AWS CloudTrail Lake Plugin for Log Shipper
This document explains how to configure the AWS Cloudtrail Lake integration with the Cloud Log Shipper module of the Netskope Cloud Exchange platform. This integration allows ingestion of Netskope events and alerts into your CloudTrail event data store.
Event Support | Yes |
Alert Support | Yes |
WebTx Support | No |
A Netskope Tenant (or multiple, for example, production and development/test instances).
A Netskope Cloud Exchange tenant with the Log Shipper module already configured.
The AWS account used must have access to the CloudTrail beta APIs.
Connectivity to the following host: aws.amazon.com.
Get your AWS Credentials and Create a Channel ARN.
Configure the AWS CloudTrail Lake Plugin.
Configure Log Shipper Business Rules for AWS CloudTrail Lake.
Configure Log Shipper SIEM mappings for AWS CloudTrail Lake.
Validate the AWS CloudTrail Lake plugin.
Click play to watch a video:
You need your AWS credentials and Channel ARN to configure the CloudTrail Lake plugin.
Log in to AWS Console.
Click on the username (top right corner) and go to Security Credentials.
Click Create Access Key.
Copy the Access Key ID and Secret access key.
Log in to your AWS CloudTrail Console.
Go to CloudTrail > Lake > Integrations and click on Add Integrations.
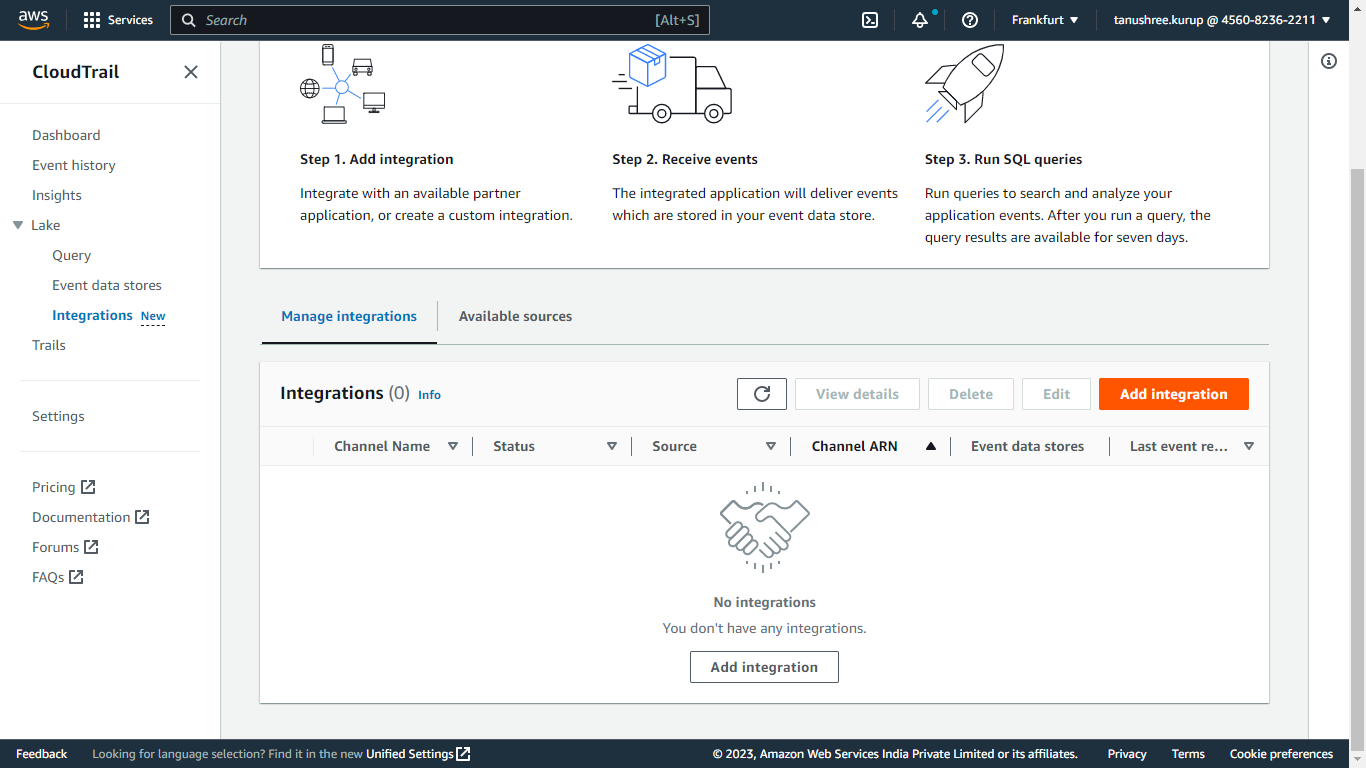
Enter a name for the channel.
Select Netskope from the source dropdown.
