Configure Okta SAML
Create a New App Integration
Log in to your Okta administrator console, and from the left-side menu go to Applications > Applications. Click Create App Integration.
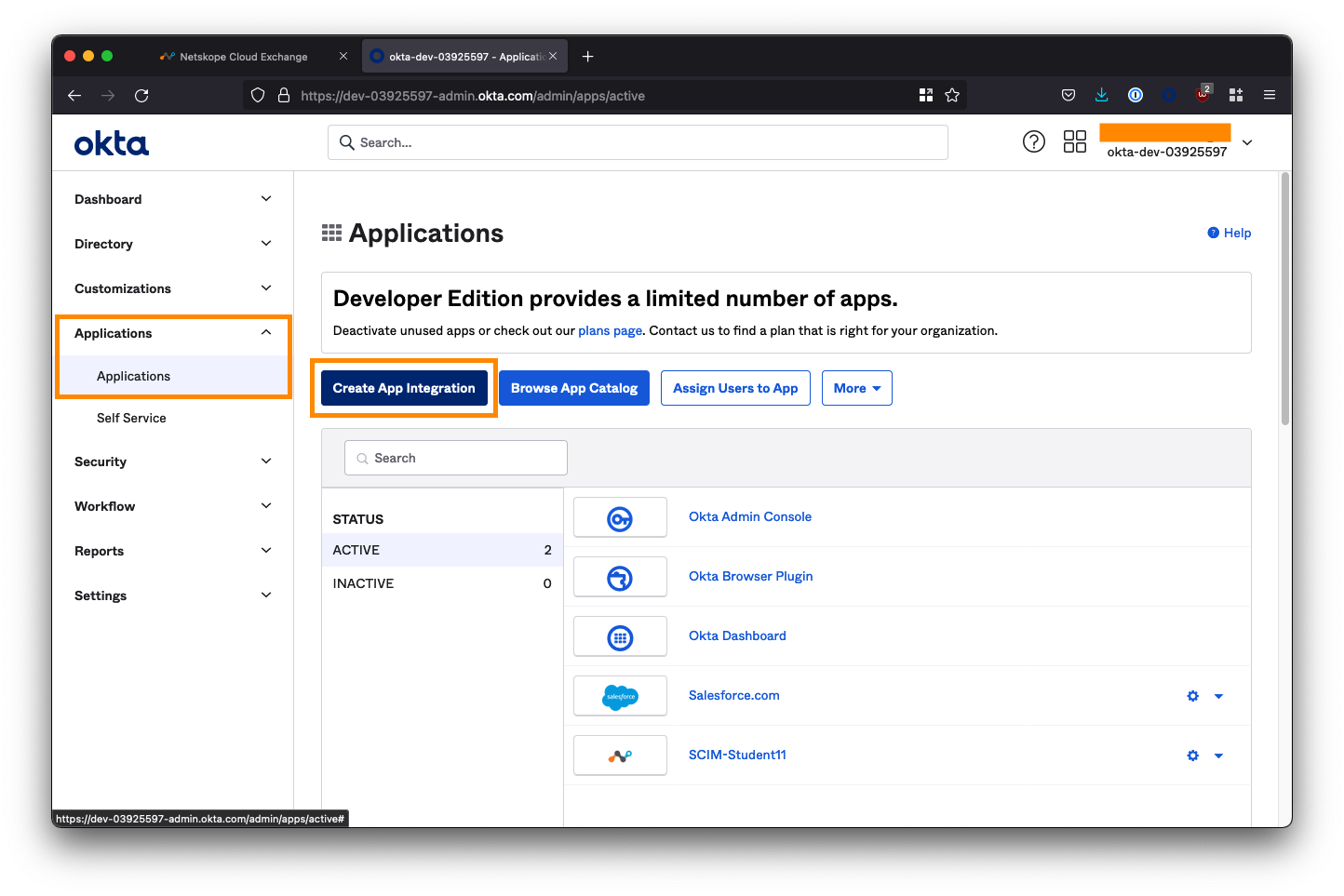
Select SAML 2.0 as the sign-in method and click Next.
