Architecture of Netskope IoT Security
An organization has a number of devices connected to the network in the environment. It is important to classify and protect these devices for security reasons. Netskope IoT Security discovers all the managed and un-managed devices in the network and the product gives a deep visibility of the connected devices. The solution uses traffic characteristics to derive metadata information and sends the metadata to the cloud for analysis and check for any potential threats using AI and machine learning. Netskope IoT Security dynamically applies policies to protect the devices by assigning the devices to VLANs, quarantining the devices, reporting to the administrators, etc.
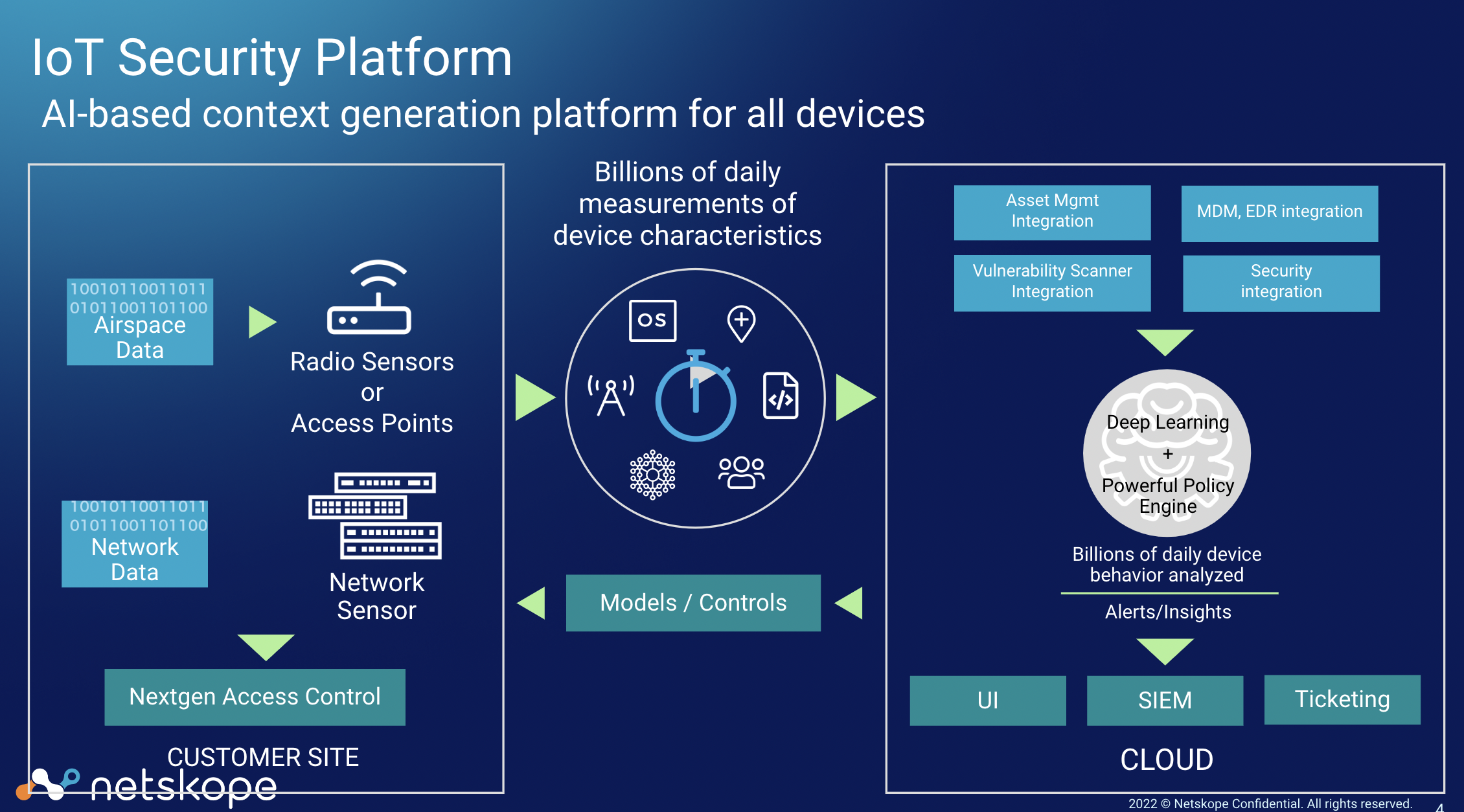 |
Following are the major components of Netskope IoT Security architecture:
Data Acquisition
Customer environments have network sensors installed as physical or virtual appliances.
These network sensors receive span traffic from core or distributed switches using Switched Port Analyzer port (SPAN), Test Access Point (TAP) or mirrored sensors and perform deep packet inspection on the traffic data.
If available, network sensors query Wireless LAN Controller (WLC) networks to get information of all connected devices supported by WLC.
If available, network sensors also query switching and routing networks in the environment to get information of all the connected wired devices.
In the case of third party cloud managed access points like MIST and Miraki, the product directly retrieves device information using cloud integrations through API.
Data Transfer
The network sensors do a deep inspection of the traffic, apply signatures and run algorithms to extract meta information.
Network sensors send this meta information via encrypted channel to the cloud to analyze the traffic metadata and events in the environment.
Data Analysis
On the cloud, various micro-services analyze the metadata.
The deep learning and powerful policy engine defines the device properties, risk and threat assessment, and determines access restrictions. Netskope IoT Security sends this information to the customer through Security Information and Event Management (SIEM), user interface, and ticketing tools.
Analytics and Protection
Netskope IoT Security sends the policy actions like blocking devices, assigning VLAN to devices, etc to the network sensors. Network sensors, in turn, use on-premise NACs and firewalls to enforce policies.
In the case of third party cloud based integrations like MIST and Miraki, the product uses the cloud access points to enforce the policies.
Customers can create the policies in the UI. Netskope IoT Security dynamically applies policies on the devices and the metadata. When the policy conditions are met, the configured policy actions are triggered.
Cloud Infrastructure
The cloud has multiple pods, and every pod has multiple tenants. Netskope IoT Security dedicates one tenant to one customer. This helps to keep the data safe and isolated from different customers.
Every tenant has a customer ID, and this ID is used to fetch and store the data. This architecture keeps your data separated and sorted from other customers.