Configure ADFS for Netskope SSO Manually
To complete these steps, you need the Netskope Assertion Consumer Service URL, Service Provider Entity ID, and SAML certificate. Go to Settings > Administration > SSO, and under Netskope Settings, copy the Assertion Consumer Service URL and Service Provider Entity ID, and then download the SAML certificate.
Add the Netskope admin console as a relying party trust. Open the ADFS Management window and right click the Relying Party Trusts folder, and then click Add Relying Party Trust.
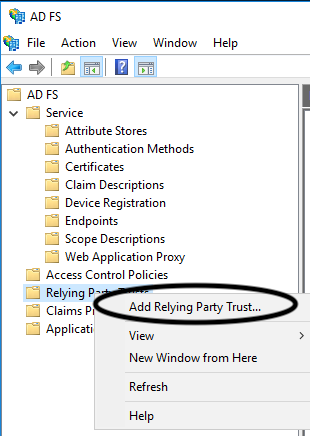
Enable Claims aware and click Start.
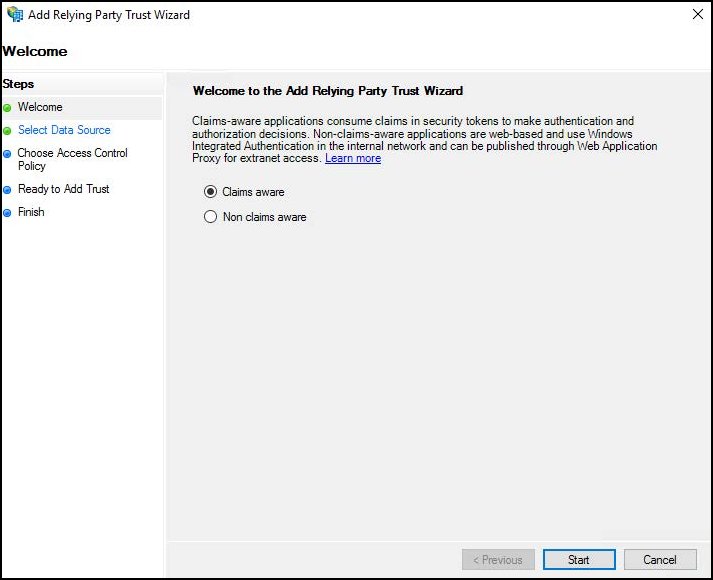
For Select Data Source, select Enter Data about the relying party trust manually and click Next.
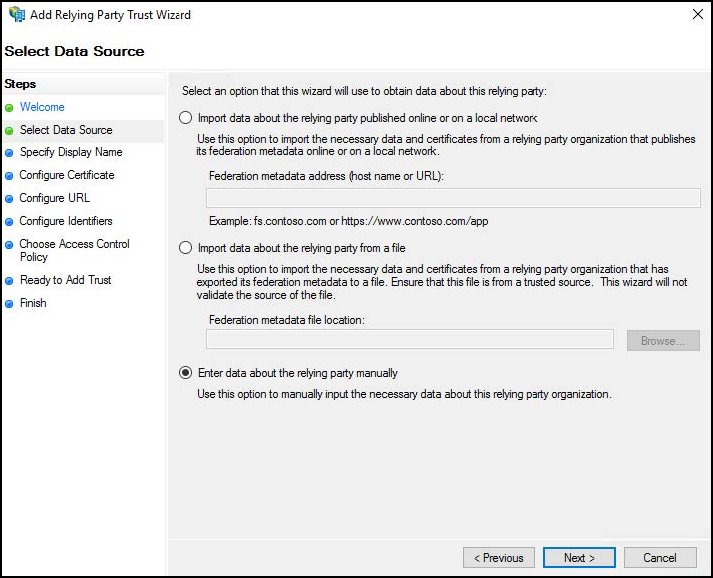
For Display name, enter a meaningful name, like Netskope Management Console, and then click Next.
For Configure Certificate, click Next and proceed to the next step.
