Configure Salesforce Instance for Next Generation SaaS Security Posture Management
The installation instructions describe how to integrate your Salesforce account with Netskope. To configure Salesforce for Next Generation SSPM, you need to authorize Netskope as a web application client to access your Salesforce account. There are two parts to this procedure:
Configure Salesforce API Access
Configure Salesforce Instance in Netskope UI
Important
If you have already configured API Data Protection for Salesforce, you need not configure the Salesforce API Access. However, you should enable the Modify Metadata Through Metadata API Functions permission under the custom profile you have already created. Thereafter, you can edit the existing Salesforce instance under Settings > API-enabled Protection > SaaS and enable the Security Posture checkbox and re-grant the app instance.
Configure Salesforce API Access
Note
The following steps are validated with Salesforce Lightning mode and may not apply to Classic mode. Lightning mode is not a requirement to run Next Generation SSPM. You can configure using Classic mode as well. To switch to the Lightning Experience UI, log in to login.salsesforce.com and on the top-right of the home page, click the User menu drop-down list and select Switch to Lightning Experience.
To authorize Netskope as a web application client to access your Salesforce instance, you should create a custom profile on the Salesforce portal.
Important
Netskope recommends creating an exclusive custom profile for the Netskope app. If you intend to run any custom processes or scripts (other than the Netskope app), create a separate custom profile. Do not use the exclusive custom profile intended for the Netskope app for custom processes or scripts (like bulk uploads, etc.) because they may interfere with the Netskope app.
Log in to login.salesforce.com.
In the left navigation bar, go to Administration > Users > Profiles.
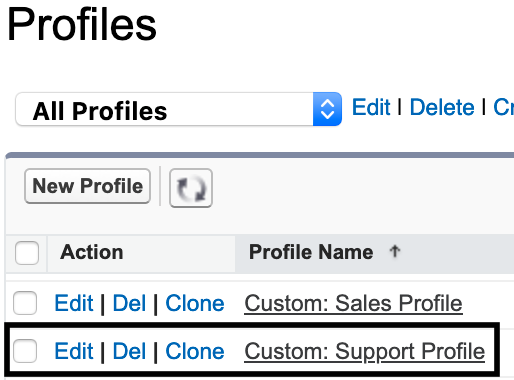
Clone a user profile. You can clone a system administrator, standard user, read-only, or any other profile. Ensure that the user profile has an active "Salesforce" license. In this example, click Clone beside the Custom: Support Profile.
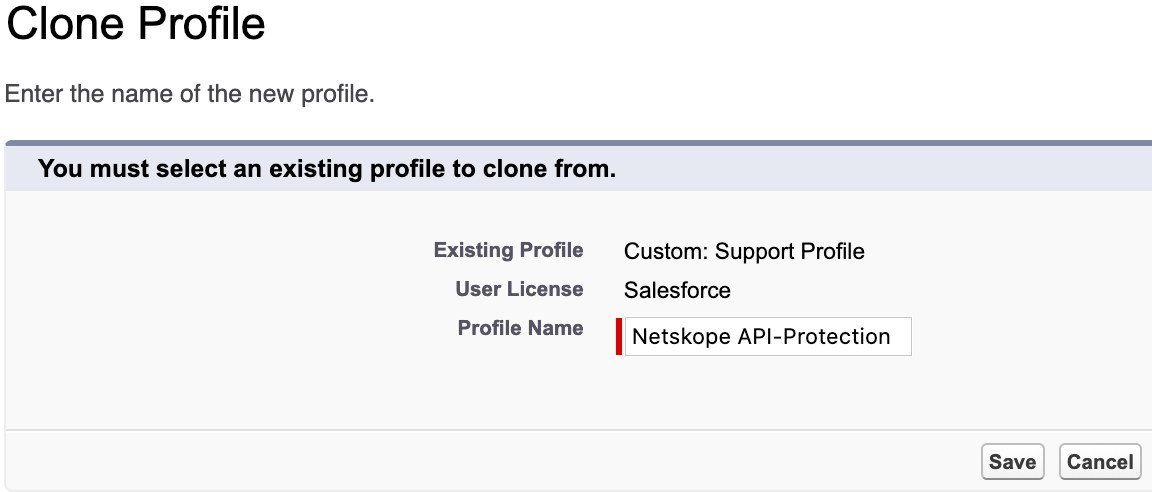
On the Clone Profile page, enter a profile name and make sure the User License shows Salesforce . When finished, click Save.