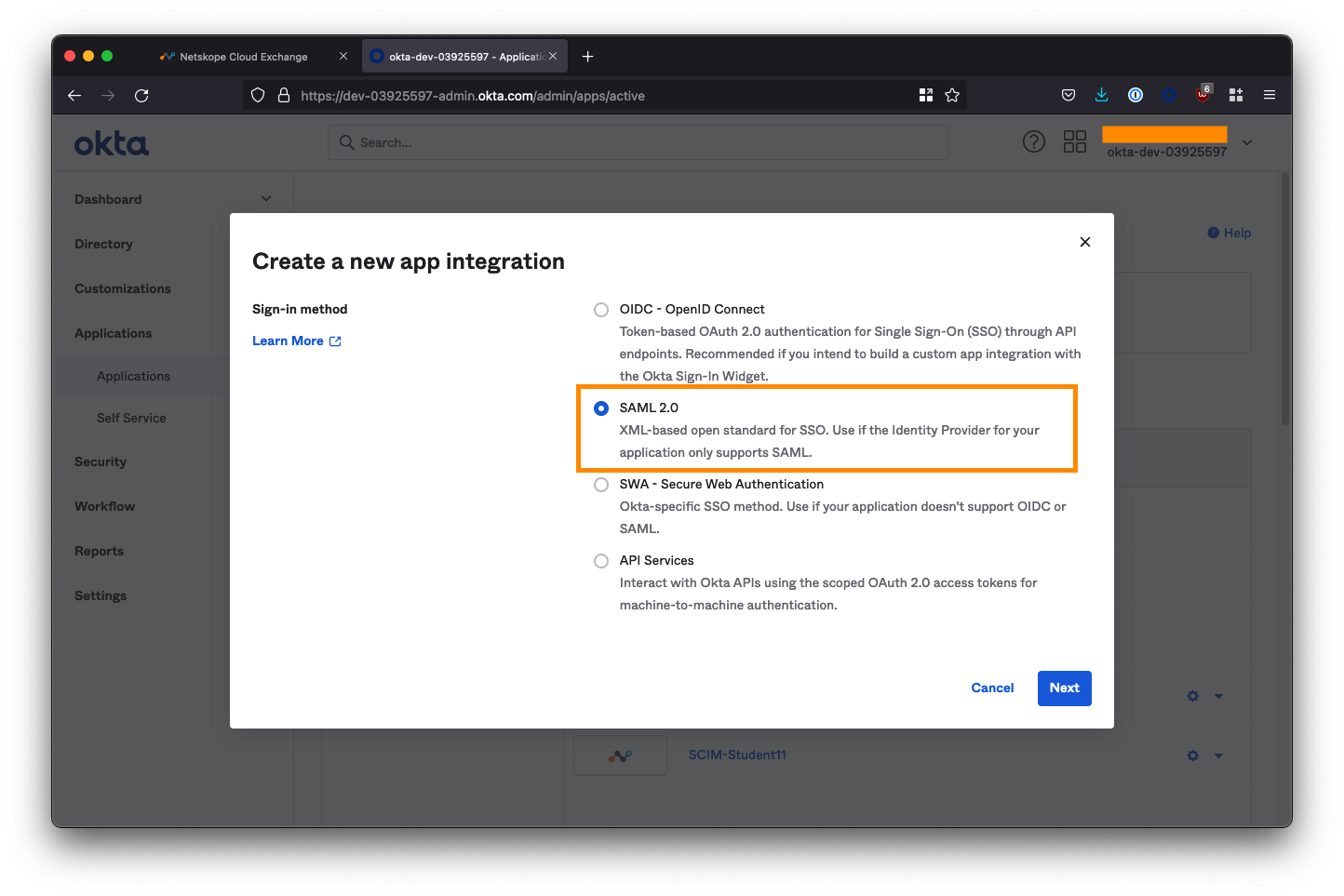
Name the application Apache Gucamole SSO and check both of the app visibility boxes to hide the app icon from users. Click Next.