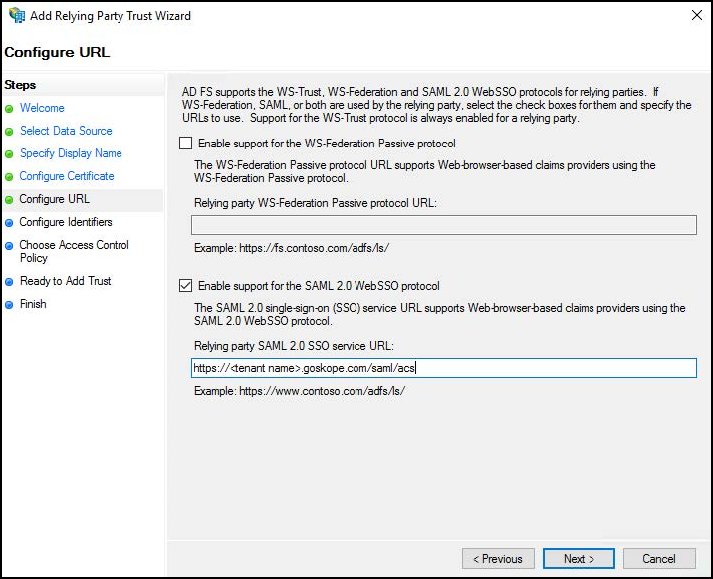
For Configure URL, select Enable support for the SAML 2.0 WebSSO protocol and enter the Netskope Assertion Consumer Service URL into ADFS, and then click Next.
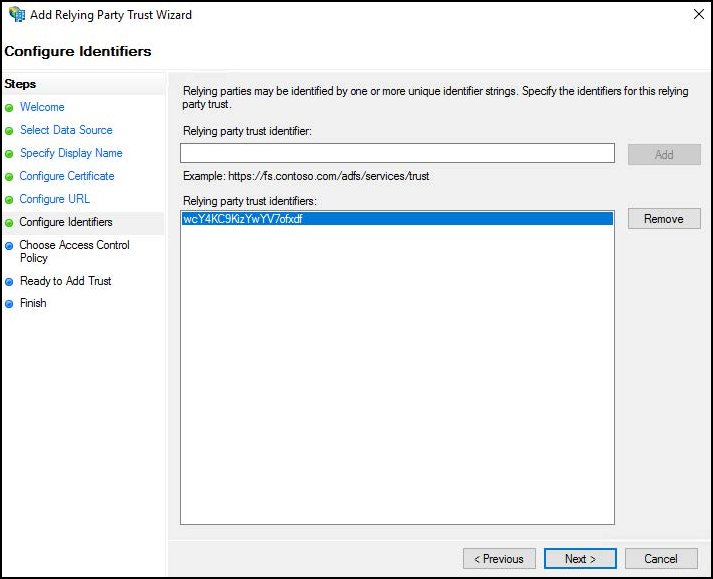
For Configure Identifiers, enter the Netskope Service Provider Entity ID into ADFS, and then click Add and Next.
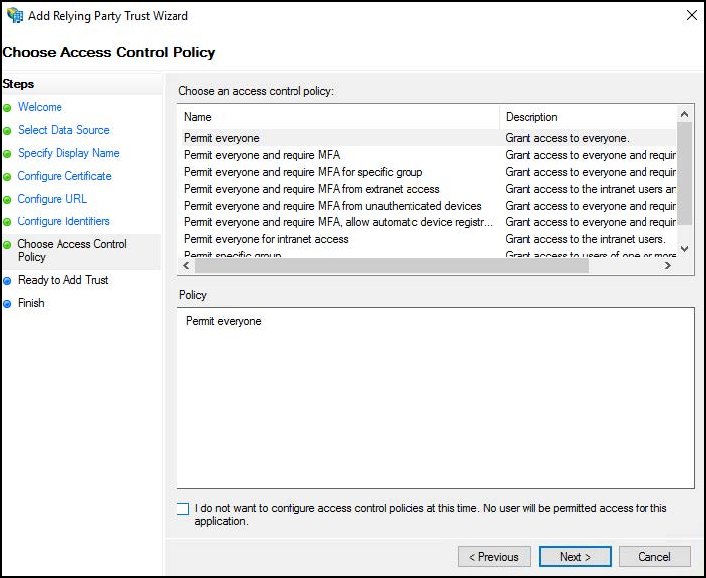
For Choose Access Control Policy, select Permit everyone and click Next.