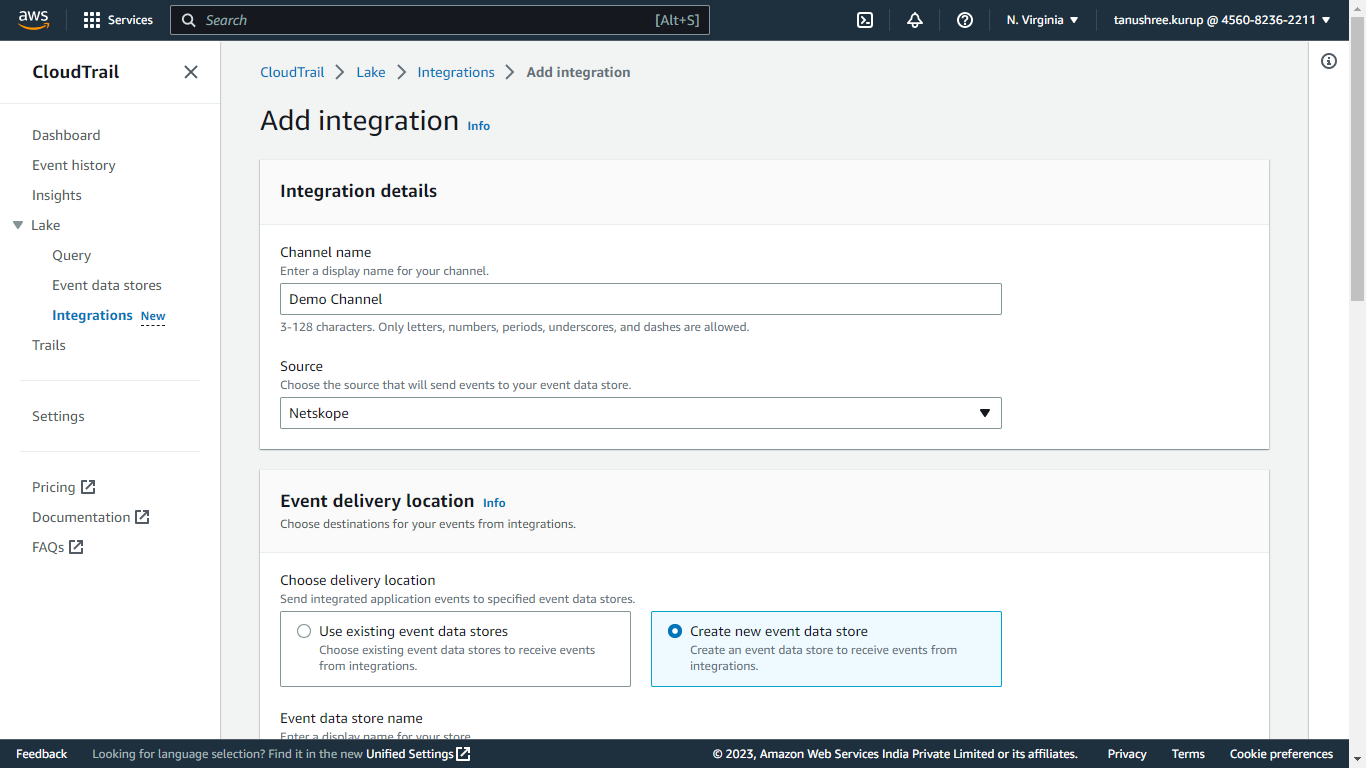
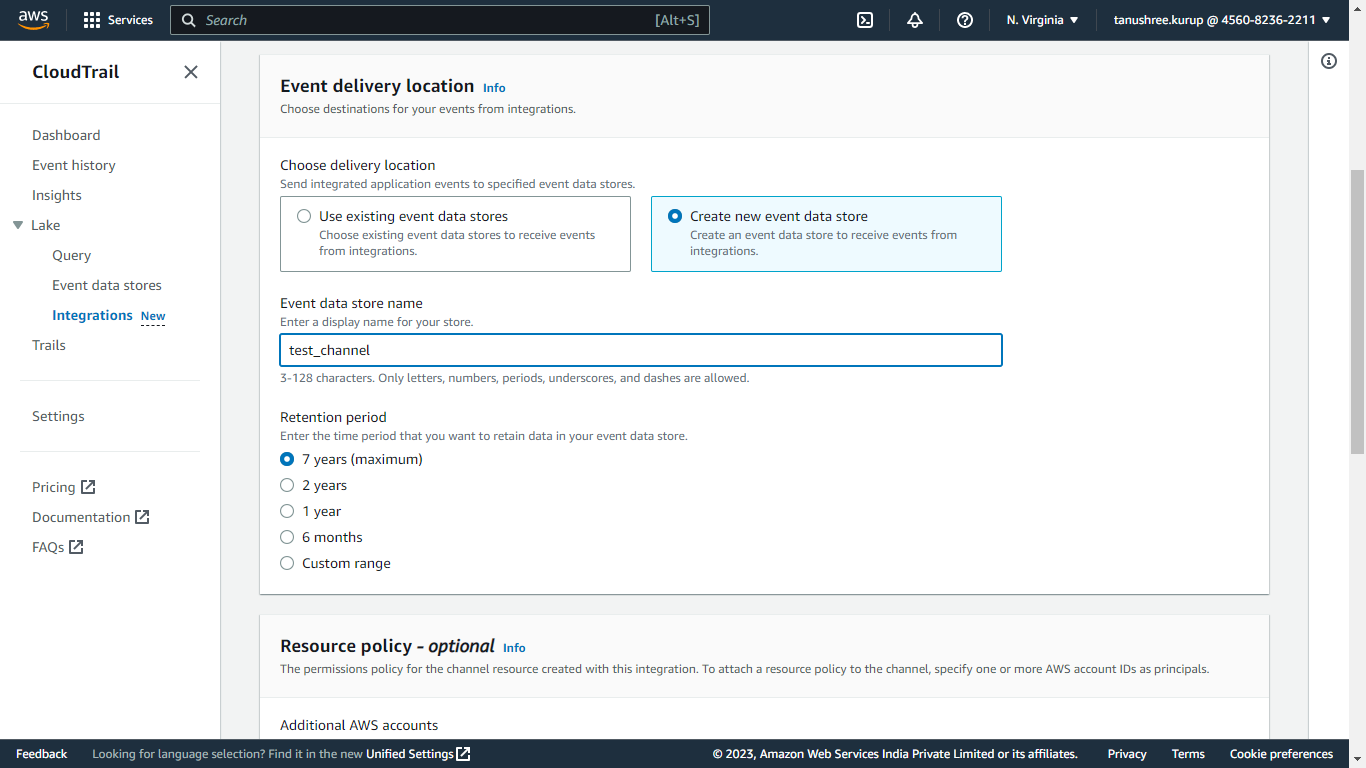
For the delivery location, select Create new event data store, and enter a name. Select the Retention period.
