Enable SAML Authentication on DPoP Appliance
You can integrate Netskope's DPoP appliance into your existing IdP deployment. When you enable SAML authentication on an appliance configured in explicit proxy mode, the user will be required to authenticate with your IdP server before their connection is sent to the origin server, for example, www.abc.com via the DPoP appliance.
The following diagram exhibits the flow of traffic between a user, IdP server and the origin server through the DPoP appliance.
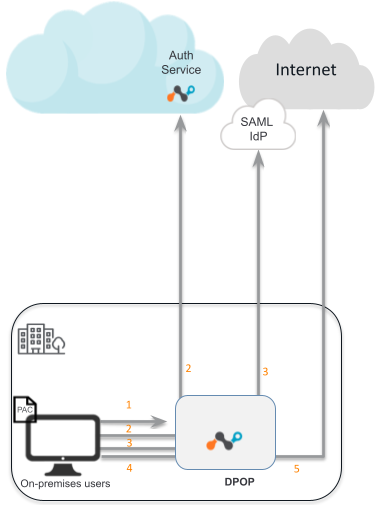
In this diagram:
The user accesses the URL, server,cnn.com. The user traffic to this origin server gets routed to DPoP through PAC redirection.
DPoP redirects the traffic to the auth service in the cloud which redirects the user to the IDP server for authentication.
The user performs SAML authentication, and the IDP server generates SAML assertion to redirect the user back to the NS auth service.
Auth service redirects the user to the original URL, server.cnn.com and the traffic will get routed to DPoP.
DPoP extracts user info, performs policy evaluation, and applies the action accordingly.
To enable SAML authentication on a DPoP appliance,
Ensure that SAML Forward Proxy is enabled on your Netskope tenant. To learn more: SAML Forward Proxy.
In the appliance CLI, enter configuration mode and run the following command.
set dataplane proxy-mode explicit saml-auth enable true
You can disable SAML authentication on the appliance by setting the value to false. Run the following command in configuration mode.
set dataplane proxy-mode explicit saml-auth enable false