Configure Google Drive for API Data Protection
Note
API Data Protection supports all editions of Google workspace i.e., basic, business, and enterprise. However, with basic edition, shared drives and Google Drive audit activities are not supported.
Important
If a user views a file immediately after uploading, Netskope receives the view event notification only, not the upload notification from Google Drive. This is a known issue in Google Workspace basic/limited account. Since this is a basic/limited account, Netskope skips the view event notification. This issue is not observed in Google Workspace enterprise/unlimited account.
Netskope does not get any notification when an internal user edits a file owned by an external user. In a nutshell, externally owned files are not audited by Google. This is a known limitation in Google Drive.
To configure Google Drive for API Data Protection, you need to authorize Netskope as a web application client to access your Google Drive instance.
An authenticated user must authorize all requests to the Google Drive API. Google Drive uses the OAuth 2.0 protocol for authenticating a Google account and authorizing access to user data.
There are two parts to this procedure:
Install Netskope for Google Apps from Google Marketplace
Configure Google Drive instance in Netskope UI
Important
Before installing the Netskope app for Google Apps, ensure that the Google Drive is available across all organization units of your google account. To check, log in to admin.google.com and then navigate to Apps > Google Workspace > Drive and Docs and ensure that Service status is set to ON for everyone.
Install Netskope for Google Apps from Google Marketplace
The administrator should install the Netskope app for API Data Protection with domain-wide delegation to allow access to all users in the organization.
Access this URL: https://workspace.google.com/marketplace/app/netskope/1055677045599.
Click Install.
Log in using the admin username and password.
Click Domain Install.
In the Domain wide install pop-up window, click CONTINUE.
The following pop-up window is displayed. For the Turn ON for drop-down menu, ensure that you select the primary domain. This ensures that the app is installed for the entire organization. Select the Terms of Service check box. Click Accept.
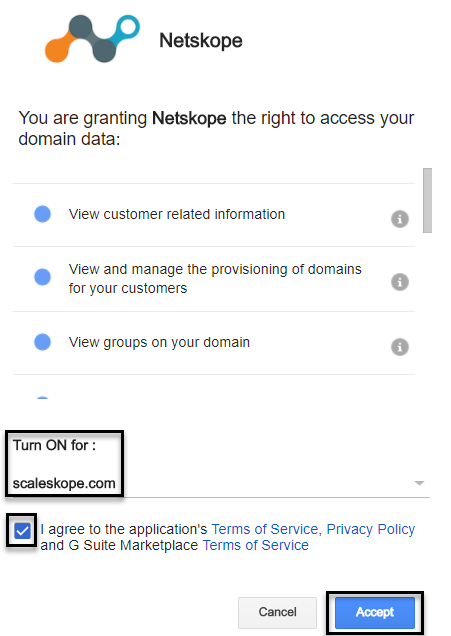
On successful installation of the app, the Netskope has been installed! message is displayed. The Netskope app installation is now complete.
Once the app is installed, ensure the following items:
The Netskope app is turned on for the entire organization. Log in to admin.google.com. In the home page, navigate to Apps > Google Workspace Marketplace apps. Look for the Netskope app and ensure that the Distribution is set to On for everyone.
The appropriate scopes are granted. You can check the scopes by logging into admin.google.com and on the home page, navigate to Apps > Google Workspace Marketplace apps. Look for the Netskope app and click it. The scopes are as follows:
Scope Name
Scope URL
Usage
Netskope Use Case
View customer related information
https://www.googleapis.com/auth/admin.directory.customer.readonly
View details (e.g., contact email, organization title etc) of customer
Not in use. To be deprecated.
View and manage the provisioning of domains for your customers
https://www.googleapis.com/auth/admin.directory.domain
Provision and delete domain aliases for your customers Provision and delete multi-domains (secondary domains) for your customers
Read all managed domains used in user listing, calculating exposure of the shared file.
View groups on your domain
https://www.googleapis.com/auth/admin.directory.group.readonly
View details (e.g., name, members) and metadata (e.g., login details) of groups on your domain
If Team Drive has a group, then get active internal member of the group for doing all the API calls.
