Azure AD Plugin for User Risk Exchange
This document explains how to configure Azure AD with User Risk Exchange in the Netskope Cloud Exchange platform. This integration enables seeing multiple connected systems’ risk values for individual users and groups. The Microsoft Azure AD Risk Exchange plugin fetches users and their respective score and perform actions on them. Supported record t types include Users.
To complete this configuration, you need:
A Netskope tenant (or multiple, for example, production and development/test instances).
A Netskope Cloud Exchange tenant with the User Risk Exchange module already configured.
An Azure AD account.
An Azure AD Premium P2 subscription.
Connectivity to the following hosts:
https://graph.microsoft.com/
https://login.microsoftonline.com/
https://portal.azure.com/
Refer to Get your Azure AD Credentials for details about obtaining and providing necessary permissions.
Group.Create
Group.ReadWrite.All
GroupMember.Read.All
IdentityRiskyUser.ReadWrite.All
User.Read.All
Instance details:
RAM: 15 GB
CPU: 8 Core
Data | Time taken to Fetch Risky Users | Time taken to Fetch Risky Users Score |
|---|---|---|
200K | ~15 Sec | ~20 Min |
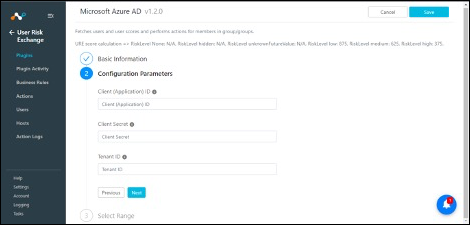
Obtain your Azure AD credentials: Client (Application) ID, Client Secret ID, Tenant ID, Microsoft Azure AD URL, and Microsoft Graph Token URL.
Configure the Azure AD plugin.
Configure User Risk Exchange Business Rules and Actions for the Azure AD plugin.
Validate the Azure AD plugin.
Click play to learn more about how this plugin works.
Go to https://portal.azure.com/ and log in.
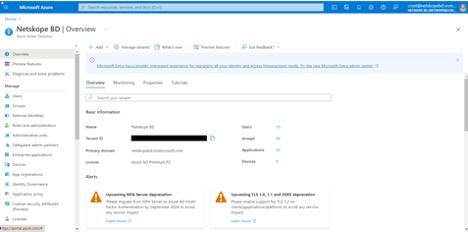
Click Azure Active Directory, and go to Overview > Basic Information.
Here you will find your Tenant ID. Copy this to use when you configure the plugin.
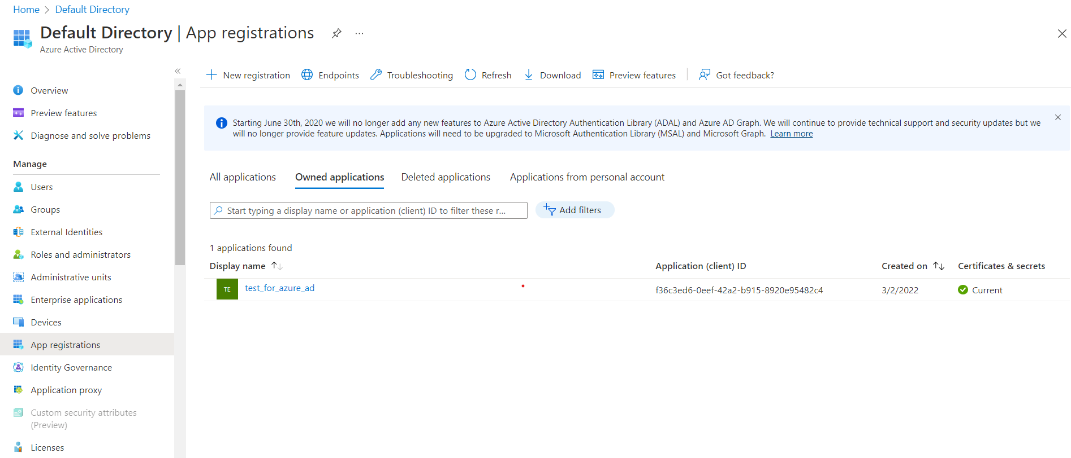
On the left hand side of Azure Active Directory, click App registrations.
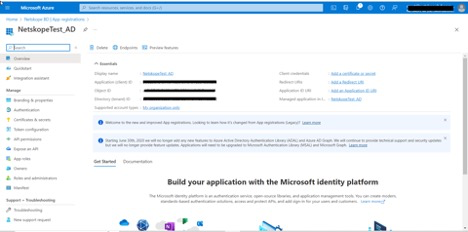
Click on your application name or New Registration. For a new registration, enter a name and click Register.
On the application page, you will find Application (client) ID. Copy this to use when you configure your plugin. This is for the Client (Application) ID setting for the plugin.
