Netskope SSO with Okta
Netskope integrates with multiple third-party applications to provide a wide range of solutions. You can configure single sign-on (SSO) on the Netskope Admin Console to connect to these applications with or without authentication. Using the SSO Enabled feature in the Netskope Admin Console, you can set up forced authentication when connecting to third-party applications through Okta.
In these instructions, Netskope Admin Console refers to the app in the Okta Applications Dashboard. Netskope UI refers to the Netskope tenant.
Locate the SSO Settings in Netskope UI
To access SSO/SLO Settings in your tenant, go to Settings > Administration > SSO.
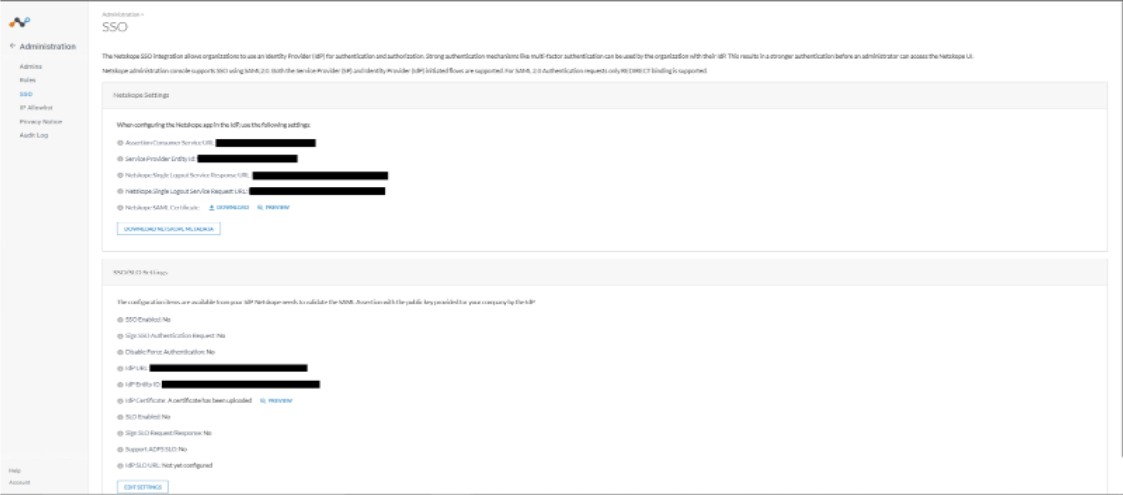
To view and edit IdP settings, click Edit Settings.
Here are the IdP URL, IdP Entity ID, IdP Certificate. Copy the IdP Entity ID to use when generating new IdP information in Okta.
Generate New IdP Information in Okta
In the Okta Dashboard, go to Applications > Browse App Catalog.
Search for Netskope and select Netskope Admin Console.
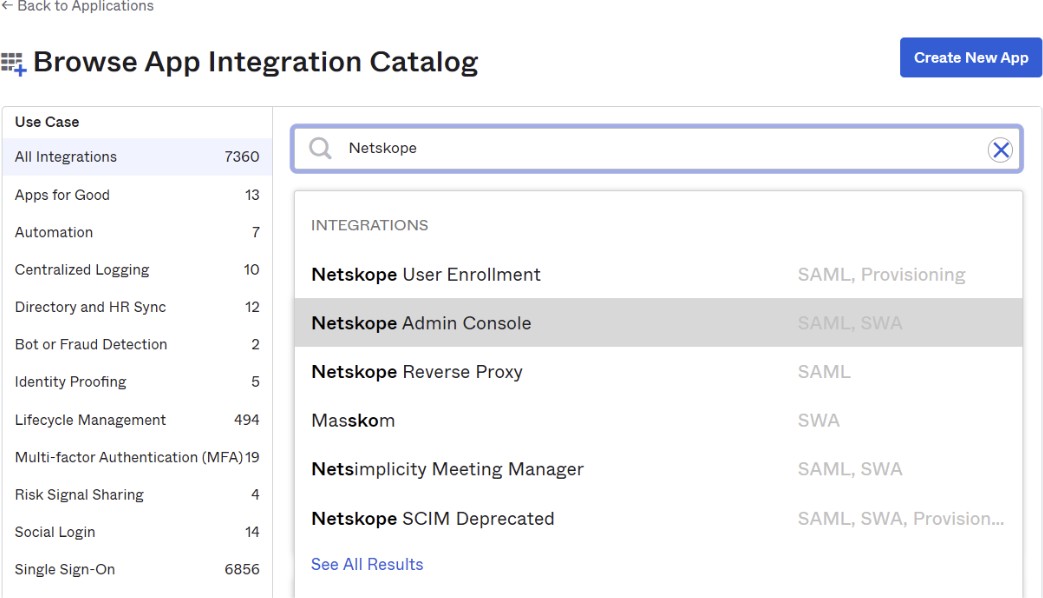
Click Add.
Enter your subdomain in the subdomain field and click Next.
Scroll down to the Service Provider Entity ID field and enter the Service Provider EntityID from the Netskope UI, and then click Done.
Go to the Sign On tab.
