Netskope Client Configuration
You can configure system-wide settings using the Client Configuration dialog box. To access client configuration pages:
Log in to your tenant with admin credentials.
Go to Settings > Security Cloud Platform > Devices
Click Client Configurations in the top right corner to open the Client Configuration page.
Click New Client Configuration to add a new global configuration.
Additional configurations can be created to obtain granular control over the behavior of the Netskope Client at a group or OU level by creating a new configuration. If these configurations are applied to groups, they must be prioritized to determine which configuration is applied to the Client when there is an overlap in group membership.
Note
Multiple configurations can be created and applied to different OUs or Groups. But when applying a configuration only one OU or User Group can be selected.
The Client configuration name cannot exceed 40 characters.
Applies To
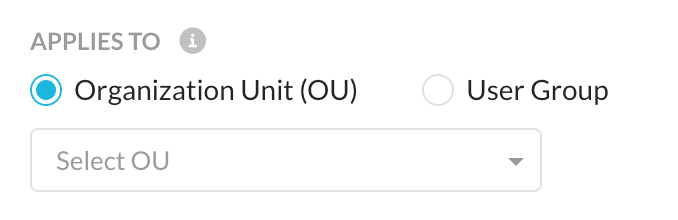 |
Select OU (Organizational Unit) or the User Group to which this configuration will be applied. You can apply the configuration either to the OU or the user group but not to both at the same time. If a user is part of multiple groups, the configuration is applied to first group in the configuration list.
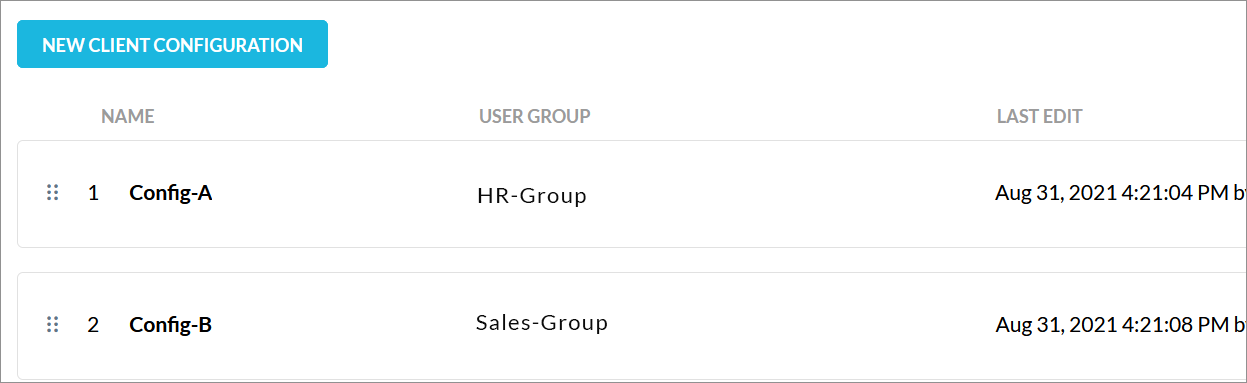
For example: John Doe is part of HR-Group and Sales-Group. The organization creates Config-A and Config-B and applies to HR-Group and Sales-Group respectively. If in the list of configurations, HR-Group is listed above Sales-Group, then only the Config-A settings are applied to John Doe. The settings in Config-B is applied to all users in Sales-Group except John Doe. The Default Config is then applied to all users who are not part of HR-Group and Sales-Group. To apply the configuration to John Doe in Sales-Group, use the reorder handles (first column dot-icons) to drag and reposition the configuration.
 |
 |
Enable DTLS (Data Transport Layer Security) - Enable DTLS (Data Transport Layer Security). Optionally, enter an MTU value.
Note
It is recommended that you enable this option, if you have users connected to a lossy network.
Enabling DTLS option supersedes TLS (Transport Layer Security) tunnel for communication thereby improving the network process. TCP inherently slows the overall flow performance if the network has high latency and packet drops. To overcome this issue, use DTLS tunnel (UDP tunnel). To know the current protocol, click the Client icon > Configurations > Tunnel Protocol.
The connection can fallback to TLS in the event of a DTLS connection issue. For example, the firewall blocking UDP traffic or data getting fragmented. To switch to DTLS, you can perform one of the following:
Manually disable and enable the Client.
Switch your network.
After enabling DTLS, you are prompted to enter the Maximum Transmission Unit (MTU) value. This value determines the number of bytes sent to a server. With Netskope Client, the maximum configurable value is 1500.