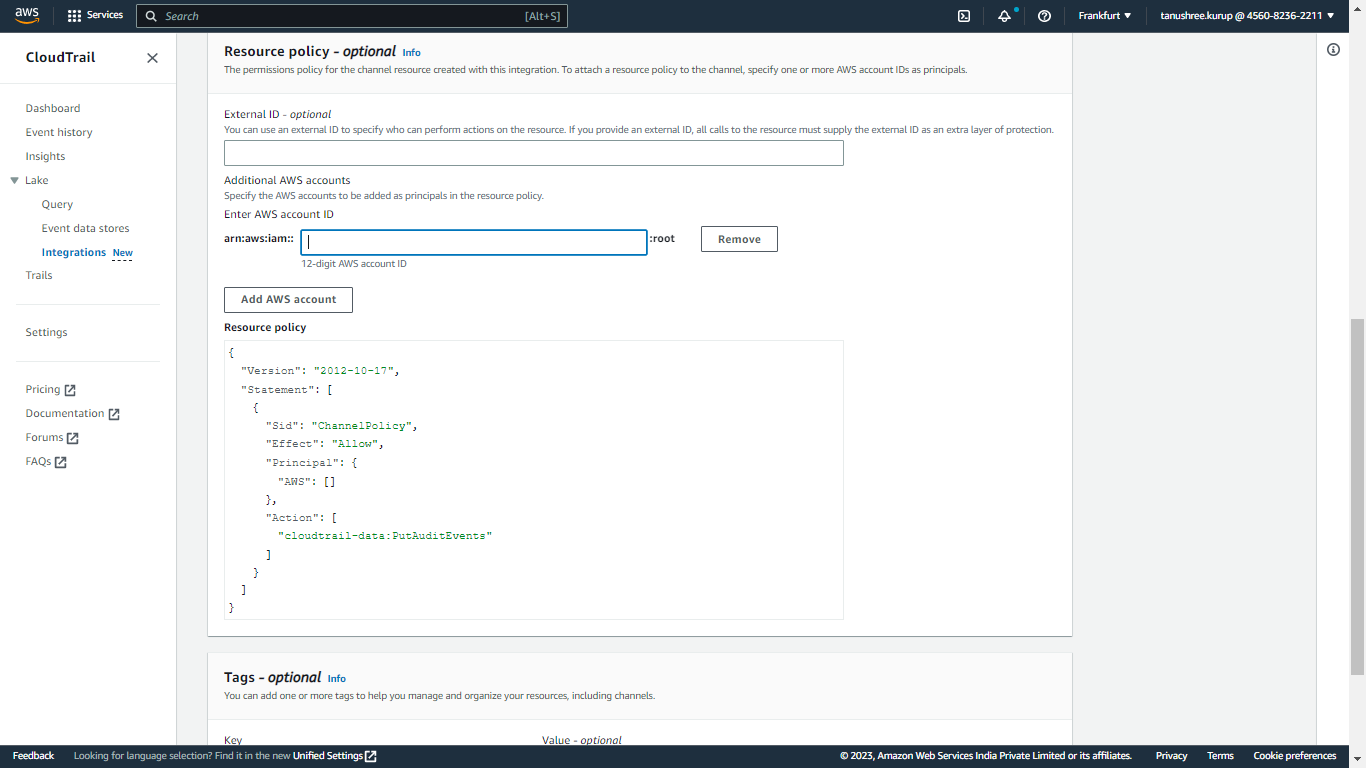
In the Resource Policy, select Add AWS account to specify an AWS account ID to add as a principal in the policy (The accounts defined as principals in the resource policy can call the
PutAuditEventsAPI to deliver events to your channel).Add tags as required (Tags are used for managing the resources).
Click Add integration. Copy the value of Channel ARN.
The user or role that you use to work with open audit events must have permissions to call the PutAuditEvents API. Apply a policy with the following permissions to the role. This policy statement allows access to create, manage, and delete event data stores in CloudTrail Lake, run and view queries and results, and load open audit events into CloudTrail.
Replace the <Channel ARN> with your Channel ARN.
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":"cloudtrail-data:PutAuditEvents",
"Resource":"<Channel ARN>"
}
]
}Log in to Cloud Exchange and go to Settings > Plugins.
Click on the AWS CloudTrail Lake plugin box.
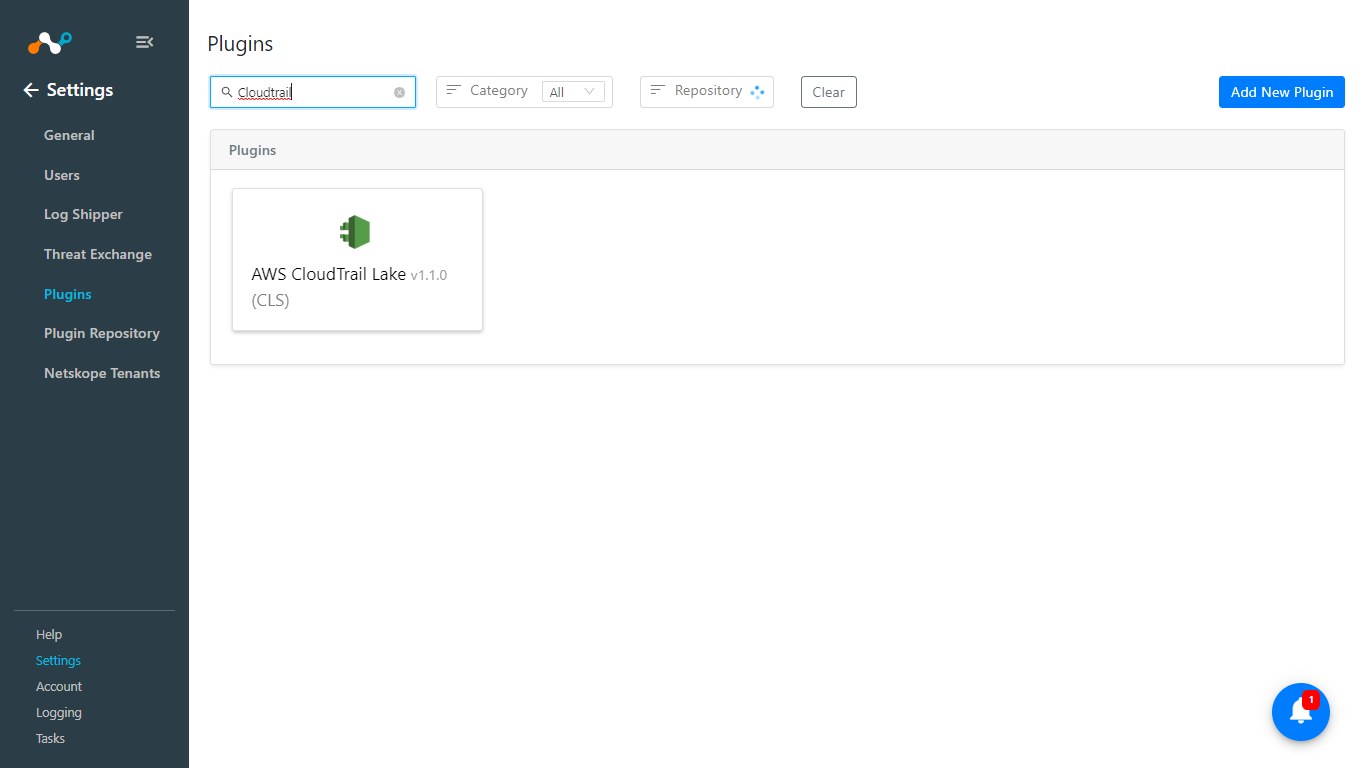
Enter and select these values:
Configuration Name: Unique name for the configuration.
