Netskope Client for macOS
This document describes the various methods to install Netskope Client on a macOS device and how to configure and steer traffic to the Netskope Cloud.
Supported Versions
Refer to Netskope Client Supported OS and Platform to understand the supported versions for macOS.
Install Netskope Client
You can install Netskope Client in macOS using one of the following methods:
Email Invite
Using PLIST
MDM Deployment Options
Using Email Invite
You can install Netskope Client using the email invitation sent from the admin console. Click the download link and install Client on your device.
Important
Email invites are time-bound and can be used only by the intended user.
After you receive the email:
Check your email from Netskope Onboarding and click the link for Mac Client.
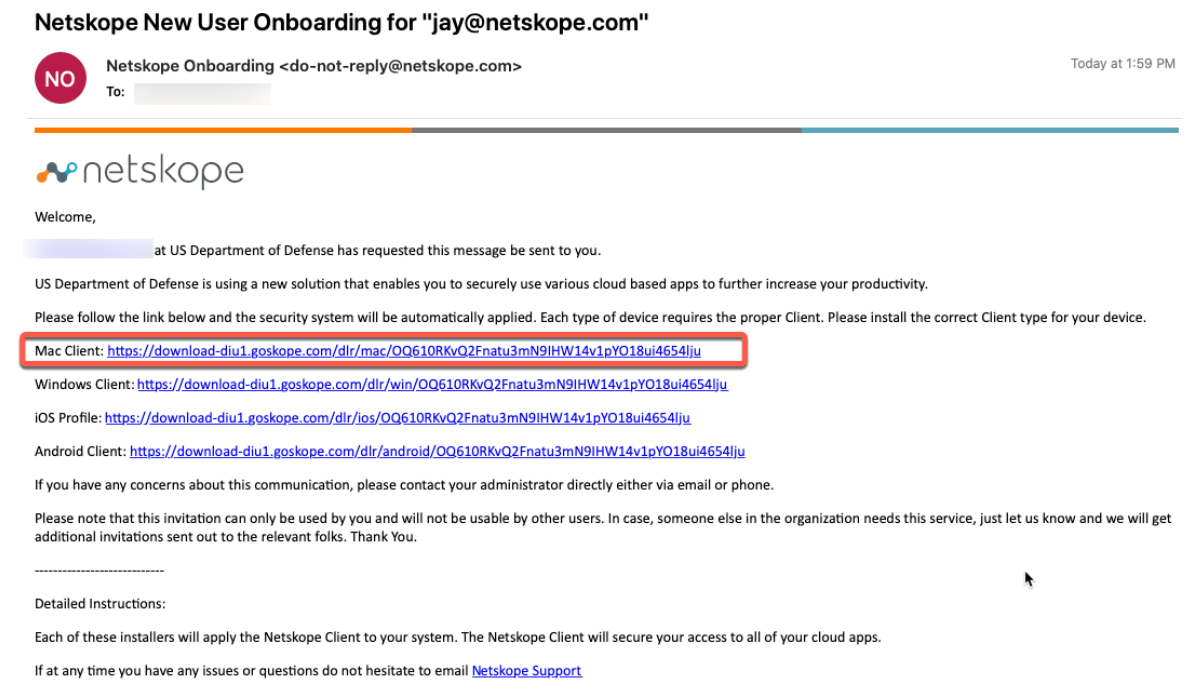
Click Download. This downloads to your default location.
Click the installer file.
Follow the steps as displayed in the Install Netskope Client window.
Once the installation is complete, you can see the Netskope Client running on your taskbar.
To learn more, view Email Invite.
Using PLIST
This method uses scripts and a PLIST to install Netskope client on macOS devices in single or multi-user mode. The steps include:
Generate .plist file.
Download script.
Generate .plist File
Run the following command in a terminal: sudo /usr/libexec/PlistBuddy -c "add email string user@example.com" /Library/Managed\ Preferences/template.plist
Generate Script
Download the configuration script from Netskope Support portal. The file contains the essential command-line executable scripts to install and configure the client.
Extract the contents of the MAC-MDM-script.zip file.
Execute this command in Terminal: sudo ./macmdmscript.sh 0 0 0 addon-< tenantname >.goskope.com < OrgID > < plist file name > <preference_email >
Other Deployment Methods
Netskope currently supports following deployment options for macOS:
Uninstall Client In macOS
To uninstall Client in macOS:
Click the Spotlight icon from your dock or the magnifying glass on the top of your taskbar.
Enter Remove Netskope.
You will be prompted to enter your administrative credentials at this point.
