McAfee Endpoint Security
McAfee Endpoint (ePO) Security offers various endpoint security solutions to managed devices. This article provides best practices recommendations to ensure smooth interoperability of Netskope Client and McAfee Endpoint Security installed in a managed device.
Recommended Reading
We recommend that you read these articles to gain a better understanding of how Client works and its interoperability with 3rd party apps.
Environment
This best practices and configurations are based on the following product versions.
McAfee Endpoint Security: 10.7
Netskope Client 92.1.0
Microsoft Windows 10
Interoperability Configuration Requirements
We recommend the following configuration requirement to ensure Netskope Client is able to steer traffic to Netskope cloud and also allow McAfee to process their traffic without any conflicts.
Configurations in McAfee ePO Console
Default policies in McAfee ePO does not introduce restrictions on Netskope Client traffic. However, when creating a new policy ensure that the ports 80 and 443 are enabled and allowed in the McAfee Security Firewall rules.
Note
HTTP/HTTPS traffic (via 80 and 443) is enabled and allowed in default firewall policy
Login to McAfee MVISION ePO.
From the top menu bar, click Policy Catalog.
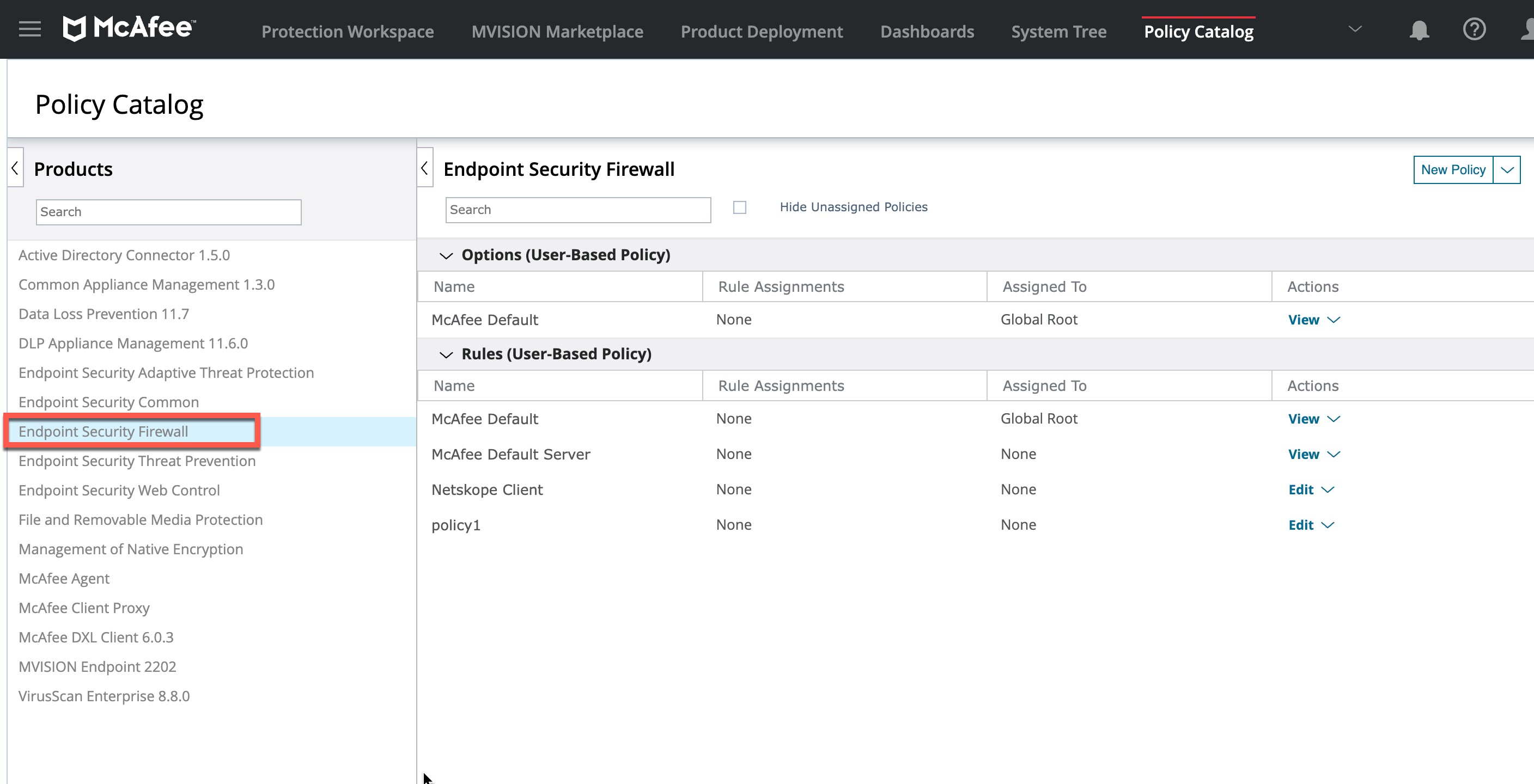
From the Products list, select Endpoint Security Firewall.
