Rule-Based Policies
To access the Rule-Based policy page, go to Policies > Behavior Analytics > Rule-Based tab.
Important
Basic UBA or UBA standard includes UEBA 9 predefined sequential rules. Advanced UBA includes UEBA ML models, UEBA user scoring with user confidence index (UCI), UCI based inline policies, and Custom UBA sequence rules.
Contact Support to enable this feature in your account, additional licensing is required.
There are nine default Rule-Based policies:
Bulk Delete: Detect suspicious/harmful user activity. Monitor potential risky users for any malicious activity that would cause data loss.
Bulk Download: Detect anomalous download activity from applications/instances where corporate data is stored. Identifies suspicious activity indicative of risky insider activity.
Bulk Failed Log ins: Identify attempts to breach corporate user accounts.
Bulk Upload: Detect suspicious data movement to authorized or unsanctioned applications/sites. Identifies potential exposure of corporate data.
Proximity: Proximity Detector will detect login activities that are geographically distant that should mark as anomalies.
Tip
Proximity only works with the Reverse Proxy method.
Rare Event: Detect user activity that is rarely observed e.g. user has never downloaded from a particular app in the past 90 days.
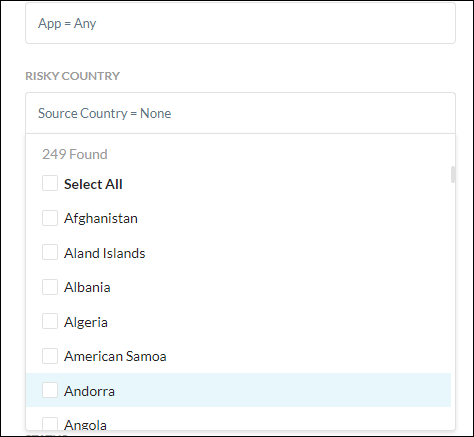
Risky Countries: Identify access/activity on applications/sites hosted in risky countries. Helps detect potential compromised or malware infected devices. Additional criteria includes specifying users, apps, and trusted IPs (like a VPN).
Shared Credentials: Detect unauthorized sharing of user credentials that may violate corporate security policies.
Note
The Shared Credentials severity is fixed at Medium.
Suspicious Data Movement: Detect accidental or intentional data exfiltration. Identifies movement of data from corporate sanctioned application instances to personal or non-corporate applications/sites.
