Creating a Firewall App Definition
If you have the Cloud Firewall license, on the App Definition page, you can create new rules for firewall apps to apply to policies. You can create multiple rules for the same firewall app. For example, if you create an app called "Allow_FTP" with a certain destination IP and protocol, this same app can be reused to add more destination IPs and protocols.
Note
Custom apps that only have traffic-based definition rules won't have activities detected. You cannot add Firewall apps to steering.
To create a firewall app definition:
Go to Settings > Security Cloud Platform > App Definition.
In the Cloud & Firewall Apps tab, click New App Definition Rule and then Firewall App.
In the New App Definition Rule: Firewall App window:
Application: Choose an existing firewall custom app or create a new one, and then enter a name for the app. A firewall custom app can't have the same name as a cloud custom app.
Destination IP: Enter a valid IP address, IP range, FQDN, PQDN, or CIDR netmask separated by commas. If you leave it empty, Netskope sets the destination IP to any.
Protocol: Choose the protocol for the firewall app. For TCP, UDP, and TCP/UDP, you can enter:
A specific port:
22A specific port range:
1024-2048A combination of ports and port ranges:
22,80,443,1024-2048
ICMP doesn't require port configuration. A TCP flow times out after 5 minutes of idle time. Netskope recommends you use a keepalive for TCP-based protocols that might leverage longer idle sessions such as SSH, FTP, etc.
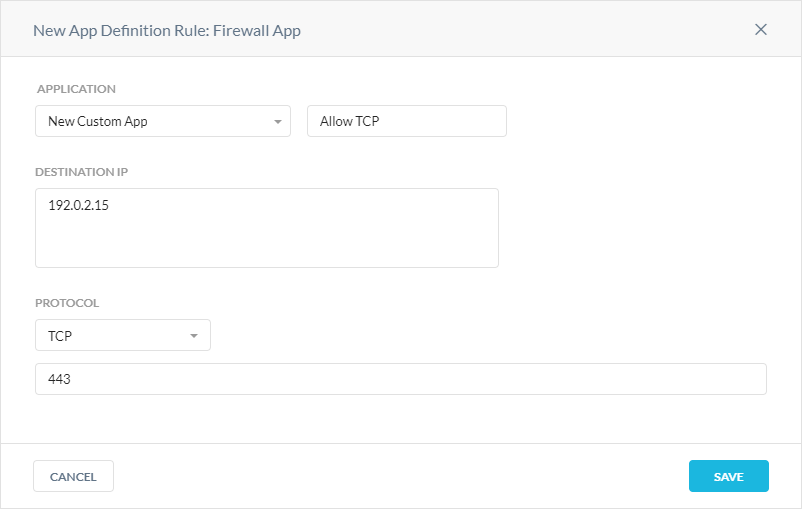
Click Save.
Following is the rule order of custom app definitions and policies:
Firewall Apps - Netskope picks the app that matches first in the policies, i.e. the app matches by the policy ordered list.
Cloud Apps - Netskope finds the most specific application first then matches by the policy ordered list.
If the app matches both Cloud and Firewall apps as described above (i.e. there is overlap), Netskope uses policy ordering to determine a priority.