Constraint Profile
A Constraint profile is used in Real-time Protection policies. They define what a user is allowed to do for a specific activity in an app and, in the case of Amazon S3, constraints detect and prevent insider threat activities.
For example:
Users are allowed to share contents only within the organization from Google Drive, or bypass inspection if the user is logging into their personal instance of Google mail.
Users cannot copy or sync data from corporate owned AWS S3 buckets to personal or non-corporate AWS S3 buckets.
User Constraint Profiles and Storage Constraint Profiles can be applied to specific activities when creating an Real-time Protection policy for an app.
To create a user constraint profile,
Go to Policies > Profiles > Constraint > Users, click New User Constraint Profile.
Configure the email address wildcard to be matched. For example, to block users from sharing files outside the organization, you would specify the email address Does not match with the value *@netskope.com.
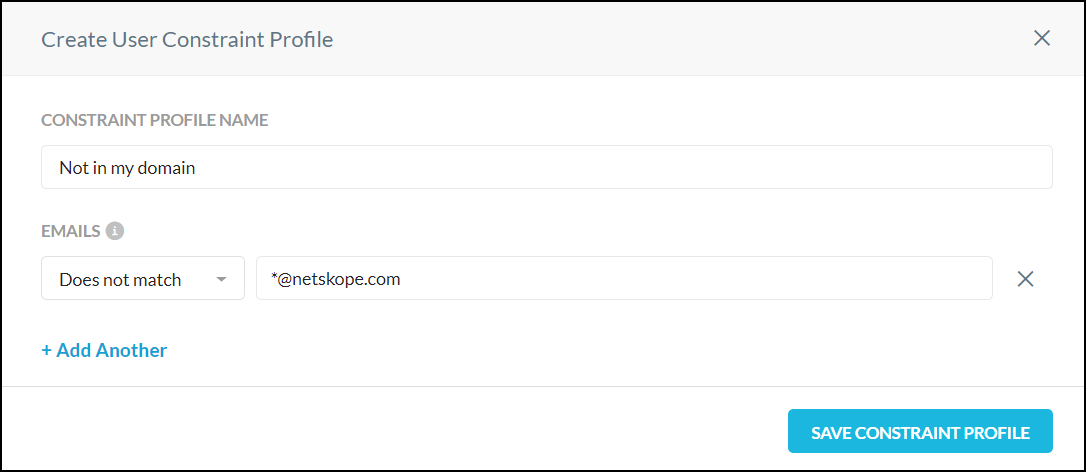
Enter a name for the User Constraint and click Save Constraint Profile.
To create a storage constraint profile,
Go to Policies > Profiles > Constraint > Storage and click New Storage Constraint Profile.
Configure the Amazon S3 Buckets to be matched. For example, to block copy or sync operations to a bucket outside the organization, you would choose, Does not match and select an instance or individual buckets in a specific region.
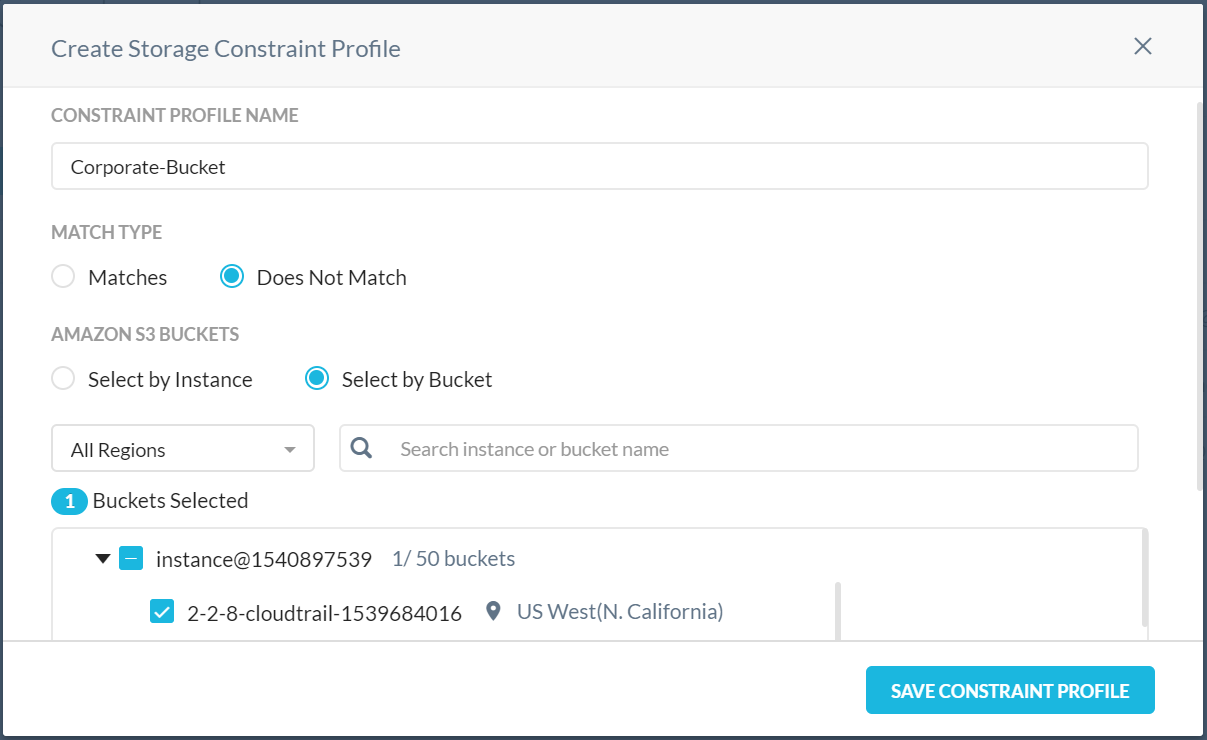
Enter a name for the Storage Constraint and click Save Constraint Profile.
You can update a constraint profile by clicking on the profile in the Users or Storage tabs.
To apply a constraint to an activity:
When creating an Real-time Protection policy, in the Activities section, look for the Constraints panel:
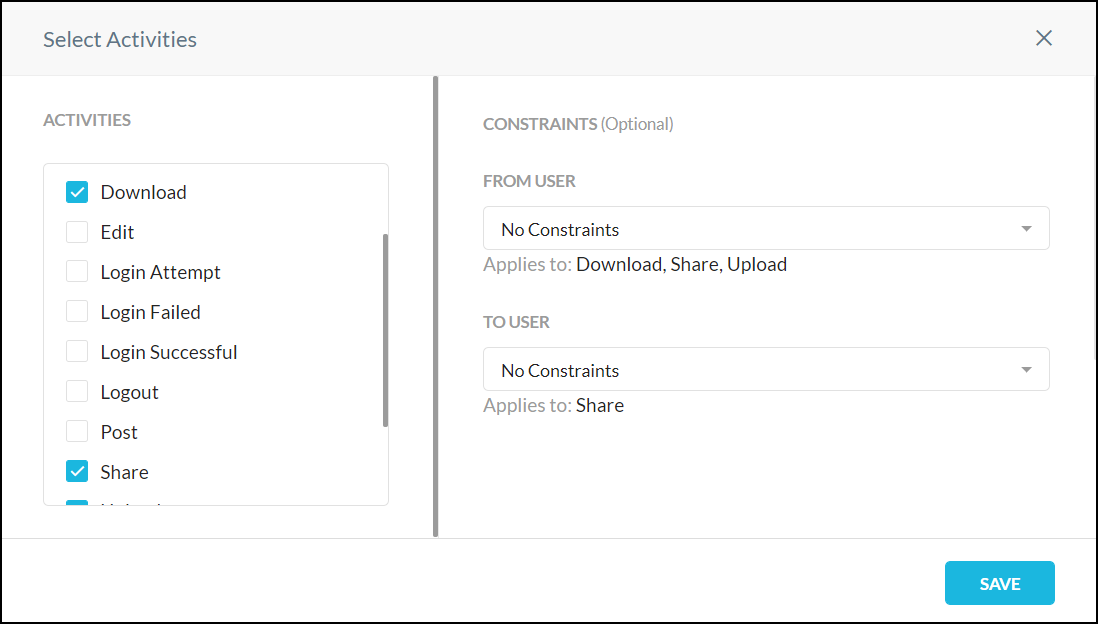
First select the activities to control in the left panel before adding User or Storage Constraints in the right panel.