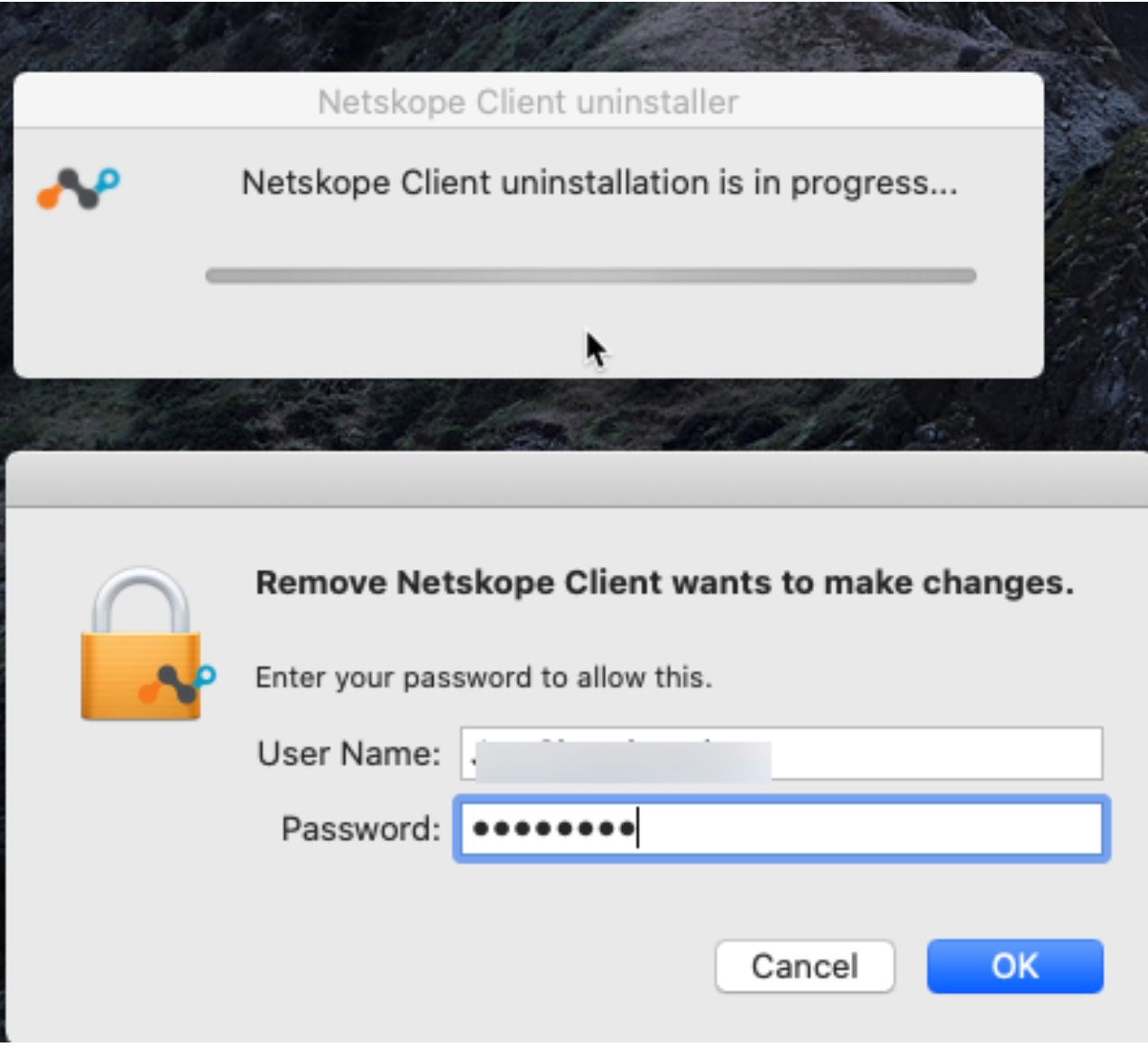
The Netskope Client is uninstalled from your machine.
Click OK.
The Password protection for client uninstallation and service stop option under Client Configuration > Tamperproof lets the administrator restrict unauthorized uninstallation of Client by the end users. The end user must know the password set by the administrator while uninstalling the Client. Service stop option is available only to Windows devices.
Tamperproofing of NS CLient in macOS Ventura
Prior to macOS Ventura versions like Monterey or older versions, the users are unaware about the applications running in the background. With macOS Ventura, it displays the applications running in the background and allows users to enable/disable them. To learn more, view Login and Background items.
