Step 2/2: Configure AWS Permissions for CSA
Netskope requires permissions to assume a role and scan your AWS resources. This screen provides a customized CFT with permissions required to set up cross account access between Netskope and your AWS accounts. The permissions defined in the CFT are updated based on the services you've enabled on the Accounts & Services page.
You can review the CFT to understand the various permissions required by Netskope.
Note
Ensure that the AWS accounts have the permissions required to run the Netskope for IaaS services.
To complete the set up you must:
Download the CFT.
Upload the CFT to a new CloudFormation stack in each AWS account.
Confirm that a cross account role with the required permissions is created.
Follow the detailed instructions below to complete the set up.
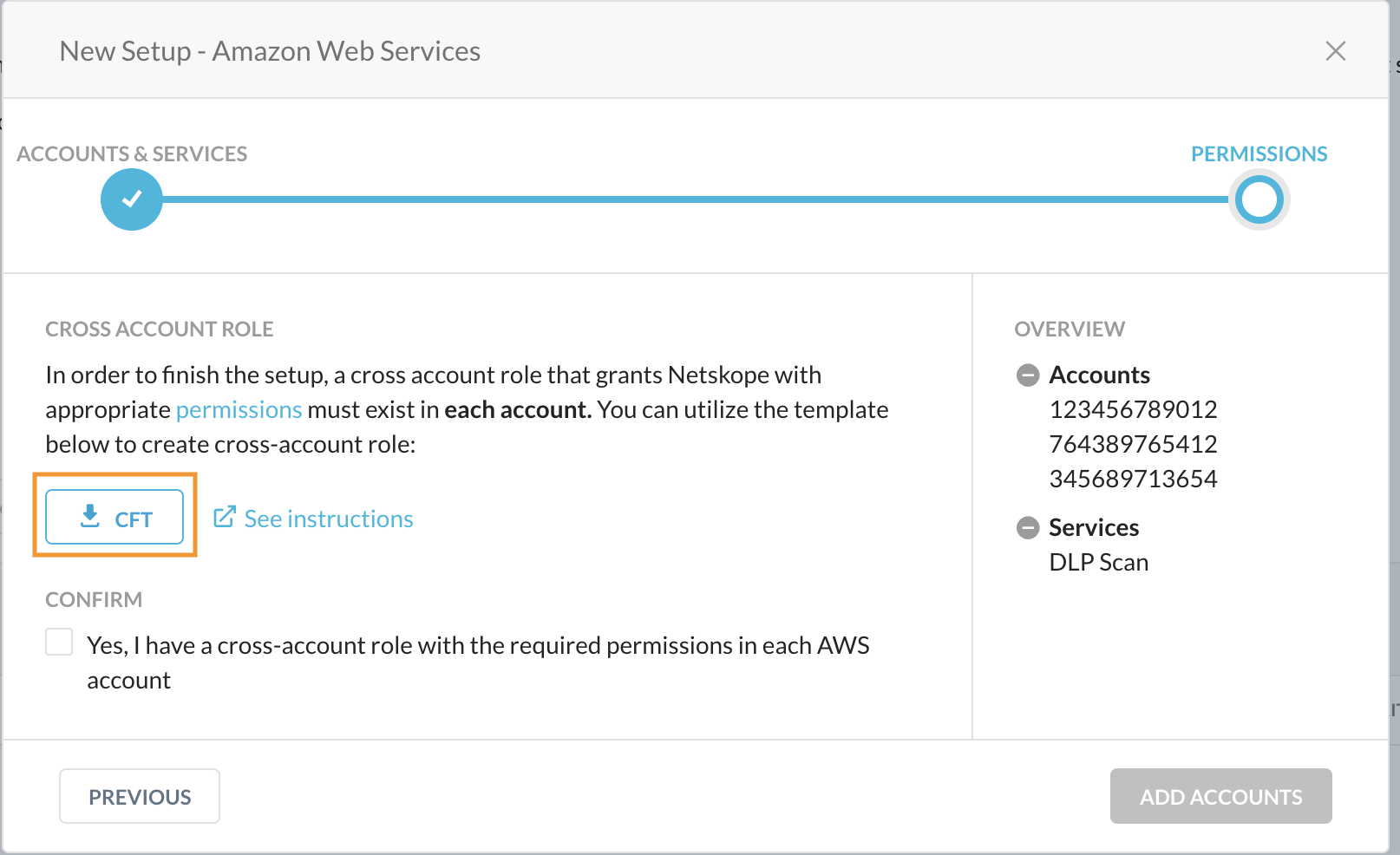
In the Permissions screen of the New Setup window, click the link to download the CFT.
Log in to the AWS Management Console using the credentials of the AWS account you are setting up with Netskope for IaaS and navigate to Services > CloudFormation.
