Private App Management
The following sections explain how to create and steer Private Apps.
Create a Private App Definition for the Publisher to steer. A message appears on the Private Apps App Definition page when you're approaching the maximum limit. You can contact Support to increase the limit.
Go to Settings > Security Cloud Platform > App Definition and click Private Apps.
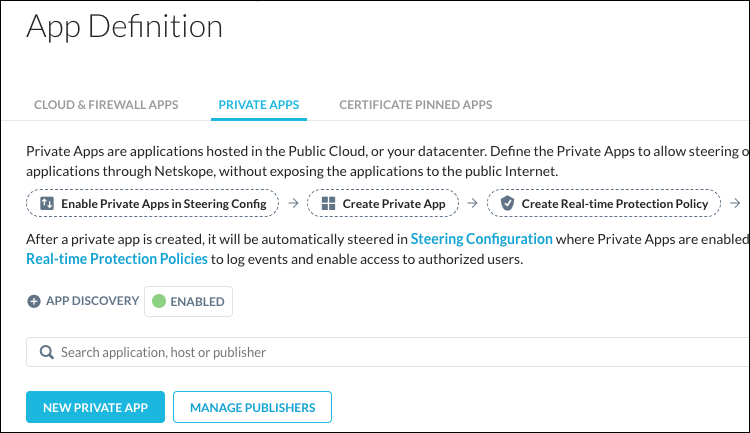
Click New Private App.
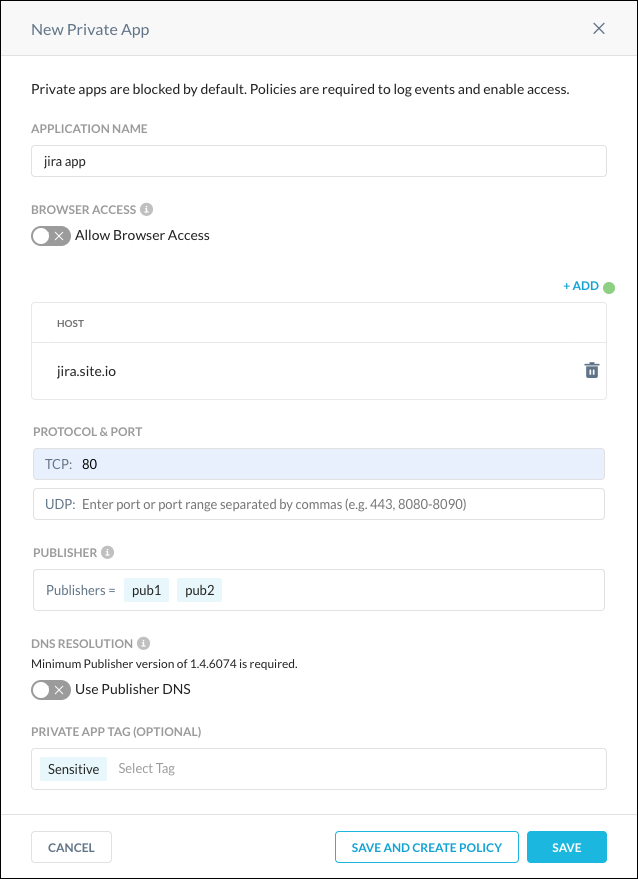
Enter a meaningful app name in the Application Name field (like
jira app).Enter the Host domain in the Host field (like
jira.site.io). The Host field supports the following syntax: Host (jira.site.io). Up to 500 hosts can be added.Important
Using a hostname is recommended. If an app needs to be accessible by hostname and IP address, enter each separately by clicking Add.
When using an IP address for a host domain, ensure the IP address differs from all IP addresses used for Publishers. Other IP factors include:
Don't use wildcards, like
*.com, and*.local, one level below the top-level domain. You can use wildcards two levels down, like*.test.xyz, for the purpose of private app discovery.Don’t use 0/0.
Don’t use any CIDR less than /8. For example, if
x.x.x.x/yis a configured CIDR, thenyshould be greater than or equal to 8. (eg 10/8 is allowed, 1/7 is not allowed).Don’t use TLD.
Don’t use ipv6 equivalents of 0/0:
“::”
“0:0:0:0:0:0:0:0”
“::0”
If the FQDN contains a .local domain, Netskope recommends one of the following for the Ubuntu-based Publishers:
Ensure Ubuntu publishers are running version 98 or later.
For Ubuntu publishers prior to version 98, execute the following commands on the publisher machines.
sudo rm -f /etc/resolv.confsudo ln -s /run/systemd/resolve/resolv.conf /etc/resolv.confdocker restart $(docker ps -a -q)
Enter the app TCP or UDP port, port range, or ports and port ranges. For example:
Enter a specific port:
80Enter a specific port range:
1024-2048Enter ports and port range(s):
22,80,443,1024-2048
Click in the Publisher text field and select one or more Publishers from the dropdown list.
Tip
For high-availability, add multiple publishers for each private app. Up to 16 Publishers can be used per app.
(Optional) To have the Netskope Client send DNS requests for the specified hosts to the configured Publishers, enable the Use Publisher DNS toggle. To learn more, go to Configure Private Apps for DNS with the Publisher DNS Feature Enabled.
(Optional) Private App Tags enable you to group multiple Private App Definitions for use in a Real-time Protection policy. Select one or more Private App Tag(s) from the dropdown list. To add a new Private App Tag, click Create New Tag. To learn more, go to Use Private Apps Tags in App Definitions.
Click Save.
Connecting the Private App to the Publisher may take several minutes. Make sure that you see the green icon  for this Private App before proceeding. If the badge is red, use the Troubleshooter feature or check your firewall rules before proceeding.
for this Private App before proceeding. If the badge is red, use the Troubleshooter feature or check your firewall rules before proceeding.
Note
When a user has access to a private app on different tenants using Netskope-encoded Private App URLs from the same browser, then after accessing the Private App on one tenant, a user will need to clear the cookies from the browser before being able to access the Private App on a different tenant.