When Netskope Client is running in the background and disabling the Client services can impact the Client functionality and end-users can encounter security issues. You can restrict users from enabling/disabling this option through MDMs like VMware Workspace ONE and JAMF using policies.
VMware Workspace ONE
The following configuration steps restrict users from disabling the Client in login items.
Go to Resources > Profiles&Baselines > Profiles.
Click Add > Add Profile.
Select Apple macOS as the platform to start.
Select Device Profile in Select Context.
Enter profile name.
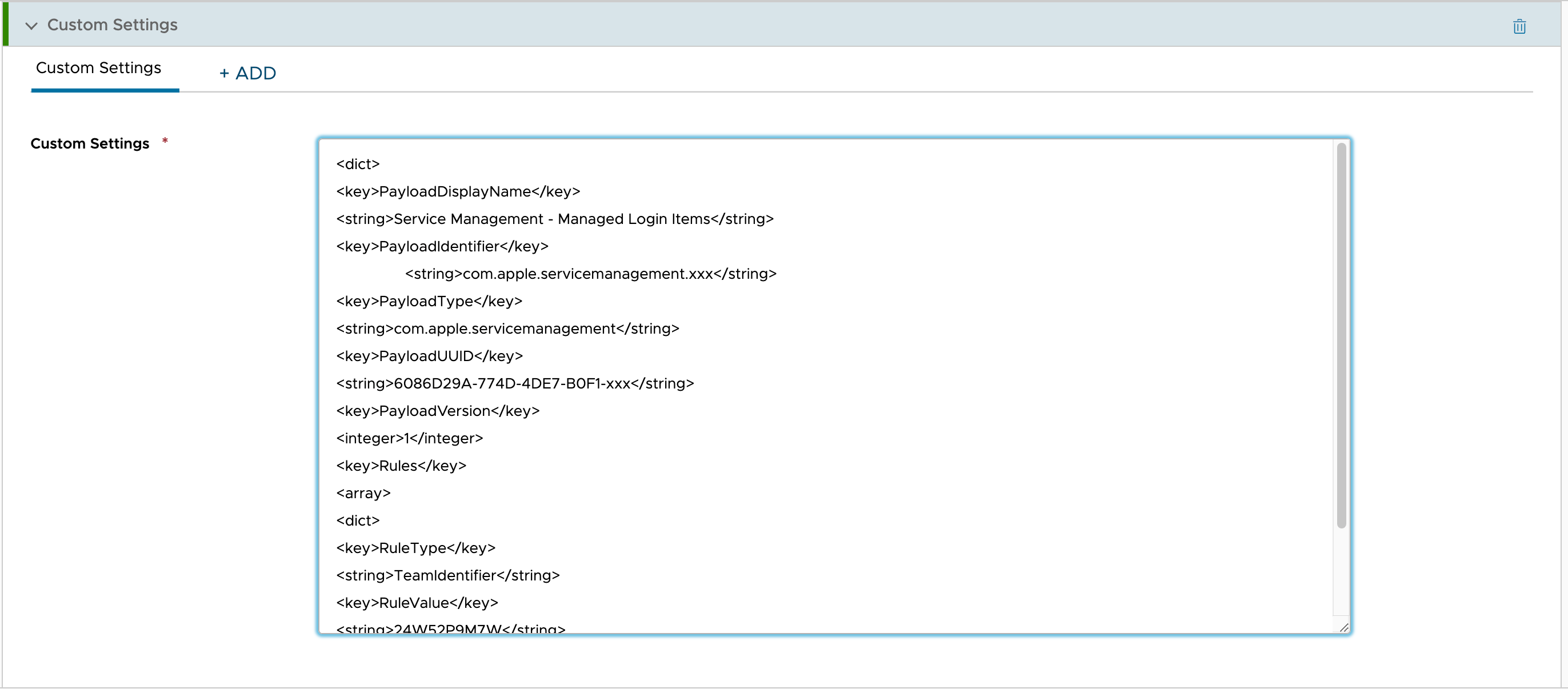
Go to the Custom Settings section and click Add at the right corner of this section. The fields get enabled now.
Provide the following custom payload information in the Custom Settings text-box:
<dict> <key>PayloadDisplayName</key> <string>Service Management - Managed Login Items</string> <key>PayloadIdentifier</key> <string>com.apple.servicemanagement.xxx</string> <key>PayloadType</key> <string>com.apple.servicemanagement</string> <key>PayloadUUID</key> <string>xxxxxxxx-xxxx-xxxx-xxxx-xxx</string> <key>PayloadVersion</key> <integer>1</integer><key>Rules</key> <array> <dict> <key>RuleType</key> <string>TeamIdentifier</string> <key>RuleValue</key> <string>24W52P9M7W</string> </dict> </array> </dict>Edit the Payload Identifier and UUID values.
