Best Practices for Real-time Protection Policies
The following sections walk you through the best practices of Real-time Protection and how to get the most out of your Real-time Protection policies.
Real-time Protection (Inline) vs API Data Protection (Out of Band) Policies
 |
Policy Placement
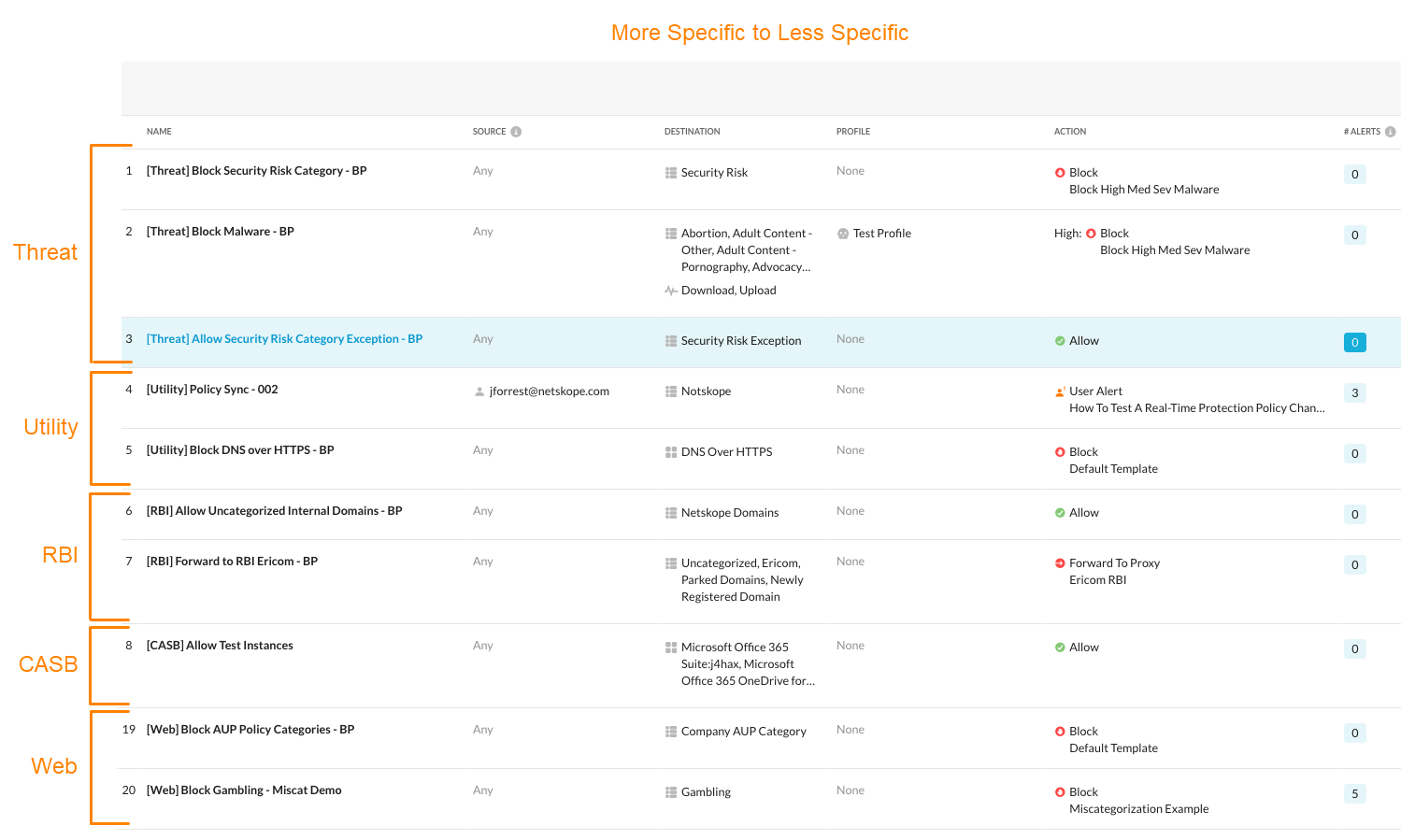
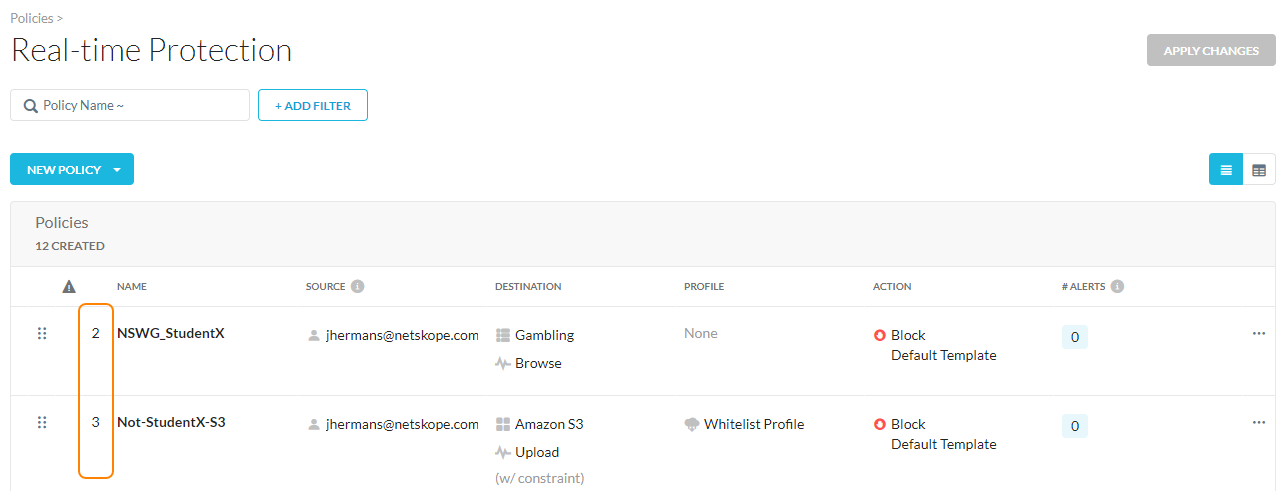
Understanding the order of your Real-time Protection policies is important:
Real-time Protection policies are processed sequentially (top to bottom).
When traffic matches rule conditions, the action (Allow/Block) applies without further processing through the rule base. All policies are terminal except for DLP policies set as Alert and Continue.
Select the rule position when saving the policy: top, bottom, before, and after.
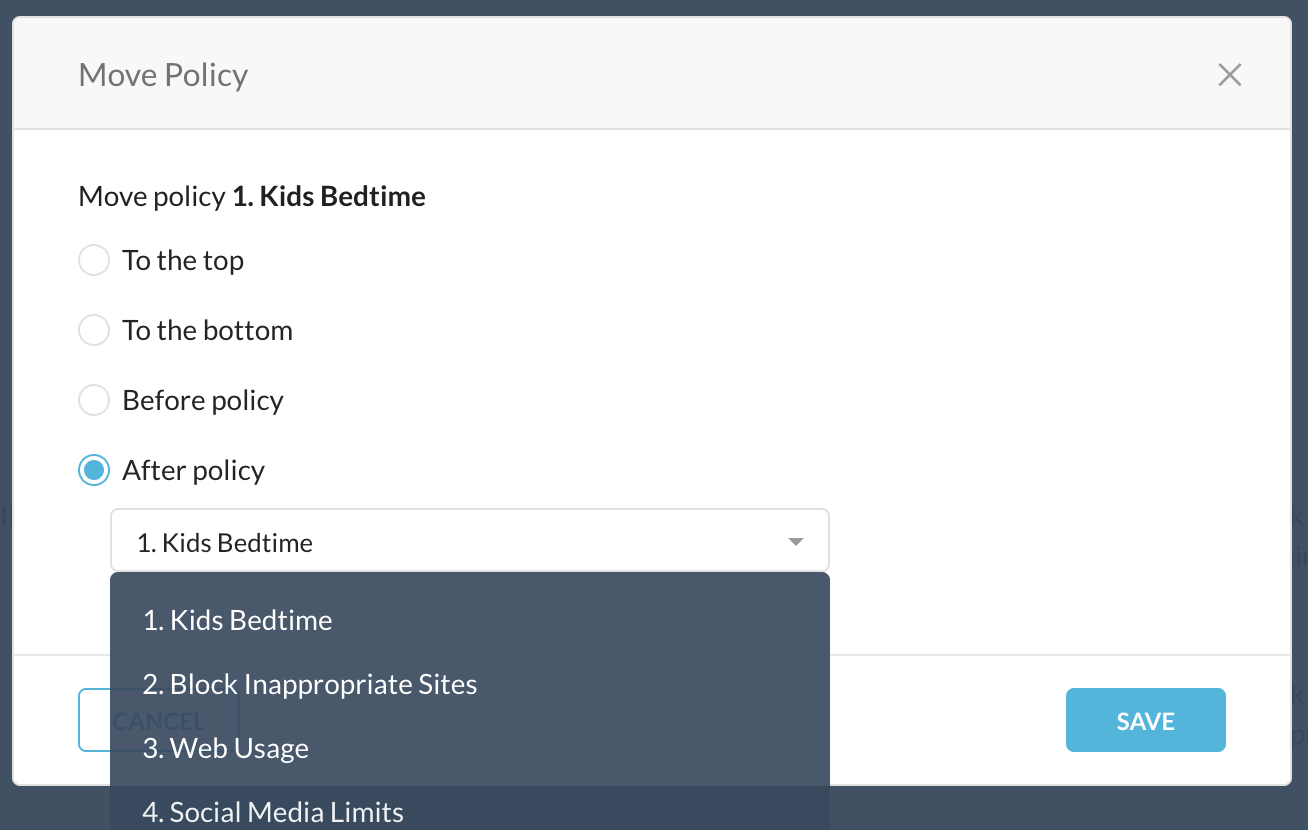 |
