Configure Microsoft Office 365 Teams for API Data Protection
Microsoft Teams is a messaging tool that enables collaboration between users or groups of users, both internal and external to the organization. Teams bring everything together in a shared workspace, letting you work from anywhere and making it easy for your team to chat, collaborate on files, and work with favorite apps. Teams extensively uses Office 365 groups, distribution lists and identities stored in Azure Active Directory (Azure AD). It is integrated with other Microsoft apps like Outlook, Skype, OneDrive, and SharePoint making it easier for users to interact.
Teams is available to Office 365 commercial customers with one of the plans described in Microsoft Office licensing page.
To configure Microsoft Office 365 Teams for API Data Protection, you need to create a Microsoft Office 365 Teams app instance in the Netskope UI.
Important
Throughout this article, you will be prompted to enter your Office 365 credentials. Netskope does not store your Office 365 credentials. The credentials are used for creating OAuth tokens. Netskope only stores these tokens and not the actual credentials.
Note
Netskope can scan files in Microsoft Office 365 Teams when they are shared and stored in the default cloud storage apps. The default cloud storage apps are:
Microsoft Office 365 OneDrive for files shared in direct messages and group chats.
Microsoft Office 365 SharePoint for files shared in channels.
Netskope does not scan files if they are shared and stored in third-party cloud storage accounts.
Microsoft does not provide any webhook notification for files uploaded through the files and wiki tab of Microsoft Teams. Due to this limitation, Netskope does not support DLP scanning for such file uploads. However, Netskope detects files sent as an attachment from a channel's chat window. For full DLP coverage, you should set up respective API Data Protection instances for Microsoft Office 365 OneDrive and SharePoint.
Prerequisites
To grant Office 365 access for audit logs, the following prerequisites must be met:
A global administrator account is required to grant access to Netskope. Post-grant, this account is not required.
Note
The way permissions work in Azure/Office 365 is that Netskope requires an administrator to grant enough privileges for Netskope to perform specific actions. Note that the Netskope app does not receive global admin permissions. It only receives permissions for the scope Netskope requests.
In particular, the global admin is the only user that can delegate access for application-level permission (as opposed to user level permissions). You can find additional Microsoft documentation on how all these work here. Furthermore, global admin credential is required for Graph and Office 365 Management APIs. Post-grant, Netskope is independent of the granting account for policy processing.
You must turn on audit logging in Microsoft 365 admin center. To enable audit logging, log in to https://compliance.microsoft.com/, then on the left navigation, click Audit. If auditing is not turned on for your organization, a banner is displayed prompting you start recording user and admin activity. Click the Start recording user and admin activity banner. It may take up to 60 minutes for the change to take effect.
Note
If you do not see this link, auditing has already been turned on for your organization. After you turn it on, a message is displayed that says the audit log is being prepared and that you can run a search in a couple of hours after the preparation is complete. You only have to do this once. For additional information, read this support article on the Microsoft site.
Configure Netskope to Access your Office 365 Teams App
To authorize Netskope to access your Microsoft Office 365 Teams account:
Log in to the Netskope tenant UI:
https://<tenant hostname>.goskope.comand go to Settings > API-enabled Protection > SaaS.Select the Microsoft Office 365 Teams icon. Enter the following details:
Under INSTANCE NAME, enter a name of the Microsoft Office 365 Teams account. You can enter any name.
For INSTANCE TYPE, select from the following options:
API Data Protection: Select this option to allow Netskope to scan through your SaaS app instance to list files, user, and other enterprise data.
Malware - You can select this option to scan any file attachment for malware in private, public channels, direct messages, and group chats. Once detected, you can quarantine* the malware file. To do so, navigate to Settings > Threat Protection > API-enabled Protection. Ensure that malware scanning is enabled for the Microsoft Teams app instance and under Settings, select a quarantine profile. To view files affected by malware, navigate to Incidents > Malware.