For Ready to Add Trust, the wizard displays the configured settings. Click Next.
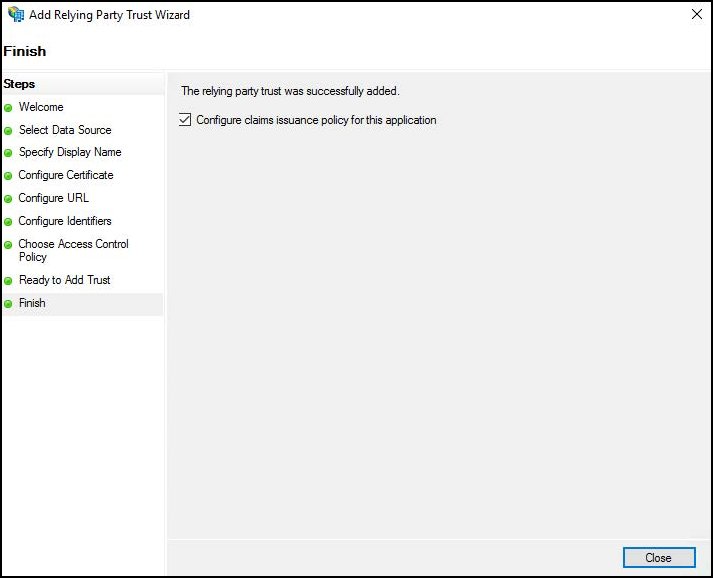
Click Finish to add the relying party trust to the database.
Enable the Configure claims issuance policy for this application checkbox and click Close.
In the ADFS Management Window, open the Trust Relationships > Relying Party Trusts folder. Right-click the relying party trust created earlier and select Edit Claim Issuance Policy. When the Edit Claim Issuance Policy appears, click Add Rule. For Choose Rule Type in the Add Transform Claim Rule Wizard, select Send LDAP attributes as Claims as the Claim Rule Template so claims contain LDAP attribute values from the AD attribute store. Click Next.
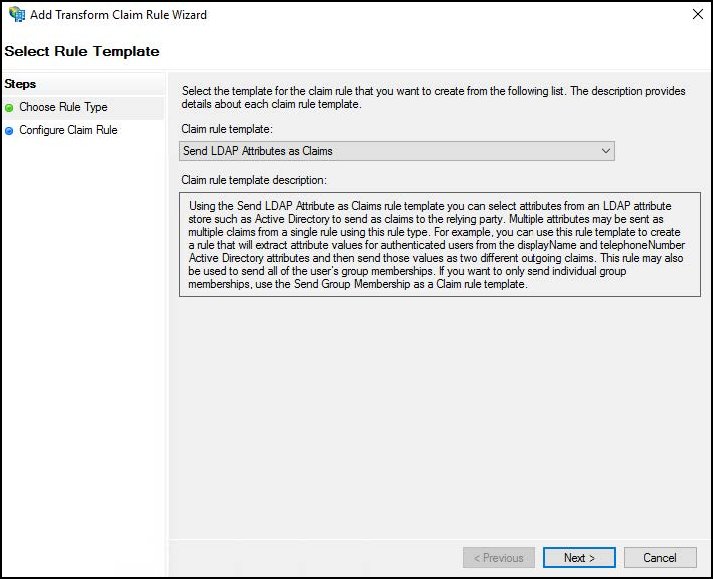
For Configure Claim Rule, enter and select the following:
Enter a name for the claim rule.
For Attribute Store, select Active Directory.
Map the LDAP attributes that represent the user’s login name to a field in the outgoing claim. In the LDAP attribute column, select E-Mail-Address. In the Outgoing Claim Type column, select or enter Name ID. (Note that Name ID is entered as two words, with a space between them).