Click Certificates and Secrets.
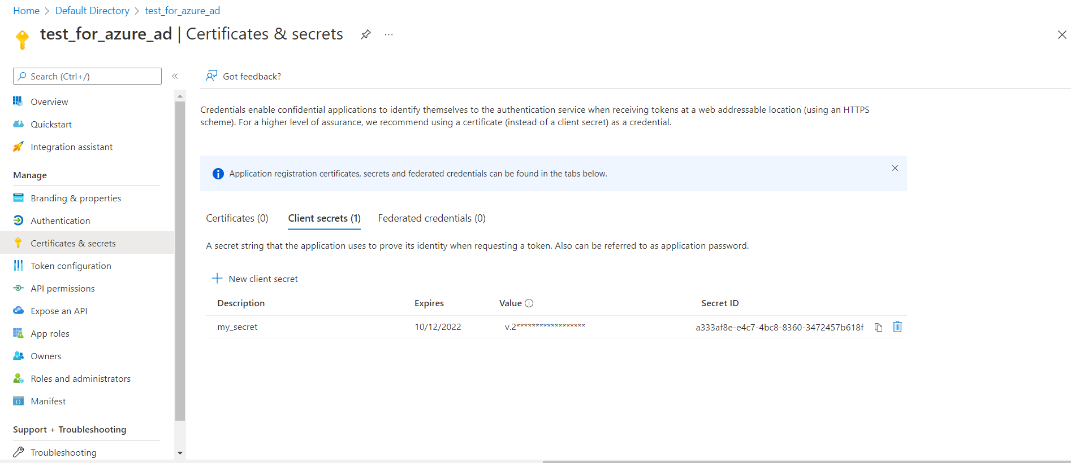
Click on + New Client Secret to create your key, and enter a description for you secret ID, select the duration for the secret value (by default it will be 6 months), click Add. Make sure you copy the value (NOT secret id), which is used for the Client Secret ID in the plugin. You can only get this when a Client Secret is first created.
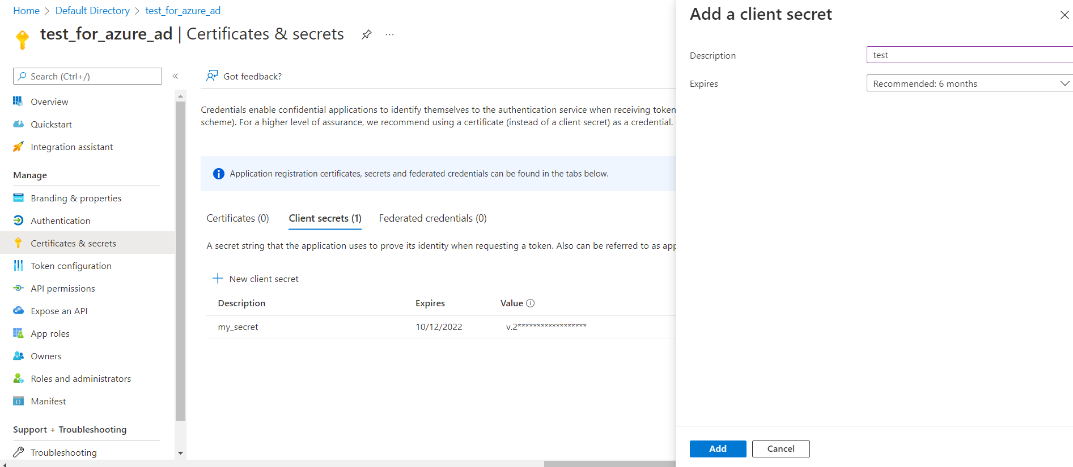
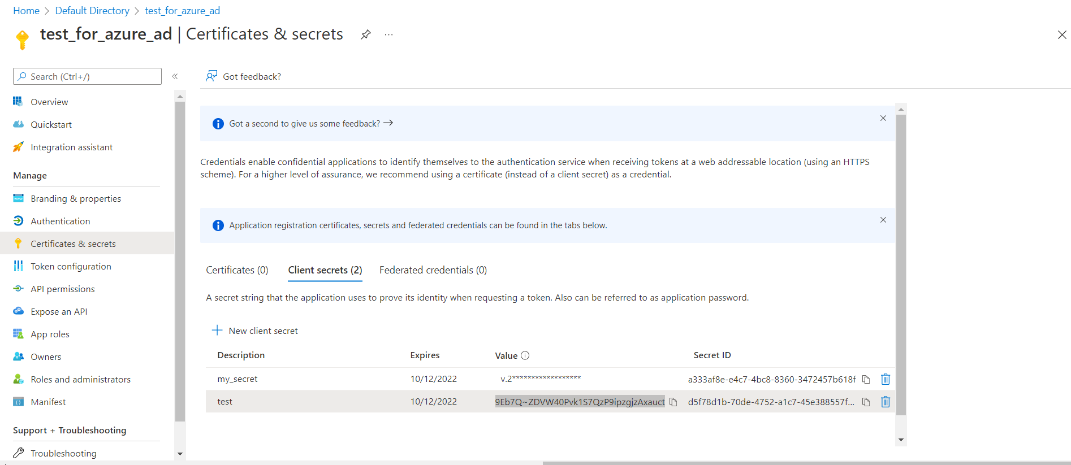
Next, perform the following steps:
Click + Add a permission and then select + Add a permission.
