About Malicious Sites
Netskope can detect malicious sites both inline and with Risk Insights. You can view detected sites on the Malicious Sites page. The Malicious Site detection engine:
Leverages the Netskope Threat Research Labs, with a dedicated team focused on new cloud threats.
Includes threat intelligence curated from 40+ external feeds.
Detects communications with malicious URLs, IP addresses, and command-and-control (C&C or C2) servers.
Provides global and collective protection against new cloud threats, and stays up to date on the latest cloud threats.
Malicious Site Categories & Security Risks
Netskope Threat Intelligence categorizes malicious sites by security risks. These include sites that are pervasive and can pose a direct threat to business availability. A risk management site is essential for managing vulnerabilities and other risks.
Following are the different security risks for malicious sites:
Security Risk | Description |
|---|---|
Ad Fraud | Sites that are being used to commit fraudulent online display advertising transactions using different ad impression boosting techniques, including but not limited to ads stacking, iframe stuffing, and hidden ads. Sites that have high non-human web traffic and with rapid, large, and unexplained changes in traffic. Web analysts should not use this category. |
Attack | Sites that attempt to gain unauthorized access to information resources or services or cause harm or damage to information systems. |
Botnets | Sites or compromised web servers running software that is used by hackers to send spam, phishing attacks, and denial of service attacks. |
Command and Control Server | Internet servers and compromised command and control (C2 or C&C) servers and centers used to send commands to infected machines called bots. And sites that are a security risk because call-home malware is detected. |
Compromised/Malicious Sites | Sites that appear to be legitimate, but house malicious code or link to malicious websites hosting malware. These sites have been compromised by someone other than the site owner. If Firefox blocks a site as malicious, use this category. Examples are defaced, hacked by, etc. |
Cryptocurrency Mining | Sites that use cryptocurrency mining technology without user permission. This is considered a malicious category. |
DGA | Domains that are generated algorithmically using a domain generation algorithm (DGA). These domains are used by DGA-based malware as their C2 channel, and they aim to hide the location of the active C2 server. |
Hacking | Sites with information or tools specifically intended to assist in online crime, such as the unauthorized access to computers, but also pages with tools and information that enables fraud and other online crime. |
Malware Distribution Point | Sites that host viruses, exploits, and other malware are considered Malware Distribution Points. Web analysts might use this category if their antivirus program triggers on a particular website. Other categories should also be added if applicable. |
Miscellaneous | Sites with security risk indicators that aren't mapped to any of the other listed security risk types (e.g., high risk, medium risk, and possible risk). |
Phishing/Fraud | Sites that impersonate other web pages, usually with the intent of stealing passwords, credit card numbers, or other information. Also includes websites that are part of scams such as a 419 scam where a person is convinced to hand over money with the expectation of a big payback that never comes (e.g., con, hoax, scam, etc.). |
Spam | URLs that frequently occur in spam messages. Web analysts shouldn't use this. |
Spyware & Questionable Software | Software that reports information back to a central server such as spyware or keystroke loggers. It also includes software that may have legitimate purposes, but some people may object to having on their system. Web analysts shouldn't use this category. |
Viewing Malicious Sites
To view malicious sites visited by internal hosts in your organization, go to Incidents > Malicious Sites.
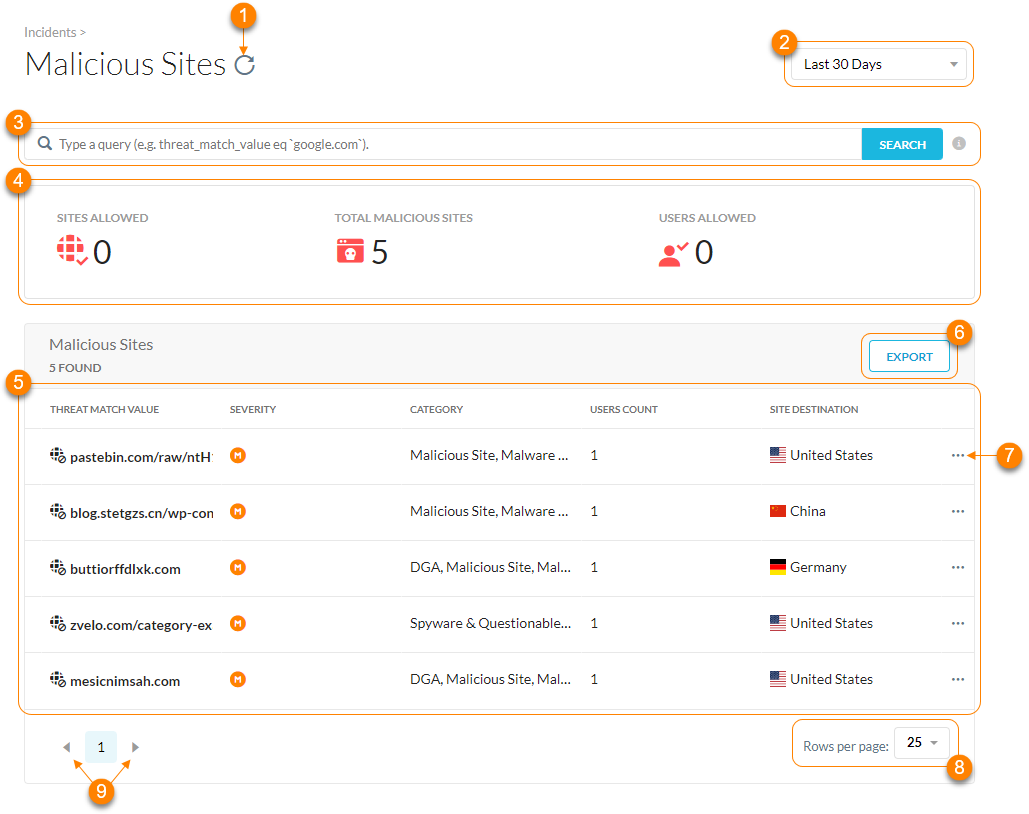
On the Malicious Sites page, you can:
Refresh the malicious site results.
