Step 3/4: Assign Azure Permissions for Data Protection
To scan Azure Blob Storage for DLP scanning and threat protection, under Roles, either create a custom role with inbuilt Reader Role or assign a Contributor role with the following permissions.
Microsoft.EventGrid/eventSubscriptions/write - This permission creates or updates an eventSubscription.
Microsoft.Storage/storageAccounts/listkeys/action - This permission returns the access keys for the specified storage account.
Microsoft.EventGrid/eventSubscriptions/delete - This permission deletes an eventSubscription. Netskope creates an eventSubscription when onboarding the tenant. When the subscription is deleted, the system topic is also deleted.
The inbuilt Reader Role permission performs the following actions.
Gets an Azure subscription definition within a management group.
Gets information about a role definition.
Lists all the permissions the caller has at a given scope.
Gets the list of storage accounts or gets the properties for the specified storage account.
Gets the list of blob services.
Gets the list of containers.
Reads an eventSubscription.
Gets the list of regional event subscriptions.
Important
If you are configuring this instance for Forensic with a combination of features such as Security Posture, DLP, and Threat Protection, then you must create separate custom roles for each feature. For a combination of feature support, assign the roles based on the table below:
Feature/Role | Reader + Custom | Inbuilt Contributor |
|---|---|---|
DLP | X | X |
Threat Protection | X | X |
DLP, Security Posture | X | X |
DLP, Forensic | X | X |
Threat Protection, Security Posture | X | X |
Threat Protection, Forensic | X | X |
DLP, Threat Protection, Security Posture, Forensic | X | X |
To create a custom role for DLP and Threat Protection,
Create a JSON file with the following script and save the file as NetskopeDLP.json.