Click Microsoft Graph.
Click Application Permission.
Search for the following:
Group.Create
Group.ReadWrite.All
GroupMember.Read.All
IdentityRiskyUser.Read.All
User.Read.All
Grant admin consent on left side.
Use
https://graph.microsoft.comas the Microsoft Azure AD URL, and usehttps://login.microsoftonline.comas the Microsoft Graph Token URL.Collect the Tenant ID, Client (Application) ID, and Client Secret ID to configure the plugin.
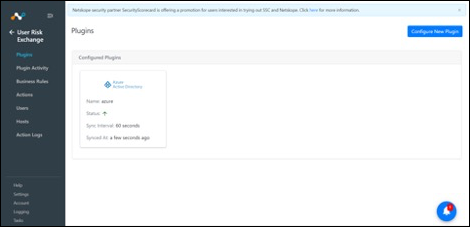
In Cloud Exchange, go to Settings > Plugins.
Search for and select the Microsoft Azure AD v1.2.0 (URE) plugin box.

Enter a Configuration Name and the Sync Interval.
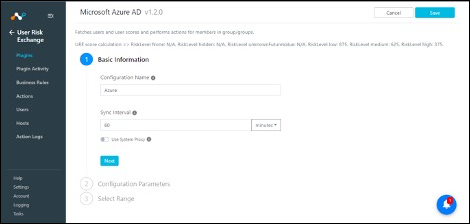
Enter the Client (Application) ID, Client Secret ID, Tenant ID, Microsoft Azure AD URL, and Microsoft Graph Token URL obtained earlier.
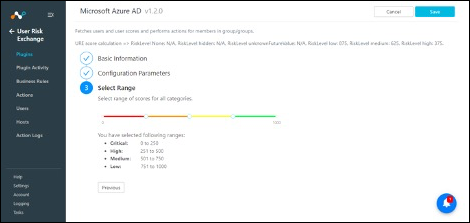
Select a range of scores.
Click Save.
Go to User Risk Exchange and click Business Rules.
Click Create New Rule
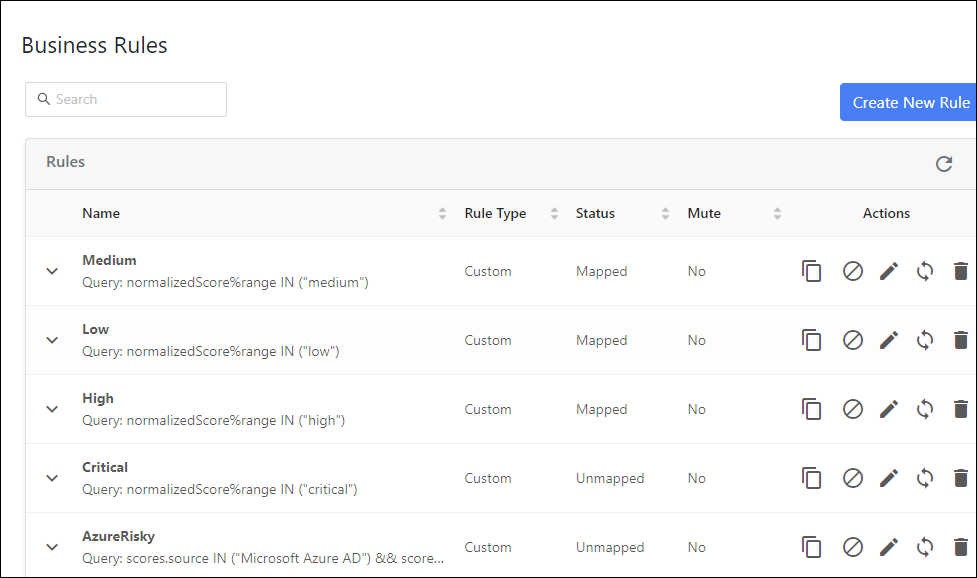
Select the options in the filter that you want to use. From the dropdowns, select a field, an operator, and a value. For example: Aggregate Score Grouping – Any in – medium.
.
You can see what your users' scores are by going to Users in the User Risk Exchange left panel.
