Creating a Threat Protection Policy for Real-time Protection
Netskope can scan files stored in your cloud storage applications for malware. Real-time Protection policies scan files for malware by default. For added protection, optional configurations include allowlist and blocklist file hash lists for malware detection, and integrating Carbon Black for endpoint protection to use remediation profiles while creating an Real-time Protection policy.
To use the optional configurations in a Real-time Protection policy, configure these options before creating the Real-time Protection policy:
Create a file hash list: Specify the type of hash lists to detect in a malware scan.
Create a detection profile: Specify which hash list file types to allowlist and blocklist.
Integrate endpoint detection and remediation: Set up a 3rd-party integration, like with Carbon Black or CrowdStrike, for endpoint protection.
Create a remediation profile: Specify the action to take, like Isolate, Alert, or Add to Watchlist/Blocklist.
To configure threat protection for Real-time Protection policies:
In the Netskope tenant UI, go to Policies > Real-time Protection and click New Policy. Select Threat Protection.
Enter the settings in the Real-time Protection policy page for Source (Users) and Destination (Cloud App/Category) first.
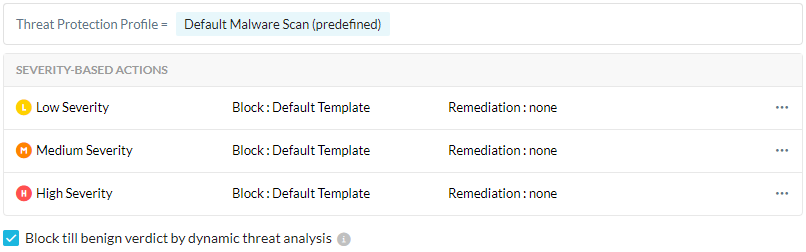
Next, in the Profile and Action section, select a Threat Protection Profile.
Select the Action for each severity level. To apply a remediation profile for each severity level, select a remediation profile from the dropdown list.
Optionally, if you selected File Type constraints and chose a Block action for a severity level, you can see the Block till benign verdict by dynamic threat analysis option. Select to block users from uploading or downloading a file until Netskope dynamic threat analysis provides a benign verdict. The analysis can take up to 10 minutes. See Creating a Threat Protection Policy for Patient Zero.
Enter a name for the policy and click Save.
Now you are ready to use the malware and malicious sites pages.