{ "Name": "custom-dlp-role", "Description": "Storage Scan", "Actions": ['Microsoft.EventGrid/eventSubscriptions/write', 'Microsoft.Storage/storageAccounts/listkeys/action', 'Microsoft.EventGrid/eventSubscriptions/delete' ], "DataActions": [], "NotDataActions": [], "AssignableScopes": ["/subscriptions/<subscriber_id>"] }To get the <subscription-id>:
Navigate to All services > General > Subscriptions.
Copy the subscription ID and replace the <subscription-id> parameter with the copied ID.
Next, use the Azure PowerShell. Click the Cloud Shell icon on the top-center bar of the Azure portal page.
Note
The shell may prompt you to create and mount a storage account.
On the PowerShell top navigation, select the Upload/Download files icon and then Upload.
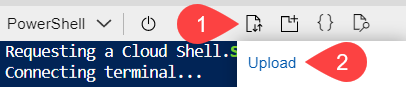
Upload the NetskopDLP.json file. Then, on the PowerShell prompt, enter the following command:
New-AzRoleDefinition -InputFile "NetskopeDLP.json"
When you run this command, Azure creates a custom role Netskope DLP Custom Role with the Microsoft.EventGrid/eventSubscriptions/write , Microsoft.Storage/storageAccounts/listkeys/action, and Microsoft.EventGrid/eventSubscriptions/delete permissions.
Navigate to Subscription, then click the desired subscription from the list.
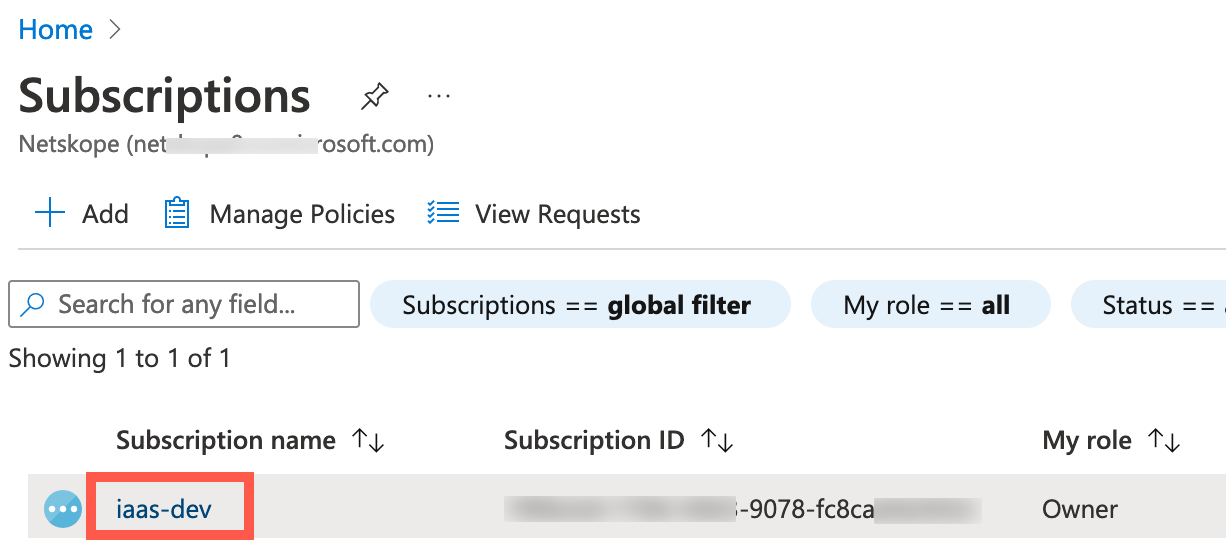
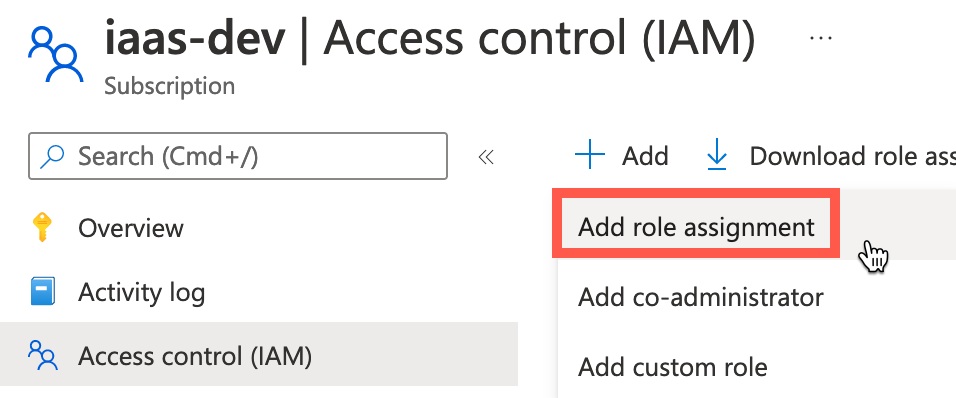
On the left navigation of the subscription, click Access Control (IAM).
Click + Add, then Add role assignment.
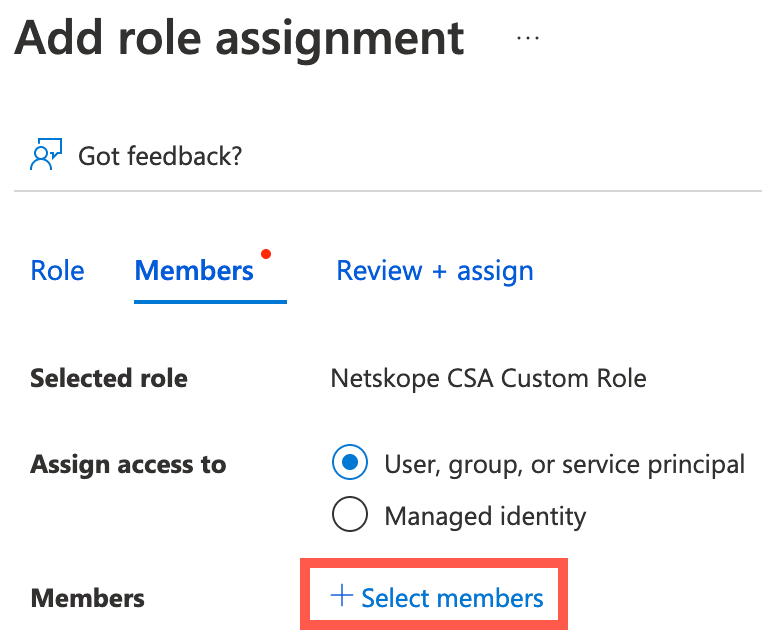
On the Add role assignment page, type the Netskope CSA Custom Role role in the search box. Click Next.
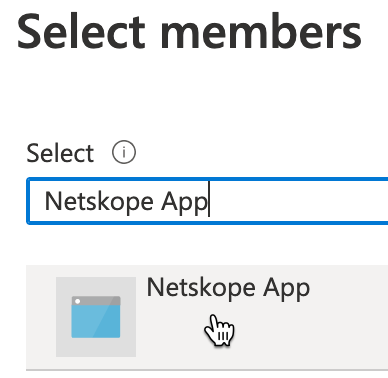
Under Members, click + Select members.
On the Select members page, type the Netskope App and select it.
Click Next followed by Review + assign.
Note
Follow steps 8-11 for the Reader role too.