Supported TLS/DTLS version: 1.2
On-Premise Detection - For On-Premises Detection, enter either your DNS FQDN and IP address or HTTP FQDN and connection timeout period that can be resolved with a known IP address. By enabling this option, you can detect the location of an endpoint. If the endpoint is on-premises or off-premises the Client tunnels the traffic based on the traffic mode configured for dynamic steering.
Use DNS
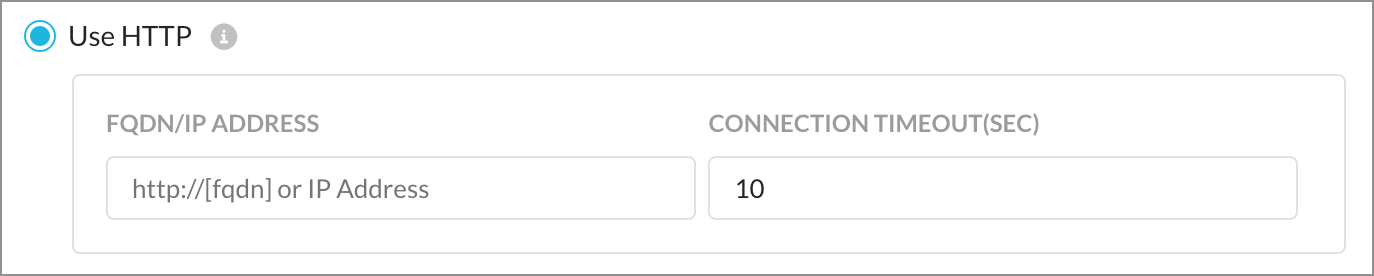
Use HTTP
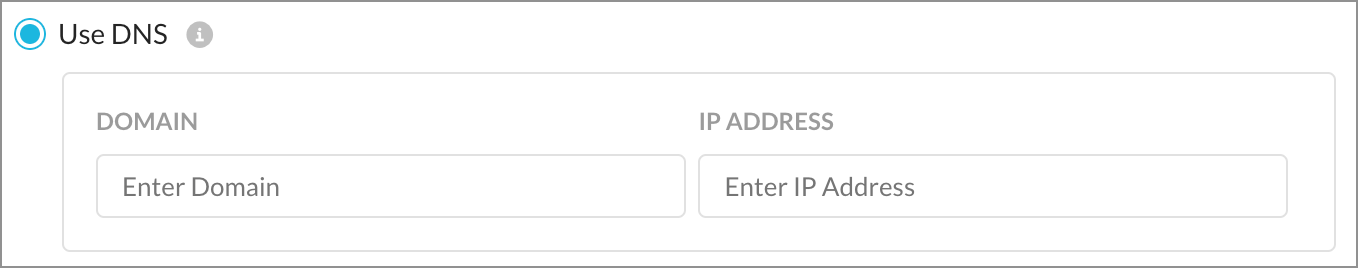
If the FQDN entered resolves to the provided IP Address, the Netskope client is considered to be on-premises. Please make sure this is a valid DNS record that is resolvable only when on your network
If the Client looks for the HTTP response code 200, and if successful, the device is deemed to be on-premises. Also enter a connection timeout value. The default is 10 seconds, and the max is 60 seconds.
Note
When a proxy server is available for Netskope Client, HTTP requests go to the proxy server from Netskope Client
Netskope Client release 72 or higher is needed for this feature to work.
On-Premises: If the endpoint is on-premise, the client will tunnel the following types of traffic and this traffic is bypassed by the Netskope Cloud
Cert pinned apps
Exception domains
Exception categories
Off-Premises: If the endpoint is off-premises, the client will bypass traffic based on the exception configurations.
Periodic re-authentication for Private Apps - Enable the Periodic re-authentication for Private Apps option to force a user to re-authenticate into the Netskope Client if the user’s device restarts, or logs out of the PC and logs back into the device. Contact Support to enable this functionality in your tenant.
Select a time period from the Re-Authentication Interval dropdown list for how often you want re-authentication to occur. To allow a user time to re-authenticate after the specified interval time has expired, enable the Grace Period checkbox and enter the minutes. The grace period must be less than the interval.
Pre-logon for Private Apps - Enable this option to allow the device to connect to the private apps. In the pre-login state, the device can authenticate to the Netskope cloud and access limited resources. After you enable the pre-logon option:
Enter a pre-logon username.
Note: The email address always end in “@prelogon.netskope.com”. This is used to create a local user for pre-logon in the next section.
To use a device certification authority, click Select File to upload the certificates in PEM format.
To validate the device certificate against a Certificate Revocation List, enable Validate CRL. The CRL used to validate the device comes from the CA certificate.
