View Security Posture Compliance
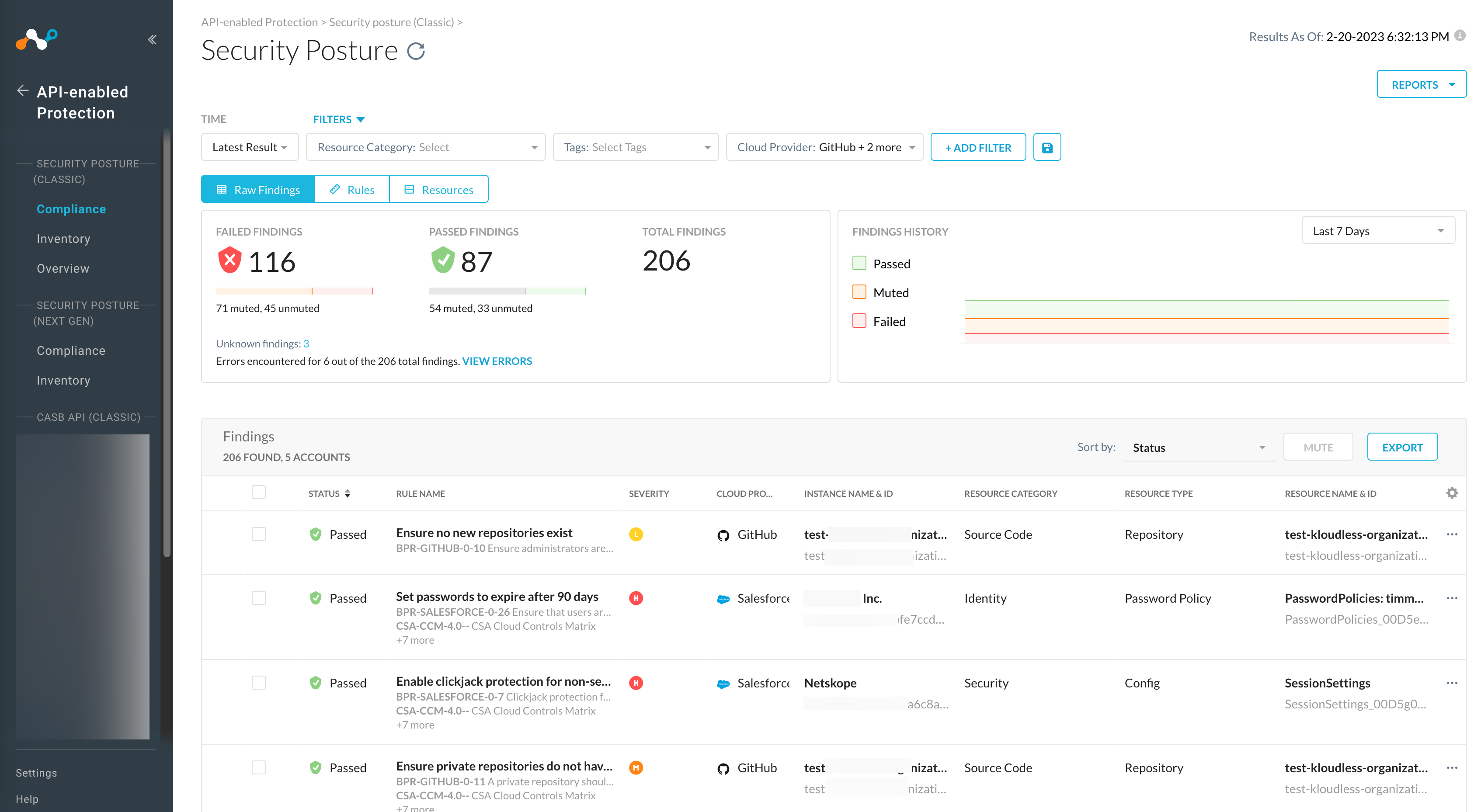
Netskope SaaS Security Posture Management (SSPM) and Cloud Security Posture Management (CSPM) continuously audit all the SaaS and IaaS resources to identify compliance rule violations. The Security Posture page provides the status of the checks on all the compliance rules and, SaaS and IaaS resources. To view the Security Posture page, go to API-enabled Protection > Security Posture (Classic) > Compliance in the Netskope UI.
You can refresh the page and the Result As Of label shows the date and local time.
You can toggle between Raw Findings, Rules, and Resources to view the audit results.
To export the table as a CSV file, click Export. You can choose which columns are shown by clicking the gear icon and enabling specific columns.