Note
*Microsoft Teams is not a storage app. Due to this, you cannot create an exclusive quarantine profile. However, if you have set up any API Data Protection-supported storage apps, you can leverage the quarantine profile of these apps. To set up a quarantine profile for any of the supported storage apps, refer to the documentation located here.
Security Posture: This option allows Netskope to continuously scan through your SaaS app to identify and remediate risky SaaS app misconfigurations and align security posture with best practices and compliance standards. This is a read-only checkbox. To enable security posture for Microsoft Teams, configure the Microsoft 365 app under Settings > API-enabled Protection > SaaS.
Note
This feature is part of the Netskope SaaS Security Posture Management solution. For additional configuration requirement, read Next Generation SaaS Security Posture Management.
Enter your Microsoft Office 365 global administrator email address.
Note
Netskope recommends creating a temporary global administrator account for this purpose. To do so, log in to your Microsoft Office 365 admin center and create a user with a global administrator role. Later, you can either delete or downgrade this account to a non-global administrator account.
Enter a list of internal domains. Important points to note:
Note
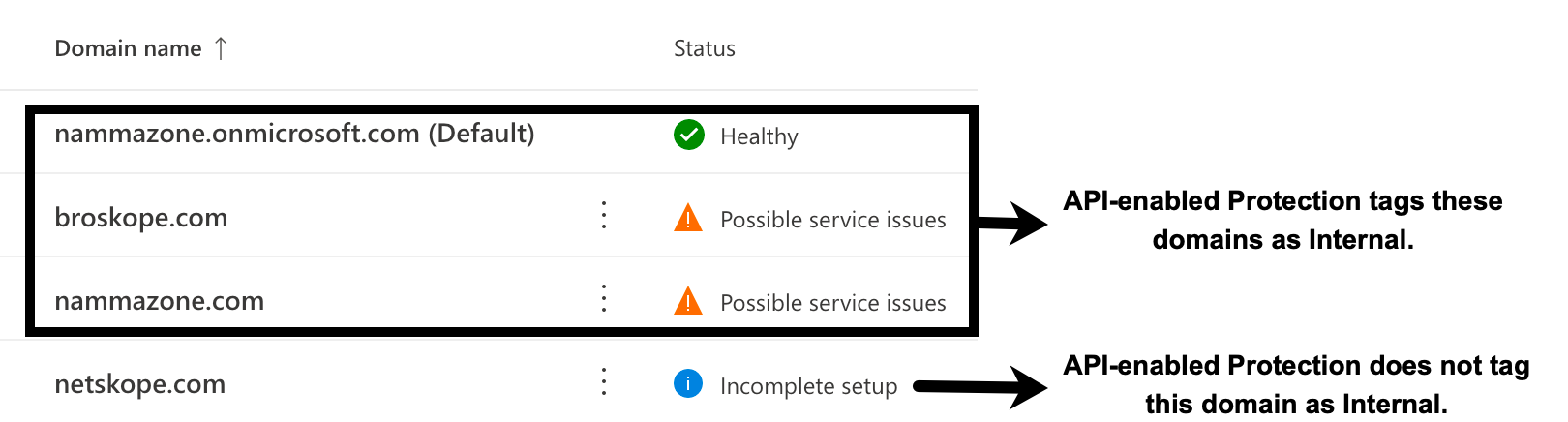
Verified domains (in Office 365 tenants, their statuses are displayed as “healthy” and “possible service issues”) provisioned in the Office 365 tenant need not be added to the internal domain list. These domains will be automatically treated as internal by API Data Protection. However, the following domains can be added during the grant time if they need to be treated as internal by API Data Protection:
domains that are unverified (status displayed as “incomplete setup”) in the Office 365 tenant.
domains that are not provisioned in the Office 365 tenant.
A sample example of Office 365 domains is as follows:
Log in to your Microsoft Office 365 Admin Center, then navigate to Settings > Domains.