Tip
If DLP or Threat Protection profiles are applied to this policy, then only the From User constraint is applicable. If neither are used, then both the From User and To User options are available.
If the policy applies to Amazon S3, then storage constraints can be applied. When you select Copy and Sync activities, To Storage and From Storage options are available.
Choose if the constraint profile applies to From User, To User, To Storage, or From Storage.
Note
You have the option to create new User and Storage constraints here if not already created. You can view or update the constraints under Policies > Profiles > Constraint.
To create custom user constraints, select Create New from the From User or To User dropdown lists.
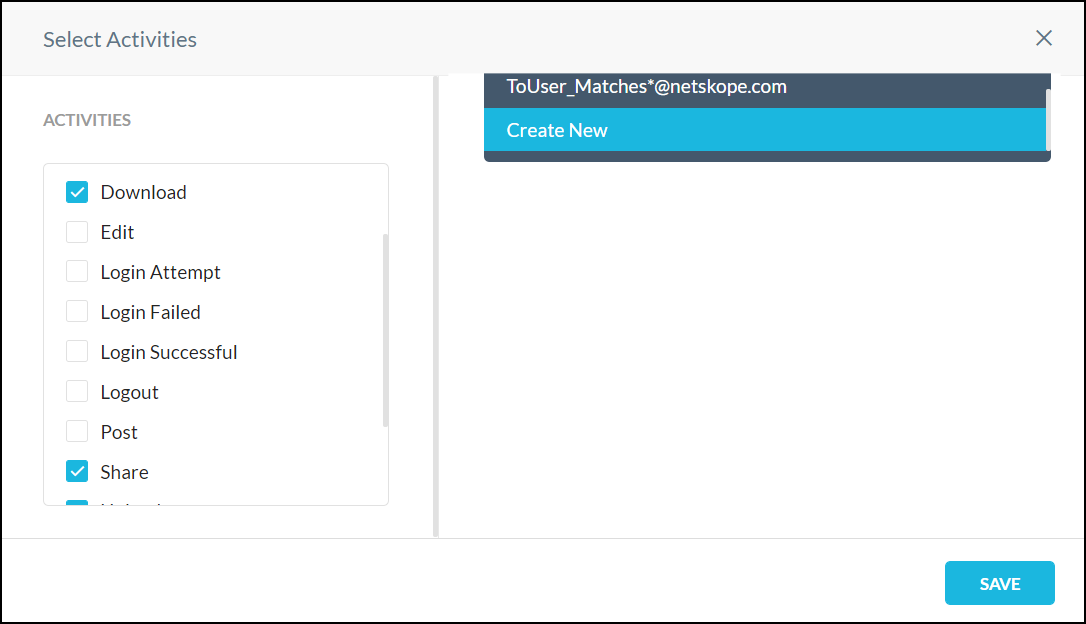
For example,
If you want to block users from sharing files outside the organization, create a user constraint for To User like Anyone not part of Netskope.
If you want to bypass policy inspection when a user logs in from their personal email address to a personal Box instance, then create a user constraint for From user like Not in my domain.
To create custom storage constraints, select Create New from the To Storage or From Storage dropdown lists.