Filter malicious site incidents by a specific time frame. You can use a predefined time frame or choose Date Range to use the calendar and time menus to customize your own.
Search and filter the malicious sites by a query.
View the primary metrics of the malicious sites:
Sites Allowed: The total number of malicious sites users were allowed to visited.
Total Malicious Sites: The total number of malicious sites users visited.
Users Allowed: The total number of users allowed to visit a malicious site.
View a list of malicious sites. For each site, you can see the following information:
Threat Match Value: The domain name or URL associated with the malicious site.
Severity: The severity level Netskope assigned to the malicious site. The severity categories are:
Critical
High
Medium
Low
Category: The malicious category and security risk of the malicious site.
Users Count: The number of users affected by the malicious site.
Site Destination: The country of the malicious site.
Export malicious sites (up to 500,000 rows) to a CSV file.
Click
 then View Alerts to go to Skope IT Alerts and see all the alerts associated with the URL/domain name of the malicious site.
then View Alerts to go to Skope IT Alerts and see all the alerts associated with the URL/domain name of the malicious site.View up to 300 malicious sites per page.
View multiple pages of the table.
Viewing Malicious Site Details
On the Malicious Sites page, you can click the Threat Match Value to see more comprehensive details.
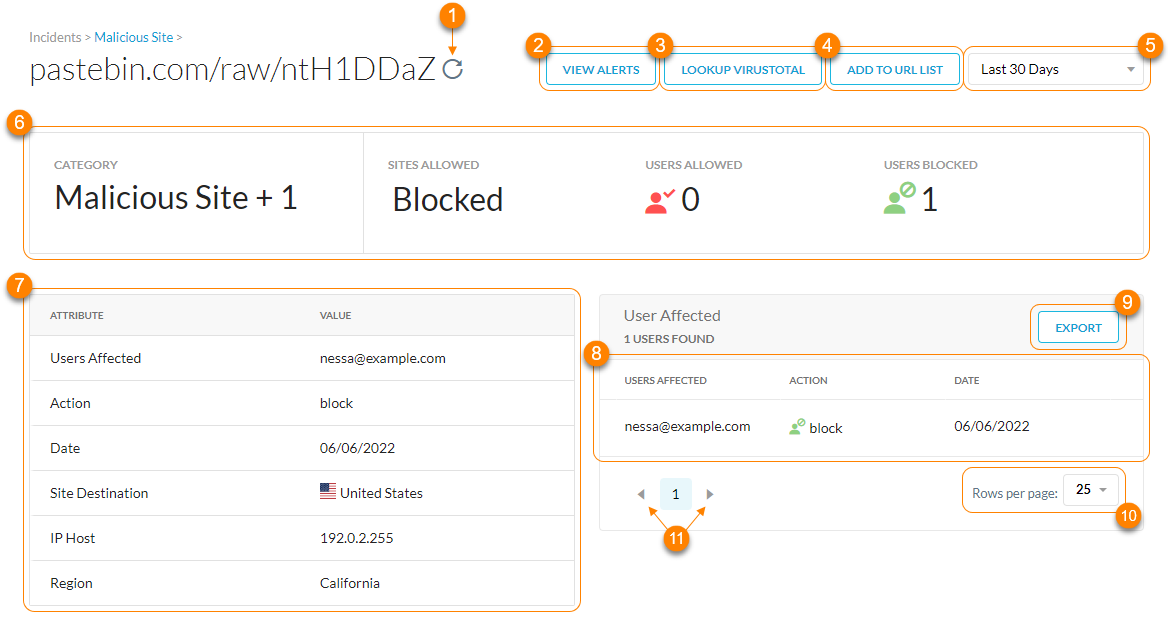
On the Malicious Site Details page, you can:
Refresh the malicious site details.
Go to Skope IT Alerts and see all the alerts associated with the URL/domain name of the malicious site.
Look up more malware information on VirusTotal, a third-party aggregator of malware information. VirusTotal is a complementary source of information and might not have details on all malware especially in documents that are private to your organization.
Add the malicious site to a new or existing URL list.
Filter malicious sites by a specific time frame. You can use a predefined time frame or choose Date Range to use the calendar and time menus to customize your own.
View the primary metrics of the malicious site:
Category: The malicious category and security risk of the malicious site. You can hover over for more details.
Site Allowed: Displays the total number of times the site was allowed or if Netskope blocked it.
Users Allowed: The total number of users allowed to visit the malicious site.
Users Blocked: The total number of users blocked from visiting the malicious site.
View the attributes of the malicious site:
Users Affected: The name of the user who visited the malicious site.
Action: The action taken on the malicious site based on your configured quarantine profile.
Date: The last date the user visited the malicious site.
Site Destination: The country of the malicious site.
IP Host: The IP address of the malicious site host.
Region: The region of the malicious site.
View a list of the users affected by the malicious site. For each user, you can see the following information:
Users Affected: The name of the user who visited the malicious site.
Action: The action taken on the malicious site based on your configured quarantine profile.
Date: The last date the user visited the malicious site.
Export a list of affected users (up to 500,000 rows) to a CSV file.
View up to 300 users per page.
View multiple pages of the table.