In the CloudFormation page, click Create stack.
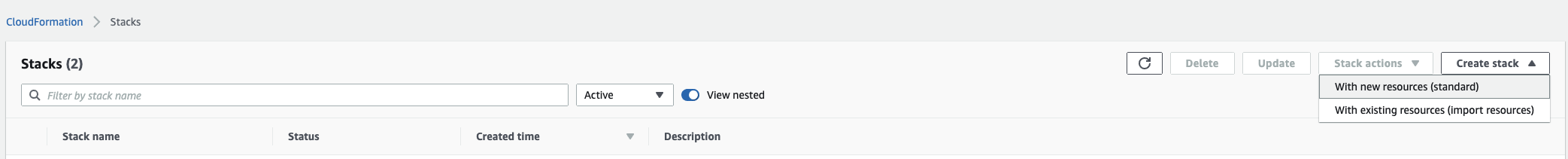
To create a stack with new resources, choose With new resources (standard).
To create a stack with existing resources, choose With existing resources (import resources).
Select Upload a template file and click Choose file to upload the aws-instance-setup.yml. Click Next.
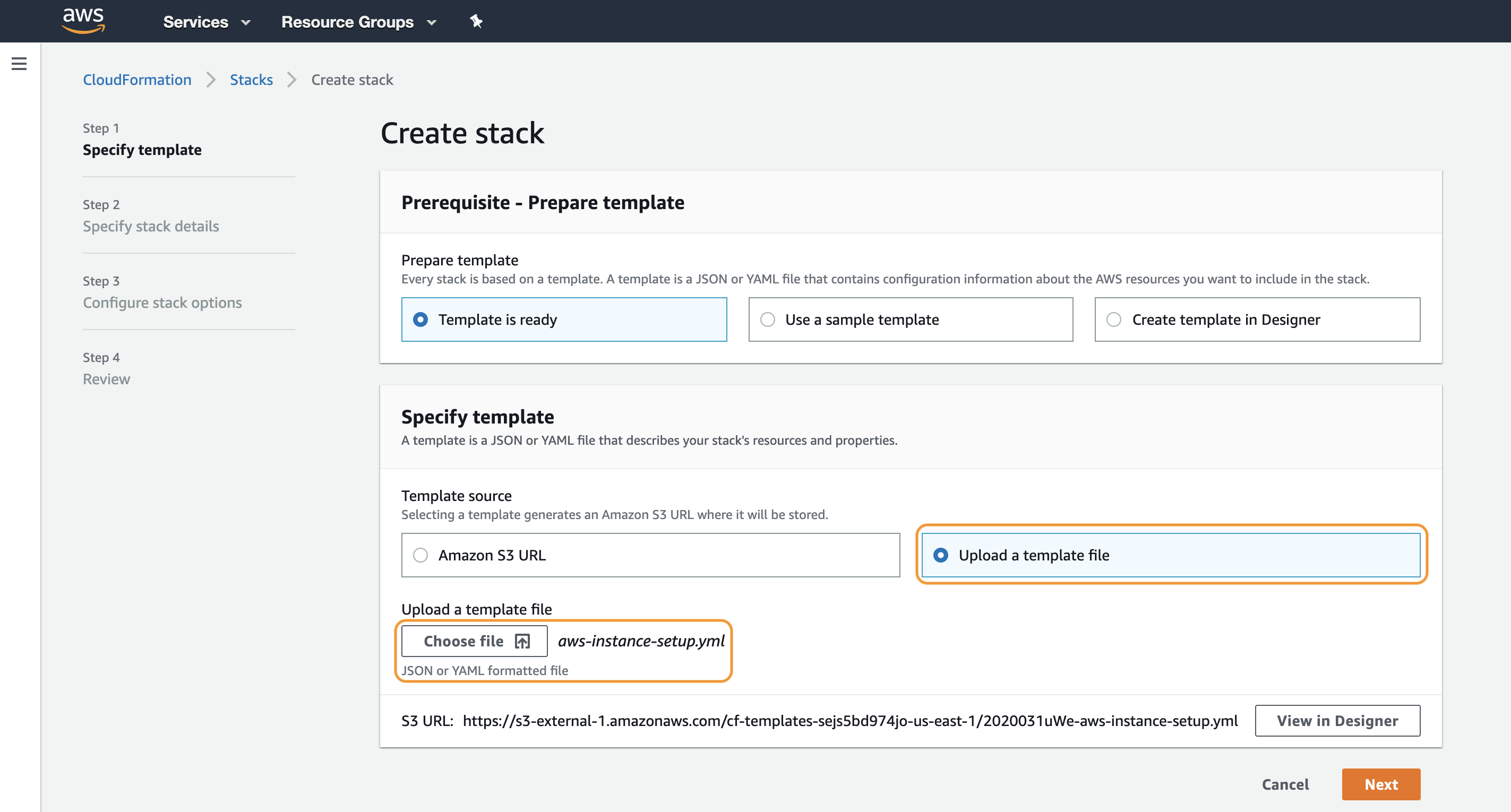
In the Specify stack details page, specify a Stack name. Click Next.