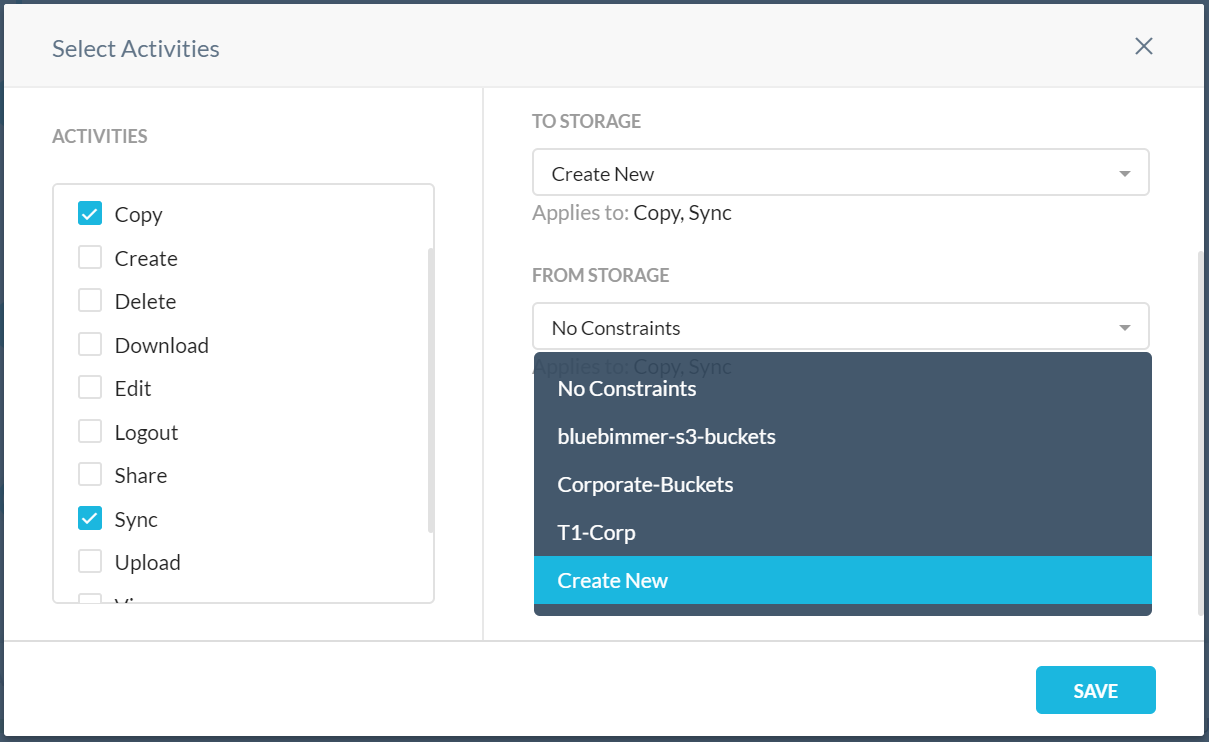
For example,
If you want to block users from performing a copy or sync operation from a personal non-corporate storage bucket to a corporate storage bucket, create a storage constraint for To Storage and choose the corporate S3 buckets or AWS instances.
If you want to block users from performing a copy or sync operation from a corporate storage bucket to a personal non-corporate storage bucket, create a storage constraint for From Storage and choose the corporate S3 buckets or AWS instances.
When finished creating and selecting the constraints, click Save.
Tip
To not use a constraint for From User, To User, To Storage, or From Storage, leave the No Constraint default in the drop-down list.
Click Apply Changes.
Creating a USB Device Constraint Profile
Note
Contact your Sales Representative to enable this feature for your account.
You can create a new constraint profile to define the USB devices that the users are allowed to access.
To create a new USB device constraint profile:
Tip
These constraint fields are evaluated on an AND-basis. For example: "Manufacturer AND Device ID AND Model AND Serial Number"
In the Netskope UI, go to Policies > Profiles > Constraint and select the USB Device tab.
In the USB Storage Device tab, click New Device Constraint Profile.
In the New USB Device Constraint Profile window, enter a profile name.
Provide the list of USB storage device manufacturers, IDs, models, and serial numbers. Select each tab and enter the values or upload a list as a CSV file. You can upload a maximum file size of 6 MB in each tab. Ensure the following:
Manufacturer and Model are partial matches. For example, enter “Sandisk” as the manufacturer to match USB device names such as “Sandisk”, “ Sandisk USB”, “Sandisk Electronics, INC”, etc.
The ID must be in the format
idVendor+idProduct\iSerialNumber.Serial_Number and ID are exact match fields.
Click Save and then click Apply Changes.
Creating a Printer (Windows) Constraint Profile
Note
Contact your Sales Representative to enable this feature for your tenant. This feature is currently Windows-only.
You can create a new constraint profile to define the printers that the users can access.
To create a new Printer device constraint profile:
In the Netskope UI, go to Policies > Profiles > Constraint and select the Printer tab.
In the Printer tab, click New Printer Constraint Profile.
In the New Printer Constraint Profile window, enter a profile name.
In the Printer Type section, select at least one type between Local Printer or Network Printer. One type must be checked.
Enter printer identifier such as Manufacturer, Device, Driver, Port, Location, UNC Path separated by new line. Wildcard expressions are supported.