Enable Start Pre-logon tunnel when user tunnel disconnects. This enables the Client to always try to re-establish the pre-logon tunnel when the user tunnel switches from connected to disconnected, even when the user disables the Client.
Warning
If you enable this option, users cannot fully disable the Client while using pre-logon. To allow users to fully disable the client, do not select this checkbox.
Periodic Validation on Device Classification - Enable this option to run periodic device classification validations. You can set the time( in minutes) while choosing this option.
Note
Keeping shorter time intervals can affect your device performance.
After enabling, the Client:
Monitors the processes, files, or other criterias configured in Device Classification.
Classifies that device as unmanaged in the event of any change in the criteria.
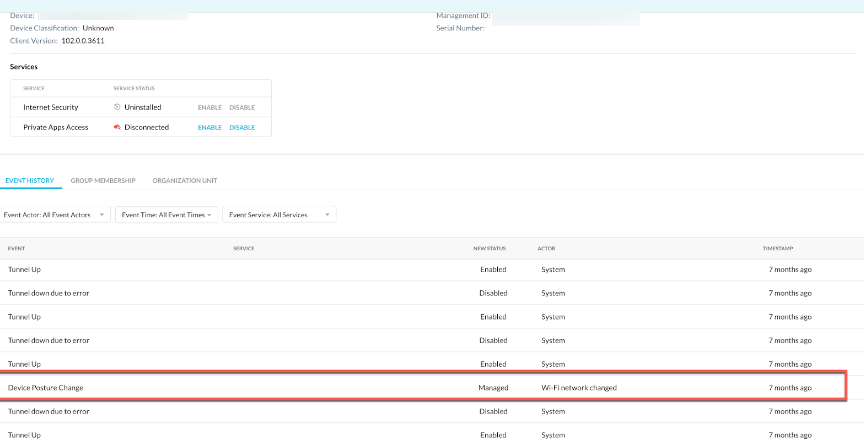
You can view the event details in Settings > Security Cloud Platform > Device details > Event History tab. In this section, check for the event Device Posture Change to understand the events in your device. The following events trigger a recheck of the device posture:
Network joined
Wi-Fi network joined
System wake up
For example, when a device connects to Wi-Fi, it triggers the Device Classification scan and checks if the current status of the device matches with the rule. The status is updated only when:
There is a change in the device status.
The current status do not match the previous status. If the previous status is unmanaged and after the device classification scan, the current status changes to managed, the New Status column in the device details user interface displays the updated status.
Advanced Options - Toggle the Advanced link to see the following options:
Interoperate with Proxy - Using this feature, the administrator can now configure proxies irrespective of their location in Netskope Client Configuration. By default, Netskope Client automatically detects the configured proxy by connecting to addon-<tenant> <MP>.goskope.com, where MP = eu|de|au. If the PAC(Proxy Auto-Configuration) file redirects some traffic to other proxies, it is mandatory to declare them in the Interoperate with Proxy settings.
Netskope Client always detect and intercept traffic that is sent to proxies declared in Interoperate with Proxy. Even though it is not mandatory to select this feature, you can use it whenever multiple proxies are deployed in the Network. Netskope Client always analyze requests sent to proxies defined in the Interoperate with Proxy settings based on the steering configuration to decide if the requests should be intercepted or bypassed.
The Netskope Client also conducts an availability check to select the proxy to use to contact Netskope Cloud services. The Netskope Client performs this check when:
The Client service starts.
Updates in the Client configuration.
Modifications in the proxy settings.
Change in the network.
Availability check is performed by contacting addon-<tenant><MP>.goskope.com. The auto detected proxy is always the preferred proxy to contact Netskope Cloud services.
After you configure the proxies along with the Port, Netskope Client checks for the system proxy along with the configured proxies and verifies if any proxy is reachable:
If the system proxy is reachable, the Client connects to the local proxy.
If the system proxy is unreachable, the Client checks with the other proxy IP addresses configured on the UI.
Supported platforms: Windows and macOS
Select the option Interoperate with Proxy to enable this feature and add multiple proxy IP addresses.