Mapping: Select a valid Mapping. A Default Mapping for all plugins are available.
Use System Proxy: Enable if proxy is required for connectivity.
Transform the raw logs: For AWS CloudTrail Lake Plugin, this toggle needs to be always enabled.
Click Next.
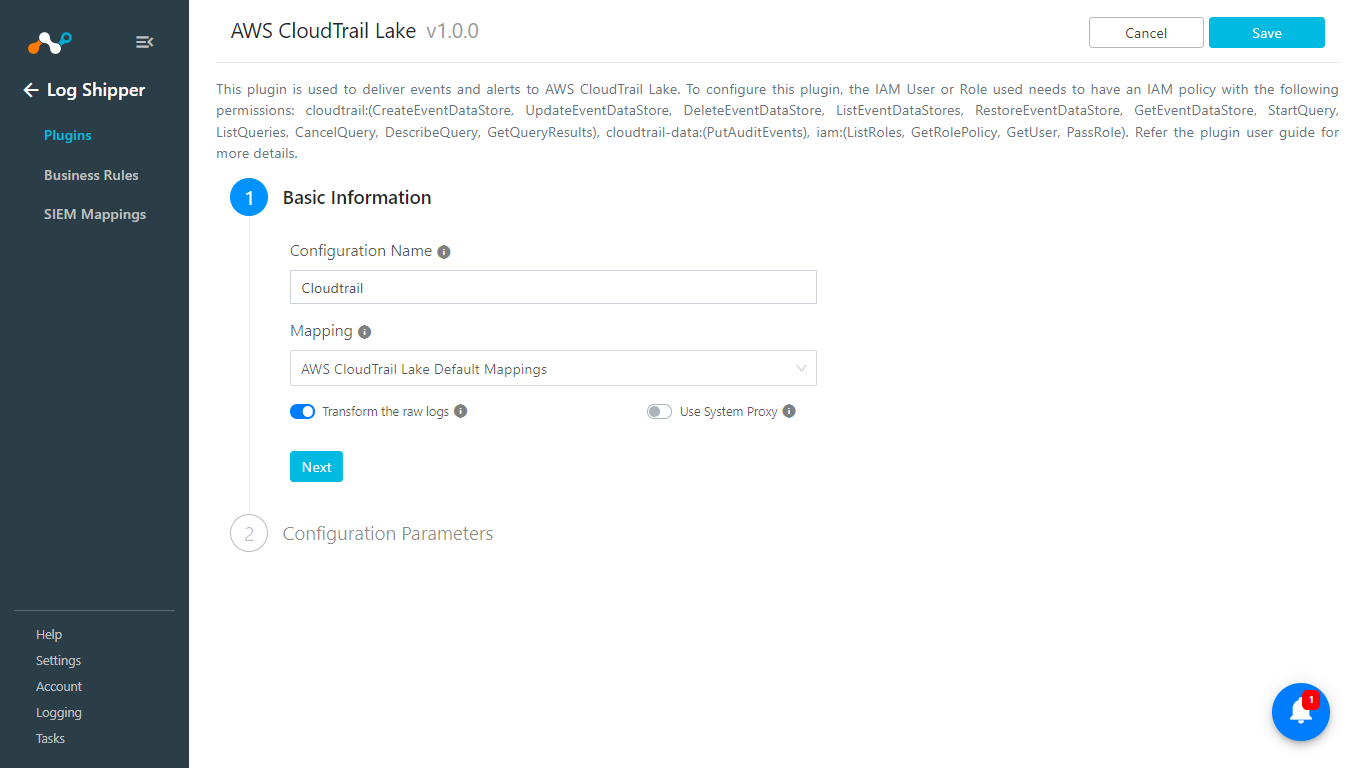
Enter and select these values:
AWS Access Key ID (Public Key): AWS Access Key ID obtained previously.
AWS Secret Access Key (Private Key): AWS Secret Access Key obtained previously.
Channel ARN: Enter the Channel ARN obtained previously.
Add Additional Data: Whether to send unmapped fields as additional event data to the CloudTrail event data store or not.
