Configure a Steering Profile
A Steering Profile tells the Netskope Client what traffic it needs to capture and send towards Netskope, and what traffic it needs to bypass and let through directly.
Steering Profiles can be global (applied for all users) or targeted to specific user groups. The latter can be useful for testing, or for use with specific groups of users that may require more granular configuration ( like developers).
Every Netskope tenant has a default steering configuration that is used as a fallback should no other Steering Profiles be present or matched on. You can simply continue to use the default steering profile if you wish (with a few small tweaks), or create your own from scratch.
To start, go to Settings > Security Cloud Platform > Steering Configuration
Note
On the Steering Configuration page, change the Bypassed Traffic setting to Log. This ensures that you retain visibility on traffic that is not sent to Netskope for inspection.
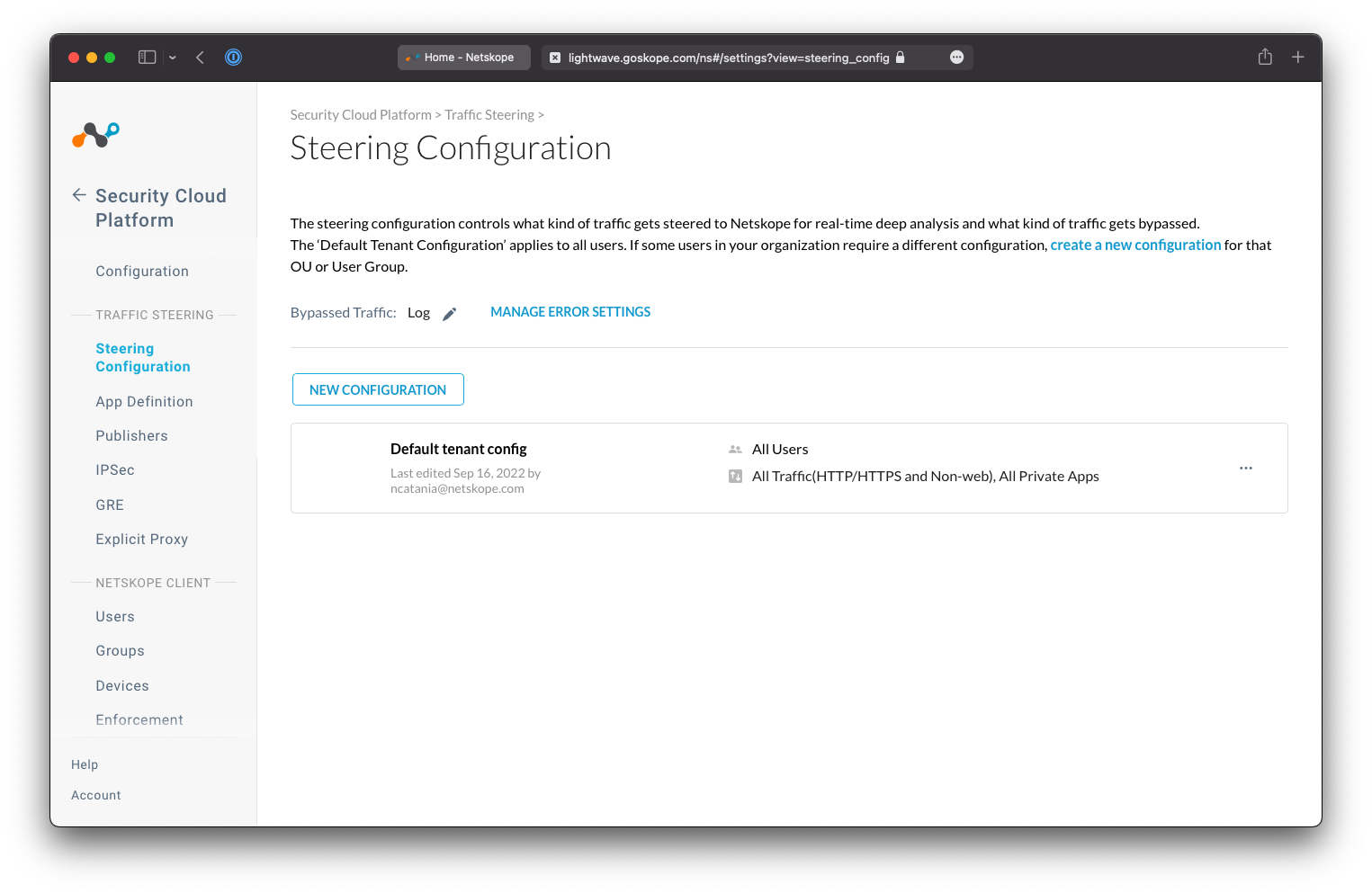 |
The Steering Configuration page is where you manage what traffic should be sent to Netskope for inspection.
Create or Edit a Steering Profile
Using the Existing Default Configuration
If you wish to leverage the existing default steering profile, click the Default tenant config profile to edit its configuration, and then click Edit.
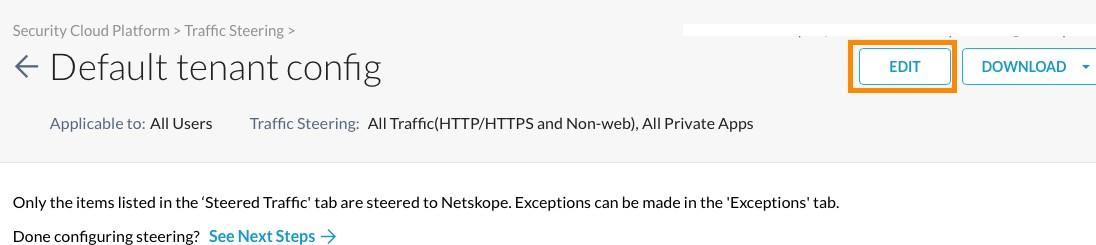 |
To edit the settings of the default steering configuration, select the profile and click Edit at the top-right.