FILTERING THE POLICY VIEW
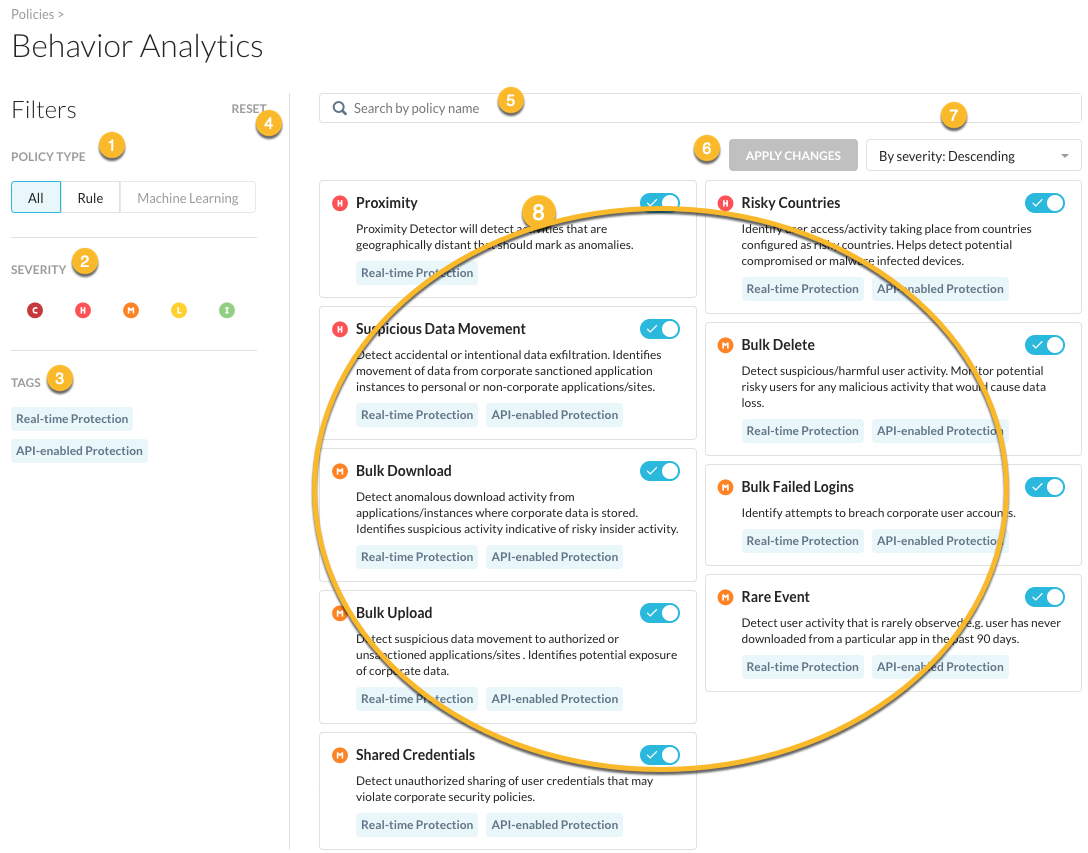
Use the left side panel to filter your policy view. The default view displays all policies and severity types.
Tip
All grayed out features or tabs means the feature is disabled by your admin or globally it's disabled because you need additional licensing.
Policy Type (image above #1) - select the All, Rule, or Machine tabs to view the particular policy type. For the Rule tab, you can further filter to view All rules, Predefined rules, or Custom rules.
Severity (image above #2) - select the severity type.
Critical
High
Medium
Low
Informational
Tags (image above #3) - select from the predefined data sources: Real-time Protection or API-enabled Protection. Each policy listed (image above #8) is tagged with a data source.
Reset (image above #4) - at any time you click reset to remove all filters and start with your default view. The default view displays all policies and severity types.
Search (image above #5) - type keywords to search for policy names.
Apply Changes (image above #6) - after you edit your policy, you must click Apply Changes to save your edits. Optionally, you can click to
 before applying changes. Anything that you changed, added, or deleted is described.
before applying changes. Anything that you changed, added, or deleted is described. 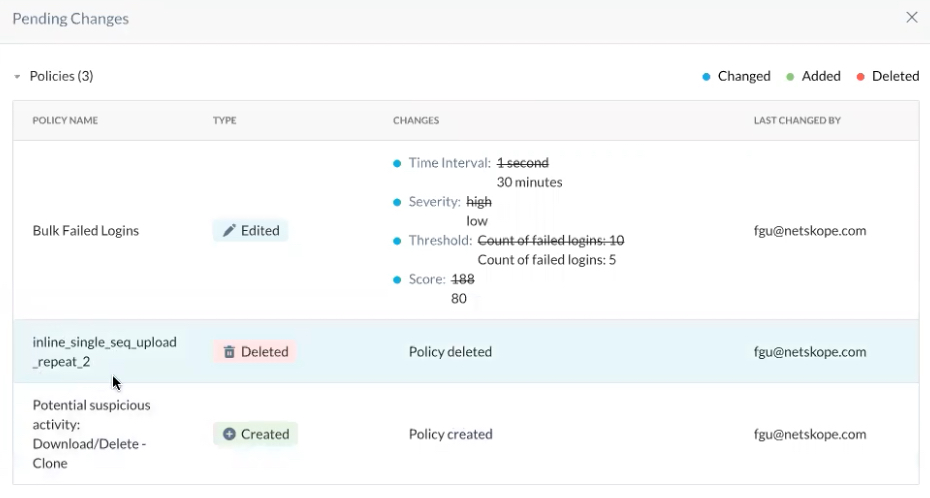
By severity (image above #7) - you can view the filtered policies by Ascending or Descending severity. The default view (Descending) displays the most critical policies first.
Policy list view (image above #8) - this section lists the policies that match the filters you apply.
EDITING A POLICY
To edit the policy, select the tile and click the pencil icon to open the Configure Policy window. Not all rules can be edited, deleted, or cloned.