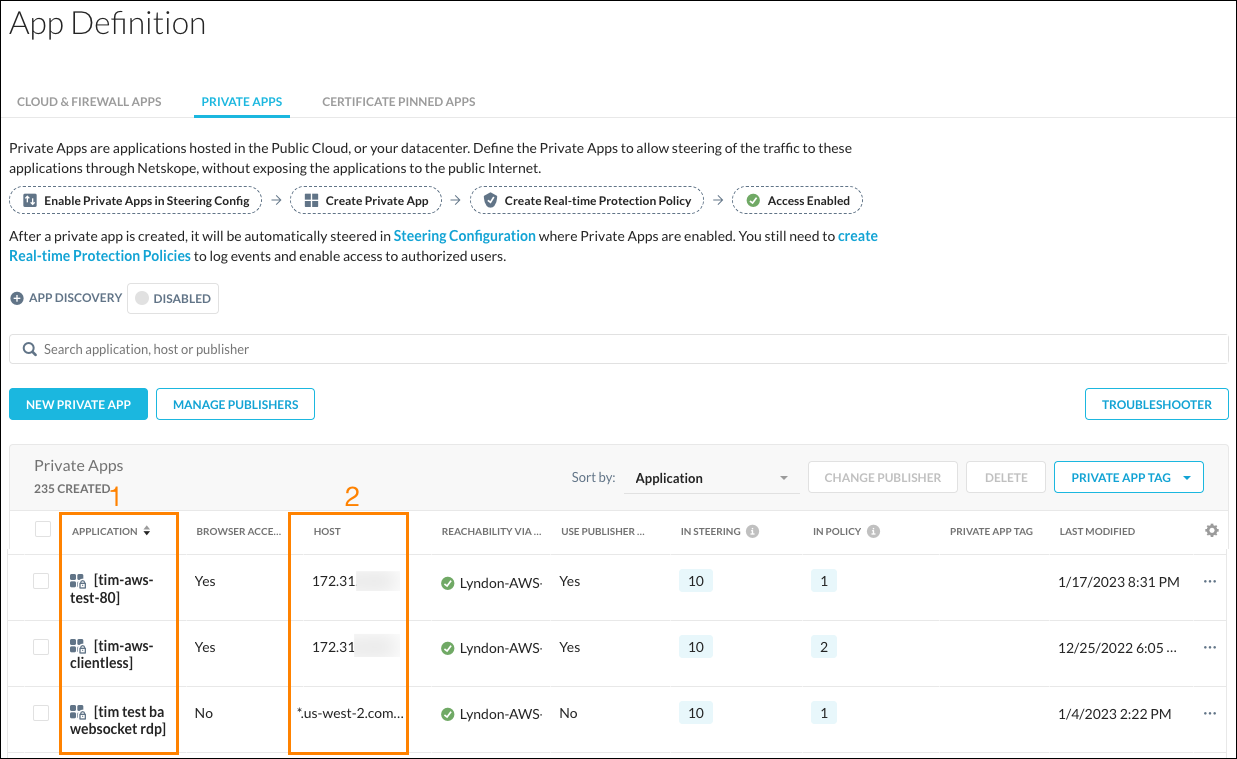
The Private App Definition page shows these specifications for each Private App.
Whether App Discovery is enabled or not.
The Private App name.
Whether Browser Access is enabled or not.
The host IP addresses or IP subnets, hostnames, or wild card domains.
The status of the Publisher connection, and the name of the Publisher used.
Whether Publisher DNS is enabled or not.
The number of steering configurations used.
The number of policies applied to a Private App.
Any Private App tags used.
The last modification date.
 |
Troubleshoot a Private App
To troubleshoot a private app:
Click Troubleshoot on the Private Apps page.
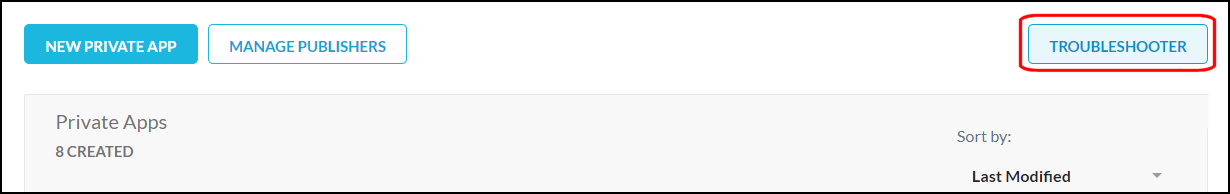
Select an option for these settings:
Private App: Select an app from the dropdown list.
User and Device: Search for and select a user and device, or select one or more from the list.
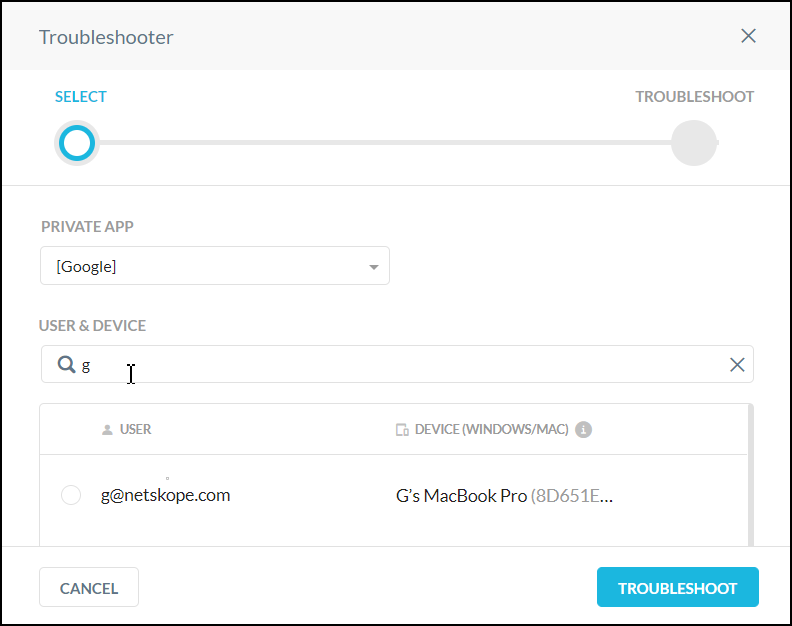
Click Troubleshoot. If the configuration is not correct, the troubleshooter will show what is not configured properly.