Important
Currently, many MDM providers do not have the user interface (UI) option to disable this functionality. Hence, use Custom Settings to add the payload.
Click Next.
On the Assignment page, assign the profile to Smart Groups.
Click Save and Publish.
JAMF
Using JAMF Pro, you can restrict users disabling Netskope Client from background services. This requires you to upload the following configuration PLIST (netskope login items.mobileconfig).
Configuration file:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN"
"http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDescription</key>
<string>Allows for netskope to register a launch daemons and launch agents</string>
<key>PayloadDisplayName</key>
<string>Managed Login Items - Netskope Apps</string>
<key>PayloadIdentifier</key>
<string>com.netskope.servicemanagement.xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx.</string>
<key>PayloadUUID</key>
<string>xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx</string>
<key>PayloadType</key>
<string>com.apple.servicemanagement</string>
<key>PayloadOrganization</key>
<string>Netskope</string>
<key>Rules</key>
<array>
<dict>
<key>RuleType</key>
<string>TeamIdentifier</string>
<key>RuleValue</key>
<string>24W52P9M7W</string>
<key>Comment</key>
<string>Allow login items for netskope apps</string>
</dict>
</array>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Managed Login Items - Netskope Apps</string>
<key>PayloadIdentifier</key>
<string>com.netskope.servicemanagement.xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx</string>
<key>PayloadUUID</key>
<string>xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadScope</key>
<string>System</string>
</dict>
</plist>To learn more, view Uploading a Configuration Profile for Managed Login Items.
Perform the following steps to upload the PLIST file to JAMF:
Log into JAMF with admin credentials.
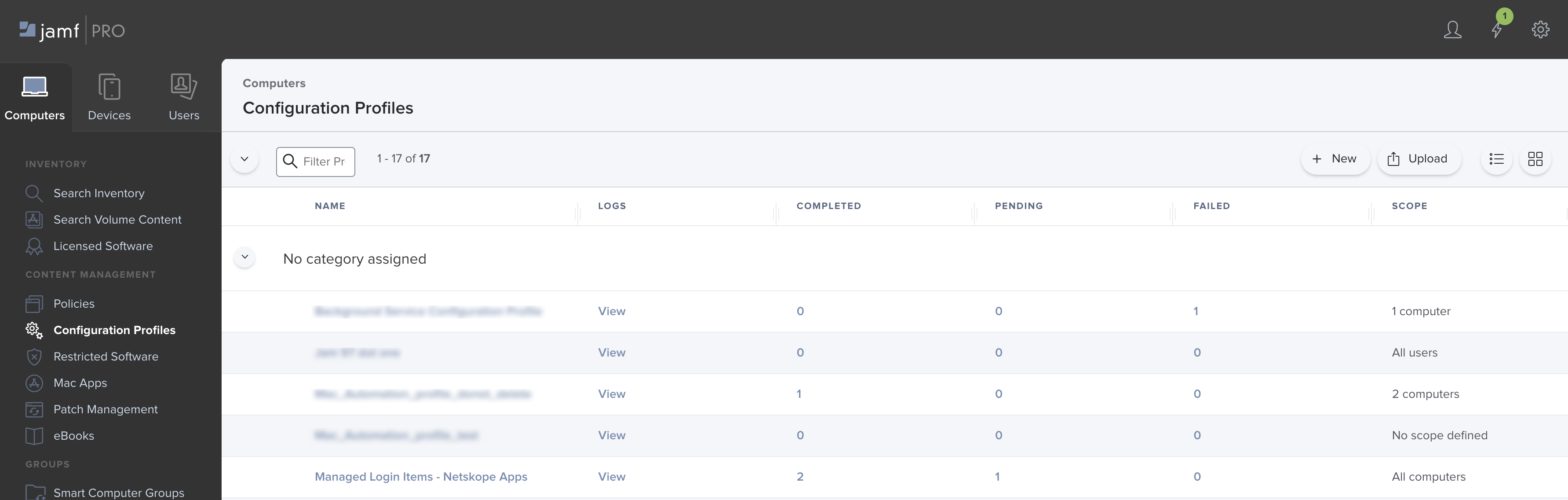
Go to Computers > Configuration Profiles.
Click Upload.