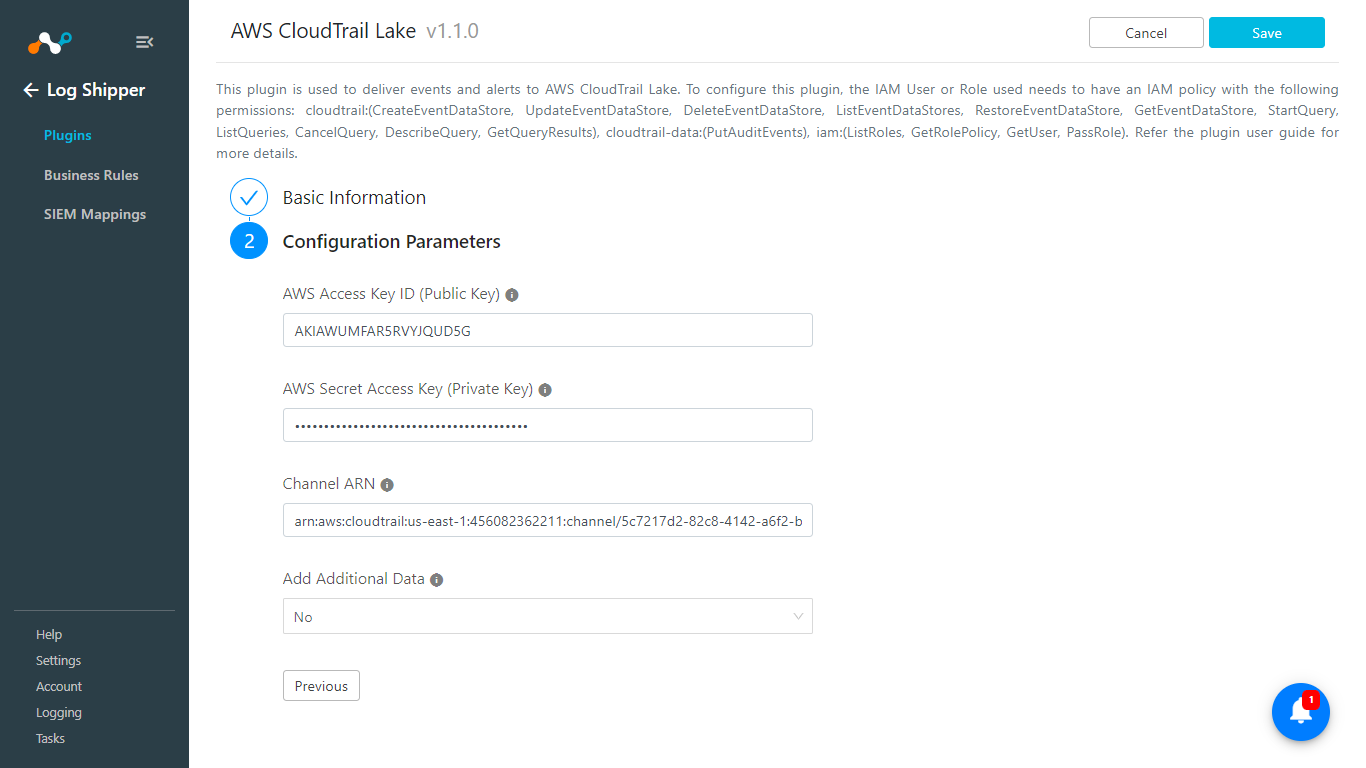
Click Save.
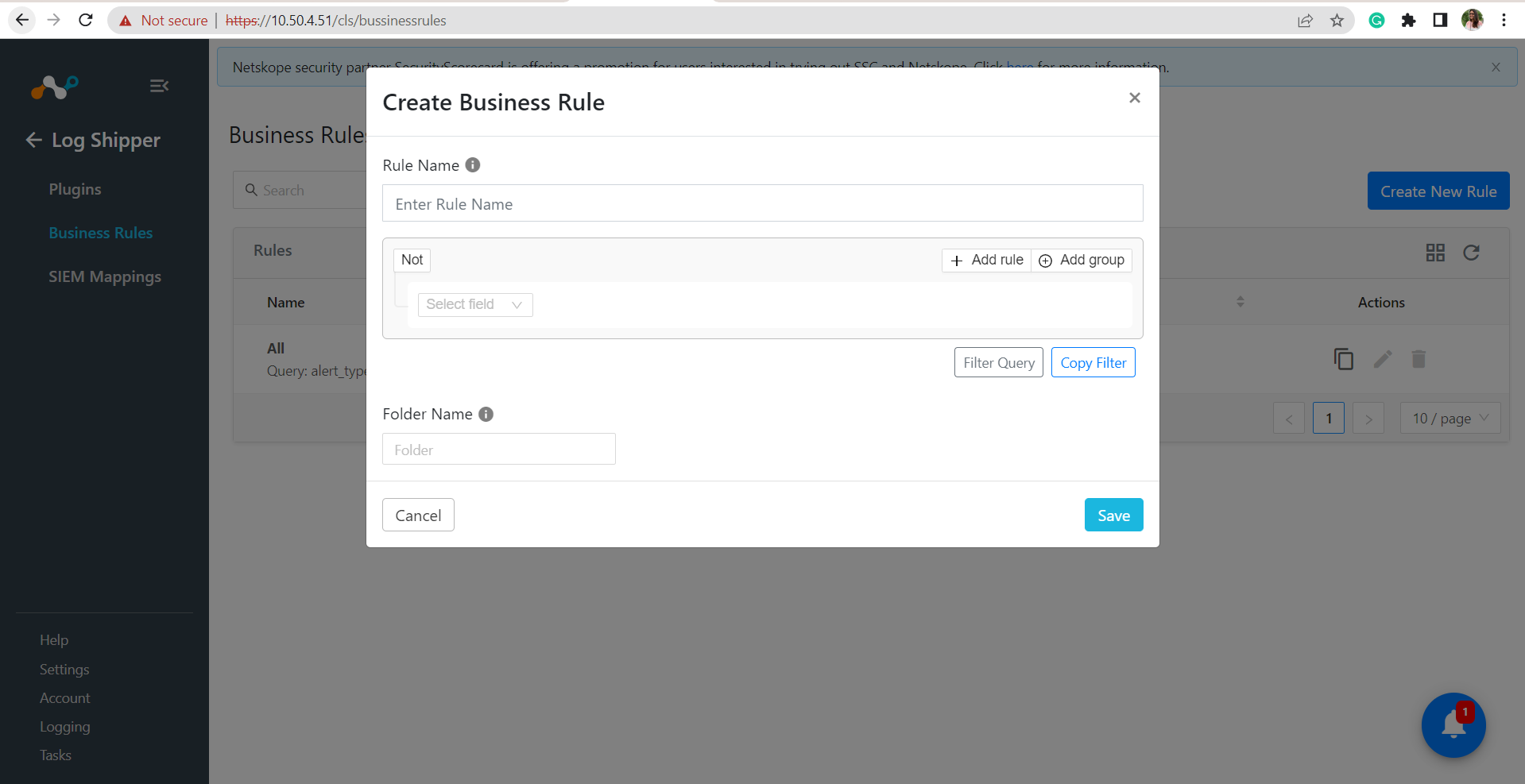
Go to Log Shipper > Business Rules.
