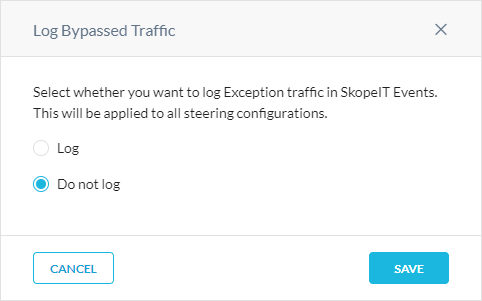
Choose whether you want to log bypassed traffic (i.e., steering exceptions) in Skope IT Events. This setting applies to all steering configurations.
Note
If you enabled dynamic steering and Netskope detects that the user is off-premises, Netskope client bypasses the traffic and doesn't log it.
Manage how certain errors that Netskope observes in HTTP/HTTPS traffic are handled by blocking or bypassing them. To learn more: Managing Error Settings.
Choose the action taken when Netskope adds new predefined certificate pinned apps or updates to existing ones. To learn more: Configuring the Steering Preferences.
Search the steering configurations by a name, OU, or user group.
View a list of steering configurations. For each configuration, you can see the OU or user group and the steering settings.
Click
 to move the steering configuration. The steering configuration placed at the top takes priority over all other configurations.
to move the steering configuration. The steering configuration placed at the top takes priority over all other configurations.Click
 to choose one of the following options:
to choose one of the following options:View Steered Items: Click to go to the Steered Traffic tab where you can add applications and steer their traffic to Netskope for deep analysis via Real-time Protection policies. To learn more: Adding Steered Items.
View Exceptions: Click to go to the Exceptions tab where you can add exceptions for the steering configuration and bypass the traffic from Netskope.
Edit Configuration: Modify the steering configuration and its settings. To learn more: Creating a Steering Configuration.
Clone: Create a copy of the steering configuration.
Disable/Enable: Enable or disable the steering configuration. You can't disable the Default tenant config.
Delete: Delete the steering configuration. You can't delete the Default tenant config.