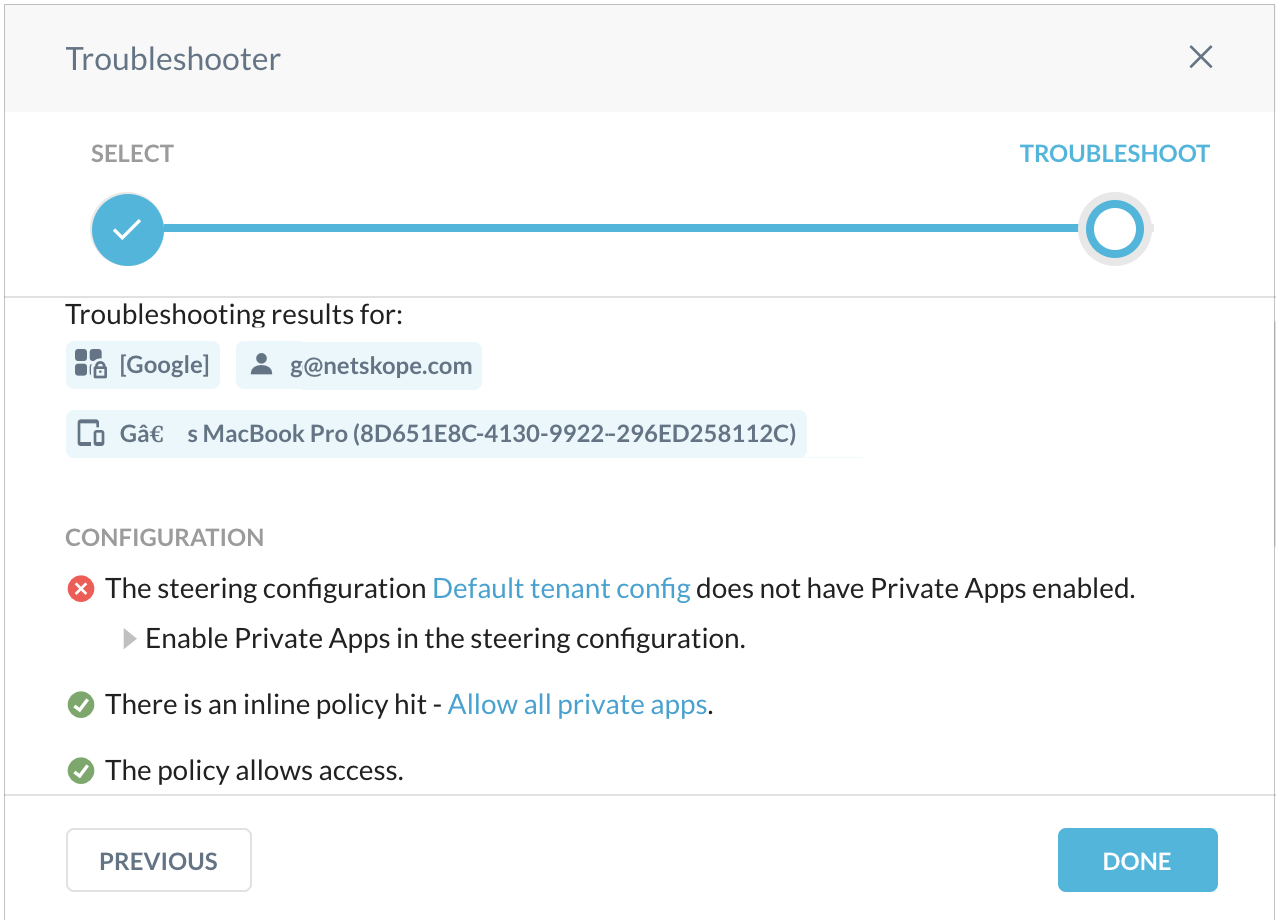
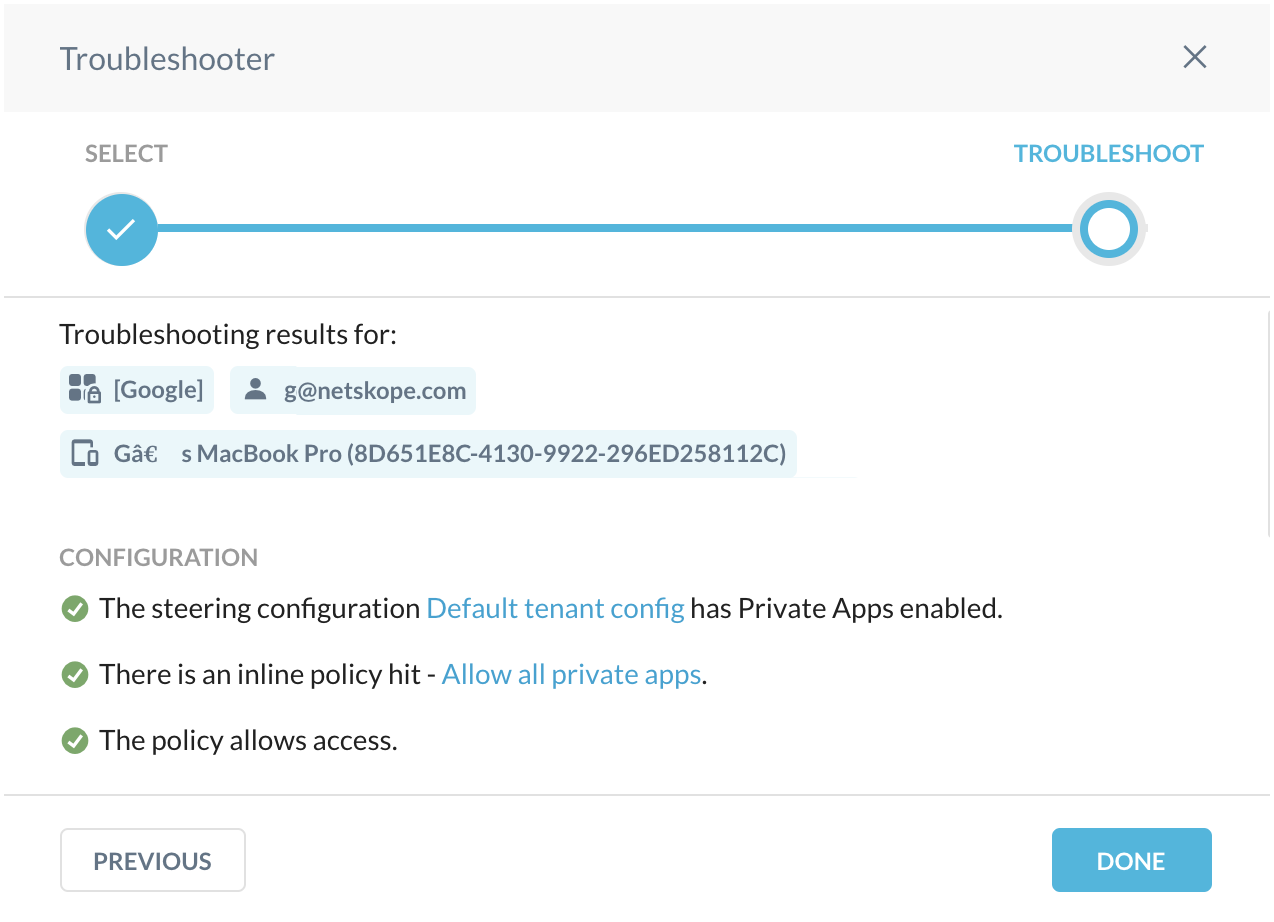
When the configuration is correct, the Troubleshooter will show all is working.