Client New Policy button.
For the new policy
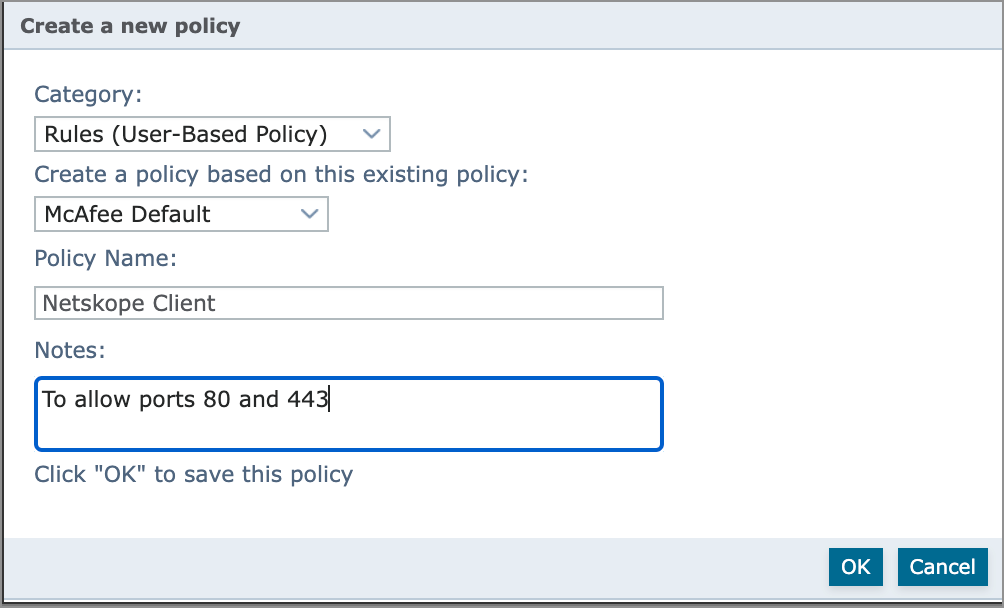
Select Category.
Select McAfee Default for Create a policy based on this existing policy option.
Give a Name for the policy and Click OK to complete this step.
In the list of Rules, click the Edit button of the policy that you created.