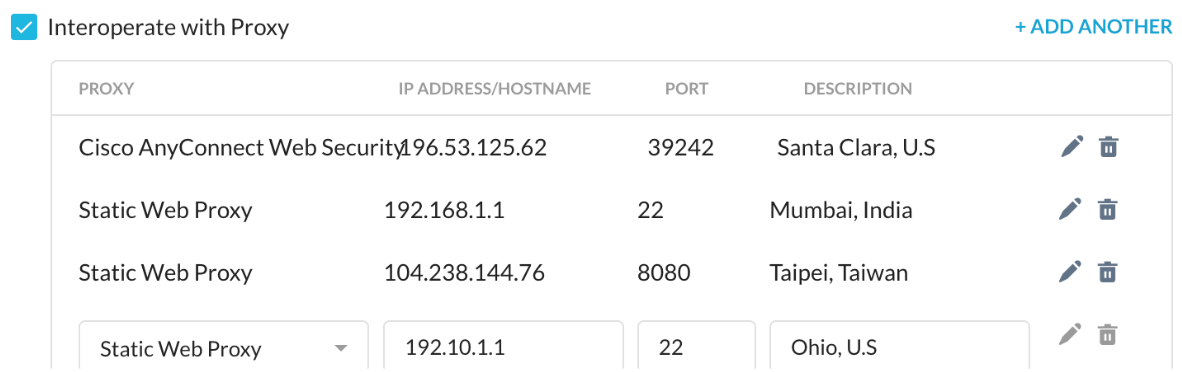
Interoperate with Proxy Workflow
The following steps describe working of Netskope Client when an administrator selects Interoperate with Proxy:
Netskope Client downloads the Client configuration that consists of all Client configurations. By default Netskope Client checks the configuration every hour and can be forced with manual update.
The Client checks if the Interoperate with proxy feature is enabled and checks if the proxy IP addresses are configured in the Client Configuration WebUI.
Afterwards, Client checks if any system proxy is configured. If yes, then the client uses that system proxy along with the configured and available proxies.
Note
Note: Preference is given to the system proxy rather than the configured IP address.
The Client then performs health check to all proxies to identify the ones that provide access to addon-<tenant><MP>.goskope.com. The first active proxy is used to contact Netskope Cloud services.
Traffic send to all proxies will be analyzed by the Client to determine if it should be intercepted and forwarded to Netskope Security Cloud.
Enable device classification and client-based end user notifications when the client is not tunneling traffic - This disables the Client when GRE, IPSec, Secure Forwarder and Data Plane On-Premises steering methods are detected.
Note
Even when the Client disables itself, the user justification rules will continue to be active.
Perform SNI (Server Name Indication) check - In scenarios where multiple domains use single IP address, it is recommended to use SNI in addition to DNS to make a steering decision.
The Netskope Client tunnels or bypasses the traffic whenever there is an overlap between the IP addresses of different domain names. Use the option Perform SNI check to get the domain name from SNI and for the Client to validate the traffic based on the SNI check. If this option is enabled, the domain name is obtained from SNI for lookup.
For example, YouTube, drive.google.com, and plus.google.com are resolved with the same IP address. In such scenarios, the unmanaged YouTube traffic is allowed to the Netskope proxy because the client steers the SaaS traffic based on the IP address. To eliminate the IP address overlapping, you can configure the Client to steer the SaaS traffic based on SNI instead of IP address. The SNI feature supports the following operating systems:
Windows 7 or higher.
macOS
Note
When SNI-based steering is enabled, the initial TCP three-way handshake is not steered inside the Netskope tunnel. The Client steers the traffic only after it retrieves SNI hostname from the SSL Client Hello packet. All applications with source IP restrictions fail as this happens outside the Netskope tunnel and is sourced from a non-Netskope IP.
Note
Contact your Sales Representative to enable this feature for your account.
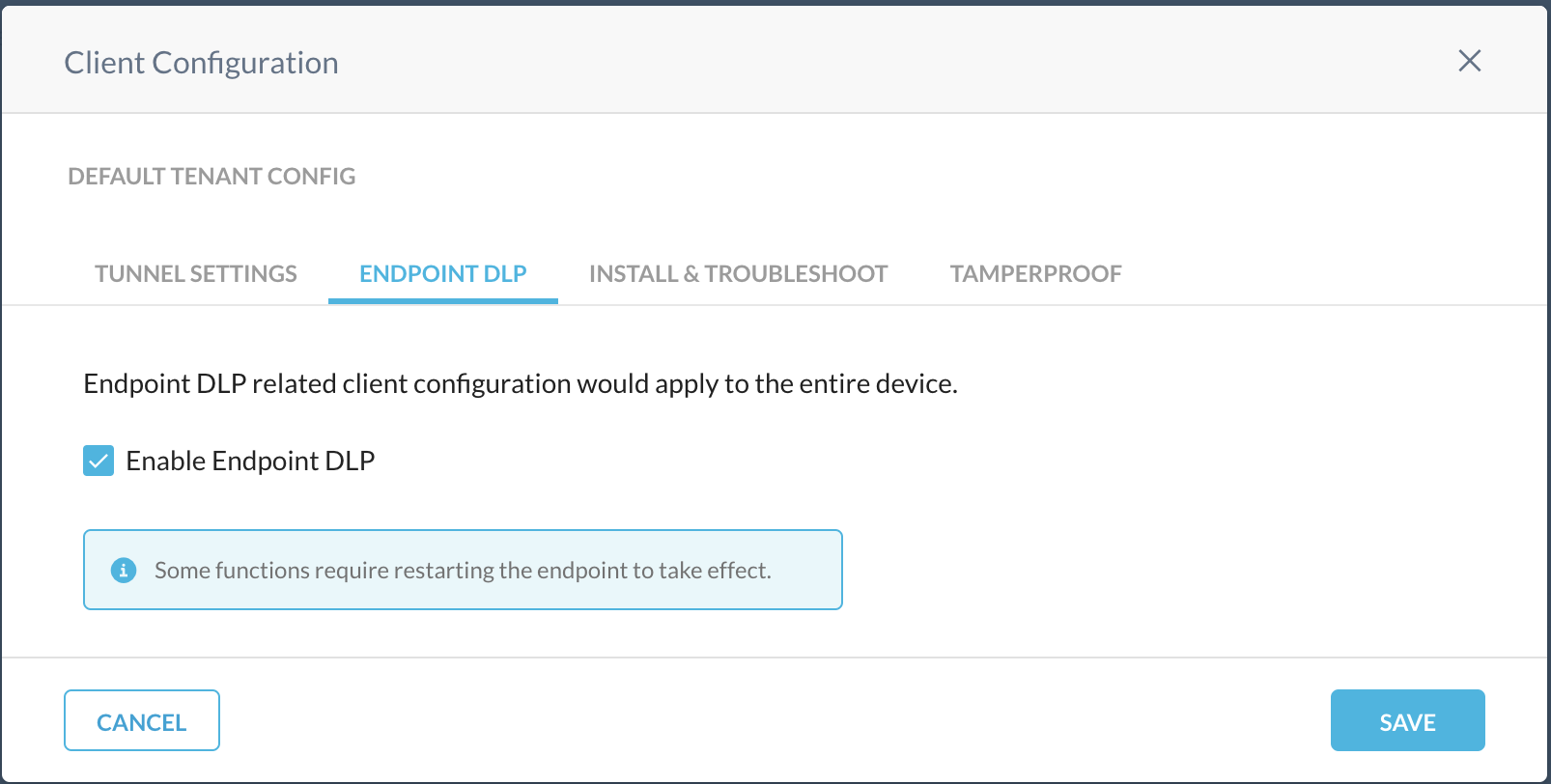
Select Enable Endpoint DLP to enable Endpoint Data Loss Prevention for the client configuration and apply Content and Device Control policies to the devices. You can enable Endpoint DLP for the Default Tenant Config to apply policies to all client users or for custom client configurations to apply policies to specific users.
 |
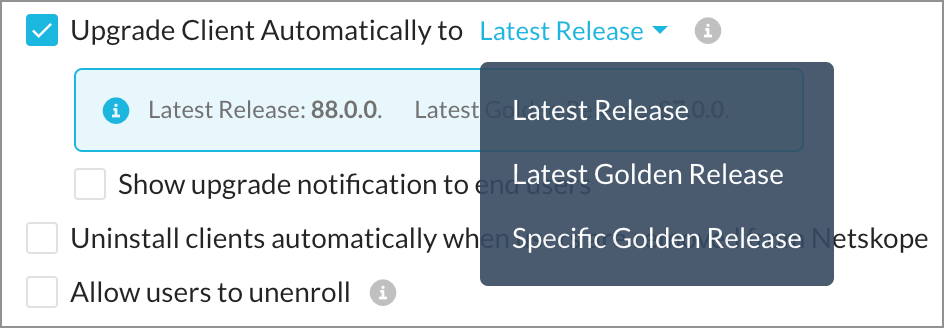
Upgrade Client automatically to a specific release version. You can choose from the following upgrade options:
Note
If a lower version is selected, then the endpoint with the higher version of Netskope Client will need manual uninstall and reinstall of the lower version of Netskope Client.
Netskope Client checks for newer versions every 4 hours and if a new version is available, the Client will silently auto-upgrade.
Latest Release - All clients will be upgraded the latest released version.
Latest Golden Release - All clients are upgraded to the latest golden release. The golden release version includes dot/hotfix release updates and automatically updates to the latest available. To know more about golden releases, view Client Downloads page.
Specific Golden Release - You can set all clients to be upgraded to a specific golden release. After selecting this option, you can select the golden release from the list of available versions. In addition, you can select Opt-in Upgrade to ensure the clients are upgraded to the latest minor or hot fix version of the selected golden release. To know more about golden releases, view Client Downloads page.
