Threat Exchange Module
Threat Exchange is a rules-based engine for collecting and sharing indicators related to file hashes of malicious software (malware), file hashes of files used in Netskope DLP policy for absolute matching, or URLs used by plugged in systems for policy enforcement of restricted or allowed access.
Click play to learn how to set up Threat Exchange.
Threat Exchange Global Settings
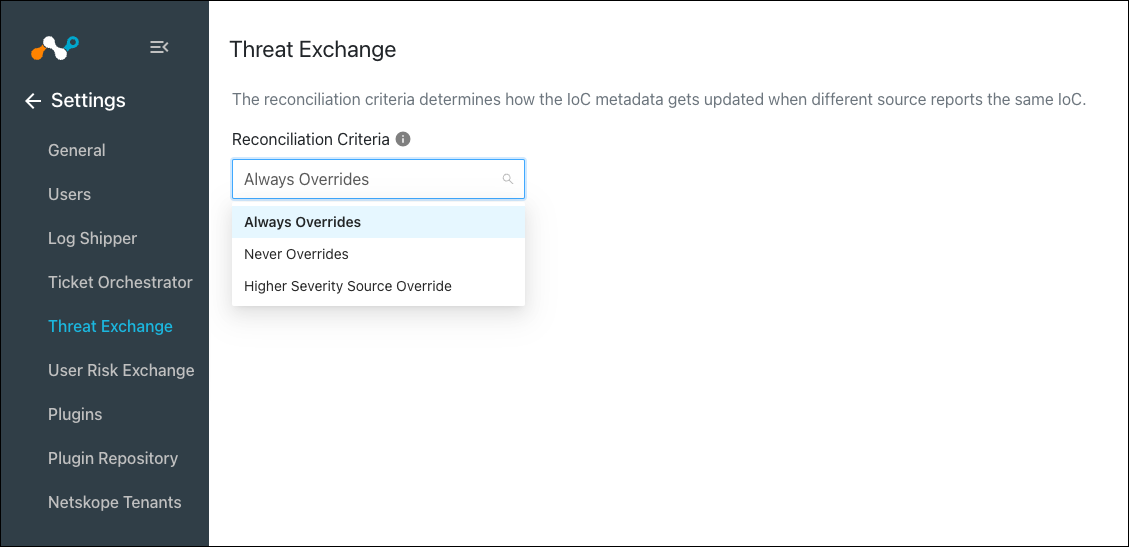
Only write-access users can change Threat Exchange Global Settings. Go to Settings > Threat Exchange. If the same IoC value is reported from different sources, then based on the reconciliation criteria, Threat Exchange will decide which IoC metadata should be kept and which will be ignored.
Possible Reconciliation Criterias include:
Always Overrides: If this criteria is selected, the latest IoC metadata will be kept in case of IoC Duplication.
Never Overrides: If this criteria is selected, the oldest IoC metadata will be kept in case of IoC Duplication.
Highest Severity Source Override: If this criteria is selected, the highest severity source’s IoC metadata will be kept in case of IoC Duplication.
 |
After selecting a criteria, click Save.