Reverse Proxy for ServiceNow with Azure AD SSO
If you don't already have a ServiceNow instance, create one following the instructions here to integrate it with Azure AD.
For testing purposes, you can create a developer account and request an instance here.
Important
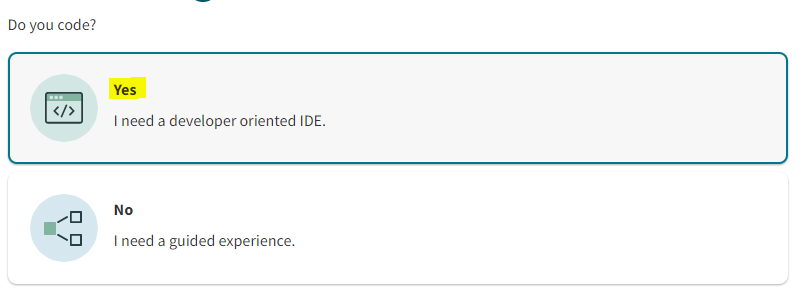
When creating the instance, select Yes for IDE.
 |
Configure SSO
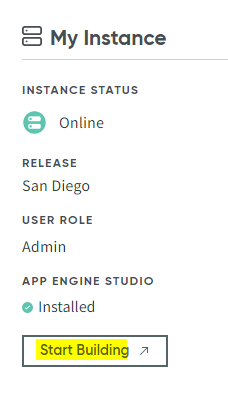
After your instance has been created, you can access the ServiceNow UI by clicking Start Building.
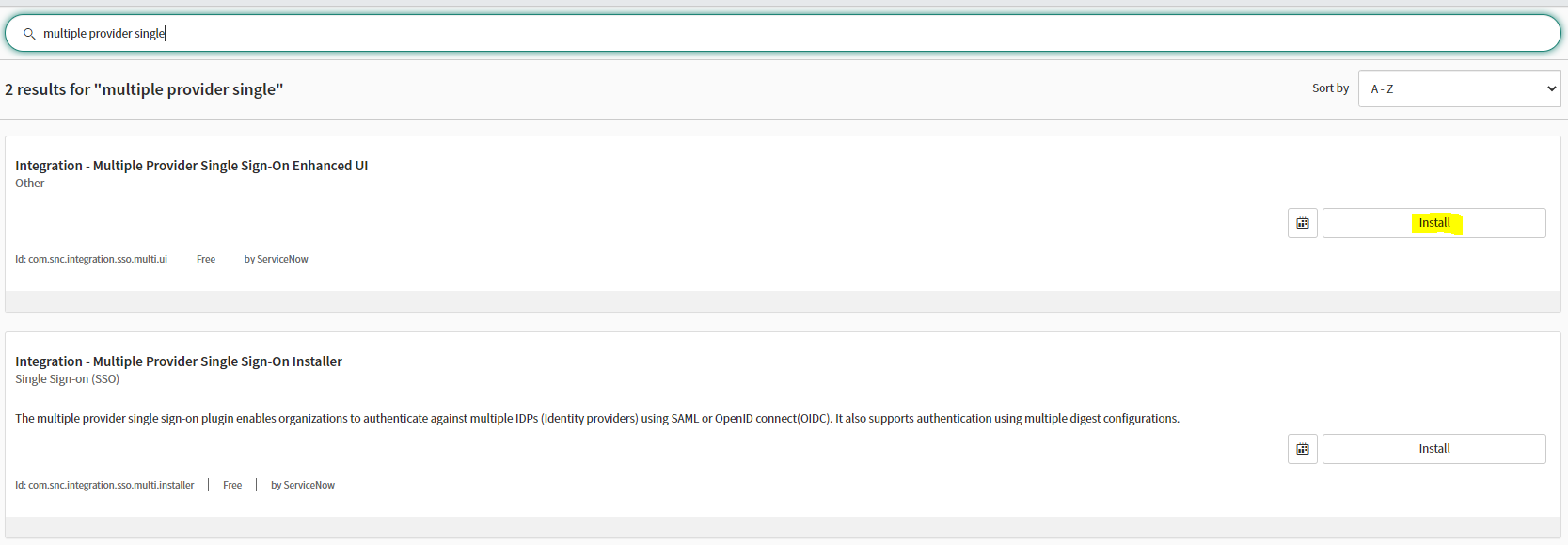
Go to All > System Definition, click Plugins, and search for Multiple Provider Single Sign-On Enhanced UI.