Create a New Steering Configuration
You may want to create a separate profile and target your IT team (or the team will be managing the Netskope platform) as a way of testing traffic steering changes in isolation before pushing them to the rest of your organization.
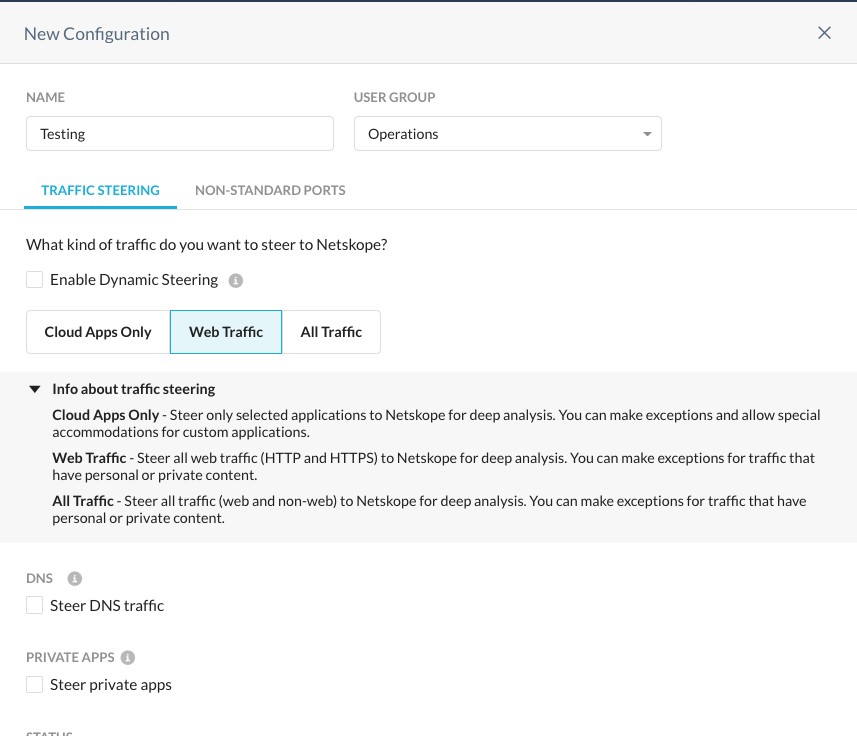
To create a new profile, click New Configuration, and if prompted, select User Group. Configure the new steering profile by giving it a name (like Testing), and assigning a user group.
The User Group field is a list of Active Directory/Security Groups that have been synchronized from the identity provider.
Configure the Steering Profile
Select the type of traffic that you would like the Netskope Client to capture and and send to the Netskope Cloud.
 |
Depending on your subscription, some options may not be visible to you:
Cloud Apps Only: Steer only selected applications to Netskope for deep analysis. You can make exceptions and allow special accommodations for custom applications. If you are a Cloud Inline or CASB-only customer, you should select this option.
Web Traffic: Steer all web traffic (HTTP and HTTPS) to Netskope for deep analysis. You can make exceptions for traffic that have personal or private content. Most organizations should select this option.
All Traffic: Steer all traffic (web and non-web) to Netskope for deep analysis. You can make exceptions for traffic that have personal or private content. If you are subscribed to Cloud Firewall, you should select this option.
If you subscribed to Netskope Private Access (NPA), then ensure that the Steer Private Apps checkbox is selected.
Click Save when you are done.
Note
You can click the Non-Standard Ports tab to specify ports other than 80 and 443 to be forwarded to the Netskope proxy.
The Dynamic Steering setting can be used to change the way traffic is forwarded by the Netskope Client based on whether the user is working from within the company network, or remotely.
If you selected the Cloud-Apps Only option above, then you now need to specify the cloud applications (like Dropbox, Teams, Sharepoint, etc) that the Netskope Client should intercept and send to Netskope.
Click Add Steered Item, and specify the applications required.
Bypassing Traffic
Traffic can also be explicitly bypassed from being sent to Netskope entirely under the Exceptions tab of the steering profile. RFC1918 traffic (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16) is always bypassed from Netskope by default, and Netskope also maintains a list of applications that usually need to be bypassed (typically due to certificate-pinning) like CrowdStrike.
Enable the Steering Profile
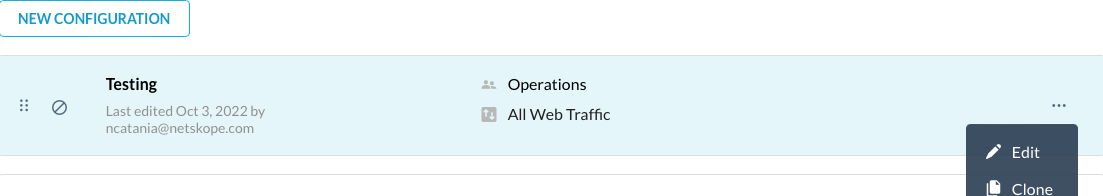
If you created a new steering profile, you will need to enable it before it can be used. On the Steering Configuration page (Settings > Security Cloud Platform > Steering Configuration), click the "..." menu next to the steering profile you wish to enable, and select Enable.
Note
The default steering configuration profile is always enabled.
 |
Important
You must enable a new steering profile for it to be actively used.
When a steering profile is enabled, it will be made available to all targeted users in production. You should always ensure that you have tested your steering profile with a smaller set of users before enabling it more broadly across the organization.