Click Create New Rule.
Note
If you want all the events and alerts ingested into your SIEM Mapping, you can use the default ALL rule.
Enter a Rule Name and configure a query for business rules based on your requirement; when finished, click Save.
SIEM mapping enables the user to ingest the Netskope logs (alerts and events) to the third-party platform.
Note
Data ingestion to the third-party SIEM server will only start if the user has added SIEM Mappings.
Go to Log Shipper > SIEM Mappings.
Click Add SIEM Mappings.
Select the Source (Netskope plugin) and Destination (AWS CloudTrail Lake) plugins, and then select a Business Rule from the dropdown list.
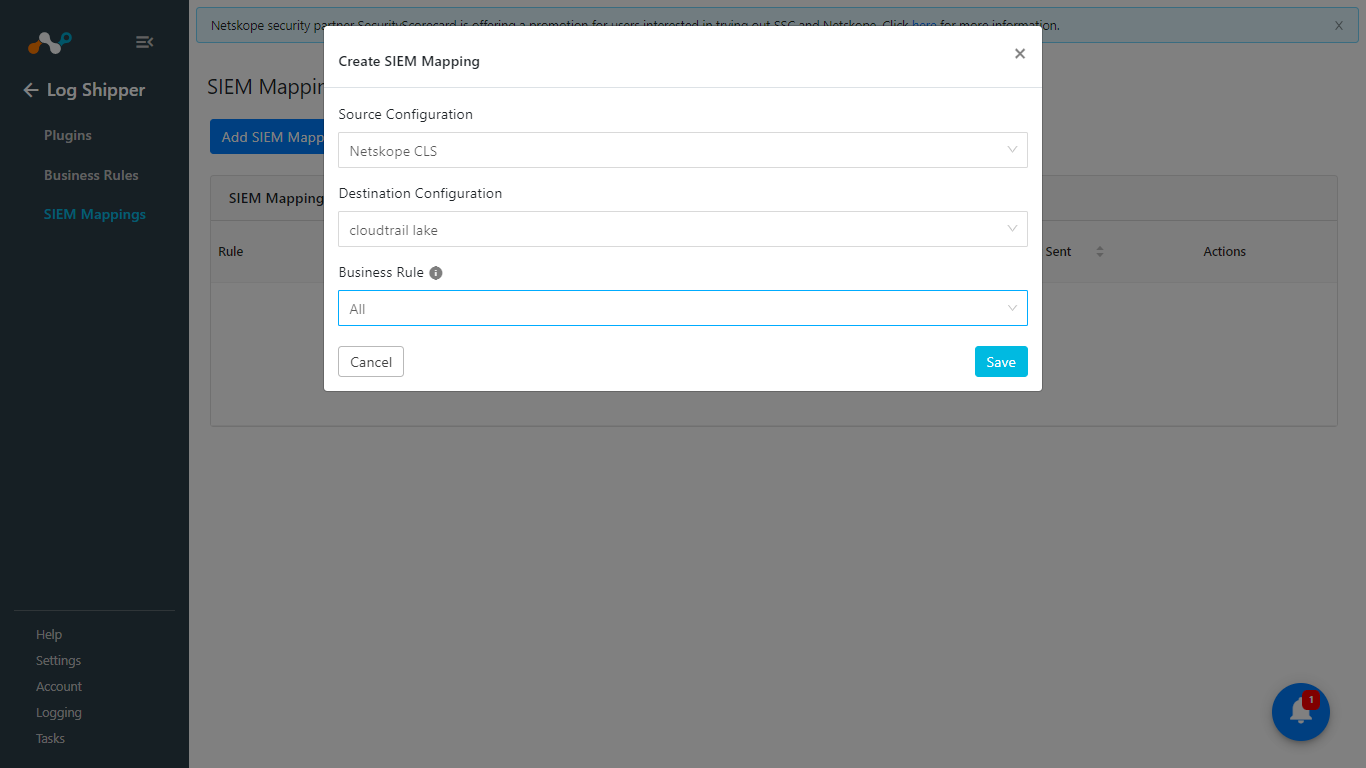
Click Save.
To validate that if the events has been pulled, transformed, and ingested from Cloud Exchange to CloudTrail Lake, you can check in Cloud Exchange and AWS CloudTrail Lake.
Log in to Cloud Exchange.
Go to to Logging.