After you press install, click Activate.
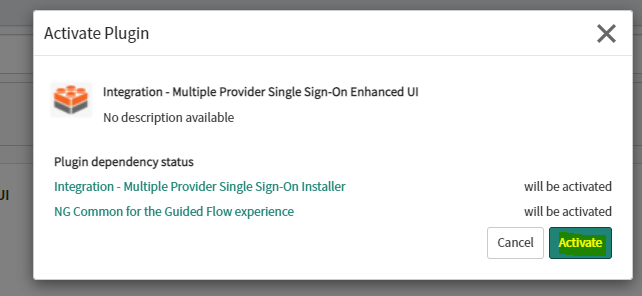
Note
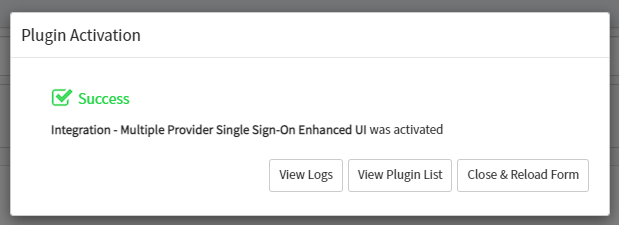
Wait for the plugin to be installed. This may take a few minutes.
Click Close & Reload Form.
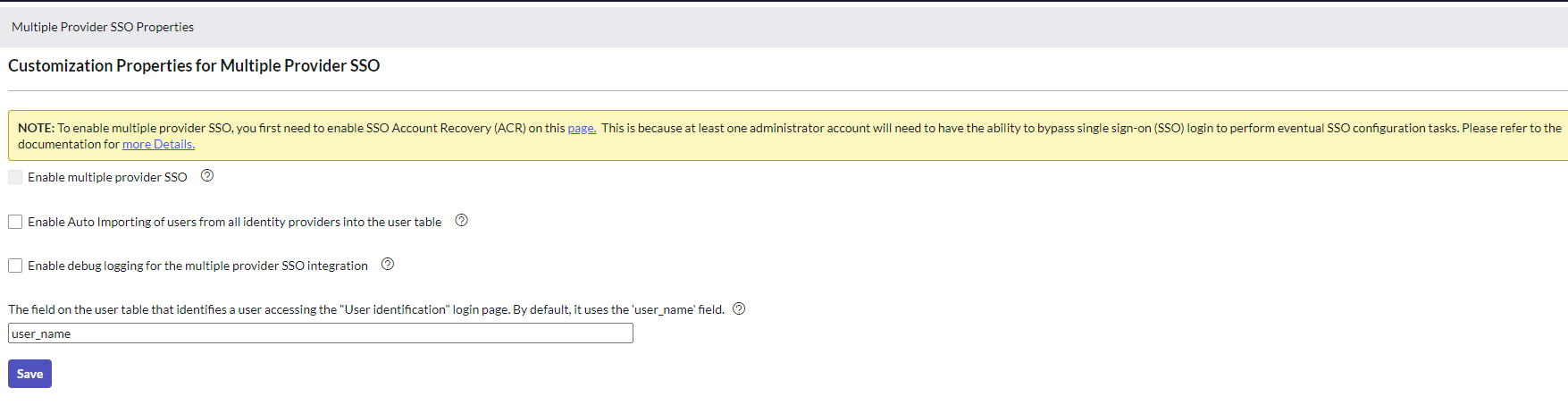
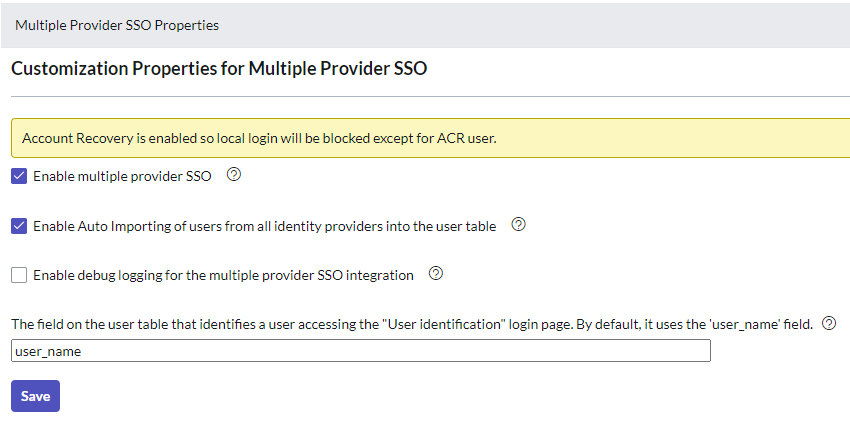
Go to All > Multiple-Provider SSO > Administrator and click Properties, and then enable ACR.