The stack name must:
Only contain alphanumeric characters and hyphens,
start with an alphabet, and
not exceed 128 characters.
In the Configure stack options page, use the default configuration, and click Next.
Review your stack details on the Review page, click the acknowledgment and then click Create stack.
When the creation process is complete, your stack will be displayed on the CloudFormation page.
You can click on the stack to view the details about the stack. The Resources tab displays the various components that are part of aws-instance-setup.yml. The Template tab displays the permissions defined in the template.
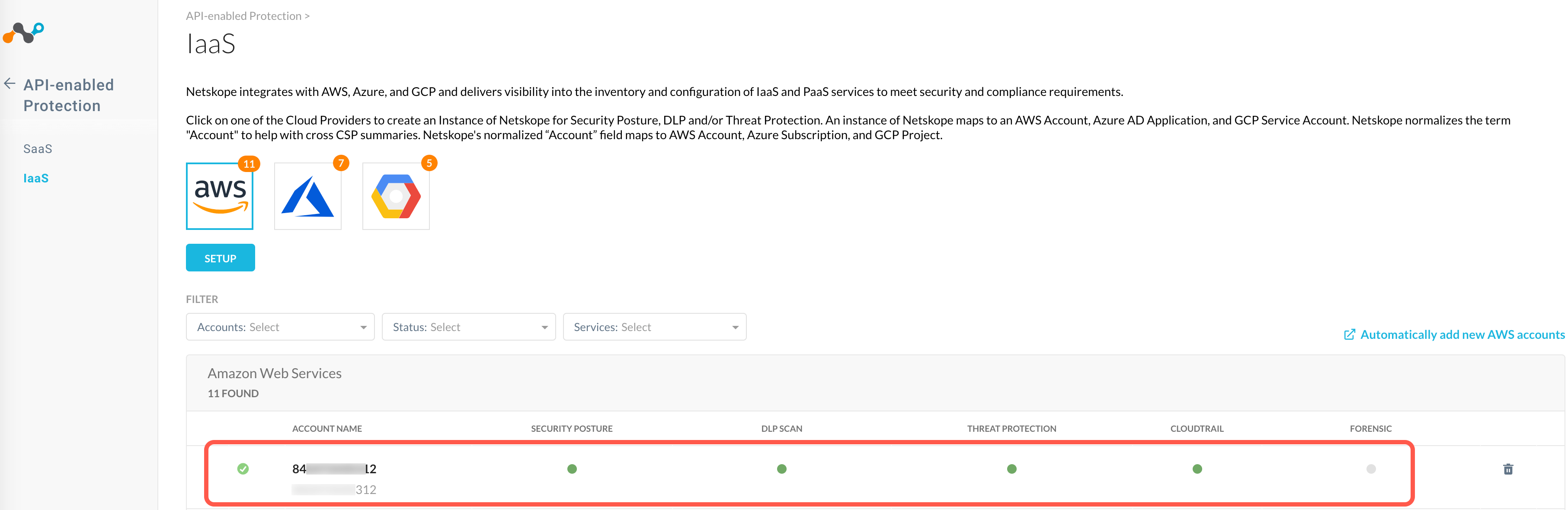
In the Netskope UI, confirm that a cross account role with permissions is created in each AWS account. Click Add Accounts.