View organization units on your domain
https://www.googleapis.com/auth/admin.directory.orgunit.readonly
View metadata (e.g., name and description) of organization units
Not in use. To be deprecated.
View and manage the provisioning of users on your domain
https://www.googleapis.com/auth/admin.directory.user
Provision and delete users on your domain View and modify details (e.g., name, address, and phone number) and metadata (e.g., login details) of users on your domain
List all users, get details of a user.
Manage data access permissions for users on your domain
https://www.googleapis.com/auth/admin.directory.user.security
View and manage data access permissions for users on your domain
Get details of third party apps and plugins installed by users (google app ecosystem).
View audit reports for your G Suite domain
https://www.googleapis.com/auth/admin.reports.audit.readonly
View audit reports of admin and user activity in your G Suite domain (e.g., password change events and document view events)
Poll audit events of Google Drive, administrator, login, mobile, and calendar. Webhooks subscription for Google Drive events of enterprise Google Suite accounts.
See, edit, create, and delete all your Google Drive files
https://www.googleapis.com/auth/drive
This app wants permission to access everything in your Google Drive. It will be able to do the same things you can do, including see your files , upload and download your files, delete your files, see the names and emails of people you share files with, share and stop sharing your files with others, remove people from your files, organize your drive.
Get Google Drive events like Team Drive details, file metadata, download, file sharing details etc.
View and modify but not delete your email
https://www.googleapis.com/auth/gmail.modify
View and modify your mail in Gmail. May move mail to Spam/Trash but not instantly delete forever Create, update, and delete labels Compose and send new email View your settings (e.g., filters and labels)
Not in use. To be deprecated.
View your email messages and settings
https://www.googleapis.com/auth/gmail.readonly
View your email messages Search your email messages View your settings (e.g., filters and labels)
Read email metadata, email details etc.
View your email address
https://www.googleapis.com/auth/userinfo.email
View the email address associated with your account
Grant the instance for Gmail, Google Drive.
See your personal info, including any personal info you've made publicly available
https://www.googleapis.com/auth/userinfo.profile
This app wants permission to see your full name, see your profile picture, see your gender, see your preferred languages, and see any other information you have made publicly available.
Grant the instance for Gmail, Google Drive.
Create a Custom Admin Role for Netskope
If you do not plan to use the Google super admin account, you can create a custom admin role and assign the role to a user to grant access to API Data Protection.
You can grant privileges/scopes for the Netskope app either using the default Google super admin role or by creating a custom admin role exclusively for the Netskope app. This section describes the steps to create a custom admin role for Netskope.
Log in to admin.google.com.
Click the triple bar on the top-left corner of the home page and navigate to Account > Admin roles.
Click Create new role.
Enter a name and description for the role and click CONTINUE.
Select privileges for the role:
Important
Netskope does not recommend to remove the following privileges. Any removal may result in failure of API calls and policy processing.
Admin Console Privileges:
The admin console privileges are automatically assigned when a new role is created in Google Workspace. The level of access provided to this role in the admin console depends on what permissions are provided for this role. Here is a list of privileges Netskope requires:
Table 11. Google Admin Console PrivilegesPrivileges
Needed for
Organizational Units > Read
This privilege is required to read the organization units (OU) in the Google account.
Users > Read
This privilege is required to list the users in the Google account.
Services > Drive and Docs > Settings
This privilege is required to get all file-based notification activities.
Security > User Security Management, Security Settings
This privilege is required to access the directory service and to list apps installed on the Google account.
Domain Settings
This privilege is required to read domains.
Reports
This privilege is required for webhook subscription and polling changes.
Admin API Privileges:
The admin API privileges are required to make any API calls.
Table 12. Google Admin API PrivilegesPrivileges
Needed for
Organizational Units > Read
This privilege is required to list users across multiple domains/OUs.
Users > Read
This privilege is required to list users.
Groups > Read
This privilege is required to read group information that users are assigned to.
User Security Management
This privilege is required to access the directory service and to list apps installed on the Google account.
Data Transfer
This privilege is required to perform the "change owner" policy action.
Domain Management
This privilege is required to determine internal/external domains which are then used in exposure calculation.
