OpenVPN Cloud
A managed cloud solution that provides a secure network connection between a private network and its remote user.
This document contains the best practices required in OpenVPN Cloud and Netskope Client to ensure smooth interoperability.
Environment
This document was created using the following components:
OpenVPN Client Version: 3.3.1.2222
Netskope Client version: 92.1.0.943
OS: Windows Server 2016 DataCenter
Specific configurations in OpenVPN Cloud and Netskope tenant web UI ensure processes or traffic from either of the applications are not blocked or directed to the Netskope Cloud.
Configurations In OpenVPN Cloud
With the split tunneling feature, you can control the VPN traffic and optimize its route to its destination. A tunnel is created when a VPN application connects to OpenVPN Access Server that redirects all traffic to its destination. Enable split tunneling to allow the Netskope Client to steer traffic smoothly to Netskope Cloud without getting blocked by OpenVPN.
To enable split tunneling when using OpenVPN Access Server from the Admin WebUI, go to Configuration > VPN Settings > Routing, toggle Should client Internet traffic be routed through the VPN? to:
No - All traffic from your private network will now route through a VPN.
Yes - To bypass VPN.sdiag.exe
Configurations In Netskope Client
When installing Netskope Client along with a VPN client, configure exceptions in steering configurations to bypass traffic from the VPN client. To learn more about adding exceptions for third-party VPN apps, view Exceptions.
To add OpenVPN as a Certificate Pinned Application on the Netskope UI:
Go to Settings > Security Cloud Platform > Steering Configuration and select a configuration.
On the configuration page, click EXCEPTIONS > NEW EXCEPTION > Certificate Pinned Applications.
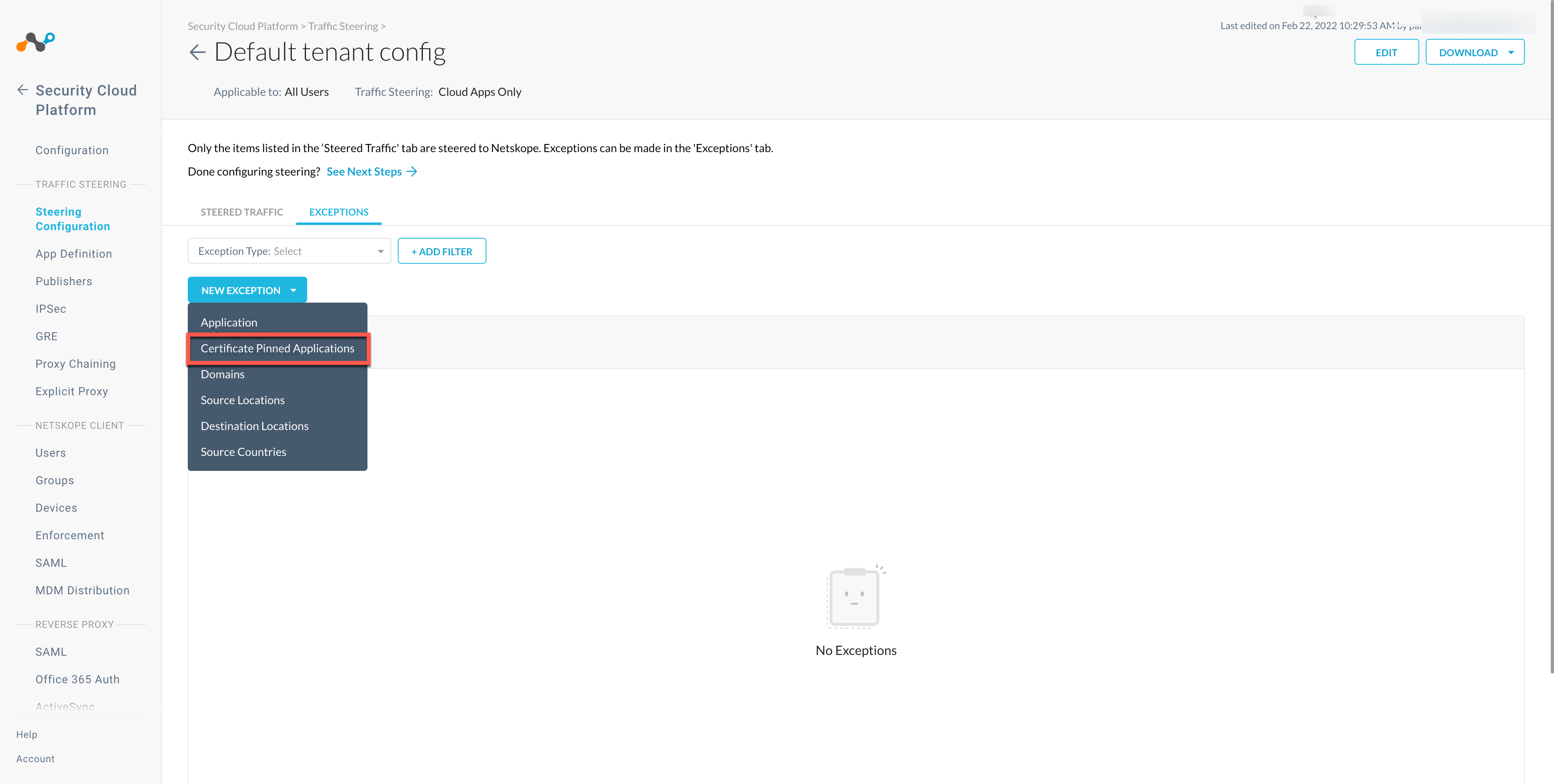
In the New Exception window, do the following:
From Certificate Pinned App, select the application. To add a new certificate pinned application in the New Certificate Pinned Application window, do the following:
Application Name: Enter the name of the application.
Platform: Select the operating system where the application is managed.
Definition: Provide the processes and .exe(s) list that you want to bypass.
From Custom App Domains, add the URLs that you want to exclude.
From Actions, select Bypass for all operating systems that you want to allow directly to the destination.
Click ADD.
Recommendation
Add server hostname as Domains exception.
To bypass the server IP, add Destination Locations as the exception type.
Best Practices
Netskope recommends that you configure the VPN to bypass Netskope Client tunnels established to Netskope NewEdge Security Cloud. With this configuration, the Netskope Client can establish a direct connection to the Netskope Security Cloud by pinning it to a VPN tunnel. In this way, Netskope can:
Provide optimal performance.
Reduce on-premises bandwidth and hardware resources utilization.
To bypass the Netskope Cloud traffic, view Allowed IP Ranges.
Netskope Client Functions
Refer to the list of validated use cases that you can use to verify Client operations.
OpenVPN Validation
Ensure that traffic is going through the VPN.