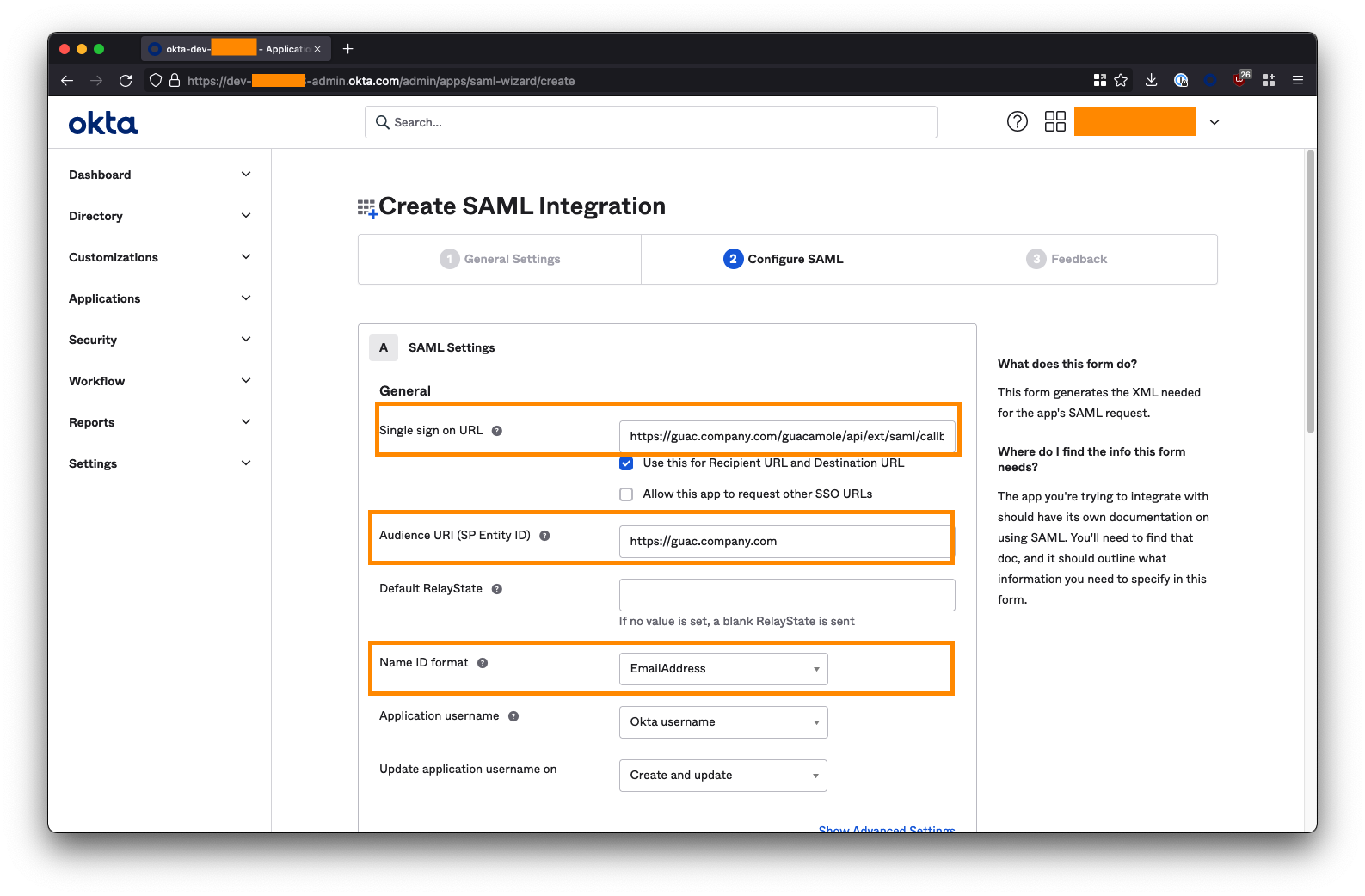
Under SAML Settings, enter the parameters for the following fields. Substitute
<fqdn-of- your-guacamole-instance>with the domain you wish to use to access the Guacamole UI. For example:guac.company.com.Single sign on URL:
https://<fqdn-of-your-guacamole- instance>/guacamole/api/ext/saml/callback. For example:https://guac.company.com/guacamole/api/ext/saml/callback **Audience URI (SP Entity ID):
https://<fqdn-of-your-guacamole- instance>For example:https://guac.company.com **Name ID format: Set this to EmailAddress.
Leave all the other fields blank or as their default values (Default RelayState, App username, etc).
Scroll down and click Next.
On the next page, check the box I’m an Okta customer adding an internal app and click Finish.
Go to the Sign On tab and click the View Setup Instructions button on the right side of the screen. You may need to scroll down.