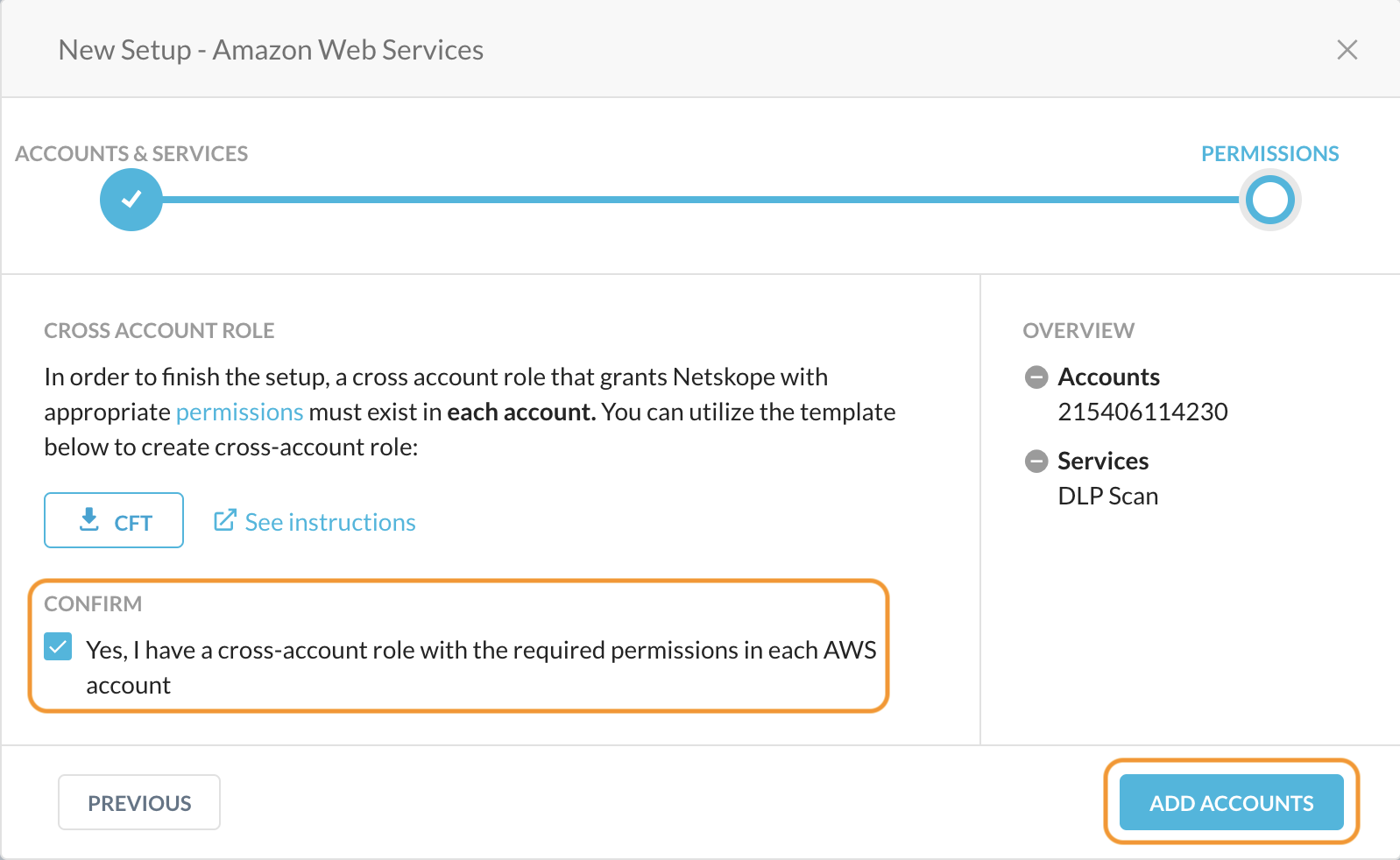
Netskope adds the AWS accounts to the Settings > API-enabled Protection > Cloud Infrastructure page. The page also displays the services that are enabled for each account.
You can view detailed information about all the events and scan results under API-enabled Protection > Compliance > Security Posture. To learn more: View Security Posture Compliance.
What happens in the process?
Netskope assumes an IAM role which enables Netskope to scan for all the resources in your AWS environment. In this case, the CFT aws-instance-setup.yml requires the following permissions to scan for resources.
AWS Permissions for Security Assessment | Purpose |
|---|---|
s3:ListBucket | Lists a specific bucket. |
ses:ListIdentityPolicies | Returns a list of sending authorization policies that are attached to the given identity (an email address or a domain). |
s3:GetBucketAcl | This implementation of the GET operation uses the acl subresource to return the access control list (ACL) of a bucket. |
s3:GetBucketLocation | This implementation of the GET operation uses the location subresource to return a bucket's region. |
s3:ListAllMyBuckets | This implementation of the GET operation returns a list of all buckets owned by the authenticated sender of the request. |
dynamodb:ListTagsOfResource | Lists all tags on an Amazon DynamoDB resource. |
sqs:ListDeadLetterSourceQueues | Returns a list of your queues that have the RedrivePolicy queue attribute configured with a dead letter queue. |
sqs:GetQueueUrl | Returns a list of your queues. |
sqs:GetQueueAttributes | Gets attributes for the specified queue. |
lambda:Get* | Returns the specified alias information such as the alias ARN, description, and function version that the Lambda function is pointing to. Also returns the configuration information of the Lambda function and a presigned URL link. |
lambda:List* | Returns list of aliases created for a Lambda function. Returns a list of your Lambda functions. Lists all versions of a function. |
cloudwatch:GetMetricStatistics | Gets statistics for the specified metric. |
cloudtrail:ListTrails | Lists all CloudTrails in your AWS account. |