Go to User Risk Exchange and click Actions.
Click Add Action Configuration.
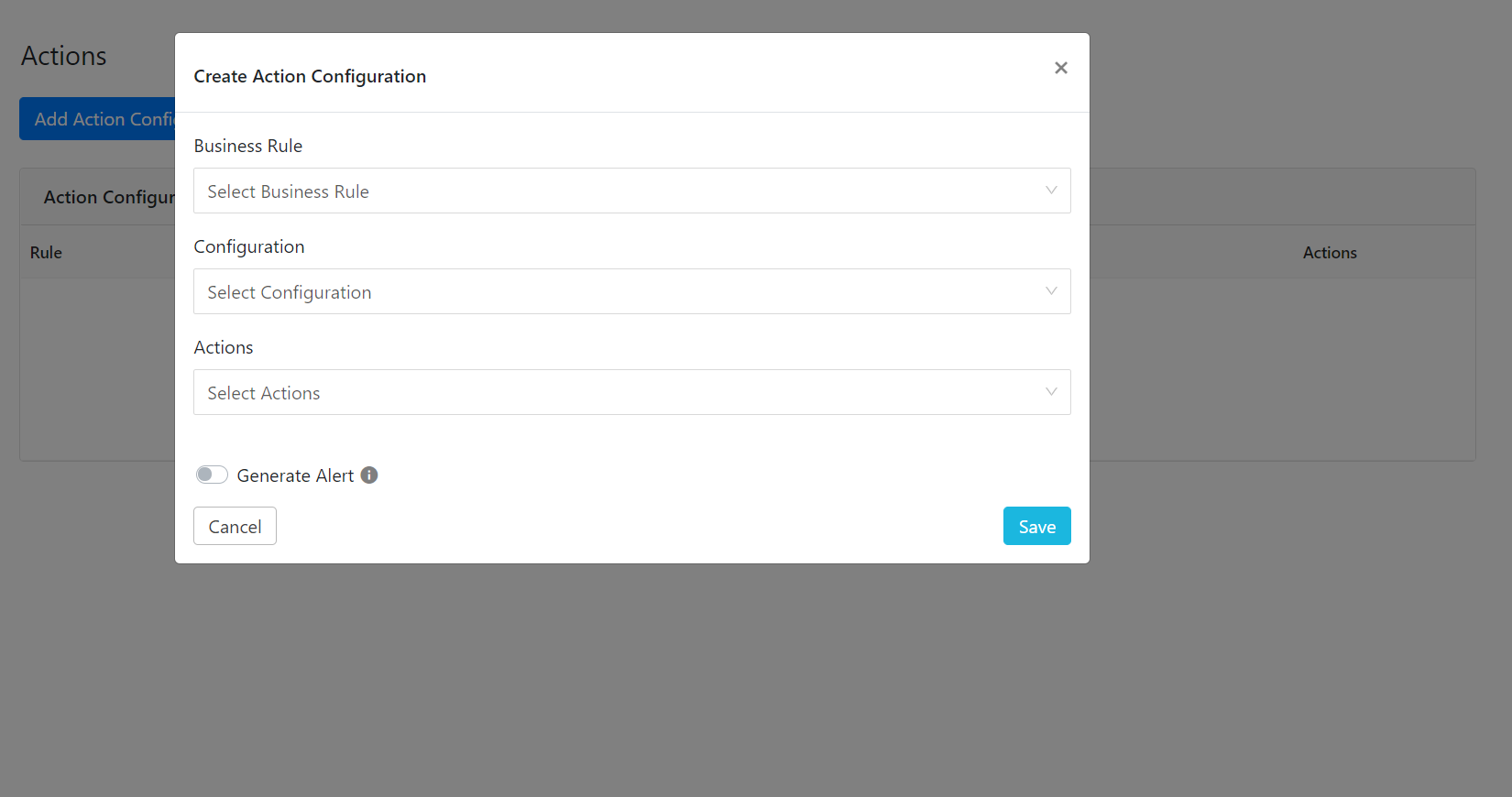
Click the Business Rule dropdown and choose the appropriate Business rule.
Select the Configuration dropdown and choose your Azure plugin.
Select Actions from the dropdown and select Add to Group, Remove to Group, No Action, or Confirm Compromised.
Add to Group : When triggered, users are added to that group.
Remove to Group : When triggered, users are removed from that group.
No Action : This does not perform any actions on users.
Confirm Compromised: When triggered, the compromised action will confirm that the user that is added to risky used is actually a risky user, and change the Risk State of that user to Confirm Compromised.