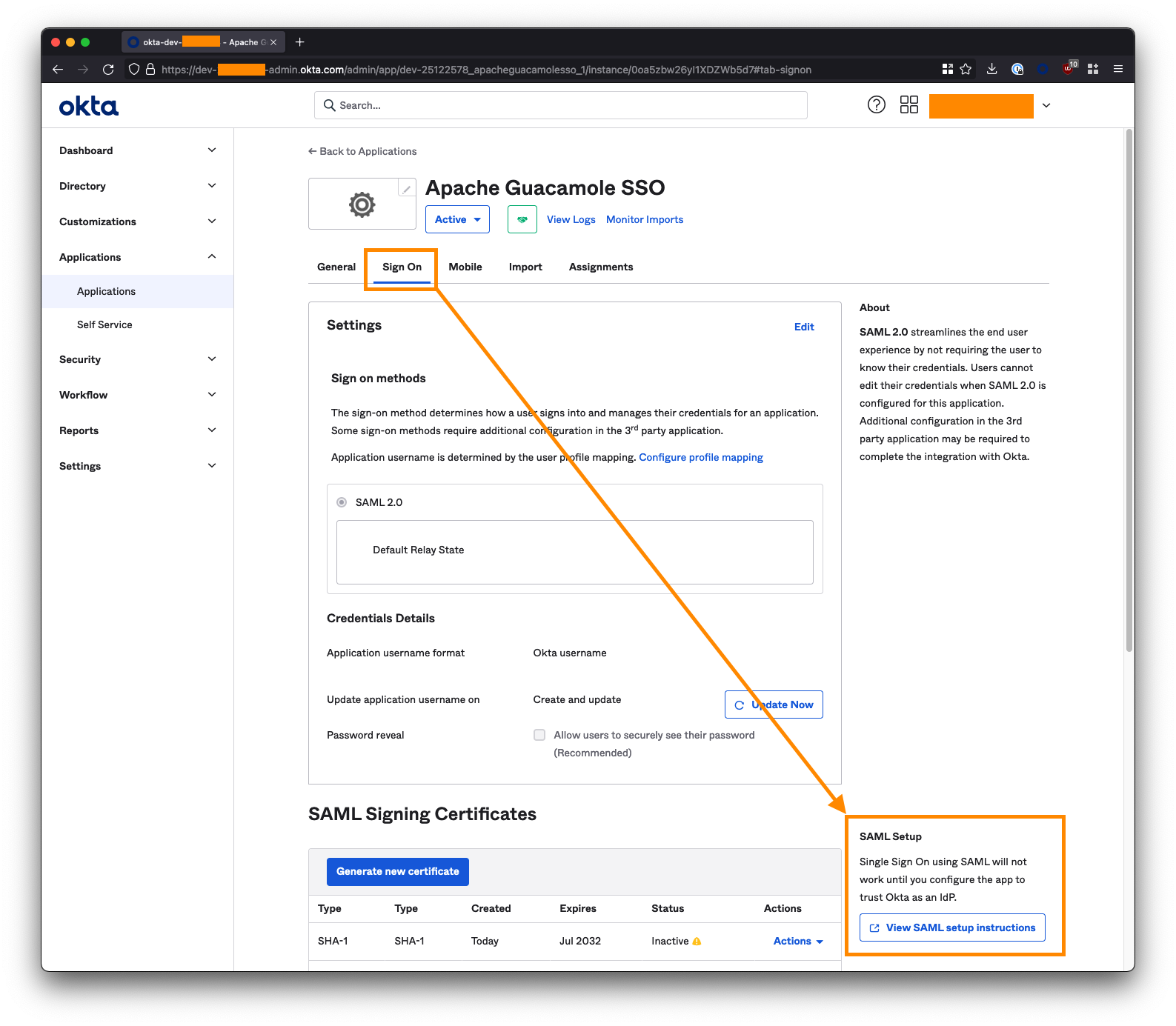
Extract your tenant ID and App ID from the Identity Provider Single Sign-On URL, which looks like this:
https://<tenant-id>.okta.com/app/<tenant-id>dev-01234567_apacheguacamolesso_1/<app-id>/sso/saml
For example, if your URL is:
https://dev-01234567.okta.com/app/dev-01234567_apacheguacamolesso_1/ezk5zbw26xt3cSSEC5d7/sso/saml
The tenant ID is
dev-01234567.The app ID is
ezk5zbw26xt3cSSEC5d7.Copy these into the below URL to form the Okta IdP Metadata URL:
https://<tenant-id>.okta.com/app/<app-id>/sso/saml/metadata