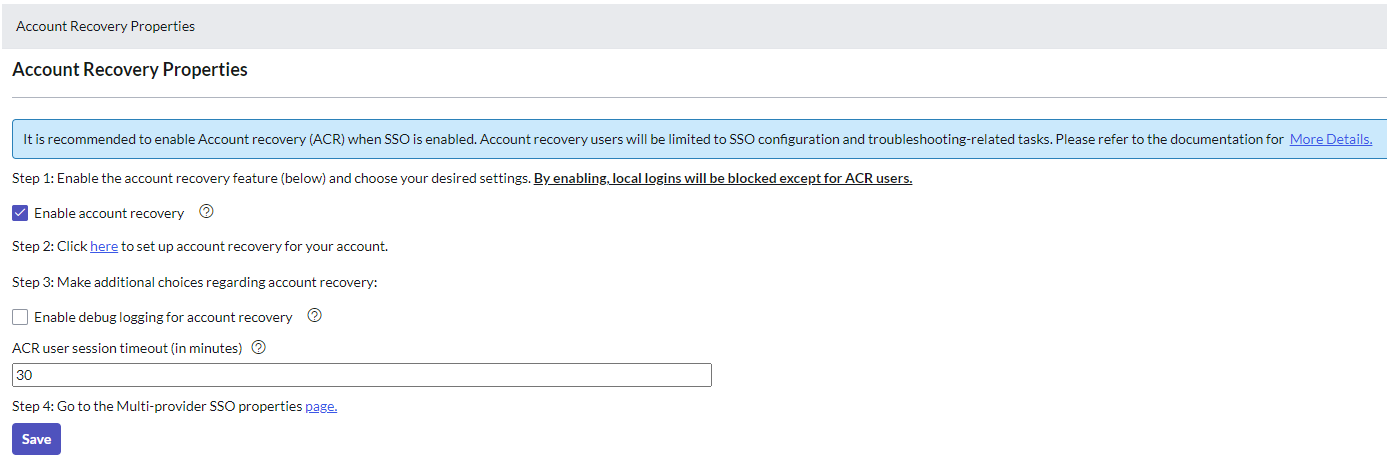
Set up Multi-factor Authentication’ in Step 2, click Save, and then go back to Properties by pressing the link in Step 4.
Select ‘Enable multiple provider SSO’ & ‘Enable Auto importing of users from all identity providers into the user table’ then press ‘Save’
Note
After enabling SSO, you can disable ACR. Otherwise, you will be logged by AR user when the session expires.
Log in to Azure AD, go to All Applications > New Application, search for ServiceNow, and then create the new app.

Once the application is created, go to Single Sign-On, select SAML, and add your instance information.
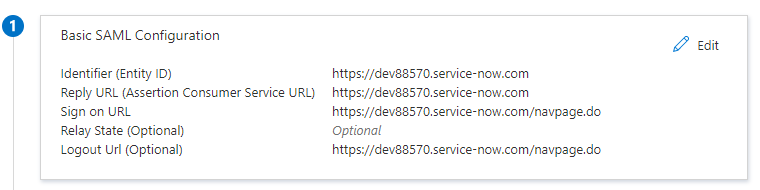
Click View step-by-step instructions in Step 4.