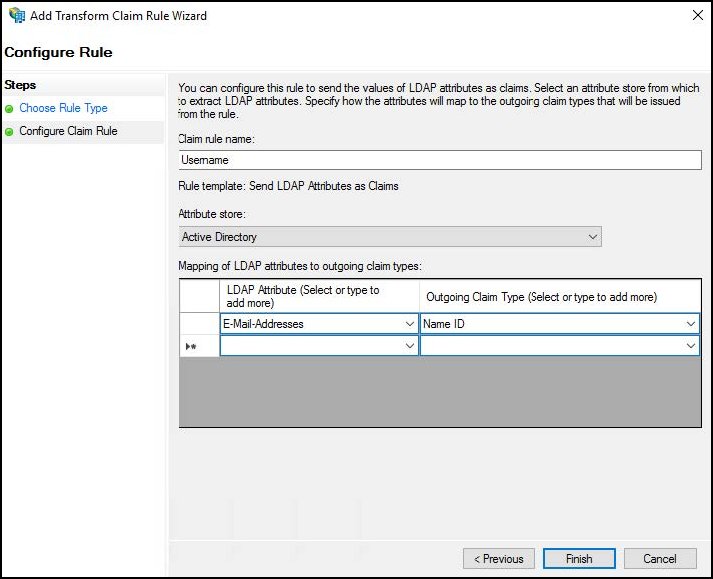
Click Finish.
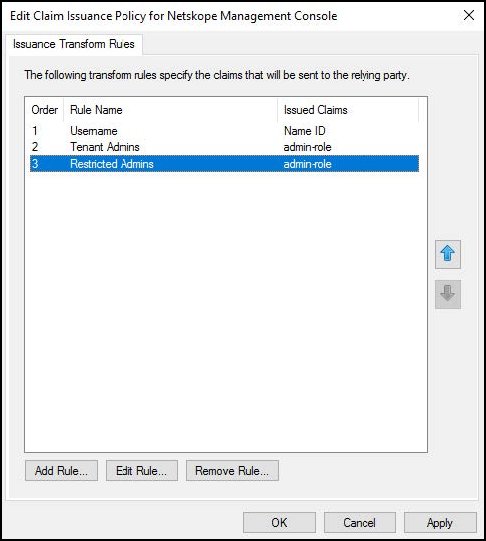
Add another Claim Issuance Policy rule. For Choose Rule Type, select Send Group Membership as a Claim, as the Claim Rule Template, and then click Next.
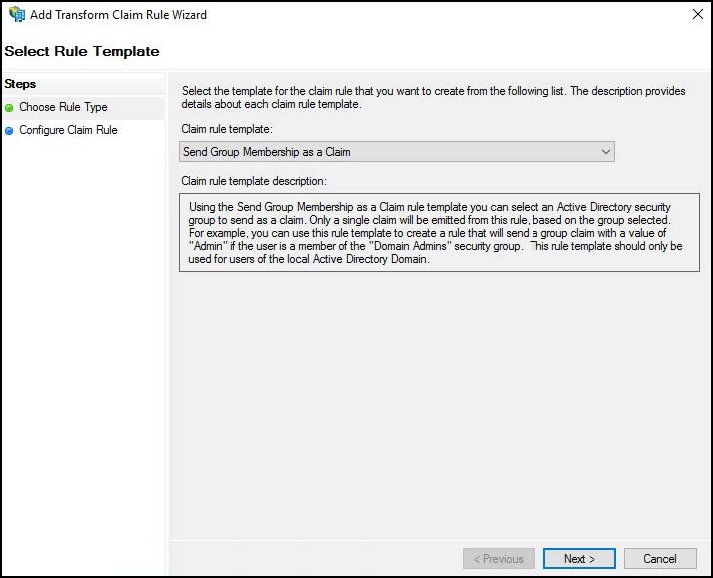
For Configure Claim Rule, enter and select the following:
Enter a name for the claim rule, like
Tenant Admins.For User's Group, browse and select the AD group that will be mapped to the Tenant Admin role in the Netskope UI.
For Outgoing Claim Type, select admin-role.
For Outgoing Claim Value, enter
Tenant Admin.