After creating the custom profile, click Edit to modify the custom profile.
Scroll down to the Administrative Permissions section of the custom profile. Enable the following permissions:
Note
You must directly assign the permissions to the profile. Do not add the permissions through permission sets.
API Enabled
Modify Metadata Through Metadata API Functions
View All Data
View All Users
To know more about the permissions, see Permissions Required for Salesforce.
When finished, click Save.
In the left navigation bar, go to Administration > Users > Users.
Click Edit to modify an existing user, or New User to define a new user.
In the User Edit > General Information section, set the Profile created in step 4.
In the User Edit > General Information section, enable Salesforce CRM Content User. This allows the user to view the CRM content files and is required to list and take actions on the Salesforce CRM Content or Library files.
When finished, click Save.
Important
Netskope recommends allowing a pool of Netskope public IP addresses in Salesforce. This will ensure events and notifications are exchanged between Salesforce and Next Generation SSPM without any restrictions. To allow the IP addresses:
Log in to login.salesforce.com.
In the left navigation bar, go to Settings > Security > Network Access.
Click New beside Trusted IP Ranges.
In the Trusted IP Range Edit page, specify the Start IP Address and End IP Address.
Click Save.
To get a pool of Netskope public IP addresses, log in to your Netskope tenant, and navigate to Settings > Security Cloud Platform > REVERSE PROXY > Office 365 Auth. Scroll down to the Netskope Source IP Address/Range section.
Configure Salesforce Instance in Netskope UI
To authorize Netskope to access your Salesforce instance:
Log in to the Netskope tenant UI:
https://<tenant hostname>.goskope.comand go to Settings > API-enabled Protection > SaaS.Select the Salesforce icon, and then click Setup Instance.
The Setup Instance window opens. Enter the following details:
In the INSTANCE NAME field, enter the organization name or ID of your Salesforce account. To locate the organization name or ID in salesforce.com, log in to the salesforce.com account. Navigate to Setup > Setting > Company Settings > Company Information and note down the Organization Name or Salesforce.com Organization ID.
Important
Under a single organization name, you can create one production and one sandbox instance only in the Netskope tenant.
In order to set up more than one Salesforce instance under the same organization name, Netskope recommends using the organization ID of the Salesforce instances as the instance name in the Netskope tenant.
Instance Type: Select the Security Posture checkbox. Select this option to allow Netskope to continuously scan through your SaaS app to identify and remediate risky SaaS app misconfigurations and align security posture with best practices and compliance standards.
Also, you have the option to run the policy at intervals (15 minutes, 30 minutes, 45 minutes, and 60 minutes).
Select the type of Salesforce account you want for Next Generation SSPM; production, or sandbox.
Note
Select the production account type if connecting a developer edition instance created in developer.salesforce.com. The sandbox account type is only intended for sandbox organizations, which are copies of production organizations and not the same as a Salesforce organization with a developer edition license.
Enter the email address of the Salesforce user that will grant access to Next Generation SSPM.
Note
The email address during instance setup should match the one provided during grant access.
Click Save, then click Grant Access for the app instance you just created. You will be prompted to log in with your admin username and password, and then click Grant. When the configuration results page opens, click Close.
Refresh your browser and you will see a green check icon next to the instance name.
Grant Failure Due To Login IP Range
The grant access may fail if the Salesforce username has any Login IP Ranges configured in Salesforce. Log in to your Salesforce account and verify if the user profile associated with the username has Login IP Ranges configured. If configured, follow the procedure below. The following procedure will ensure that the grant goes through successfully.
Log in to login.salesforce.com.
On the top right, click Setup > Setup.
On the left navigation pane, go to PLATFORM TOOLS > Apps > Connected Apps > Connected Apps OAuth Usage.
Beside the Netskope Introspection for Salesforce app, click Install.