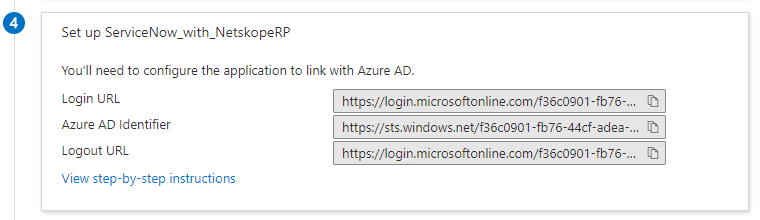
Add your Admin credentials and click Configure Now.
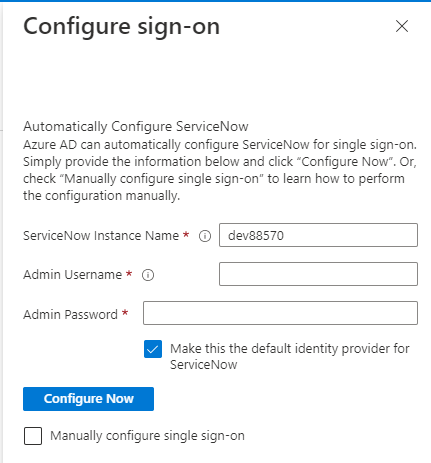
If successful, this will create an SSO entry for Azure in ServiceNow that can be seenon All > Multi-Provider SSO > Providers.

If not, follow the manual configuration steps (in Step 5).
Important
The above SSO with Azure must be successful before continuing with Netskope configuration.
Configure Netskope Reverse Proxy ServiceNow
Go to Settings > Security Cloud Platform > Reverse Proxy SAML and click Add Account, and enter your ACS URL (instance information), IdP SSO (URL Azure), and Azure Certificate
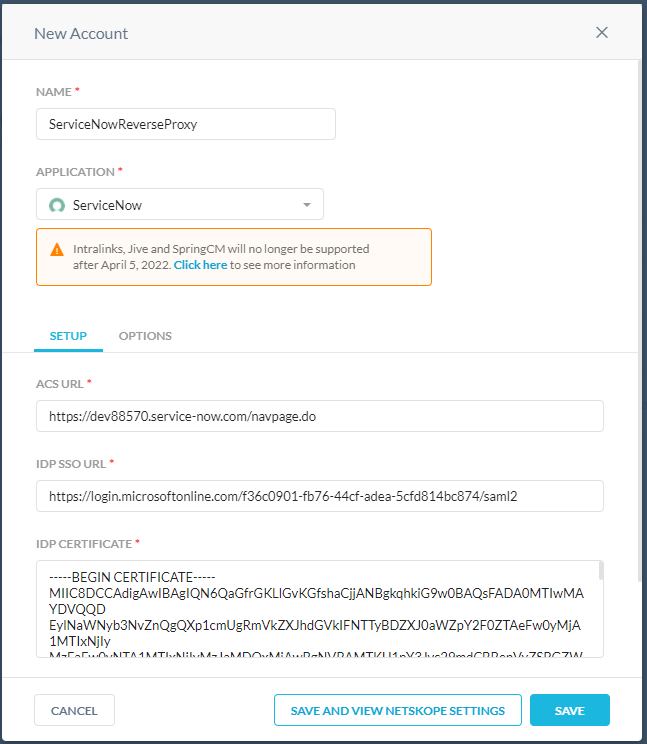
Note
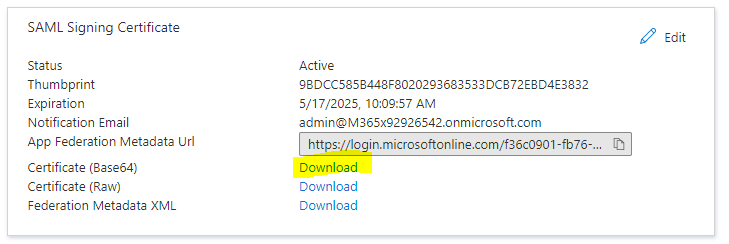
Your Azure certificate can be found here:
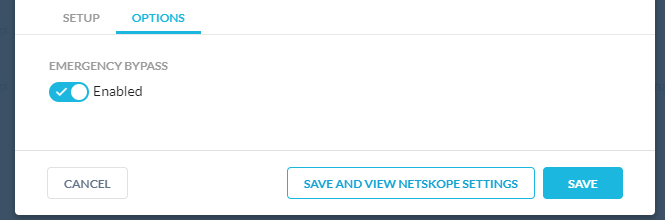
Enable Emergency Bypass while testing the connection.