Filter using a message contains
<<plugin_configuration_name>>.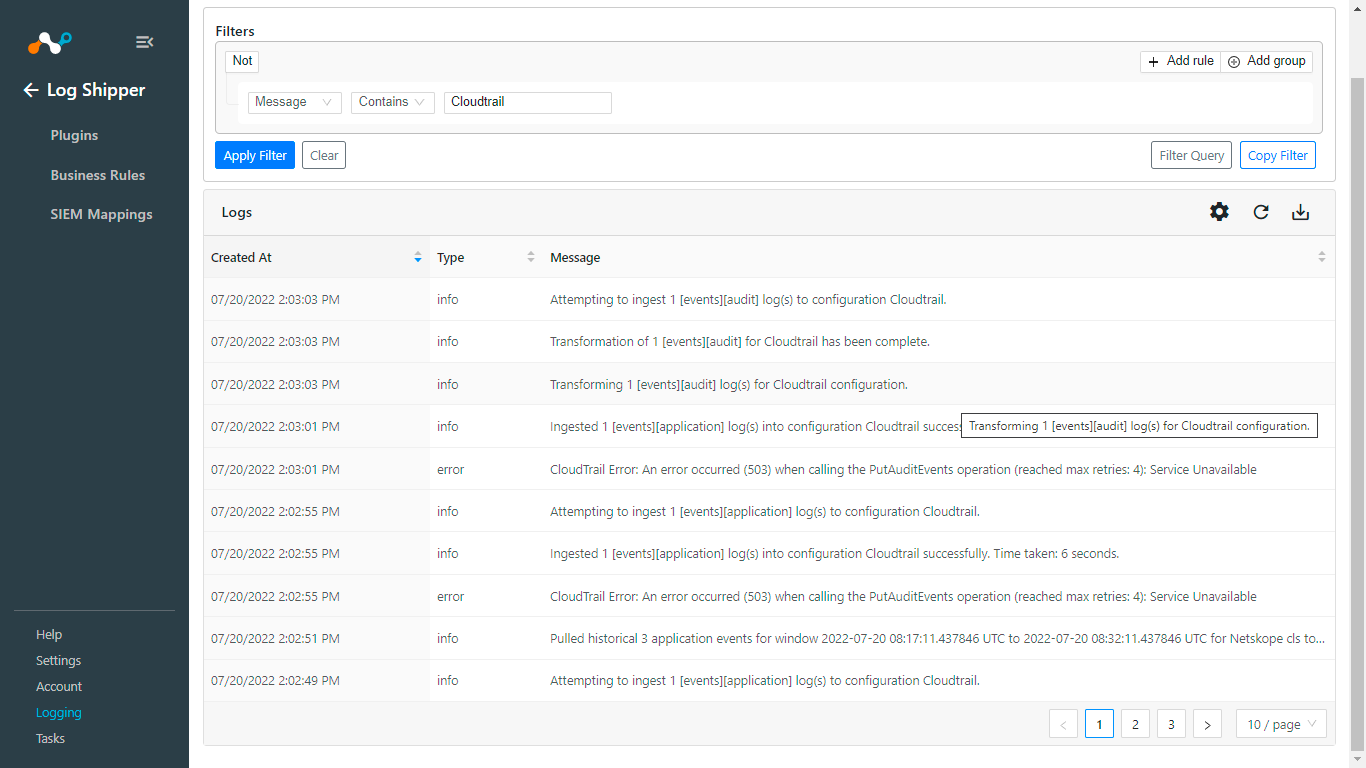
Log in to the AWS Console.
Go to Cloud Trail > Lake. Click on the Editor tab.
Copy the Event data store ID.
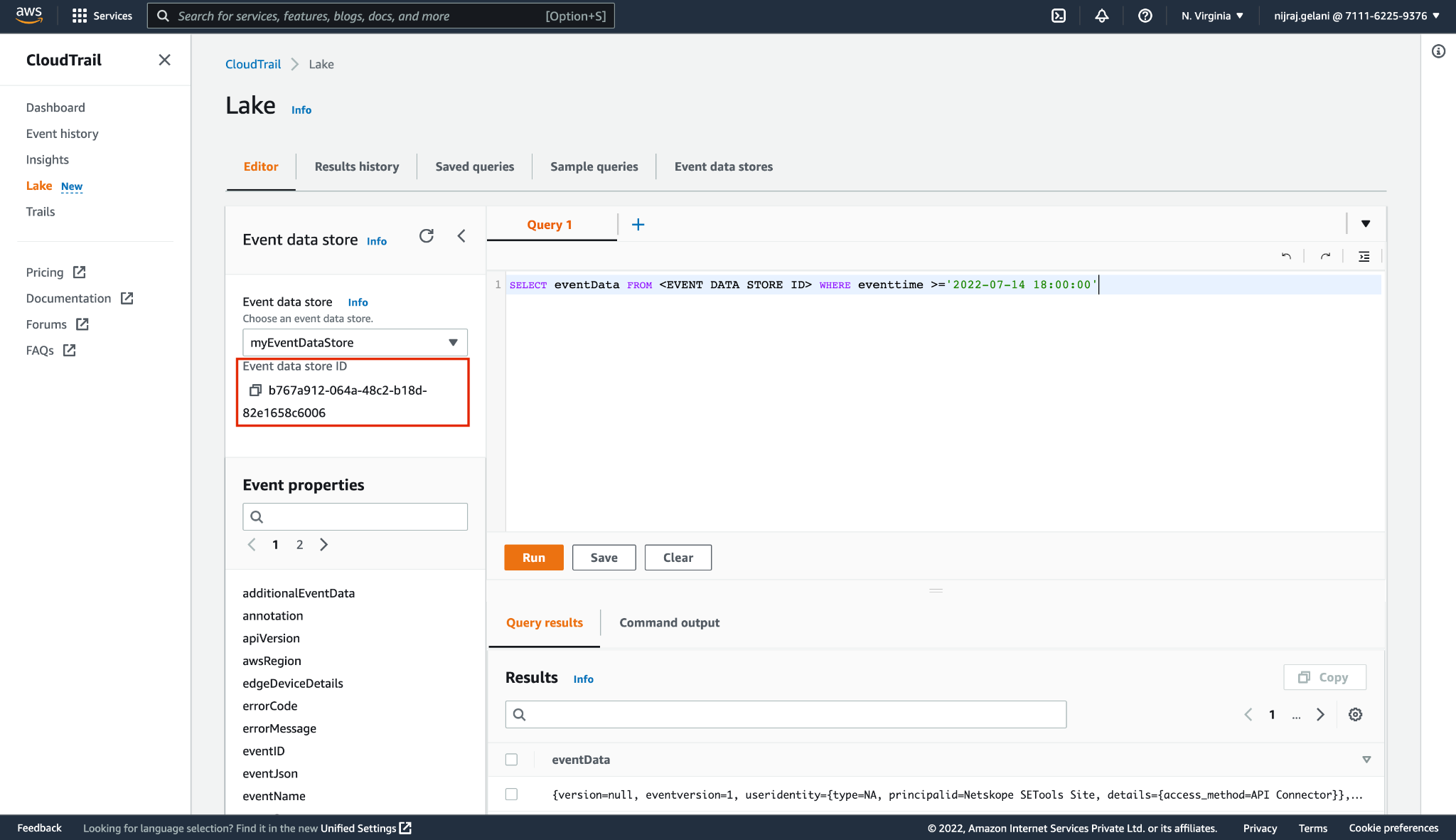
Enter this query (replace the
<EVENT DATA STORE ID>with the previously copied ID, and the<DATE TIME>with your desired date time. Events created after this date time will be shown.) in the editor and click Run.SELECT eventData FROM <EVENT DATA STORE ID> WHERE eventtime >='DATE TIME’For example:
SELECT eventData FROM 58cfe6e1-093c-45da-a837-990bca613536 WHERE eventtime >='2022-07-14 18:00:00'
You can also filter results for a specific event/audit time with the following query (replace
<EVENT DATA STORE ID>with your event data store ID and<DATA_TYPE>and<SUB_TYPE>with Netskope’s data type and subtype that you want to search.SELECT * FROM <EVENT DATA STORE ID> WHERE eventData.eventSource = ‘netskope<DATA_TYPE>.<SUB_TYPE>’
For example:
SELECT * FROM 58cfe6e1-093c-45da-a837-990bca613536 WHERE eventData.eventSource = ‘netskopeevent.audit’
Scroll down to see the ingested events in the Query results tab.