For more information about troubleshooting, refer to the Private Access Troubleshooting .
When migrating to ZTNA-based solutions, you may want to retain the same user experience for their users. One of the frequent requirements is the ability to support application access by PQDN (a short name). For example, instead of app1.example.com, a user could type app1 in the browser. Within the boundaries of a corporate network (either campus or VPN), this works seamlessly because the user’s device receives the DNS search domain from a corporate DHCP server. This search domain is an actual example.com string that gets appended to every partial DNS query before sending it out for resolution.
Netskope Private Access (NPA) can support access by short names with a few simple configuration tweaks. All required NPA Publishers should have DNS search domain(s) configured, either manually or via DHCP settings.
Application should be defined by both PQDN and FQDN. In order to enable this capability, you will have to make your configurations more granular because a simple wildcard-based approach (like *.example) won’t allow you to access apps by short names.
In the Netskope UI, go to Settings > Security Cloud Platform > App Definition, click Private Apps, and then click New Private App.
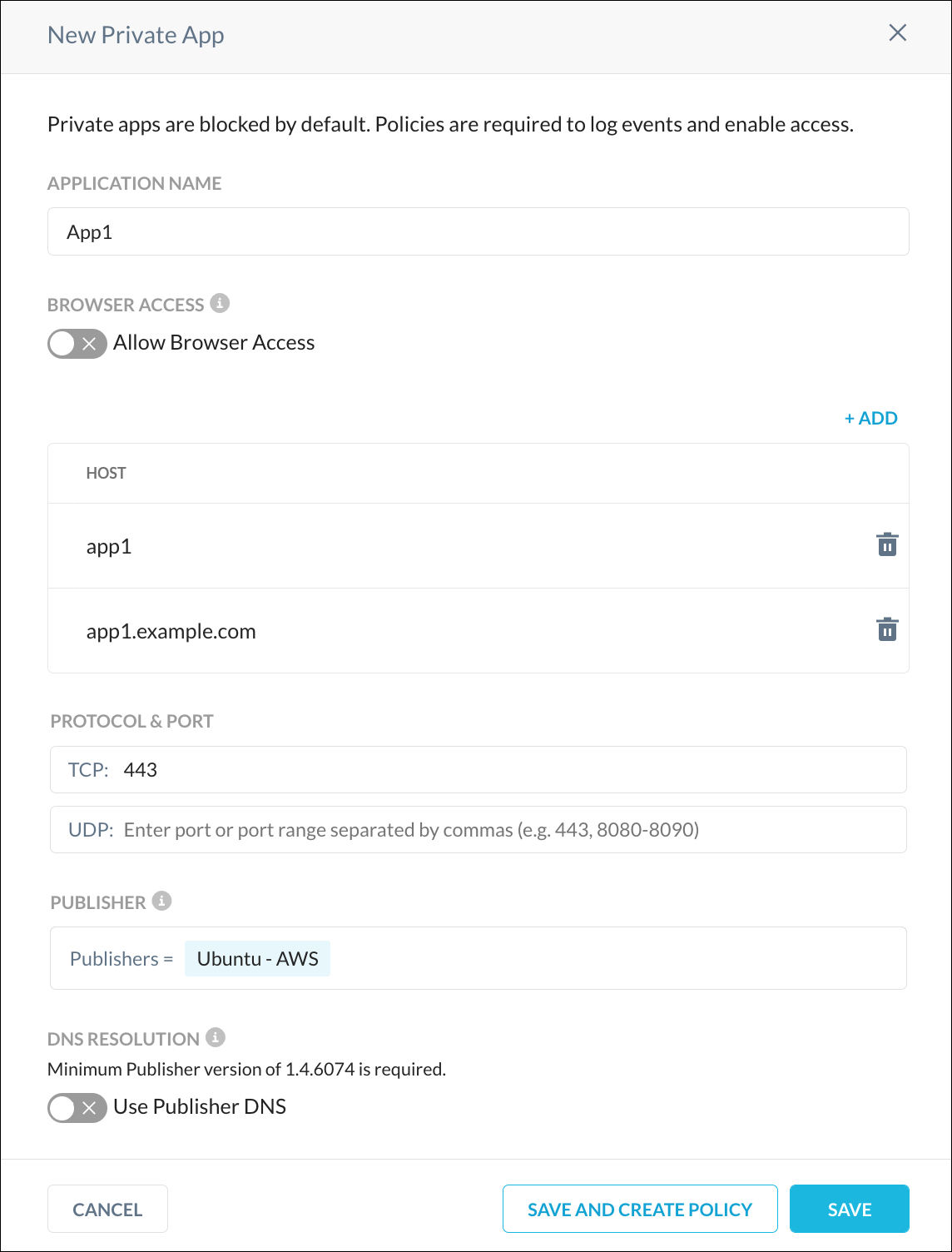 |
Enter an Application Name, add the PQDN and FQDN host names, enter a port, and select a Publisher. Publisher DNS mode is not supported for short name access and should be disabled. When finished, click Save.
