Cisco AnyConnect
This article provides instructions to configure Netskope steered traffic to go directly to the Netskope cloud without traversing the full VPN tunnel.
Note
You must add exceptions to your Netskope steering configuration to bypass VPN traffic. To learn more see: Exception Configuration for VPN Applications.
Environment
Netskope Client 90.1.0.805
Cisco AnyConnect 4.10.05111 or higher
macOS 10.15 (Catalina)
Interoperability Configuration Requirements
When deploying Netskope Client along with a 3rd party VPN app, we recommend the following configuration changes in both the VPN client and Netskope Tenant. The following configuration changes ensure that both, the Client and the VPN app are able to operate smoothly without any conflicts.
Note
While working on the macOS performance improvement using the enableMacPerformance feature flag, Netskope observed an interoperability issue with Cisco Anyconnect in full-tunnel mode. To address the same, when the Client tunnel is established, a probe process starts within three seconds to detect AnyConnect full tunnel mode. The Client switches to lwip (method prior to enableMacPerformance flag) if the probe is unsuccessful and generates a “tunnel down due to error” event. If this occurs, the Client might disconnect and reconnect intermittently for 10-20 seconds. As a workaround, Netskope recommends adding the macOS Client VIF IP range (100.127.100.0/24) to Cisco AnyConnect split tunnel exclusion range.
Configuring Cisco AnyConnect for Netskope Client
We recommend the following configuration changes in Cisco AnyConnect to bypass Client traffic to Netskope Cloud.
SSH into the Cisco ASA (Adaptive Security Appliance) and enter into the config mode.
Copy the following ACLs and ensure that you remember the name of the this ACL.
access-list Netskope_NewEdge_Exclusions standard deny 8.36.116.0 255.255.255.0 access-list Netskope_NewEdge_Exclusions standard deny 8.39.144.0 255.255.255.0 access-list Netskope_NewEdge_Exclusions standard deny 31.186.239.0 255.255.255.0 access-list Netskope_NewEdge_Exclusions standard deny 74.217.93.0 255.255.255.0 access-list Netskope_NewEdge_Exclusions standard deny 103.219.79.0 255.255.255.0 access-list Netskope_NewEdge_Exclusions standard deny 163.116.128.0 255.255.128.0 access-list Netskope_NewEdge_Exclusions standard deny 8.8.8.8 255.255.255.255 access-list Netskope_NewEdge_Exclusions standard deny 8.8.4.4 255.255.255.255
While in config mode, create a group policy and specify the exclusion ACLs to the Split Tunnel List.
Enter the following command:
group-policy grouppolicyname attributes
In the group policy prompt, specify the exclusion ACLs to split tunnel policy
split-tunnel-network-list value Netskope_NewEdge_Exclusions
Write changes to memory
wr mem
Configuring Netskope Client for Cisco AnyConnect
To allow 3rd party apps to co-exist with Netskope Client, we recommend configuring Destination Location exceptions to your steering configurations. To learn more about adding exceptions, see Exception Configuration for VPN Applications article.
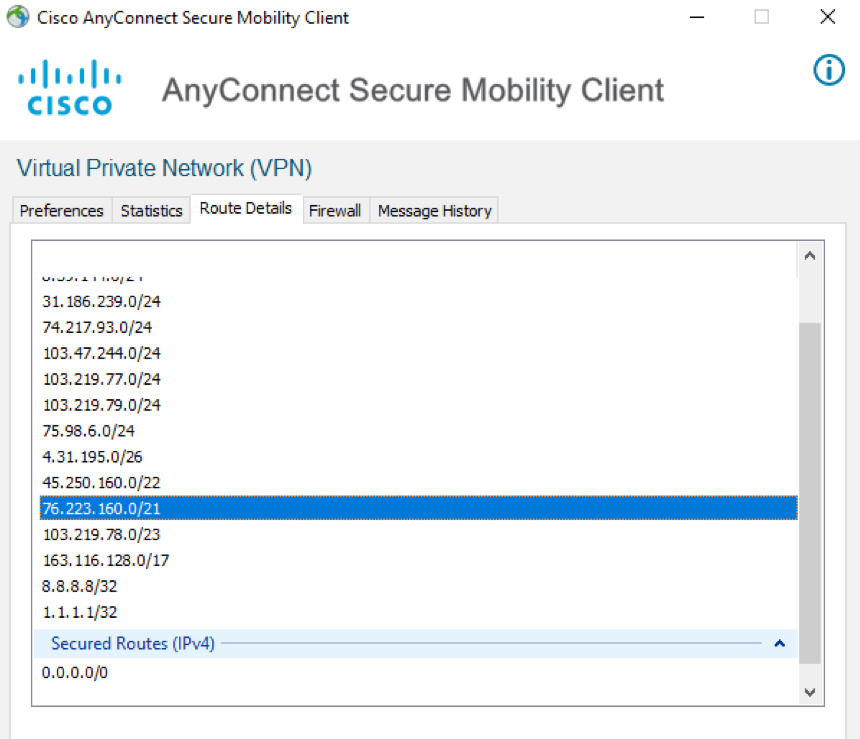
To verify if Netskope Client is able to directly send traffic to Netskope Cloud, check the routing table in the AnyConnect client. A successful configuration will have a routing table similar to the following example screenshot.