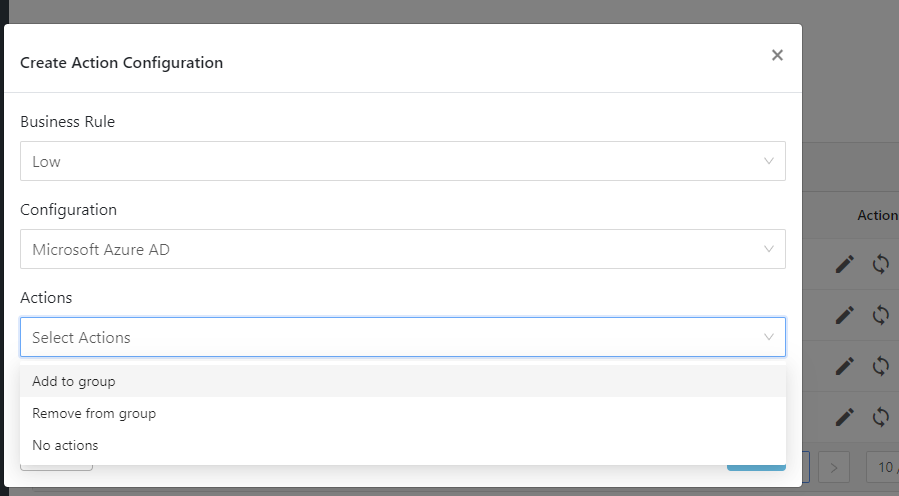
Select a Group from the dropdown, or select Create new group from the Group dropdown, and enter the Group Name if you want to create a new group in Azure AD.
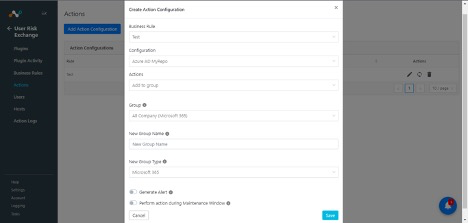
Click Save.
Click Sync to perform the action manually. Enter the days and click Fetch button to see the number of users that will be affected by this action.
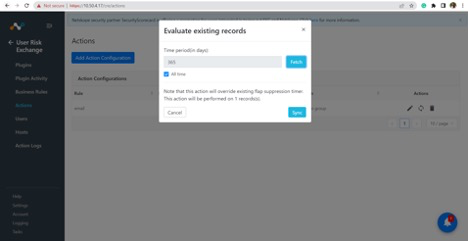
Click Sync for performing actions.
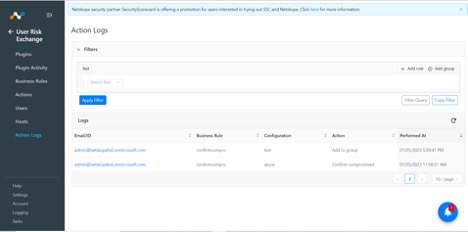
To verify the plugin is working correctly, go to User Risk Exchange > Action Logs to confirm whether any Azure AD risky users are being listed.
Validate from Microsoft Azure AD