After creating this new Private App, create an appropriate real-time policy for the Netskope client to receive the Private App definition in the form of both short and full name. When the user will try to access application by short name, the Client will respond with a dummy IP. In the meantime, the Publisher will append a DNS search suffix to the query.
Note
Multicast DNS (mDNS) within the Netskope Client is not supported.
When deploying Netskope Private Access as a ZTNA product, it may not be clear how your enterprise applications work (like ports necessary), and whether there is a reliance on other hosts to make the applications function correctly. App Discovery is a cornerstone for the successful deployment of a ZTNA product.
When configuring Private App Discovery in a production environment, using a dedicated Publisher for app discovery is recommended.
On the Private Apps page, click the + icon beside App Discovery.
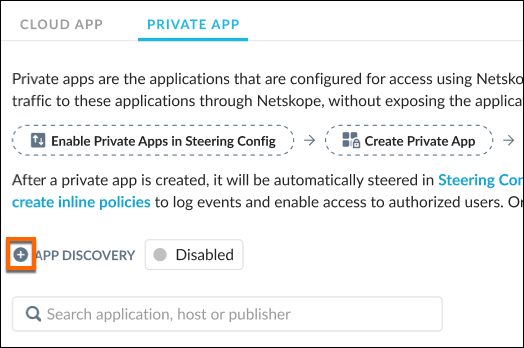
Click Edit.
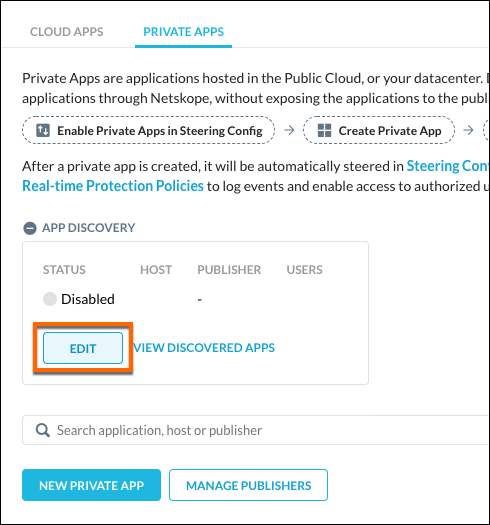
Enter these parameters:
Host: Enter a Hostname for the DNS-based Private Apps and click Add. You can also enter a CIDR or IP addresses for IP-based Private Apps.
Publisher: Select the Publisher dedicated for the Private Apps.
User: Enter the user(s) that will access the Private Apps.
Status: Enable Allow.
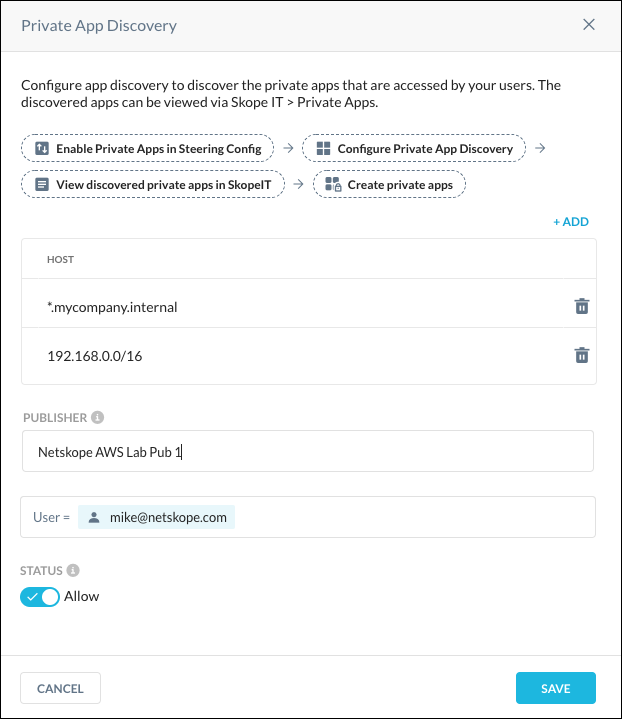
Click Save. The App Discovery Status is now green (Enabled) on the Private Apps page.
Have users start generating traffic using the Private Apps.
Once App Discovery is Enabled, NPA will allow access to the Apps covered by the App Discovery definition, unless there is a more specific rule in a Real-time Protection policy that blocks access to the requested App. An explicit rule in a policy is not required for a Discovery definition.
To create a Private App Definition for a Discovered App, click the + icon beside App Discovery, and then click View Discovered Apps.
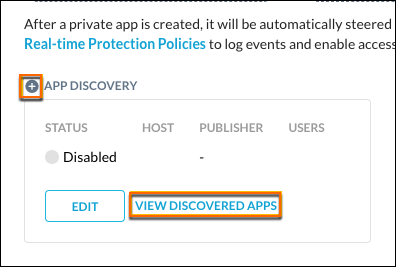 |
To create an App Definition for a single Discovered App, click the menu icon for a Discovered App, and then click Create Private App.
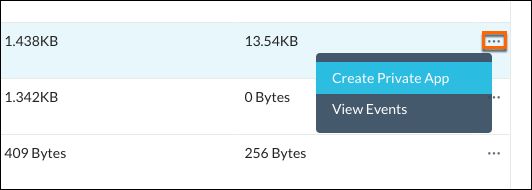 |
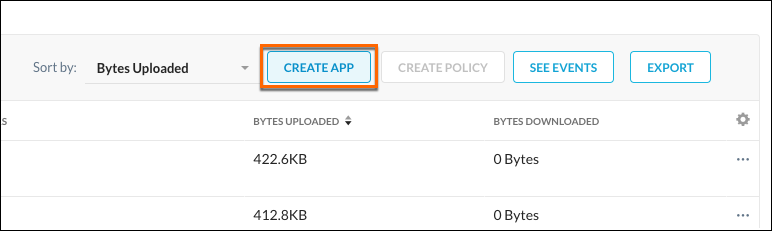
To create an App Definition for multiple Discovered Apps, select the Discovered Apps, and then click Create App in the table header.