Click Netskope Settings from your new SAML – Reverse Proxy,
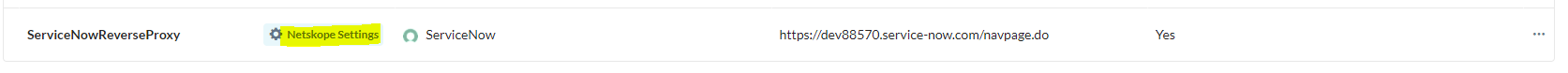
Copy all the information in order to enter it in your ServiceNow instance.
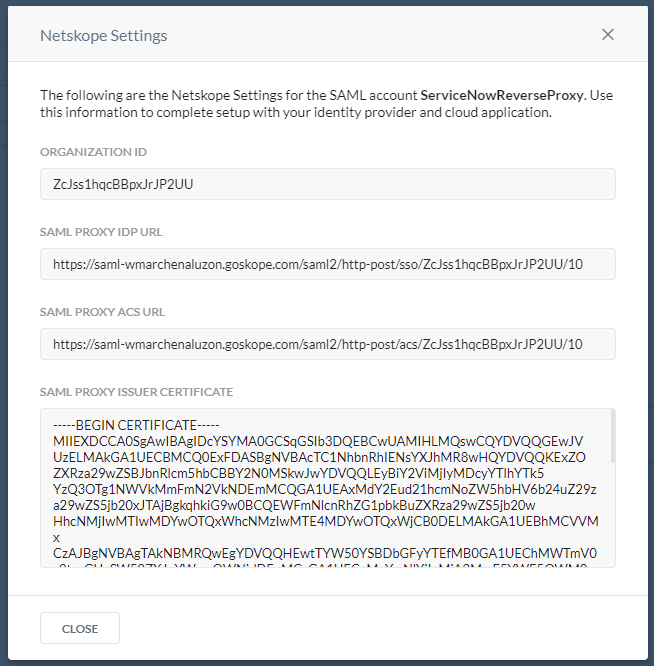
The Organization ID is used for your ServiceNow Identity Provider URL.
The SAML Proxy IDP URL is used for your ServiceNow Identity Provider's AuthnRequest.
The SAML Proxy ACS URL is used for your Azure AD Reply URL (Assertion Consumer Service URL).
The SAML Proxy Issuer Certificate is used for your ServiceNow X.509 Certificate.
Go to the X.509 Certificates section in ServiceNow and click New.

Copy the full content of SAML Proxy Issuer Certificate from step 4, paste it in PEM Certificate, and then click Submit.
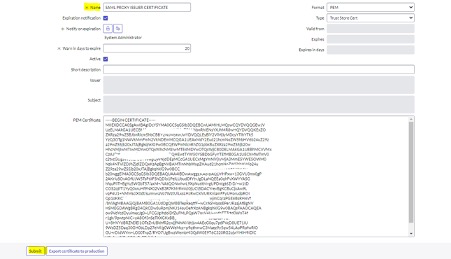
The new certificate should appear on the X.509 Certificates page.