For example:
https://dev- 01234567.okta.com/app/ezk5zbw26xt3cSSEC5d7/sso/saml/metadata
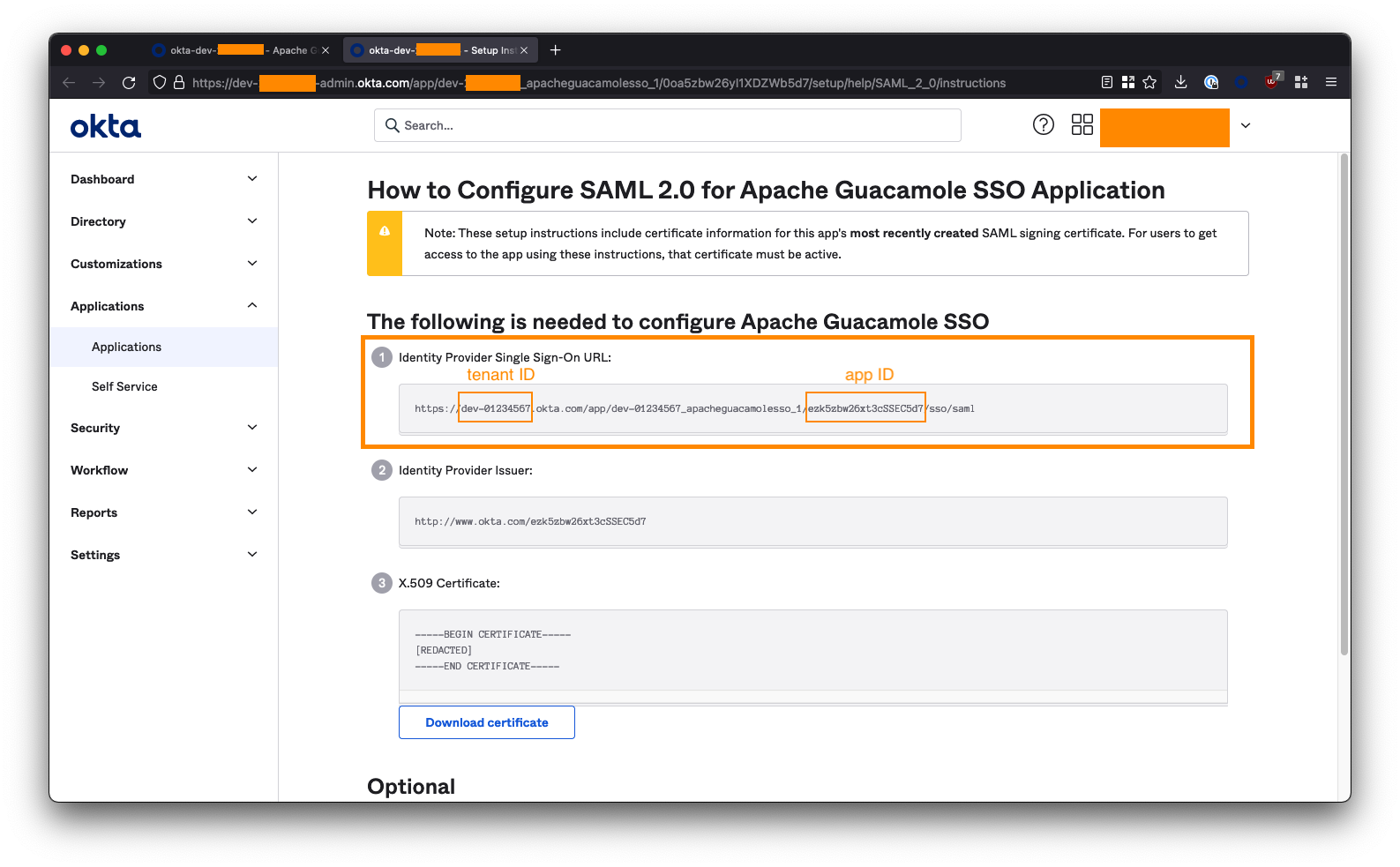
Copy this URL. You will need it to configure Guacamole later.
You will know your URL is correct if you visit it in your browser and it loads a bunch of XML:
The last step we need to perform in Okta is to assign users and/or groups to the Apache Guacamole SSO app to provide them with access. Any user or group added here will be permitted to SSO through to and access your Guacamole instance, so be careful!