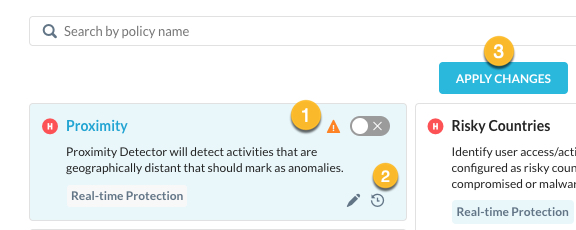
After you make your changes you will see an important icon (image above #1). This will remain visible until you apply your changes (image above #3).
Optionally, you can revert your changes (image above #2). You will see the following dialog box.
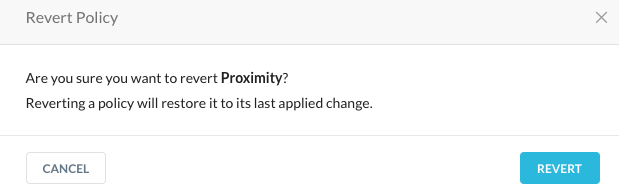
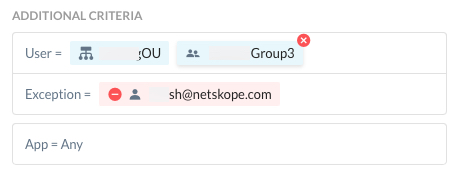
For the rule-based policies above, you can include or exclude certain users, user groups, or organizational units from the policy.
Click the pencil icon to edit the policy. The Configure Rule Policy panel displays.
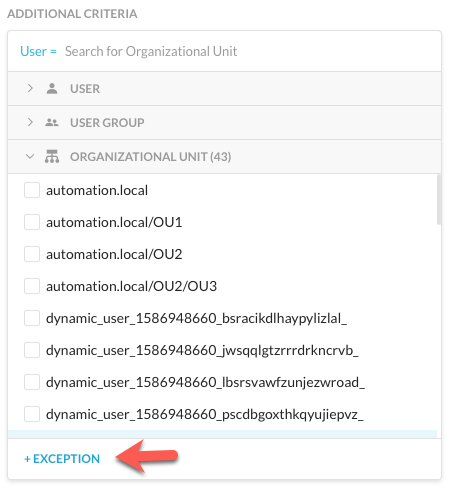
Click User, User Group, or Organizational Unit to display the dropdown. Note, only one dropdown will display at a time.
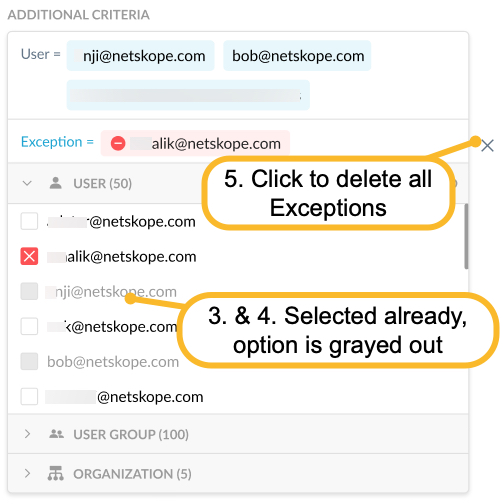
Click Exception to select the User, User Group, or Organizational Unit to exclude. Note, exclude options that were already selected are disabled in the UI and cannot be used again until you delete the selection.
Optionally, you can include any User, User Group, or Organizational Unit before saving. Note, options that were already selected are disabled in the UI and cannot be used again until you delete the selection.
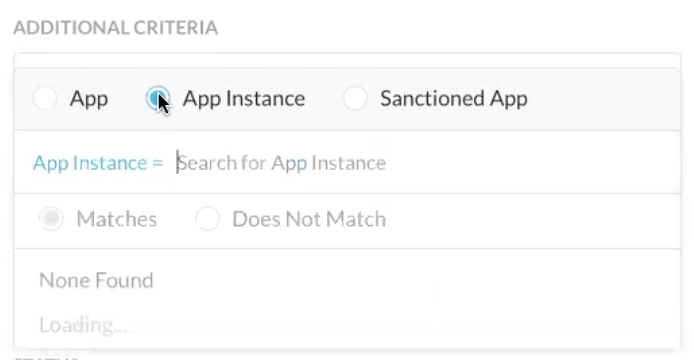
Also, you can add or exclude additional criteria such as sanctioned apps configured for your account, as well as applications and application instances. Note, custom apps and predefined apps also appear in the app list and can be used (included or excluded) for policies.