Your settings should look like this:
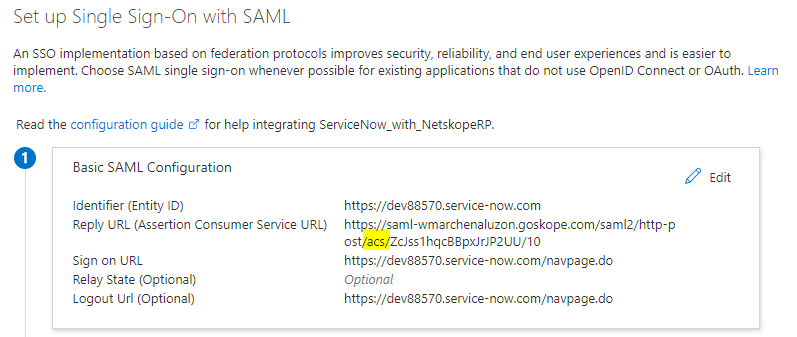
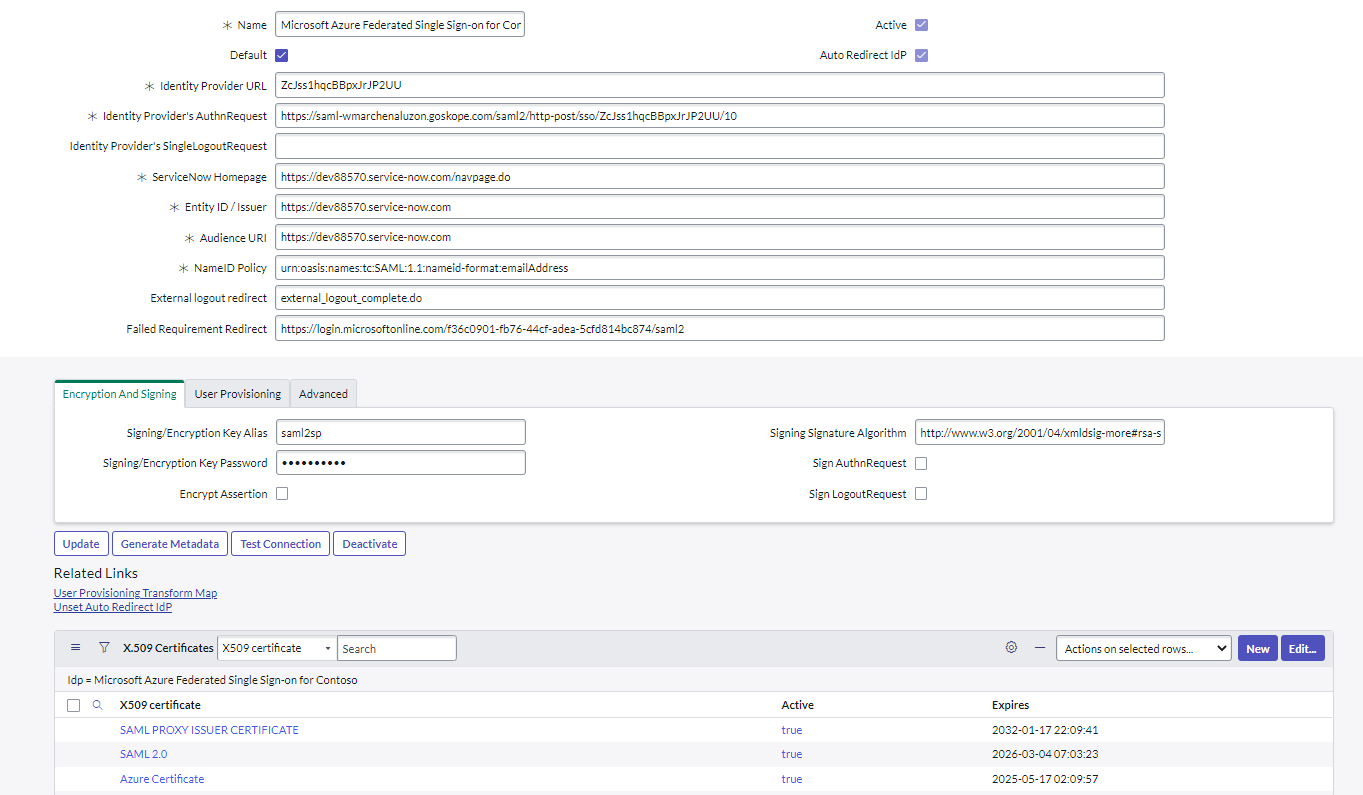
Test the connection. Save the new configuration by clicking Active.
Disable the emergency bypass option in the Netskope UI.
Go to the log in page, authenticate with Azure, and the URL should show the Netskope reverse proxy.