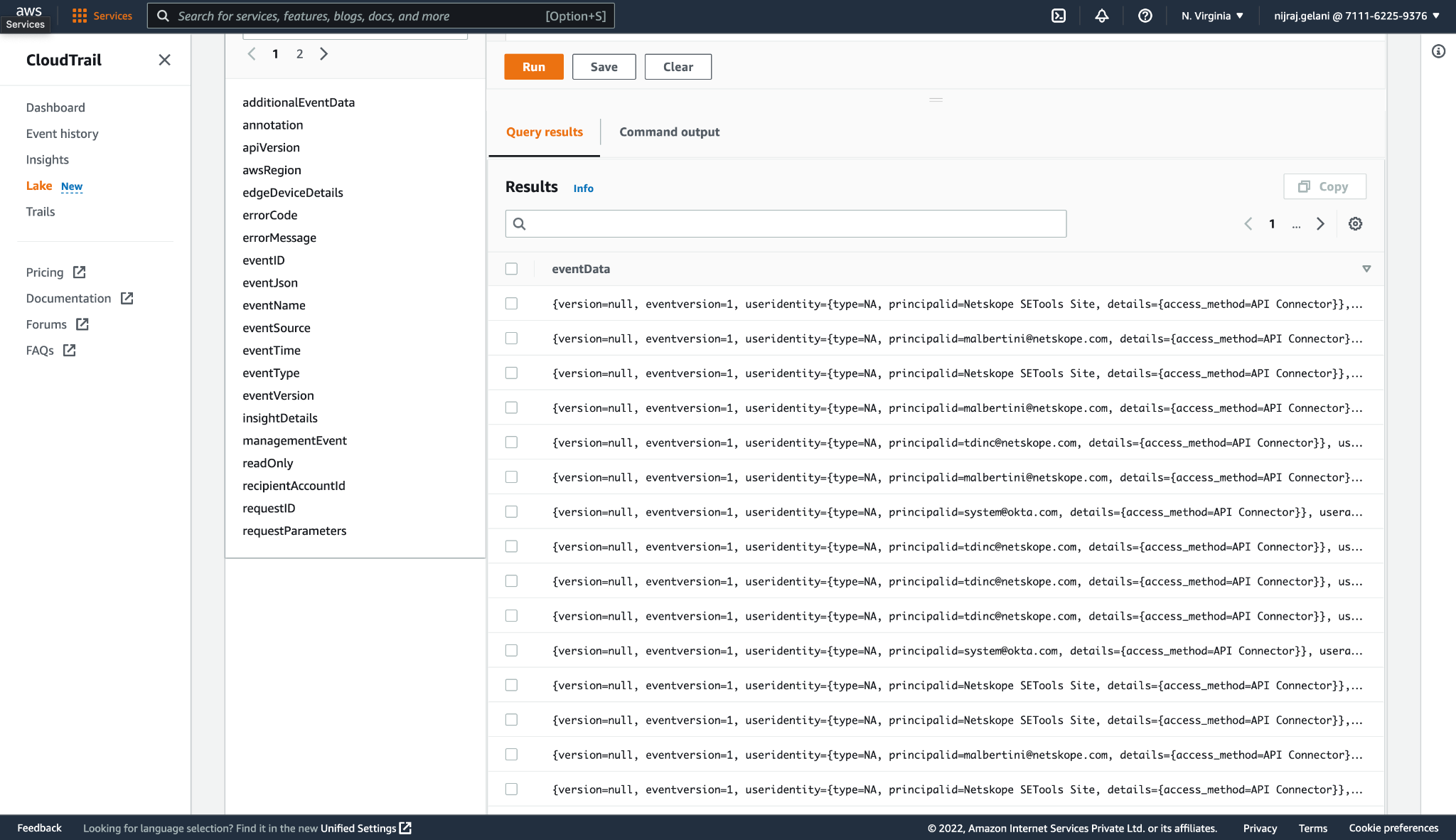
Alerts of the type UBA will not be ingested to AWS Cloudtrail Lake event data store as it is not supported by the Source Destination Netskope present in the AWS CloudTrail Lake.
If multiple alerts and events have the same ID, those alerts and events will not be ingested as Duplicate event IDs are not allowed in the event data stores.