In Azure, go to Home > Azure Active Directory.
Click Groups on the menu on the left hand side.
Search and select the name of your group. For example, Netskope in this case.
Click Members from the menu on the left hand side.
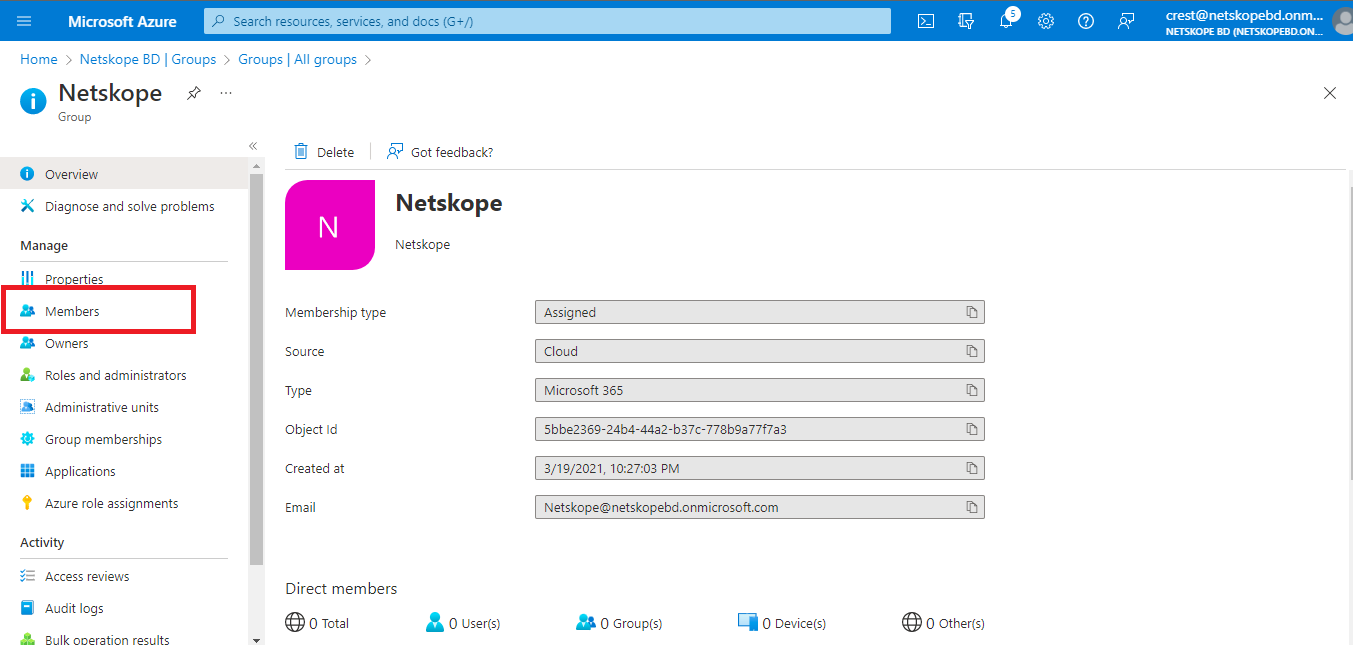
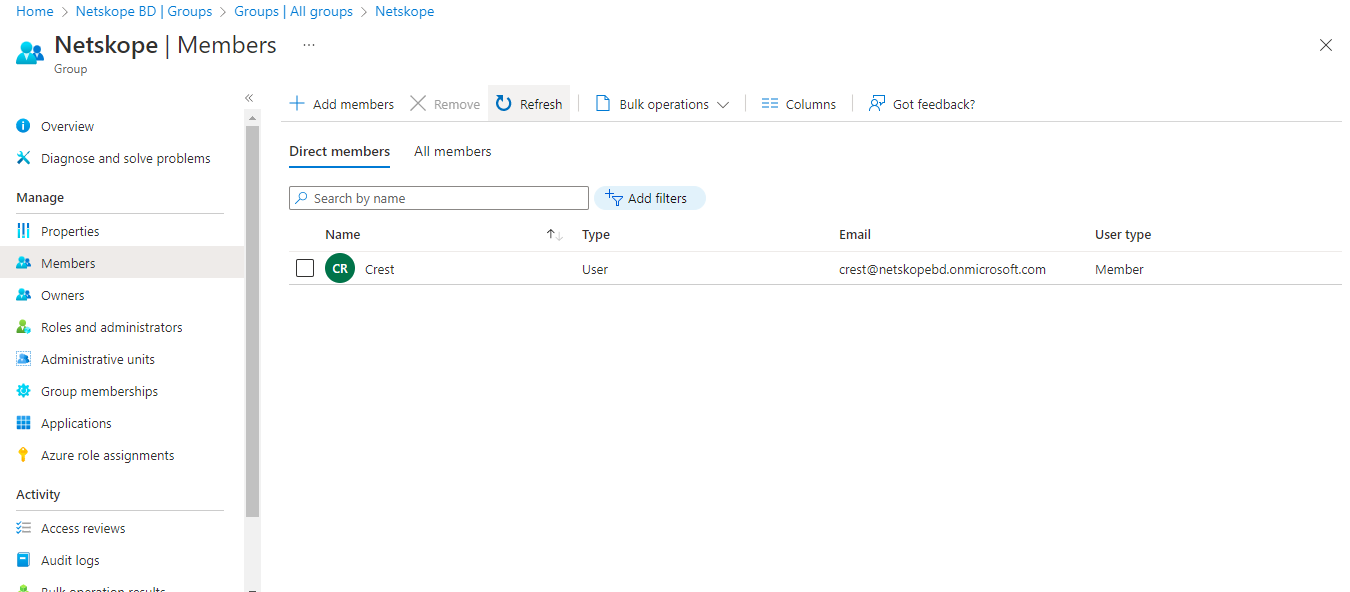
Verify the member is in or not in the group according to the action you performed. In this case, we added a member and we have a member (JA) in the group.
If Add to group action is performed, then user will be added to the group.
If Remove from group action is performed, then user will be deleted to the group.
Log in to Microsoft Azure platform and search for Azure AD Risky Users.