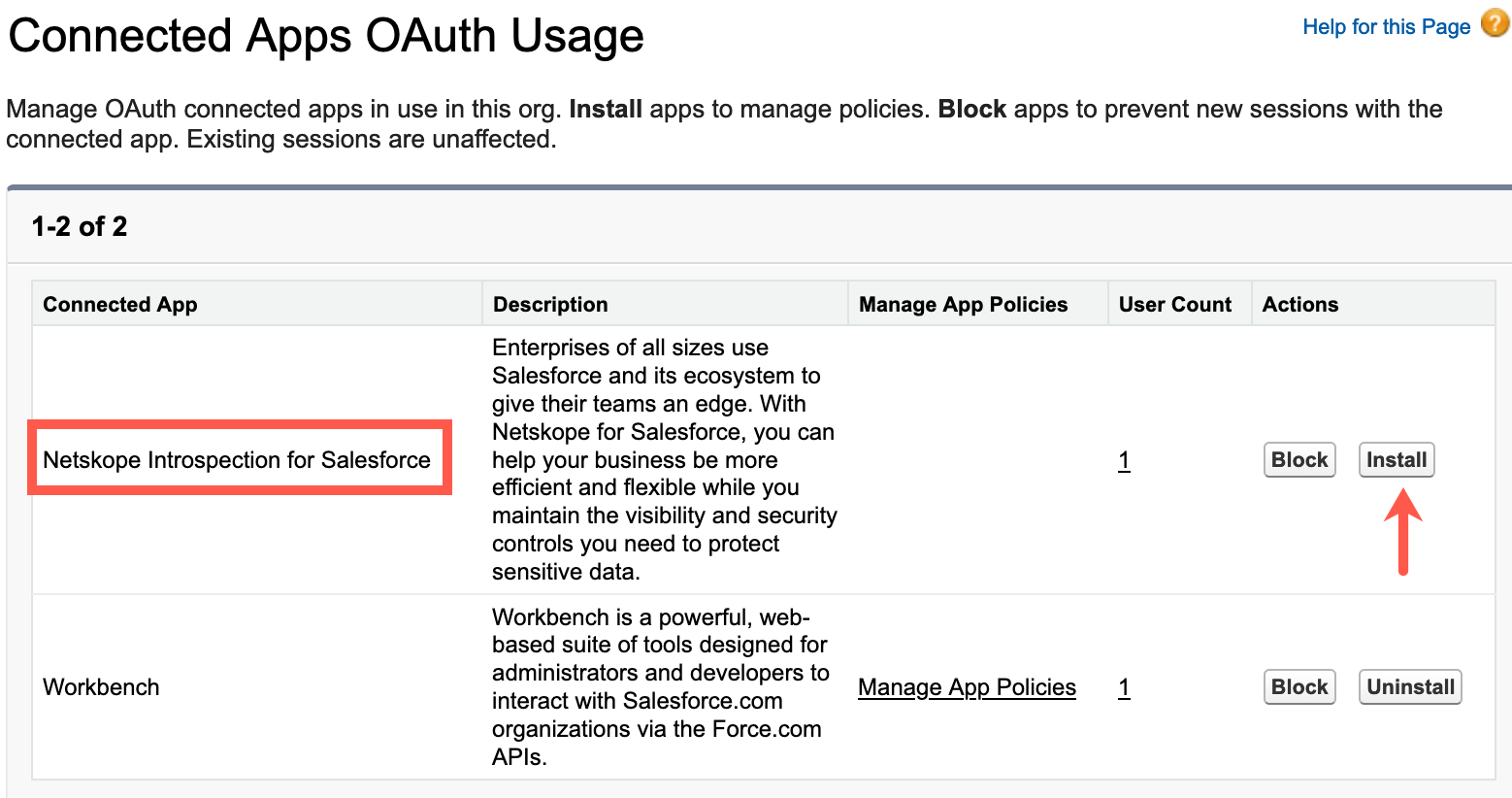
A new window opens. Click Install.
On the Netskope Introspection for Salesforce Connected app page, click Edit Policies.
Under OAuth Policies, set IP Relaxation to Relax IP restrictions.