Show upgrade notification to end users. Select this option to send notification to end-users for an upcoming Client upgrade. This option is visible only if an upgrade option is selected
Uninstall clients automatically when users are removed from Netskope.
Allow users to unenroll. - If the Netskope client is provisioned via IdP, selecting this option allows users to unenroll from Netskope. When unenrolled the user is logged out from client and the Client is disabled, the user will be required to enter their IdP credentials to enroll again to enable client.
Advanced Options
Enable advanced debug option - Select this option to select the log level. Default is Info. The log levels in nsdebug.log are displayed as info, warning, error, and critical. The log files are stored by default in the following location:
Windows Devices: %PUBLIC%/Netskope/nsdebug.log
macOS Devices: /Library/Logs/Netskope/nsdebug.log
Warning
Setting log level to Debug may impact the performance due to high disk operations.
Allow disabling of Clients - Prevents end-users from disabling clients in the devices.
Allow disabling of Private Apps access - Allow users to disable the Client for Private Apps Access. After enabling this option, you can view Enable/Disable Private Apps Access in the Netskope Client system tray icon.
Hide Client Icon on System Tray - Hides the Client icon from end users devices system tray. This will also prevent Client notifications from being displayed to the user.
Password protection for client uninstallation - Enable this option to prevent unauthorized uninstallation of the Client from end user devices. The end users need to enter the admin password for uninstalling the Client. Password protected uninstallation is supported in both Windows, macOS, and Linux devices. Service stop option is available only to Windows devices.
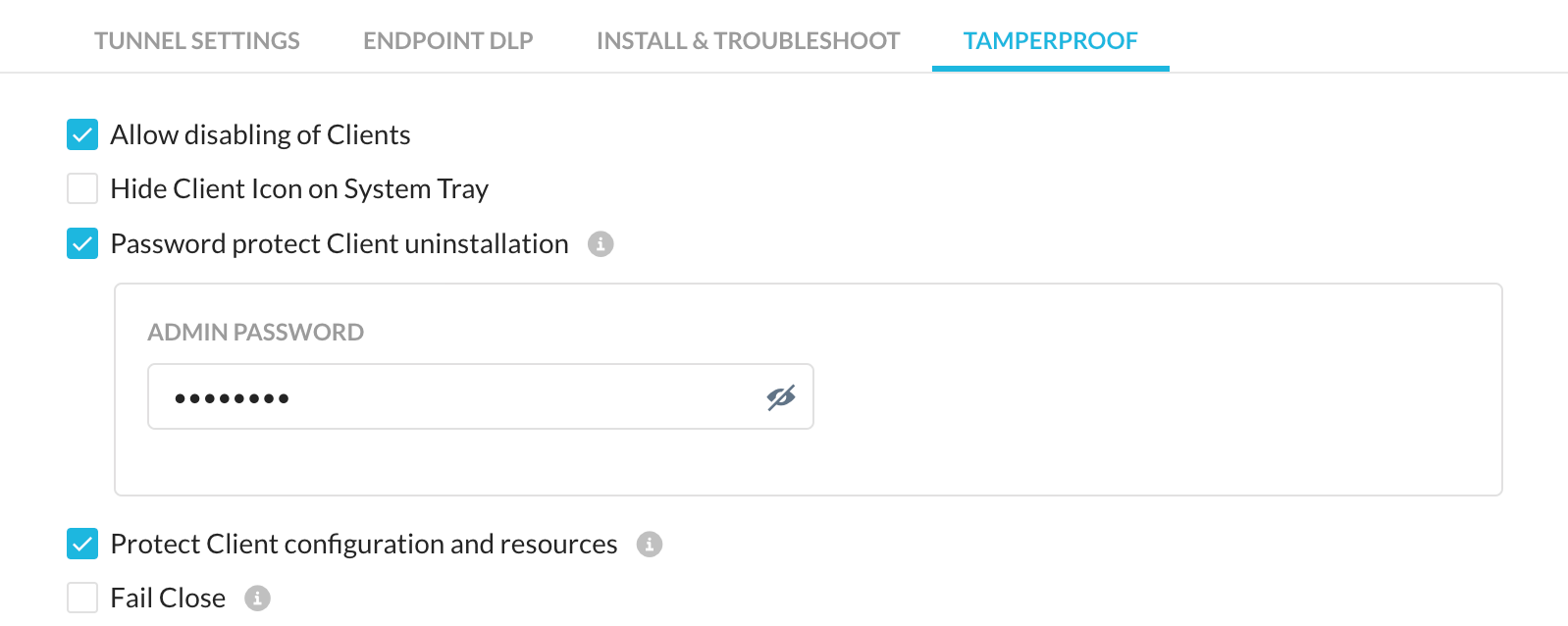
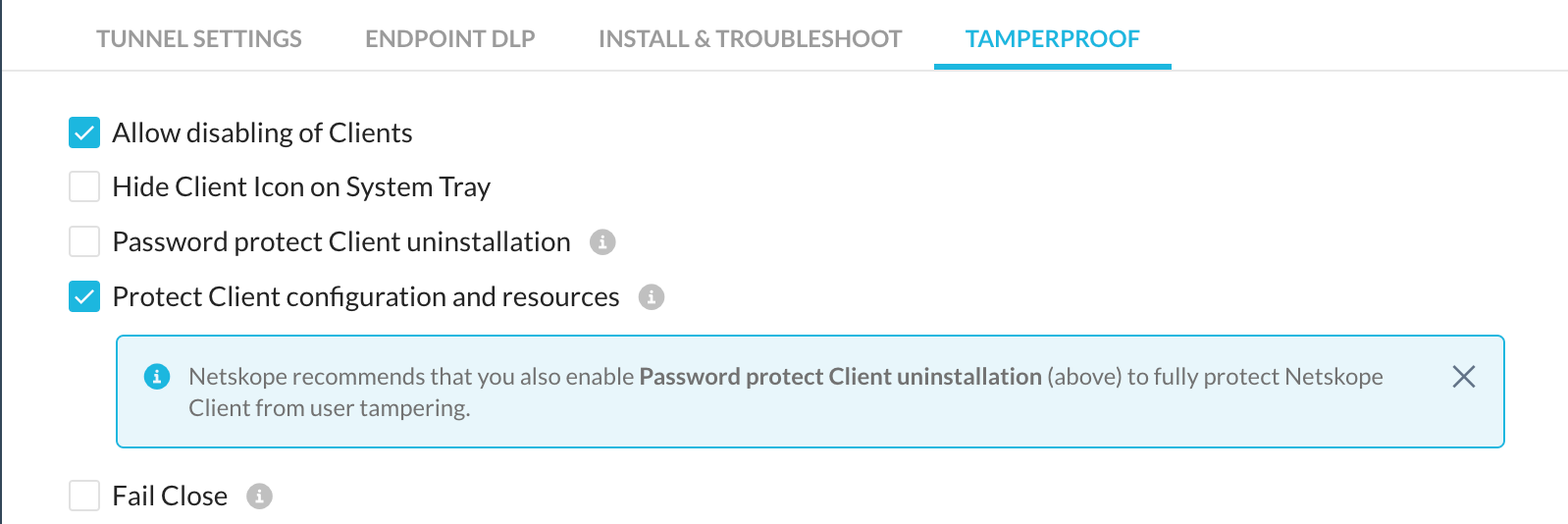
Protect Client configuration and resources - After you select this option, users with elevated permissions are prevented from altering any sub-part (files, folders, and process) of the Netskope Client installation. It prevents users from modifying, renaming, or deleting Netskope processes, folders, files, and registry keys.
Note
Supported Platforms: Windows 10 or higher versions.
Netskope recommends you to enable the Password protect Client uninstallation option for to restrict users from uninstalling or stopping the Netskope Client services.