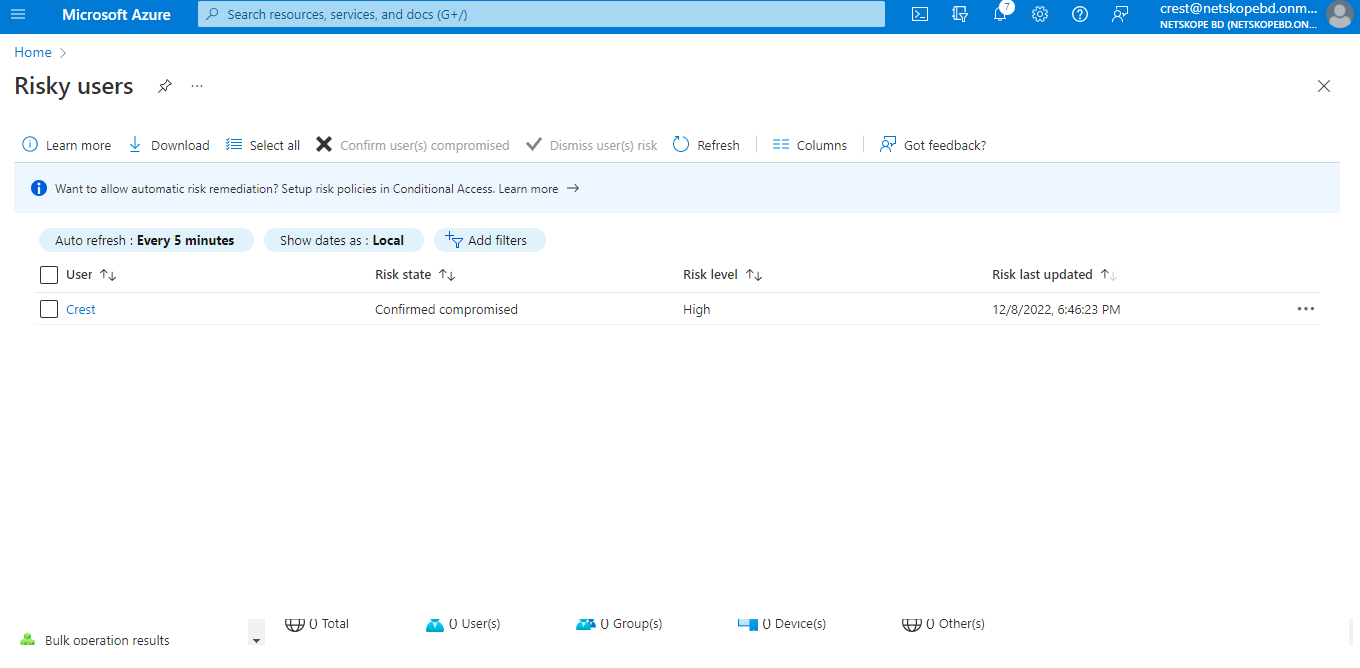
You’ll see Risk State. Initially when user is added to Risky Users then its risk state is At Risk and after the action performed then it’s risk state should changed to Confirm compromised as shown in below screenshot.
Note
This may take a few minutes (around 3 minutes) after the action Confirm Compromised is performed for the status of a user to change on the Azure platform.
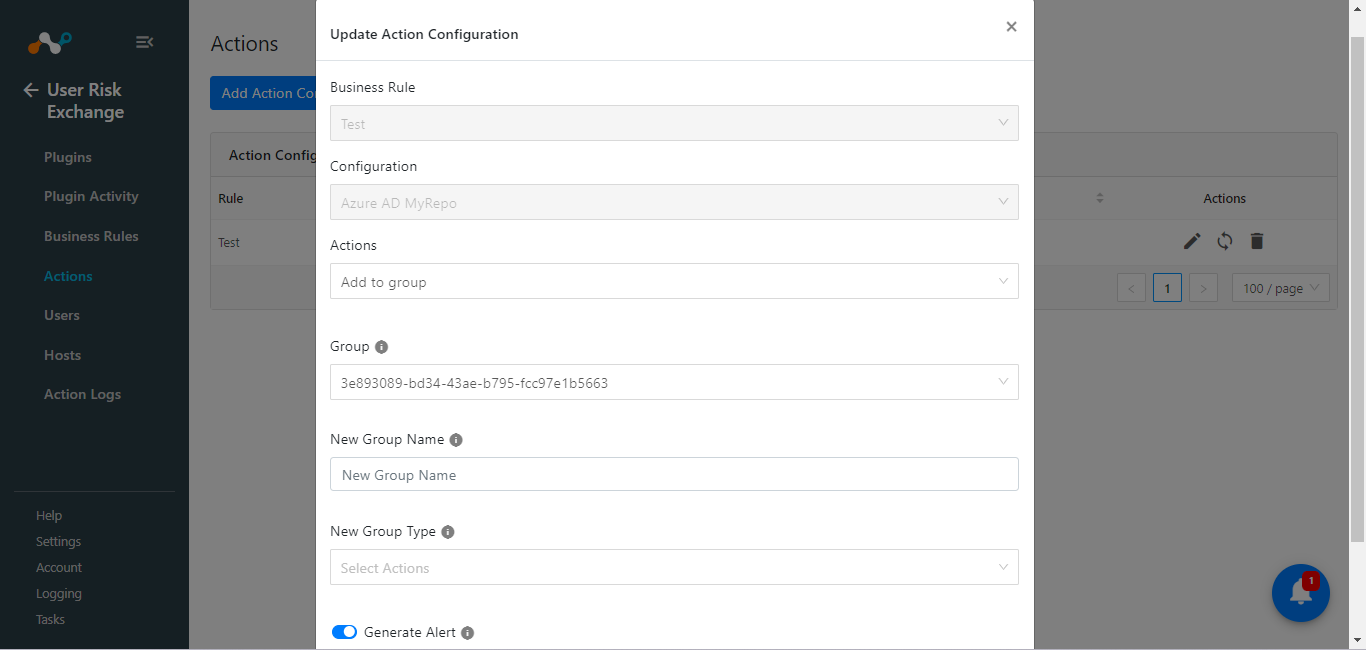
Netskope CE has some limitations related to Actions in the User Risk Exchange module. Here are the known limitation and steps to prevent them.