Click CONTINUE, and then click CREATE ROLE.
Once you have created the custom role, you can assign the role to a user. The user can then authorize Netskope to grant access to your Google Drive instance.
Possible Permission Errors and Solutions
Access to Google Workspace data via API is Restricted
Symptom: Google Workspace does not allow file listing or other file operations via API.
Back end error message: HTTPError403 when requesting https://www.googleapis.com/drive/v2/files?alt=json returned "The domain policy has disabled third-party Drive apps"
Solution: Under Admin Console, navigate to Apps > Google Workspace > Drive and Docs > Features and Applications, verify that the Drive SDK option is set to ON.
Unauthorized app or scopes for Netskope
Back end error message: AccessTokenRefreshError: unauthorized_client: Client is unauthorized to retrieve access tokens using this method
Solution: Under Admin Console, navigate to Apps > Google Workspace Marketplace apps, verify that the Netskope app has all the required scopes. In case any scope has the “Read-only” scope instead of “Read-write” scope, modify the scopes accordingly.
Invalid credentials
Symptom: Google Workspace does not allow users to access Google Drive directly or via API.
Back end error message: HttpError 401 when requesting https://www.googleapis.com/drive/v2/files?alt=json returned "Invalid Credentials"
Solution: Under Admin Console, navigate to Apps > Google Workspace > Drive and Docs, ensure that the Service Status is set to ON for everyone for all and specific organization units.
Note
You should enable the Service Status for all organization units as well specific organization units where the groups/users reside. If this option is not enabled for all and/or specific OUs, Netskope cannot access Google Drive activities for groups/users residing under these OUs.
Ensure that the user has an active Google Drive license.
Configure Google Drive Instance in Netskope UI
To authorize Netskope to access your Google Drive instance:
Log in to the Netskope tenant UI:
https://<tenant hostname>.goskope.comand go to Settings > API-enabled Protection > SaaS .Select the Google Drive icon, and then click Setup Instance.
The Setup Instance window opens.
Instance Name: Enter the top-level domain name of your Google organization. To know your top-level domain, log in to admin.google.com. On the admin console, navigate to Domains > Manage domains. The Primary Domain is the top-level domain.
Instance Type: Select the appropriate features from the following options:
API Data Protection: Select this option to allow Netskope to scan through your SaaS app instance to list files, user, and other enterprise data.
Quarantine: Select this option to quarantine a file if a user uploads a document that has a DLP violation. This moves the file to a quarantine folder for you to review and take appropriate action (allow the file to be uploaded or block the file from being uploaded). For more information to set up quarantine, see Quarantine Profile.
Legal Hold: Select this option if you would like to preserve all forms of relevant information when litigation is reasonably anticipated. You can choose to have a copy of the file saved for legal purposes if it matches policy criteria. For more information to set up legal hold, see Legal Hold Profile.
Malware: Select this option to detect malware in files, emails, attachments, chat messages, posts etc. For more information to set up malware, see Creating a Threat Protection Policy for API Data Protection.
Forensic: Select this option to apply a forensic profile that flags policy violations and then stores the file in a forensic folder. For more information to set up forensic, see Forensics.
In Enter the email address of the admins for Google Data Transfer, enter the email address of the super admin or a user with custom role (see Create a Custom Admin Role for Netskope). The email address should have full access privileges to the following APIs:
The Data Transfer API, required to transfer data from one user to another within a domain: https://www.googleapis.com/auth/admin.datatransfer
In Enter email address of the admins for Google Directory, enter the email address of the super admin or a user with custom role (see Create a Custom Admin Role for Netskope). The email address should have full access privileges to the following APIs:
The Directory API, required to list users: https://www.googleapis.com/auth/admin.directory.user
The Security API, required to list third-party apps, like Google App Ecosystem: https://www.googleapis.com/auth/admin.directory.user.security
The Domain API, required to list all internal domains of an instance: https://www.googleapis.com/auth/admin.directory.domain
In Enter email address of the admins for Google Drive, enter the email address of the super admin or a user with custom role (see Create a Custom Admin Role for Netskope). The email address should have full access privileges to the following APIs:
The Drive API, required to list files: https://www.googleapis.com/auth/drive
In Enter email address of the admins for Google Reports, enter the email address of the super admin or a user with custom role (see Create a Custom Admin Role for Netskope). The email address should have full access privileges to the following APIs:
The Reports API, required for generating Audit Skope IT events: https://www.googleapis.com/auth/admin.reports.audit.readonly
Note
If different email addresses are specified for each email address field, ensure that each email address has the appropriate privileges. To know more about the privileges, see Create a Custom Admin Role for Netskope.