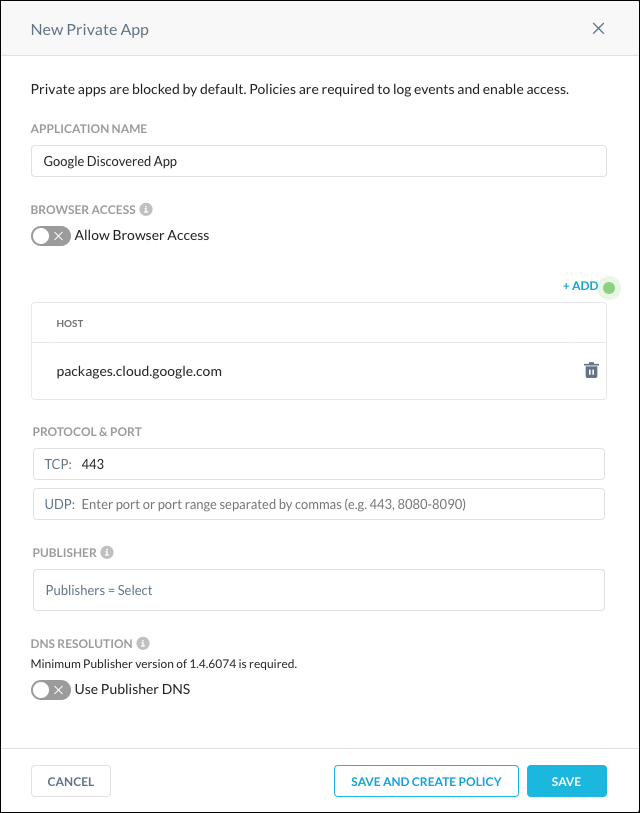 |
Enter a Application Name and click Save. This new App Definition can now be used in a Real-time Protection policy.
If you select multiple Discovered Apps, and the Discovered Apps have different Publishers and ports, the new App Definition will include all Publishers and ports across the selected apps. This may result in certain Publishers being unable to access selected applications.
 |
You can also add a Discovered App to an existing App Definition. Select the existing App Definition and the Discovered App(s) to add to the App Definition, and then click Create App. Review the settings and click Save.
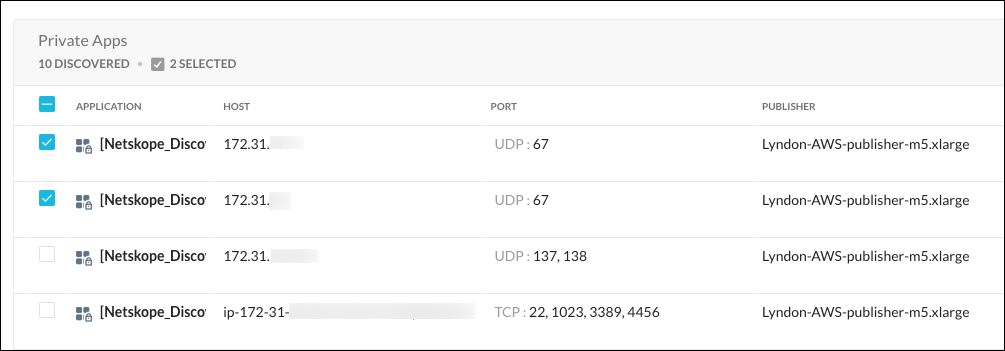 |
After users generate traffic via Netskope Private Access, on the Private Apps page, click the + icon beside App Discovery, and then click View Discovered Apps.
 |
Another option is to go to Skope IT > Private Apps and click the + icon beside App Discovery, and then click View Discovered Apps.
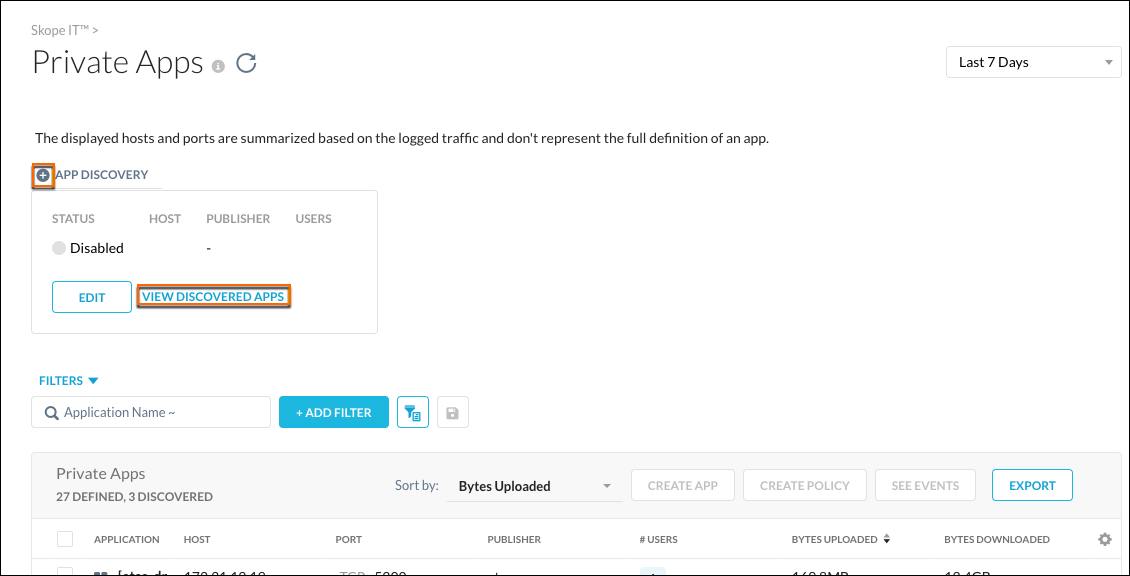 |
This page shows:
Discovered Application Names
Hosts
Ports
Publishers
Number of users
Bytes Uploaded
Bytes Downloaded
Private App Tags enable you to group multiple Private App Definitions for use in a Real-time Protection Private App policy, which alleviates having to choose multiple Private App Definitions in a policy. Instead, you select the Private App tag in a policy that includes multiple Private App Definitions.