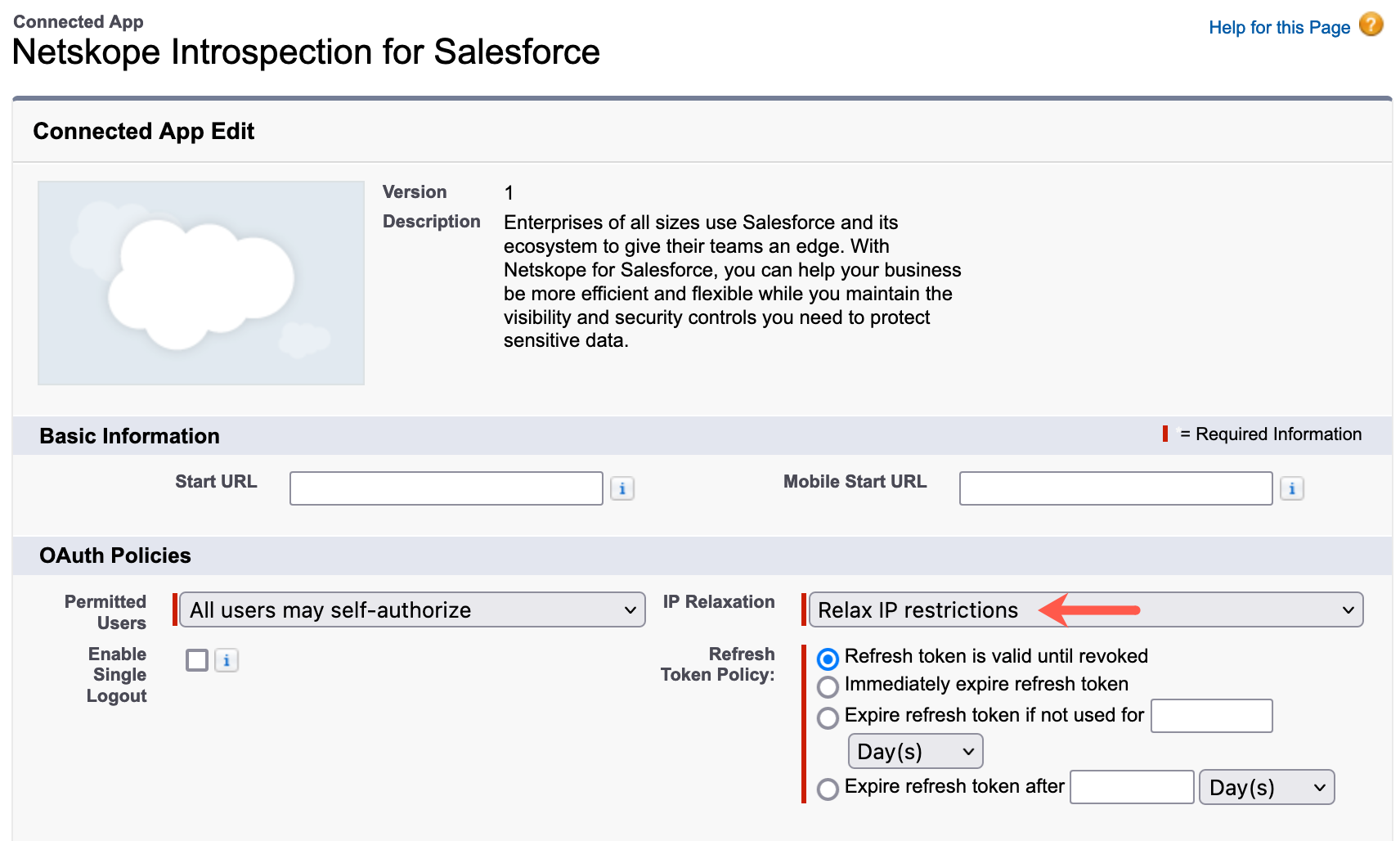
Click Save.
Log back in to your Netskope tenant and grant access to your Salesforce app.
The grant should go through successfully.
(optional) Post successful grant, you can rollback IP Relaxation to Enforce IP restrictions.
Netskope API Data Protection OAuth Refresh Token Policy
Once you have successfully granted access, the Salesforce administrator should ensure that the Netskope API Data Protection OAuth refresh token is valid until revoked. To do so:
Log in to login.salesforce.com.
On the top right, click Setup > Setup.