Go to the Assignments tab within the Apache Guacamole SSO app. Use the Assign button to select either the individual users or groups that are permitted to access your Guacamole instance.
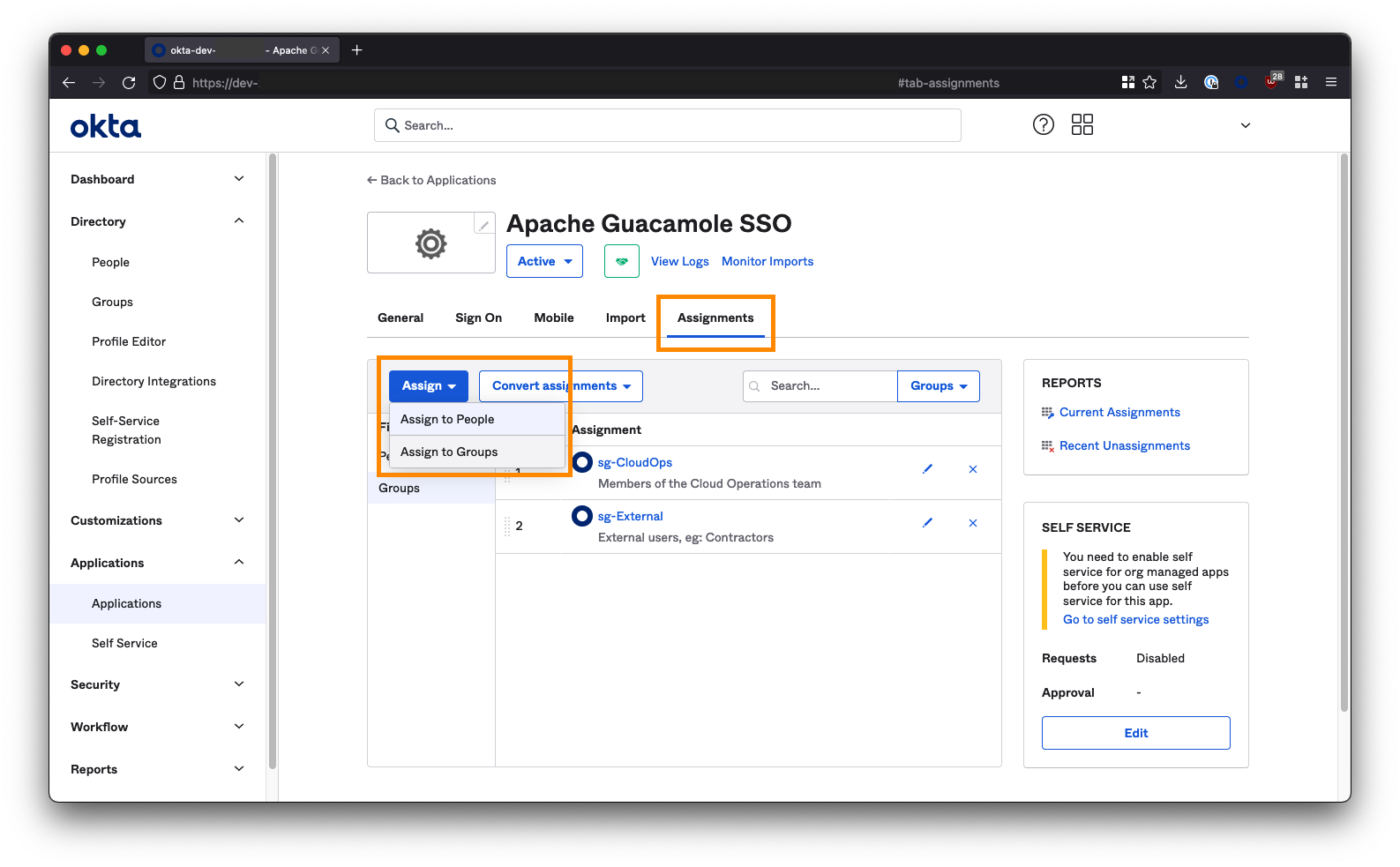
If you are deploying Guacamole to provide clientless access for 3rd parties/contractors to access internal resources via a ZTNA solution (like Netskope NPA), then you may want to create a group/security group specifically for these individuals and assign it to the Guacamole app. For example:
sg-External. Note down the groups you select here as these will be the same groups that you add to ZTNA policy later on..You’ve finished this configuration in Okta and can proceed to installing Guacamole.