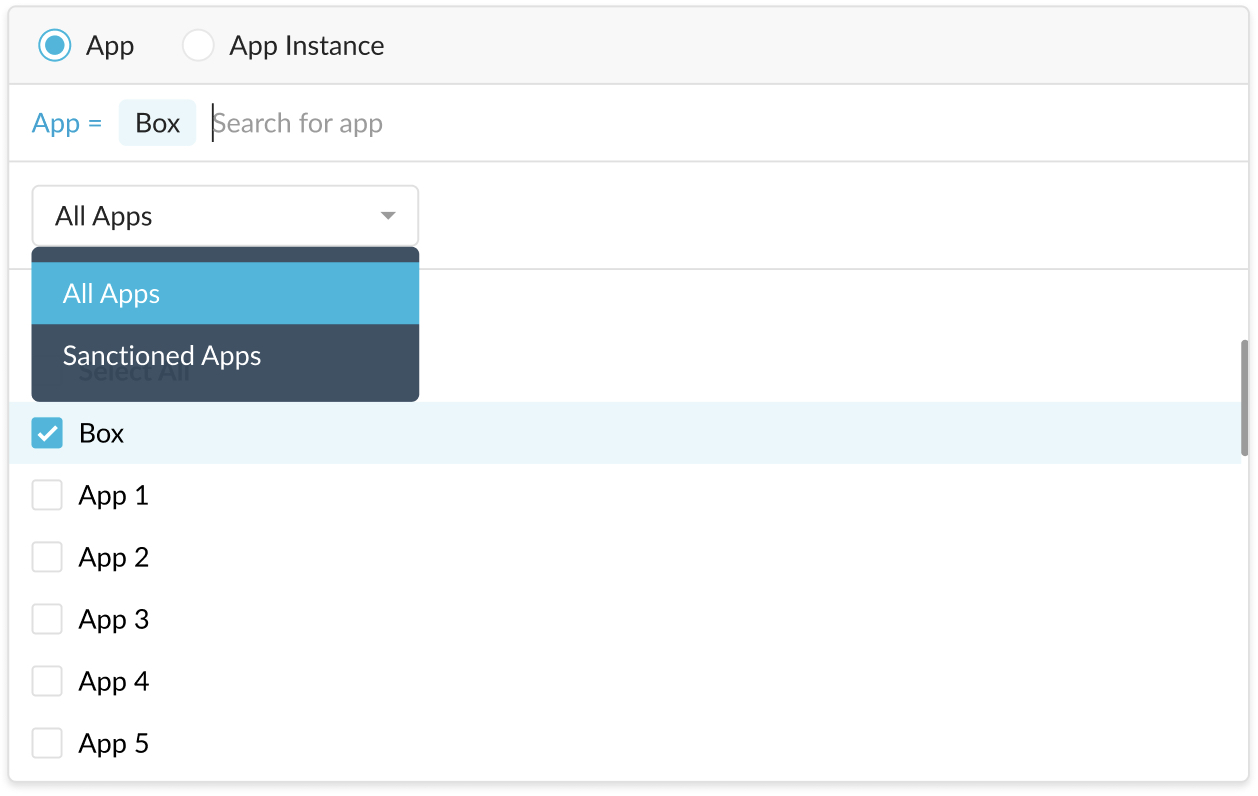
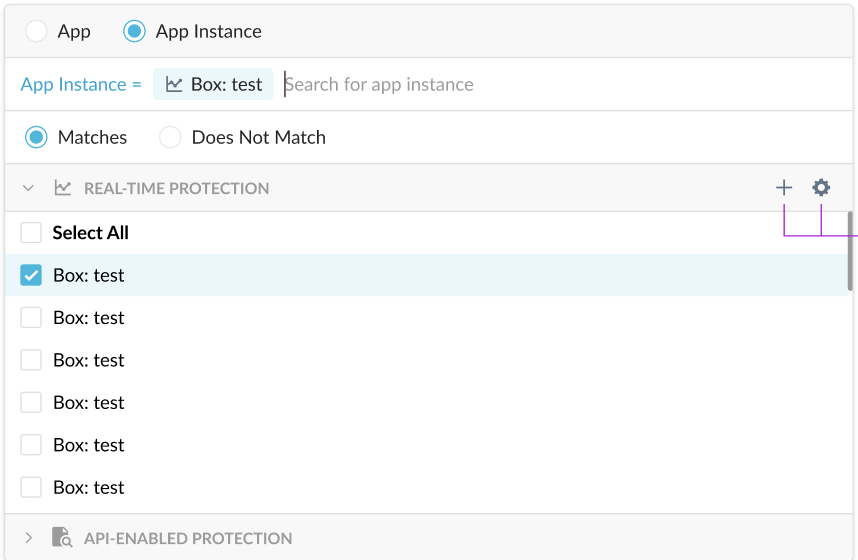
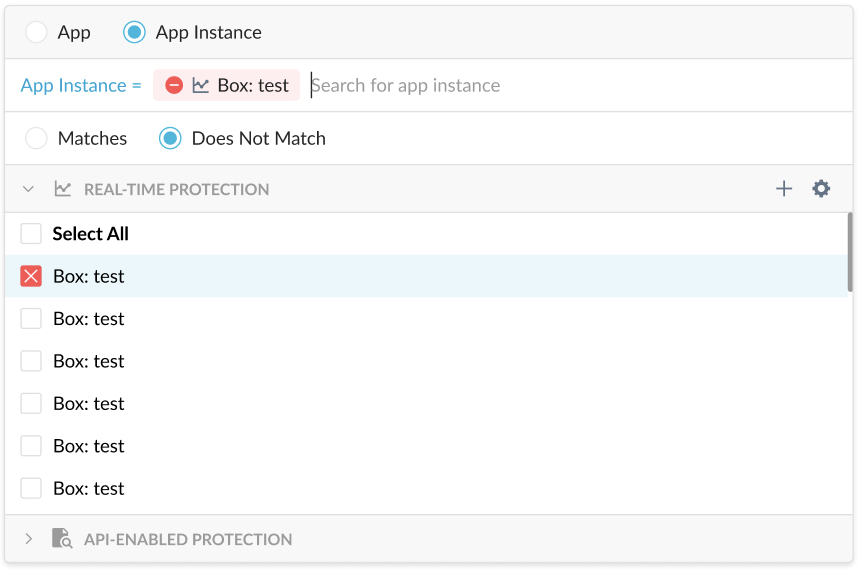
Tip
The following apps appear in the list but are not triggering alerts at this time.
Amazon Web Services
Google Cloud Dataflow
Google Cloud Platform
Google Cloud Big Data
Google Cloud Storage
Microsoft Azure
Amazon DynamoDB
Amazon Web Services
Amazon S3
Windows Azure
To undo the include or exclude action, hover over the selection and click the "X". If you are in a field and cannot see the Exception field, click out of the box to make it visible. You can also click the "X" beside the box to delete all the selections.
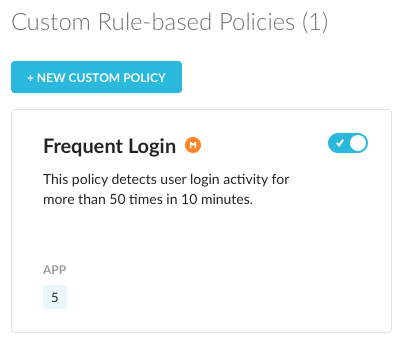
Custom Rule-Based Policies
Click the  dropdown to create a rule-based policy. You can create a new policy or create a policy from the template library.
dropdown to create a rule-based policy. You can create a new policy or create a policy from the template library.
New Policy From Template
The template library contains the following templates for the new Behavior Analytics custom rule-based policies for potential suspicious activity. You can change any option once you select a template. The right panel edit window opens to enable editing.
Download / Delete: Download and Delete, 20 repetitions in one hour on Box.
Share / Delete: Share and Delete, 10 repetitions in one hour on Dropbox.
Upload / Share: Upload and Share, 10 repetitions in one hour on Google Drive.
Policies are defined using a set of variables. These variables define the criteria for detecting policy violations. Specify the match criteria for the activity sequence that you want to be alerted on. Each sequence is defined based on a single user, group, organizational unit, and app. All match criteria are 'And'ed.