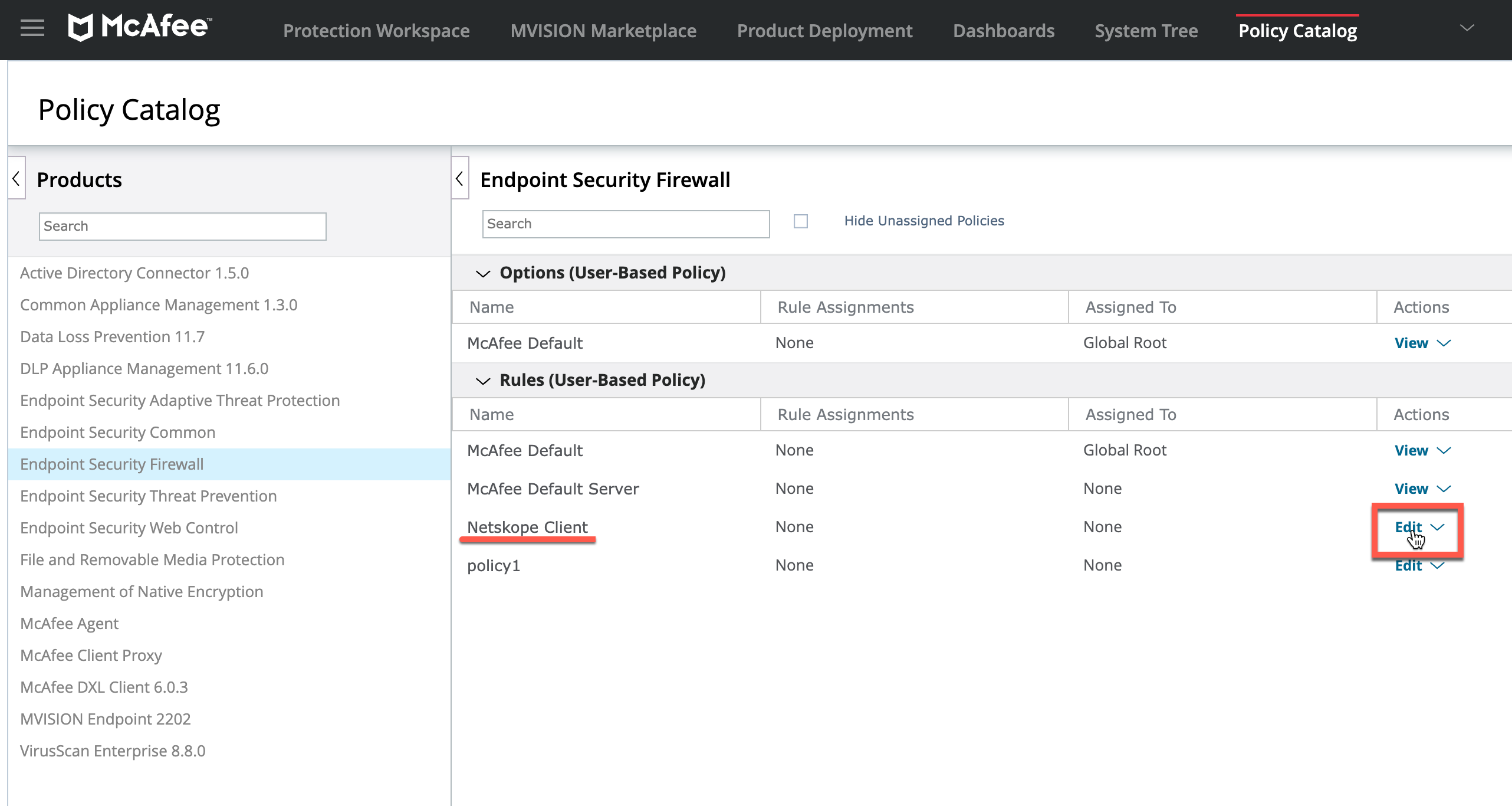
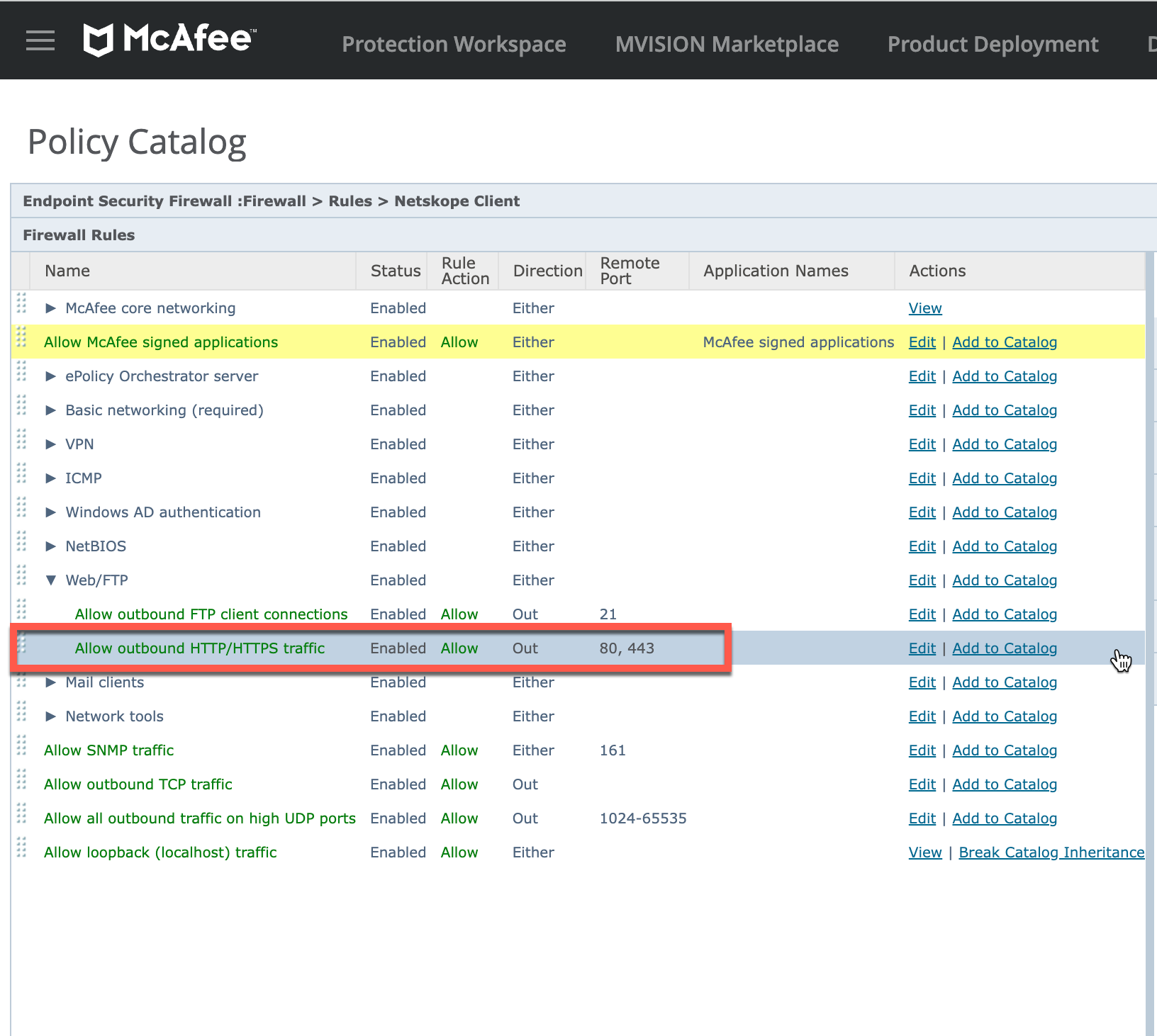
Under Firewall Rules, expand Web/FTP. In the Remote Port column, ensure that ports 80, 443 are Enabled and Allowed for outbound HTTP/HTTPS traffic.
Note
If the ports are not allowed or enabled, click the Edit button open the Edit Rule page to select the Allow option listed under Actions and select Enable rule under Status.
Click Save. This process ensures that the Netskope Client can steer traffic from the managed device to Netskope cloud.
Configuration in Netskope Tenant WebUI
In the Netskope tenant WebUI, add McAfee Agent as a certificate pinned app exception and add a set of McAfee URLs as domain exception to the appropriate steering configuration.
Login to Netskope Tenant WebUI using your admin credentials.
Go to Settings > Security Cloud Platform > Steering Configuration.
Select the appropriate steering configuration and click the EXCEPTION tab.