You can also drag and drop, or choose the policies to re-order.
Click Apply Changes to save the order.
Policy changes don't take effect until you apply changes.
General Guidelines
Rules are processed from the top-down in the Real-time Protection policies list.
Place any rules applied to individuals or small groups near the top of the list.
Place exceptions at the top for block policies.
Use the Filter option to view specific policies.
Netskope allows the activity by default if it doesn't match a policy.
Consider enabling dynamic URL classification. Dynamic URL classification looks at the textual contents of a page and dynamically determines the category for the uncategorized URLs. This feature is turned off by default. After a page has been dynamically categorized, the classification applies to all of your account instances. The page classification to a category expires every 12 hours, so if any changes occur to the page, the content is re-evaluated so the chosen category matches the current page content.
Allow list business critical applications.
Block list predefined high risk categories and IOCs.
Leverage the Netskope REST API to maintain URL lists.
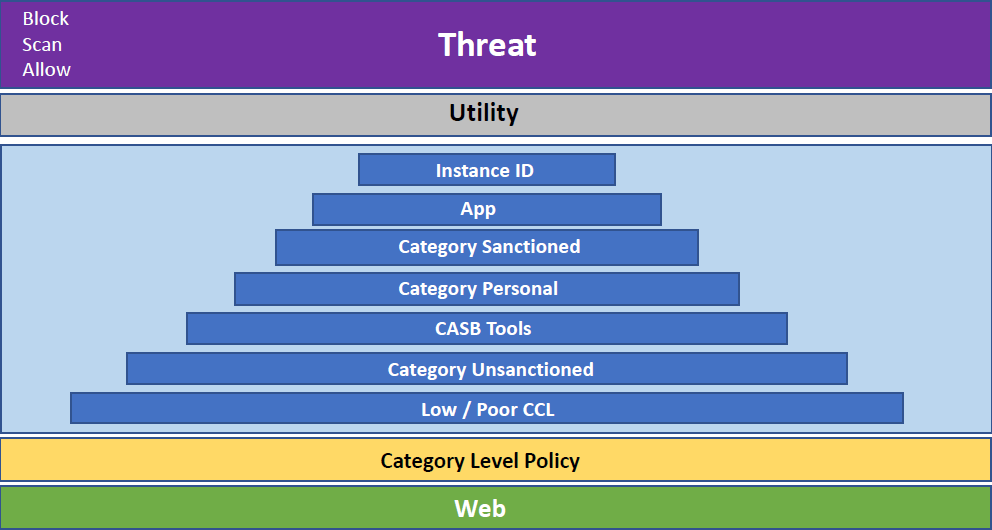
Structuring Real-time Protection Policies
Netskope recommends using Threat Protection policies to block high risk behaviors, such as downloading malware or uploading sensitive data to an unsanctioned application. Broader access control policies must be towards the bottom of the policy list.
Threat Protection (High risk)
Remote Browser Isolation (RBI)
CASB (Activity Oriented)
Web (Category Based)
Netskope Private Access (NPA)