Ensure that you add the internal domains at grant time. Adding internal domains post-grant will require a re-grant, and will not mark the existing external users and files as internal even if the users and files are part of the internal domain.
For internal domains, wildcard DNS entries are not allowed.
Click SAVE, then click Grant Access for the app instance you just created.
After clicking Grant Access, you will be prompted to log in with your global administrator username and password. Accept the permissions and click Close.
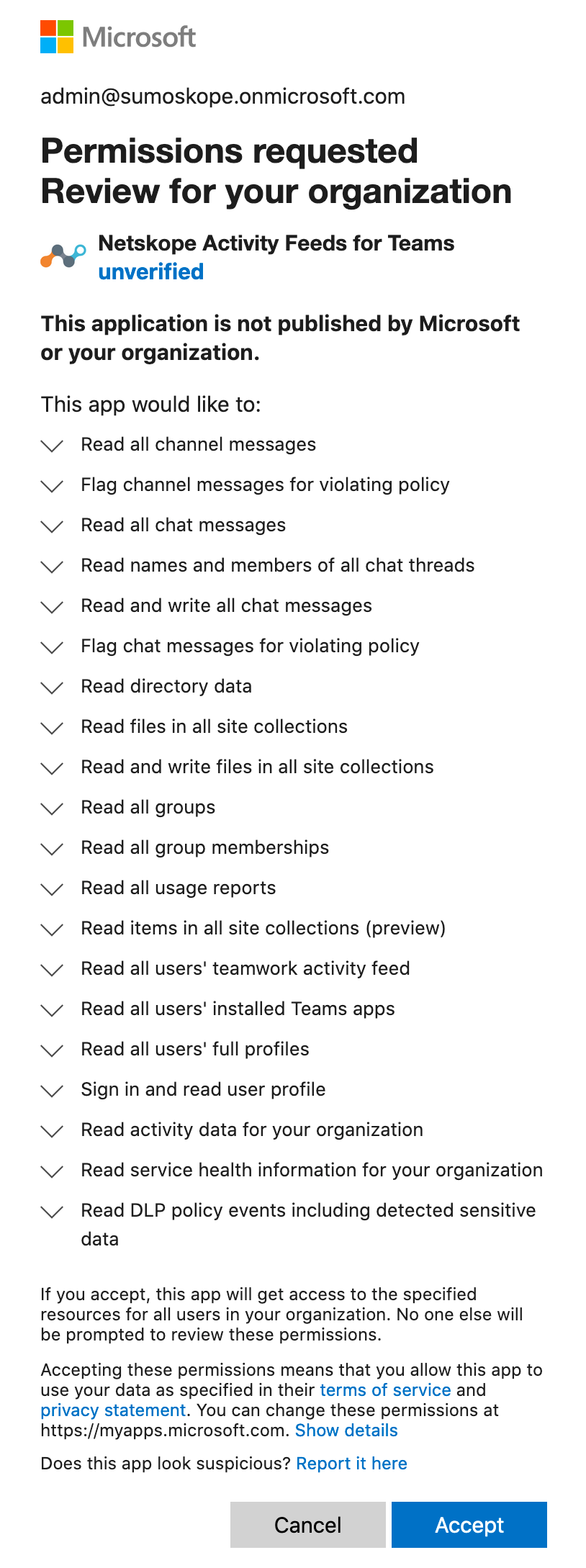
The Netskope for Teams enterprise app is installed in Azure AD with the appropriate permissions once you grant the Microsoft Office 365 Teams app. For details on the permissions, refer Azure Web App Permissions for Microsoft Office 365 Teams.
Refresh your browser, and you should see a green check icon next to the instance name.
Important
After granting access, make sure you log in to https://login.microsoftonline.com/ from a browser at least once with the email address you added in step 2c. This step is mandatory so that Netskope can make successful API calls with the Microsoft Office 365 account.
This completes the Microsoft Office 365 Teams integration with Netskope.