Click the Raw Findings tab to view the compliance findings of your rules and resources. This page provides an aggregated list of all the rules and resources that have failed, passed, remediated, and muted. You can view data for the last 7, 30, 60, and 90 days. You can select the check box beside a rule or select multiple check boxes and mute or unmute rule(s). Click a rule name to get a detailed view of the rule. The Raw Findings tab displays the following information:
Has Error: Rules that have errors.
Status: Status of the rule when checked against the resource. If the resource contains rule violations, the rule status shows Failed.
Profile: The name of the profile against which the rule is checked.
Policy: Name of the security posture policy.
Severity: The level of severity of the violation. There are four levels: Critical, High, Medium, and Low.
Cloud Provider: The cloud service provider. Netskope provides security for Amazon Web Services, Microsoft Azure, Google Cloud Platform, Microsoft 365, GitHub, Salesforce, ServiceNow, Workday, and Zoom.
Instance Name & ID: Name of the SaaS account instance and ID.
Region Name: The location of the account.
Resource Category: The SaaS resources category.
Resource Type: The cloud resource type.
Failing Since: The date since the rule is failing.
Muted: Status if the rule-resource pair is muted.
Compliance Standard: Gives a brief description of the compliance standard.
Click the Rules tab to view information on rules compliance. The Rules tab displays the following information:
With Errors: The total number of rules with errors.
Rules Failed: Total number of compliance rules that failed against a resource.
Rules Passed: Total number of compliance rules that passed against a resource.
Total Rules: Total number of compliance rules checked against a resource.
Status: A rule can be checked against multiple resources. The status of the rule is defined as follows:
if all resources pass, the rule passes.
if any resources fails, the rule fails.
if all resources are unknown, the rule is unknown.
Name: The compliance rule name.
Severity: The level of severity of the violation. There are four levels: Critical, High, Medium, and Low.
Resource Category: The SaaS resources category.
Resource Type: The cloud resource type.
Cloud Provider: The cloud service provider. Netskope provides security for Amazon Web Services, Microsoft Azure, Google Cloud Platform, Microsoft 365, GitHub, Salesforce, ServiceNow, Workday, and Zoom.
# Failed Resources: Total number of resources that failed the compliance rule.
# Unknown Resources: Total number of unknown resources.
# Passed Resources: Total number of resources that passed the compliance rule.
# Total Resources: Total number of resources checked against a compliance rule.
Click the Resources tab to view information on the SaaS resources. The Resources tab displays the following information:
With Errors: The total number of resources with errors.
Status: Status of the resource when checked for compliance. If the resource contains rule violations, the resource status shows Failed.
Name: The resource name.
Region: The location of the account.
Resource Category: The SaaS resources category.
Resource Type: The cloud resource type.
Cloud Provider: The cloud service provider. Netskope provides security for Amazon Web Services, Microsoft Azure, Google Cloud Platform, Microsoft 365, GitHub, Salesforce, ServiceNow, Workday, and Zoom.
Account: The account name of the SaaS service.
# Failed Rules: The total number of compliance rules that failed against a resource.
# Unknown Rules: Total number of rules which could not be evaluated for the resource.
# Passed Rules: The total number of compliance rules that passed against a resource.
# Total Rules: The total number of compliance rules checked against a resource.
Filters
By default, the Raw Findings, Rules, and Resources tabs display the latest audit results. You can choose to view the results for a specific date.
To filter your view by a specific date,
Click the Time drop-down to select Latest Result or As of Date to select a specific date.
Specify the date and time in the date picker. Click Apply.
You can filter the results displayed on the page by selecting Resource Category, Tags, and Cloud Provider. To further narrow the results on the page, click Add Filter and select an option from the list.
You can choose to filter based on the following options:
Status: Select Failed, Passed, or Unknown.
With Error: Select Yes or No.
Muted: Select Yes or No.
Last Remediation Status: Select None, Started, Completed, or Error.
Remediated By: Select Auto-remediation or On-demand remediation.
Rule name: Select Rule Name and enter a rule name in the search field.
Profile: Select a security assessment profile from the list.
Policy: Select security assessment policy from the list.
Severity: Select a severity level. There are four levels: Critical, High, Medium, and Low.
Compliance Standard: Select or search for a compliance standard. For example, NIST-CSF-1.1.
Resource Name: Select Resource Name and enter a resource name in the search field.
Netskope Resource ID: Select Netskope Resource ID and enter a resource ID in the search field.