To create a new custom policy:
On the Rule-Based Policies page, select the
 > New. The New Custom Policy right panel window opens.
> New. The New Custom Policy right panel window opens.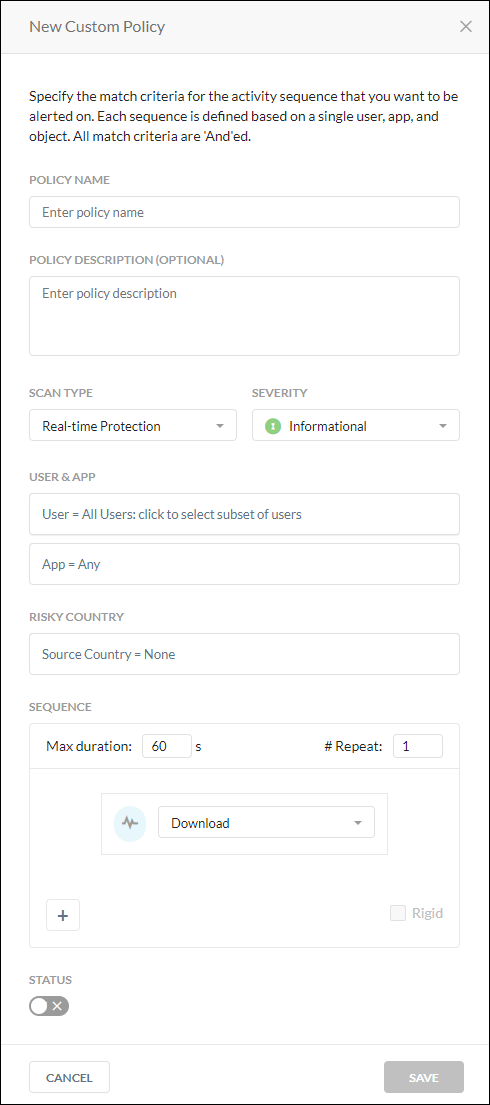
Type a name for the new policy.
Optionally, type a policy description.
Select a Scan Type, either Real-time Protection or API-enabled Protection. Real-time Protection will monitor all Inline activities including Client, Reverse Proxy, GRE, and Forward Proxy. API Protection monitors all Introspection traffic which is captured by the APIs.
Select a severity for this new policy.
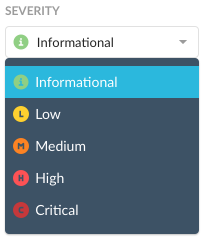
Note
The Shared Credentials severity is fixed at Medium.
Define the policy for apps, app instance, or sanctioned apps. Based on your Access Method selection, the list will dynamically generate the available choices for apps, app instance, and sanctioned apps.
Select any Risky Countries that you want to trigger a policy violation.
Select the Sequence of activities that will trigger the policy. You cannot have more than four activities listed in the sequence and actions cannot be the same.
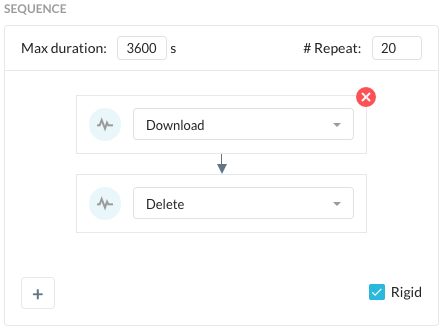
Max duration time cannot exceed 3600 seconds. This is the max duration of time for the sequence of activities that will trigger the policy.
Number of times the activity was repeated. The number must be greater than zero.
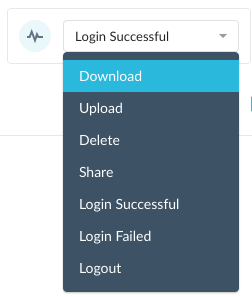
Add an activity. Your choices may include the following or a subset based on your Access Method selection:
Select the Rigid text box if you want to enforce the order of activities. Rigid means that the activities must occur inn the order specified to raise a detection. If not selected, the activities can occur in any order.
Enable Status to activate the policy.
Click Save to create the new policy. The policy name appears in the Rule-Based tab under the Custom Rule-Based Policies section.