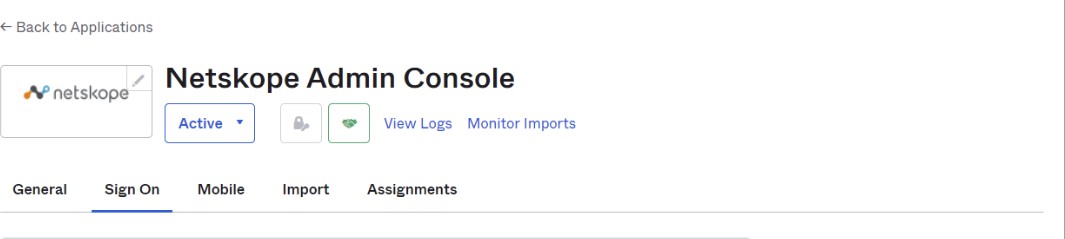
Scroll down to SAML Signing Certificates and click View SAML setup instructions.
Here are the IdP URL, IdP Entity ID, IdP Certificate to be copied into Netskope UI.
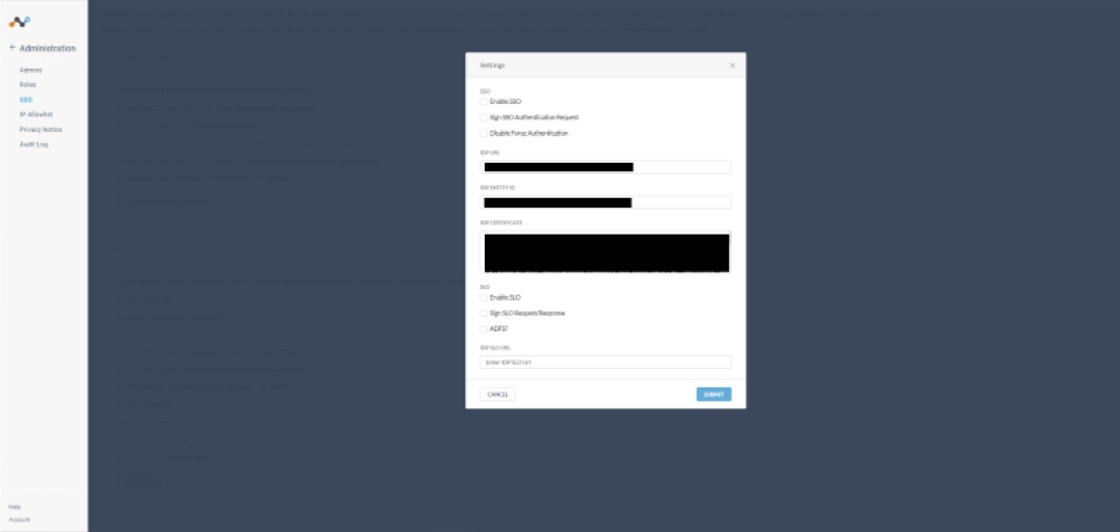
Copy the new IdP information from Okta and enter them into the Netskope IdP fields.

In the Netskope UI, go to Settings > Administration > SSO and under SSO/SLO click Edit Settings. Enter your Okta information and click Save.
Go to the Assignments tab and click Assign > Add People/Group, and then add users/groups who need access to the Netskope Admin Console.
Deactivate any old instances of Netskope Admin Console from Okta Applications Dashboard.
Provision Custom Roles with Okta using the Netskope Admin Console
Integrate Okta with Netskope so that Admins can access the Netskope Admin Console. The integration uses the Netskope Admin Console App (available in Okta), to provision users based on Custom Groups defined in Okta.
Provisioning Custom Admin Roles
This remaining sections explain how to assign custom roles to Netskope Admins that are provisioned via Okta. This does not work for local admin accounts. Using a predefined role like “Tenant Admin” will only allow you to provision admins with this role, so you need to have a more scalable way to assign different roles to admins that are provisioned through Okta.
Prerequisites
In order to complete this section, you must first:
Have existing Okta and Netskope Admin accounts
Enable SSO for your Netskope tenant
Deploy the Netskope Admin Console App in Okta
Create Custom Roles in Netskope
First confirm you have created your custom roles within Netskope. These roles need to have a similar naming convention as shown for this integration to work. Because you will use a contains statement within the Okta App, it’s important to prefix each custom role with an identical value. For example:
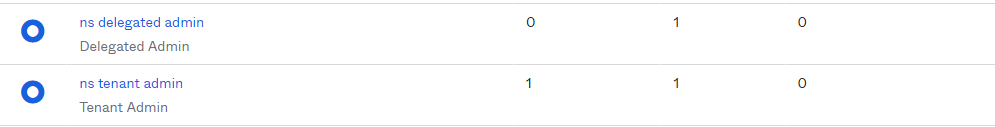
ns tenant admin
ns delegated admin
The prefix ns should be there for all custom roles. Assign whatever attributes you like for each custom role.
 |
Create Custom Groups within Okta
Now create the custom Groups inside Okta. These groups should match what you just created within Netskope.
Go to Directory > Groups > Add Group.
Check to ensure the prefix ns is there for all custom Groups that you will assign Admins to.

Assign admins to their respective group based on the roles you assigned for each group within Netskope.
Define the Admin Role Attribute in the Netskope Admin Console
Now set the admin-role attribute to ns in the Netskope Admin Console App withing Okta.
Open the Netskope Admin Console, go to the Sign On tab and click Edit.
Set the admin-role attribute under SAML 2.0 to:
Starts withandns,and then click Save.
The integration to assign custom roles for Netskope admins via Okta is complete.