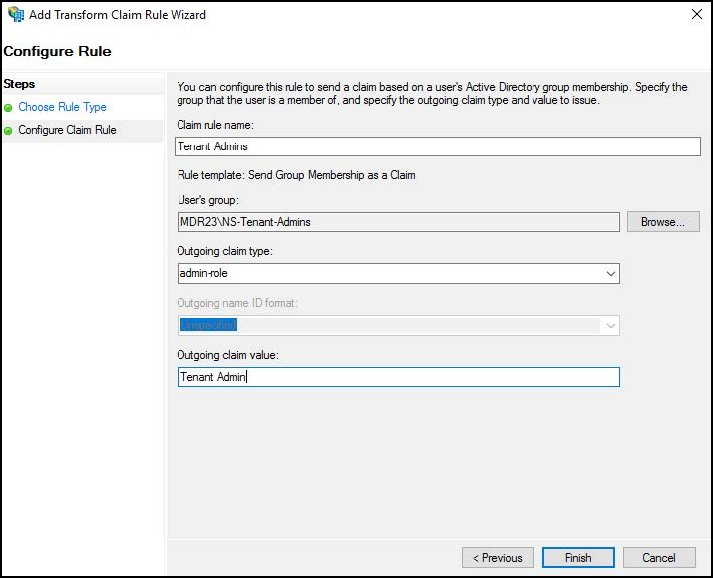
In this rule, users in the NS-Tenant-Admins group are mapped to the pre-defined Tenant Admin role on the Netskope UI. Click Finish.
Add another Claim Issuance Policy rule. For Choose Rule Type, select Send Group Membership as a Claim, as the Claim Rule Template, and then click Next.
For Configure Claim Rule, enter and select the following:
Enter a name for the claim rule, like
Restricted Admins.For User's Group, browse and select the AD group that will be mapped to the Restricted Admin role in the Netskope UI.
For Outgoing Claim Type, select admin-role.
For Outgoing Claim Value, enter
Restricted Admin.
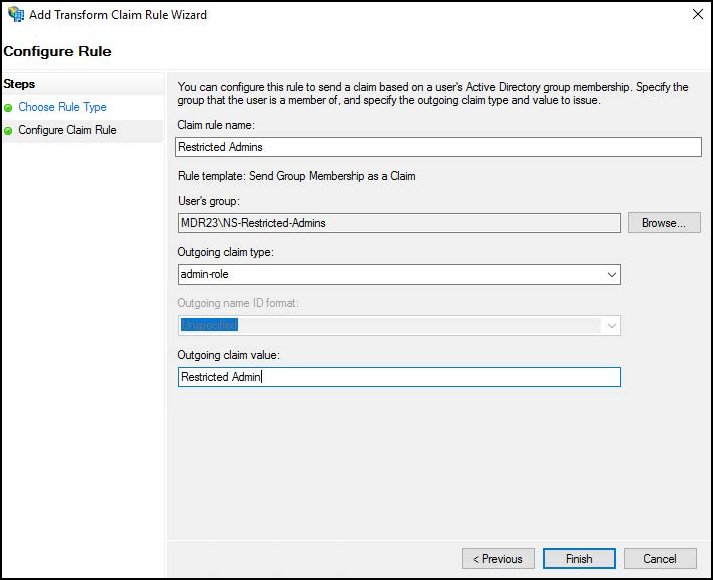
In this rule, users in the NS-Restricted-Admins group are mapped to the pre-defined Restricted Admin role on the Netskope UI. Click Finish.
Note
Configure further roles as needed.
In the Claim Issuance Policy dialog, click OK.
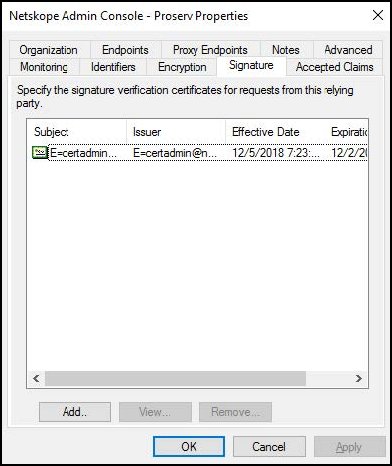
Open Properties for the newly created Netskope management console Relying Party Trust object in ADFS. Select the Signature tab, click Add, locate and select the Netskope SAML Certificate file, and then click OK.
Run the below PowerShell commands to disable the CRL Check:
PS C:\Users\Administrator> Set-ADFSRelyingPartyTrust -TargetIdentifier <org_key> -SigningCertificateRevocationCheck None PS C:\Users\Administrator> Set-ADFSRelyingPartyTrust -TargetIdentifier <org_key> -EncryptionCertificateRevocationCheck None
ADFS is now configured for Netskope SSO. Proceed to the Configure Netskope SSO for ADFS section to complete the integration.