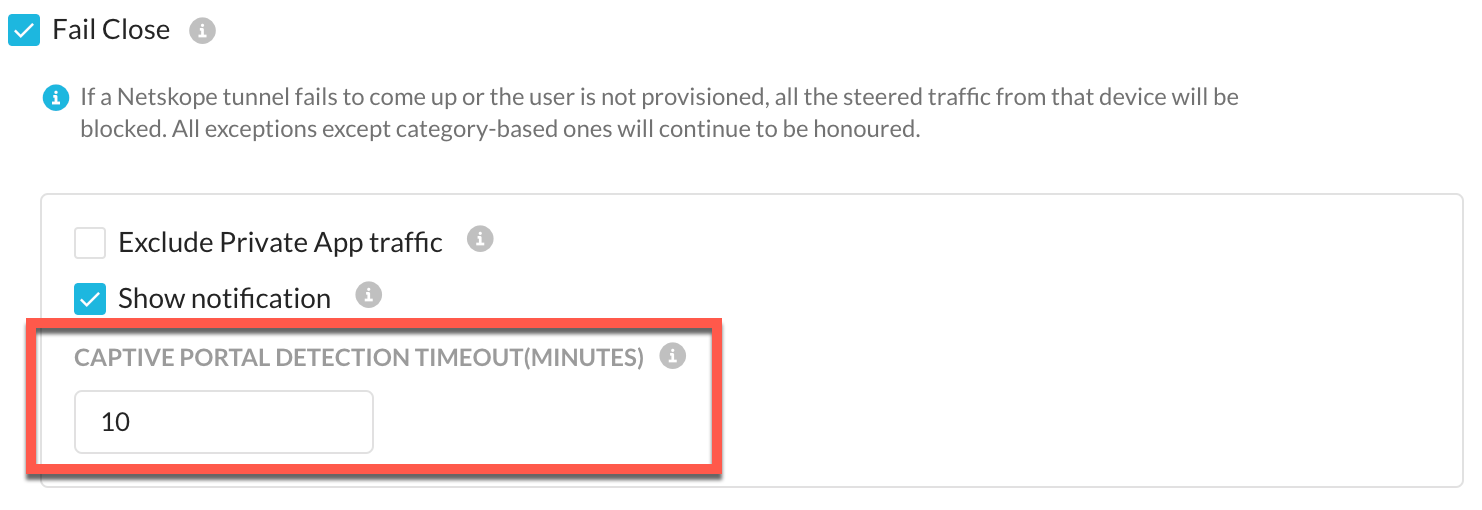
Fail Close - Blocks all traffic when a tunnel to Netskope is not established or a user device is not provisioned in the Netskope Cloud. Domain-based, IP-based, and cert-pinned exceptions will be applied, but category-based exceptions will be blocked. When a user is detected as on-premises, the exceptions will be blocked.
Note
If a Netskope tunnel fails to come up we recommend that you block the steered traffic from that device.
When Fail Close is enabled, the Password Protection for Client Uninstallation and Service Stop become enabled and Allow Disabling of Clients options becomes disabled. With Fail Close, you can Exclude Private Apps Traffic, so Private Access is not affected, and also Show Notifications.
To enable Fail Close:
Select the checkbox.
This prompts a warning pop-up Enabling "Fail Close" will also enable "Password protection for client uninstallation and service stop" and disable "Allow disabling of clients". Click Proceed.
Upon selecting Proceed, the following options are displayed:
Exclude Private App Traffic: Use this option to exempt private access traffic while fail close is enabled.
Show Notification: A fail-close pop-up is displayed whenever the tunneling to Netskope is blocked. You can select the checkbox for Show Notification to alert users why they are unable to access web applications.
Note
Netskope recommends to enable the Show Notification option to get notifications.
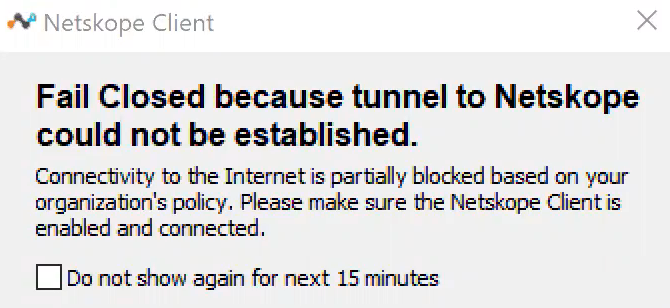
Captive Portal Detection Timeout (Minutes): A captive portal is a web page displayed, whenever a user tries to access the network where captive portal is enabled, to let the users authenticate prior to accessing the network. For example, if you are trying to connect to the free Wi-Fi or hotspot in an airport or restaurant where captive portals are enabled, you need to complete a set of actions to access the network.
This option enables administrator to define captive portal grace period. If Netskope Client detects a captive portal, it does not enforce fail close for the configured duration even if Netskope cannot establish a tunnel. This allows the user to perform captive portal authentication. Admin can enter a value between 5 -10 (minutes) in the Captive Portal Detection Timeout text box.
The Netskope Client tries to detect the captive portal on Windows and macOS respectively. The Netskope Client makes the request to the platform specific URL and if captive portal is in the network, it redirects to captive portal URL. Netskope client adds the redirected URL to exception configuration. Netskope Client blocks all traffic if user cannot connect to the network within the configured time.
Client Configuration Encryption
Client configuration files generated in the admin config and downloaded by the client can be encrypted via the encryptClientConfig feature flag. This flag is disabled by default. To enable encryption reach out to Netskope Support.
Note
The encryption is performed on all files except the nsbranding file. The nsbranding file is encrypted via the encryptbranding feature flag. This can be enabled via a support ticket. Also, files generated by the user device are not encrypted. This option is not available in the Netskope Tenant Admin console and can be enabled only via a support ticket.
Log files sent for debugging are decrypted before creating a zip bundle of all the log files.