Update Plugin
After upgrading the Plugin from v1.1.2 to v1.2.0, you may get the Group ID displayed in the Action instead of the Group Display Name.
Edit the Action and select the Group according to the previously saved group.
 |
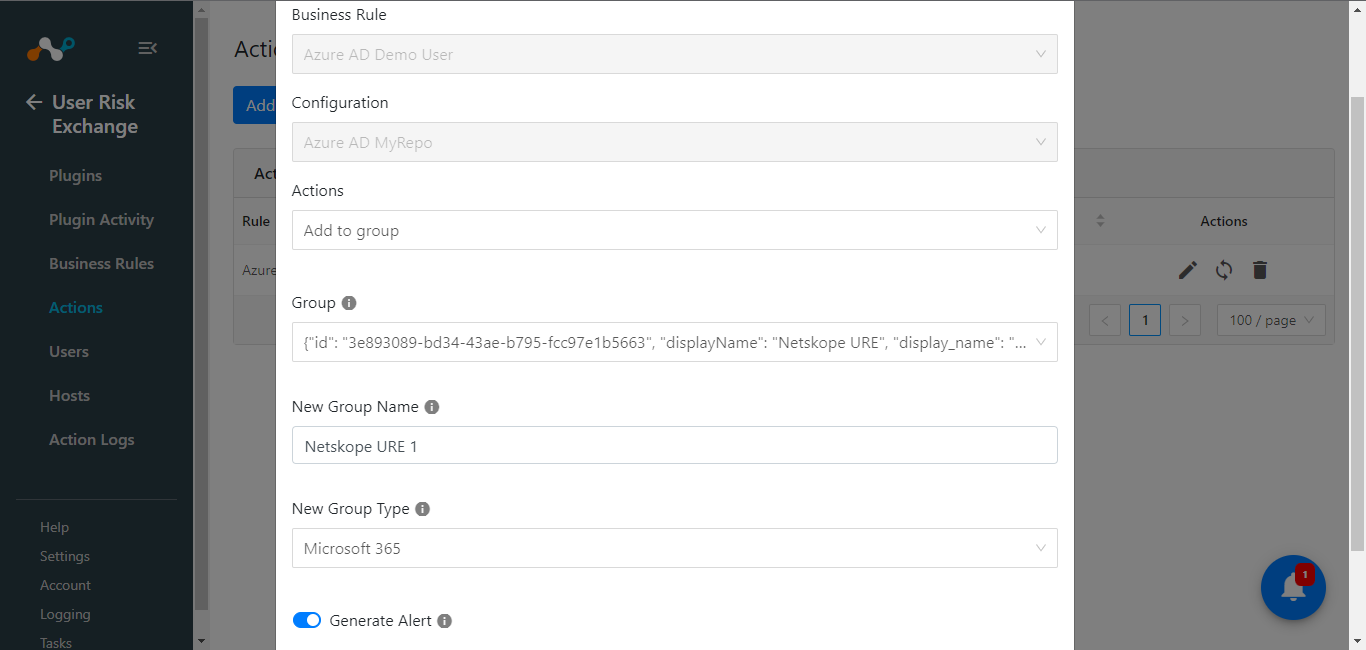
Delete/Edit Group
If the Group is Updated/Deleted from the Microsoft Azure AD then the Group name will be displayed as below.
{"id": "26739fd0-bba6-4eb7-b761-878e6f460a1c", "displayName": "Netskope CE Azure AD Demo", "display_name": "Netskope CE Azure AD Demo (Security)", "group_type": "Security"}
In the case of an Updated Group name, it won’t cause any failure, but if a Group is deleted it, will throw an error.
 |