Private App Tags can be applied to new and existing Private App Definitions. In the App Definition dialog box, click in the Private App Tag text field and select one or more tags. To search for a tag, starting entering the name, and then select it when it appears. After adding a Private App Tag to an App Definition, the tag name is shown in the Private Apps Tag column on the App Definition page.
The v2 REST APIs can be used to incorporate Private App Tags in App Definitions. In your Netskope tenant, go to Settings > Tools > REST API v2 and click the API Documentation link. In the Swagger UI, look for the /api/v2/steering/apps/private/tags endpoints. To learn more, go to: REST API v2 Overview.
You can create a Private App Tag when creating an App Definition, or create a new tag when editing an existing App Definition. In both cases, click in the Private App Tag field in the App Definition dialog box, and then enter a tag name. When you see the new tag at the bottom of the list, click Create New Tag and then Save. The new tag now appears in the list and can be used in a Private App policy.
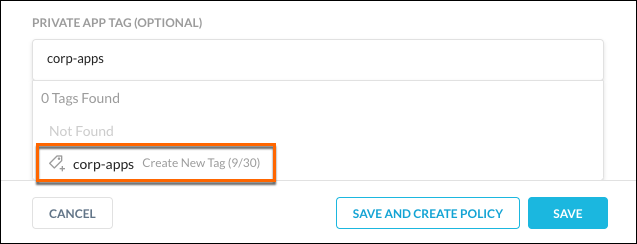 |
After adding a tag to a Private App Definition, the name appears in the Private App Tag column on the App Definition page.
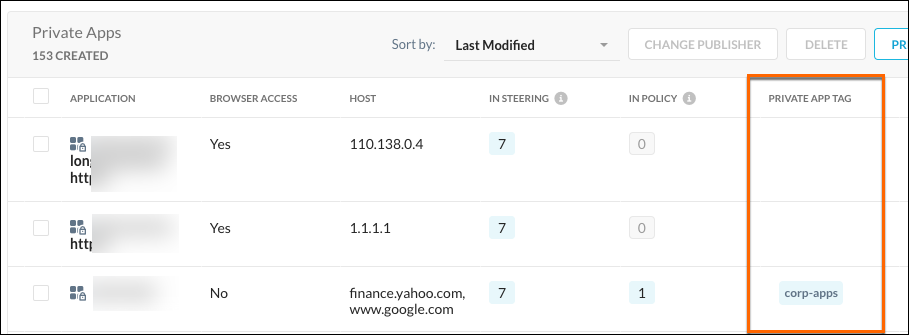 |
You can bulk add or delete Private App Tag(s) in one or more App Definitions. Select the App Definition(s) in the left column of the App Definitions page, and then select Edit Tags from the Private App Tag dropdown list. Renaming a tag is not supported.
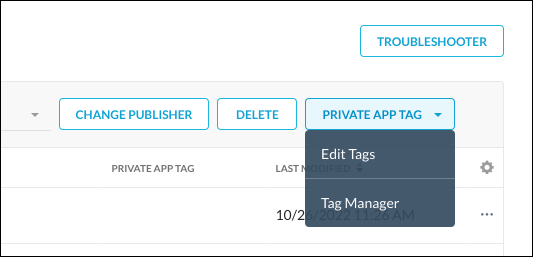 |
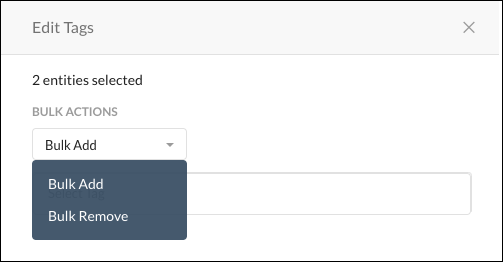
In the Edit Tags dialog box, choose to do a bulk add or bulk remove for the tags you will select next.
 |
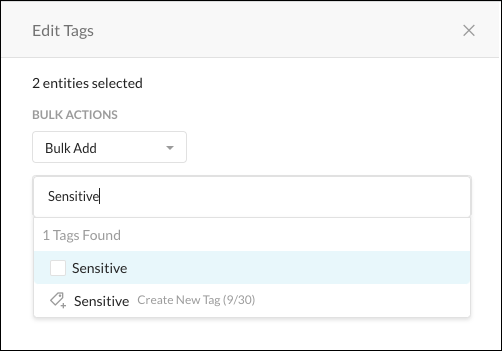
Search for the Private App Tags by entering text in the search field, or select the tag from the dropdown list.
 |
When finished, click Save.
You can bulk add or delete Private App Tag(s) in one or more App Definitions. . Select the App Definition(s) in the left column of the App Definitions page, and then select Tag Manager from the Private App Tag dropdown list.
 |
In the Manage Tags dialog box, search for the Private App Tags by entering text in the search field, or select the tag from the dropdown list.
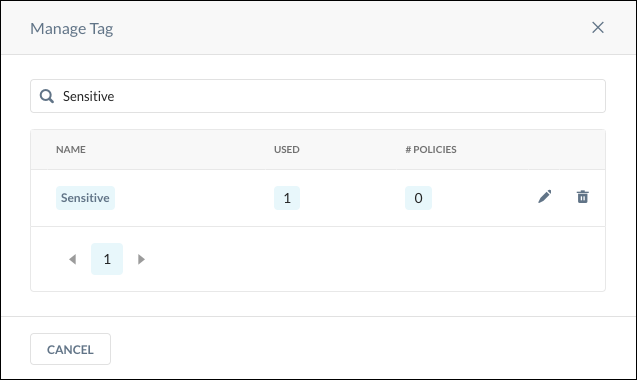 |
The Pencil icon allows you to rename the Private App Tag, and the Trash icon allows you to delete the tag. When finished, click Save.