Account: Select Account Name and enter an account name in the search field.
Region: Select Region and select a region from the list or enter the region in the search field.
Rule Detail
You can click on a rule in the rules table in the Rules or Raw Findings pages to view detailed information about the rule. The Rule Detail window provides a description of the rule.
The window contains the following three tabs,
Definition: The rule syntax defining the predefined or custom rule. Custom rules can be defined using Domain Specific Language.
Remediation: The remediation action to be performed to remediate the violation. Some rules also provide manual steps to remediate the violation.
Compliance: The various compliance standards that the rule satisfies. This tab provides the compliance standard, section, control, and description of the rule defined in the compliance standard's documentation.
Other: Displays the rule description, service the resource uses, and rule type; custom or predefined.
Reports
Use the Reports option to create a compliance report or to view existing reports.
Navigate to API-enabled Protection > Security Posture (Classic) > Compliance. On the top right, under Reports, select Create Compliance Report to build a custom template for your compliance reports and create a schedule to generate the reports. The Cloud Infrastructure Compliance Report page is displayed.
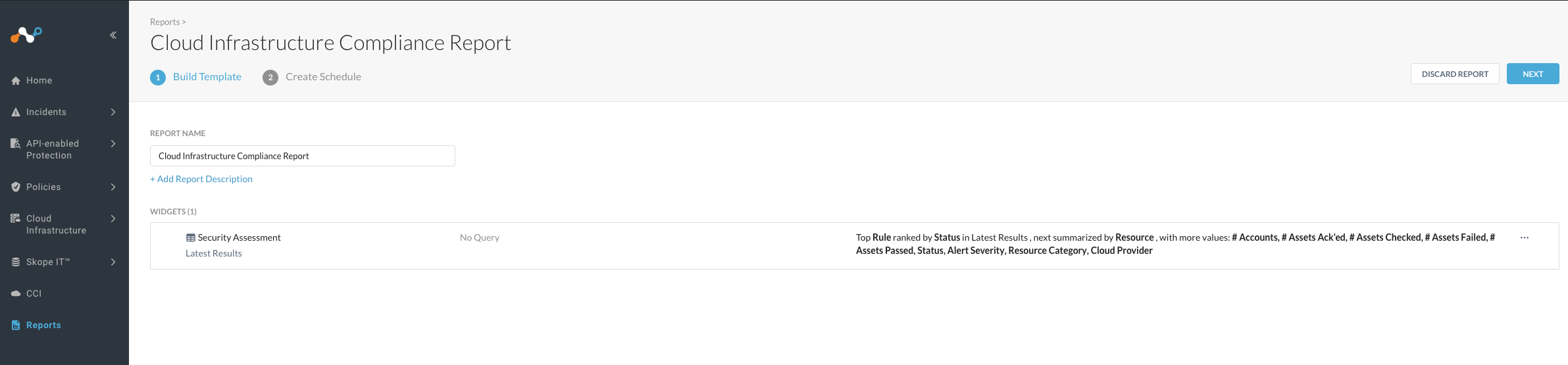
Under Build Template, provide a report name and description.
Click on the default Security Assessment widget. You can edit the name of the widget.
Under Query, select a cloud provider and add filters to query the compliance findings. When finished, click Save to save the query to the widget.
Click Next to create a reporting schedule.
Select the frequency and time at which the reports are to be generated.
Specify the users to be notified and select the output format as PDF or CSV or both. Click Create and then click Done.
The compliance report template is displayed in the Reports page. You can also view the Reports page from API Data Protection > Compliance > Security Posture, then click Reports > Go To Reports Page.
Manage Compliance Findings
You can mute failed assessments to indicate false positives or allow the DevOps team some time to remediate. The mute feature does the following:
Automatically acknowledges any alerts generated from an assessment. The alerts are muted indefinitely, until you unmute. This allows you to grant a DevOps team a window of time to remediate the service configurations to get compliant.
Excludes the failed resources (when muted) in computing the compliance score for a profile.
You can access the mute and unmute capabilities under API Data Protection > Compliance > Security Posture.
To mute a rule-resource pair,
Click on Raw Findings tab.
Click the More Options icon (...) to the right of the rule name and click Mute.
In the Mute window, select how long you want to mute this finding. You can add a short label under Justification Label to justify why you're muting this finding.
Click Mute.
Since every finding has a corresponding Skope IT alert, muting a finding auto acknowledges the corresponding alert. You will stop receiving alerts related to failed rule-resource pairs until you click Unmute.