On the left navigation pane, go to PLATFORM TOOLS > Apps > Connected Apps > Manage Connected Apps.
Click the Netskope Introspection for Salesforce app.
Click Edit Policies.
Under OAuth Policies, set Refresh Token Policy to Refresh token is valid until revoked.
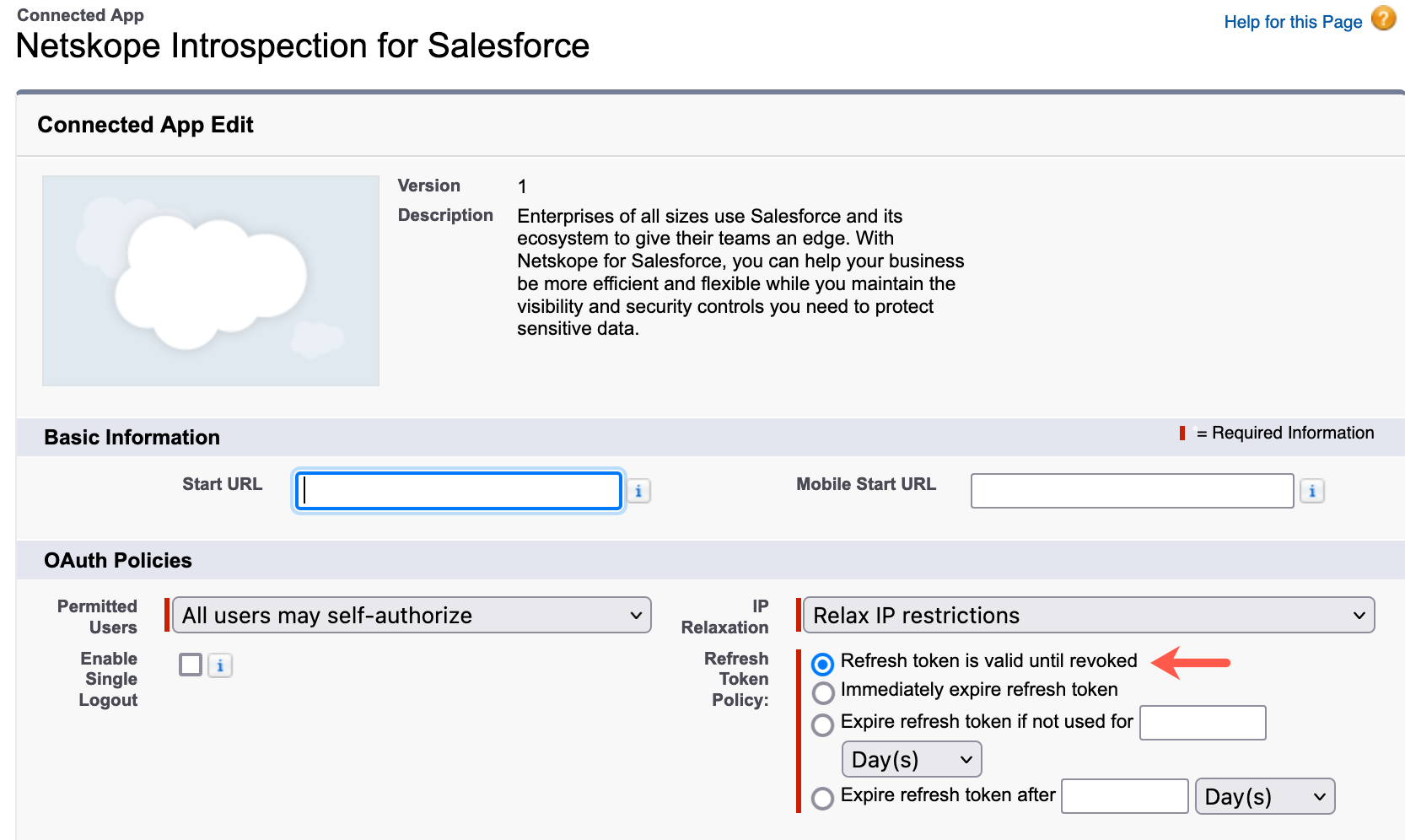
Click Save.
Next, you should configure a security posture policy. To do so, see Next Generation SaaS Security Posture Management Policy Wizard.