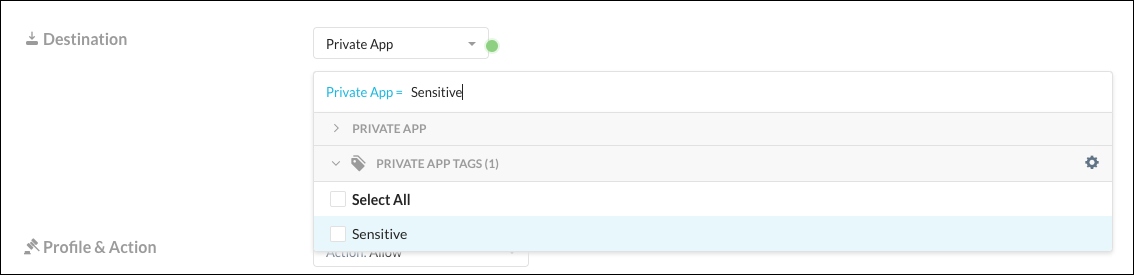
When creating a new policy, or updating an existing policy, you have the option to select Private App Tags in addition to selecting Private Apps. For Destination, click on Private App Tags to select the tags you want to include in the policy.
 |
To steer traffic for private apps, you can add users or create a steering configuration that specifies an Organizational Unit (OU) or User Group.
OUs or User Groups are specified in the Real-time Protection policy that grants access to private apps.
If you do not already have a steering configuration that specifies the Organization Unit (OU) or User Group you want to steer to a private apps, follow these steps.
If you already have such a steering configuration, you can simply enable private apps for that steering configuration. For more details, refer to Change Steering Configurations to Include Private Apps.
Go to Settings > Security Cloud Platform > Steering Configuration and click Create a New Configuration.
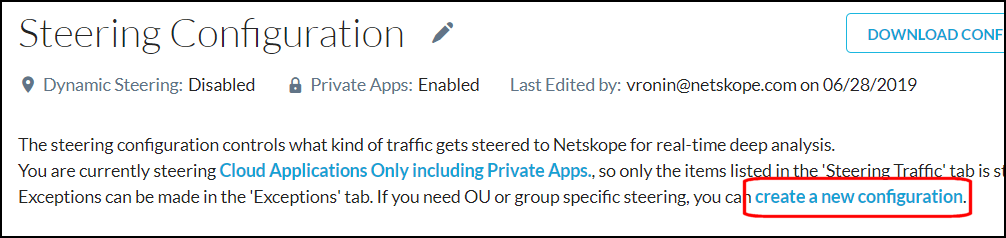
In the New Configuration dialog box, enter and select the following settings:
Configuration Name: Enter a meaningful name for this steering configuration.
Organizational Unit (OU)/User Group. The dropdown/search field allows you to select and search for an OU or User Group.
Traffic: Select Cloud Apps Only or All Web Traffic.
Status: Change to Enabled.
Private Apps: Change to Steer All Private Apps.
Click Save.
To update a steering configuration for private apps, follow these steps:
Go to Settings > Security Cloud Platform > Steering Configuration. Complete the following steps for each steering configuration that you want to steer to private apps. There are two methods:
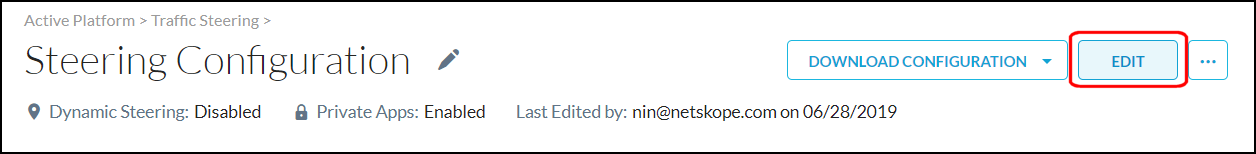
If you have just one Default steering configuration, you can use the Edit button in the top right corner.
If you have multiple steering configurations, click the
 icon on the right side of each configuration and select Edit Configuration.
icon on the right side of each configuration and select Edit Configuration.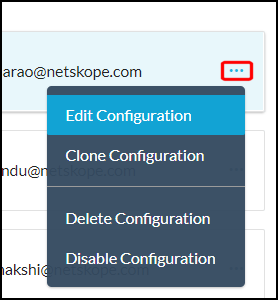
For Private Apps, change to Steer All Private Apps.
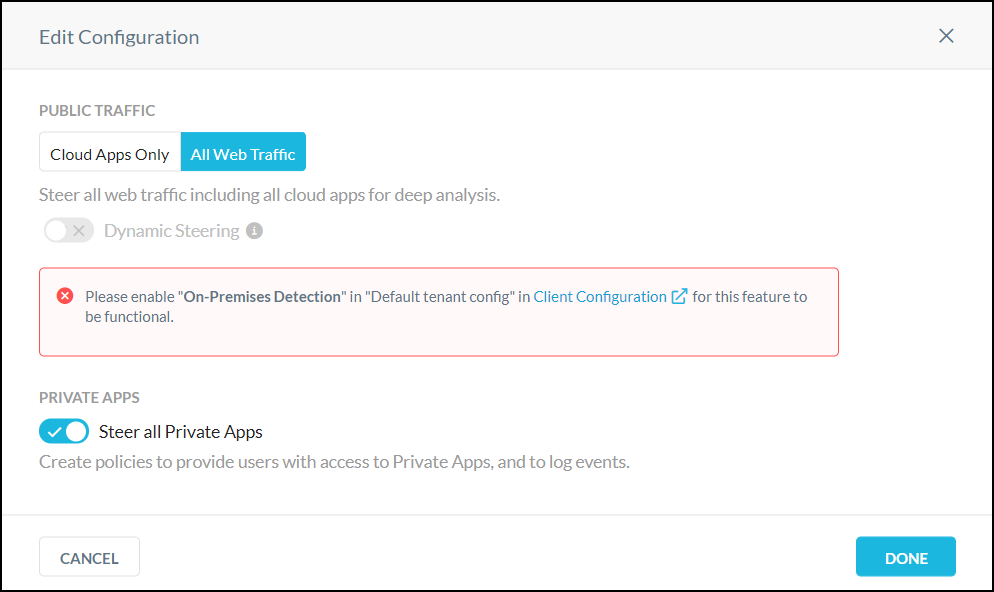
Click Done.