In the NEW EXCEPTION list, select Certified Pinned Applications. In the New Exception pop-up window, do the following:
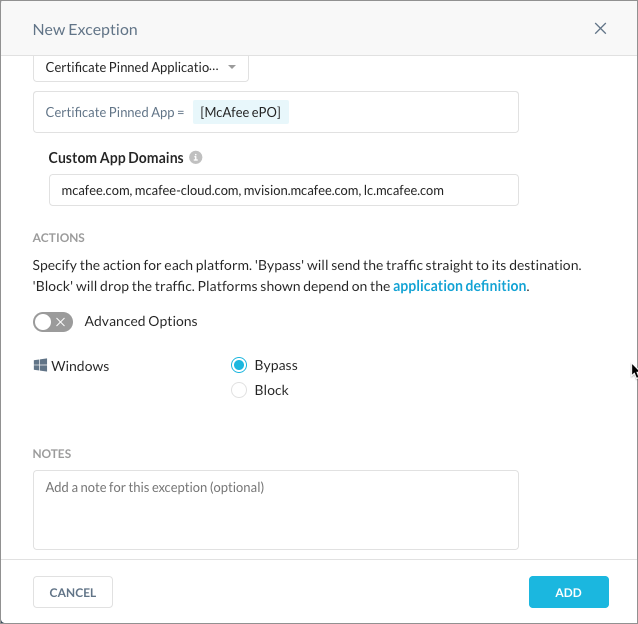
Select McAfee as Certified Pinned App.
Specify the following as Custom App Domains:
masvc.exe
macmnsvc.exe
mcscript_inuse.exe
Select Bypass and click the ADD button.
In the NEW EXCEPTION list, select Domains. In the New Exception pop-up window, do the following:
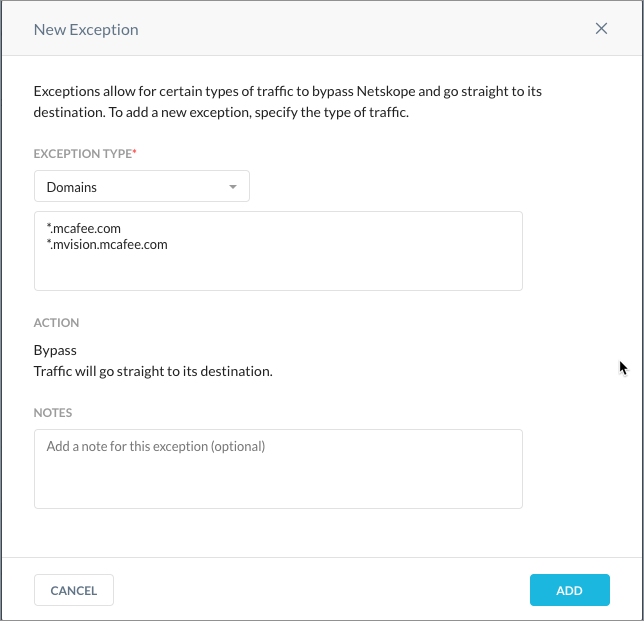
Enter the following domains and click the ADD button:
mcafee.com
mcafee-cloud.com
mvision.mcafee.com
lc.mcafee.com
Note
The mcscript_inuse executable requires domain exception for
*.mvision.mcafee.comand*.mcafee.comto:Download McAfee installer package from mvision cloud.
Download the McAfee Endpoint security download from mvision cloud and also allow lc.mcafee.com to check the license for the endpoint.
Interoperability Validation
Netskope Client Functions
Netskope Client is validated to work smoothly with McAfee ePO. To view the validation tests for Netskope Client, see Netskope Client Interoperability
McAfee Functions
McAfee functions were validated by executing the following tasks:
Security status of all products were verified to be up to date (OK) from the McAfee Mctray.
Security packages (V2 DAT, Extra DAT) updated successfully the McAfee agent.
Successfully installed McAfee ePO in the device that already had Netskope Client.
McAfee ePO console displayed appropriate status when McAfee products where uninstalled from devices.