Click Save , then click Grant Access for the app instance you just created. You will be prompted to log in using a super admin or a user with custom role and password, and then click Grant. When the configuration results page open, click Close .
Note
Netskope requires you have an active Google Drive license before granting access.
If different email addresses are specified for each address field, only the Google Directory API email address can grant access.
Refresh your browser and you will see a green check icon next instance name.
The list of users and files associated with your Google Drive domain appear once the connection is established between the Netskope API connector and the Google Drive API for your domain. Features such as File and User listings are not populated in real-time. They are populated at the configured time intervals. However, running policies on files and folders are populated in real time.
Change in Google Drive Forensic Folder
Google has enforced the following folder limit in Google Drive:
Any single folder in Google Drive which is not in a shared drive can have a maximum of 500,000 items placed within it. This limit does not apply to the root folder of 'My Drive'.
For more information on folder limits, refer to Folder limits in Google Drive.
In order to integrate with this change, Netskope has introduced an automatic sharding of forensics folders, such that a new folder is created every day with the name format Netskope Forensic Folder - <current date hash>. All subsequent forensics incidents will be stored under this folder with a new folder created every subsequent day.
Frequently Asked Question
- 1. What happens when this feature is released?
- 2. What happens to the older forensics and older forensics folder if the above is the case?
- 3. Does the customer need to take any explicit action to use this feature?
1. | What happens when this feature is released? |
After release 80 deployment, there are two scenarios:
| |
2. | What happens to the older forensics and older forensics folder if the above is the case? |
There is no change to the existing older folders and forensics data and they continue to exist as it was present earlier. | |
3. | Does the customer need to take any explicit action to use this feature? |
Customer does not need to take any action. |
Change Ownership Behavior in Google Drive
In Google Drive, when you change ownership of a folder, it changes the ownership of the selected folder only and does not include the files inside. For example, if you change the ownership of a folder from user A to user B:
the ownership of the folder changes to user B.
the ownership of the contents of the folder i.e., files and folders does not change to user B. It remains with user A.
This is how Google handles change in folder ownership.
Google Drive Connected Apps and Plugins
Google App Ecosystem lists the apps that are installed in the domain using an OAuth 2.0 token. In previous releases, Netskope identified these apps and described them using a CCI score, scope used, and app type. From release 48 on wards, users can create policies to revoke apps based on specific criteria. This feature allows creation of policies on third-party apps displayed in Google App Ecosystem. Policies may be based on an app ID, scopes used, CCI score, and more. Users may also create a list of apps that may be included or excluded from a policy trigger. App revocation can be done for all or selected users who have installed the app.
Google Team/Shared Drive Support
Netskope supports Google Team/Shared Drive. Google Team/Shared Drive is available for business and enterprise accounts only. The salient features are:
Track content shared within team/shared drives and externally.
Scan files for sensitive content based on team/shared drive policies (including retroactive and ongoing policies).
Monitor activity in the organization's team/shared drives.
Support audit logs for team/shared drive events.
You can configure a Google team/shared drive policy from the the Policies > API Data Protection > SaaS page.
Important
For Team/Shared Drive folders to populate on the policy wizard page of API Data Protection, ensure that the Team/Shared Drive folders are in active state. To check, log in to admin.google.com and then navigate to Apps > Google Workspace > Drive and Docs > Manage shared drives and ensure that the Team/Shared Drive folders are in active state.
Ensure that one of the team/shared drives' member has a managers' role. This is required to scan and list Team Drive files, ongoing and retroactive API Data Protection policy scans.
Ensure that the manager has an active Google Workspace Business or Enterprise license.