In Upload OS X Configuration Profile, click Choose File and select the file (netskope login items.mobileconfig) from your local machine.
Click Upload. This navigates to the New macOS Configuration Profile.
In the New macOS Configuration Profile, Name under General displays the Payload Display Name string provided in the PLIST file.
Click Save.
Click the Scope tab and configure the scope of the configuration profile.
Click Save.
The configuration profile is now pushed to the target devices in your scope and you can view the new profile from Configuration Profiles.
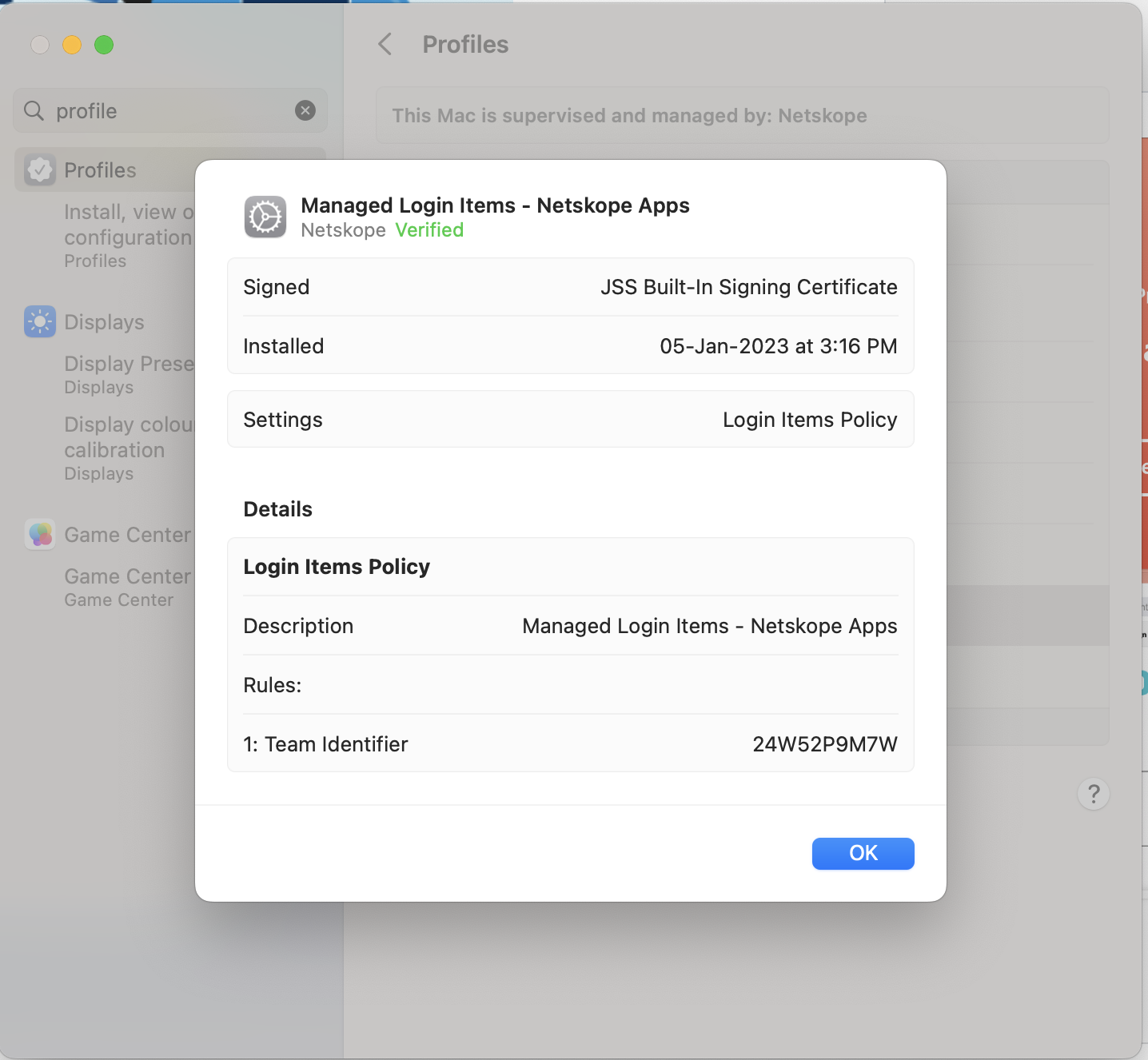
 |
To check the configuration profile from your macOS device, go to System Settings > General Settings > Profiles. Here you can see Managed Login Items - Netskope Apps listed under Devices (Managed) section.
 |