Best Practices for Utility Policies
Netskope recommends creating two policies for coverage and placing them after your Threat Protection policies.
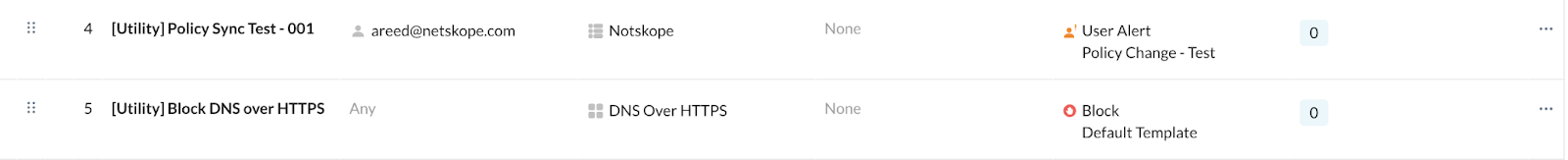
The first policy (i.e., [Utility] Policy Sync Test - 001) sends users an alert for non-critical, low-use websites with an option to proceed. These websites are entries in a custom category you can create to tailor to your organization's needs.
The second policy (i.e., [Utility] Block DNS over HTTPS) blocks DNS operating over port 443 (HTTPS) due to its incompatibility for steering. This policy will block silently. Netskope recommends placing this policy after your first one.
 |
Recommended Utility Policy #1
When a Netskope administrator applies a Real-time Protection policy change in the Netskope UI, those changes are replicated across the NewEdge data plane. Replication is generally complete within five minutes, but there are times where replication can take a prolonged period of time.
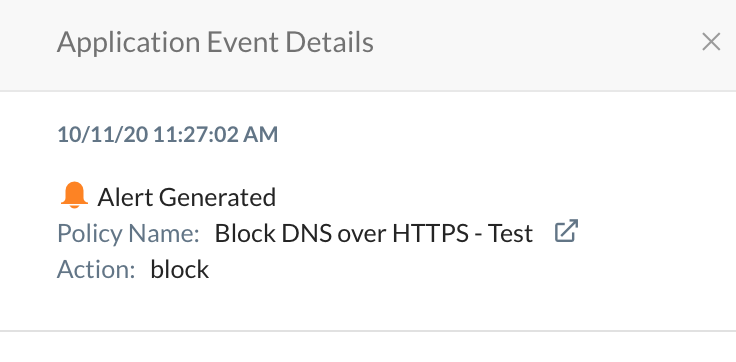
To confirm which policy is active, a user notification can be configured to inform the administrator which version of the policy is currently being applied through the POP within the NewEdge data plane being used. To learn more: How to Test a Real time Protection Policy Change Runbook.
Go to Policies > Real-time Protection.
Click New Policy and then Web Access.
On the Real-time Protection Policy page:
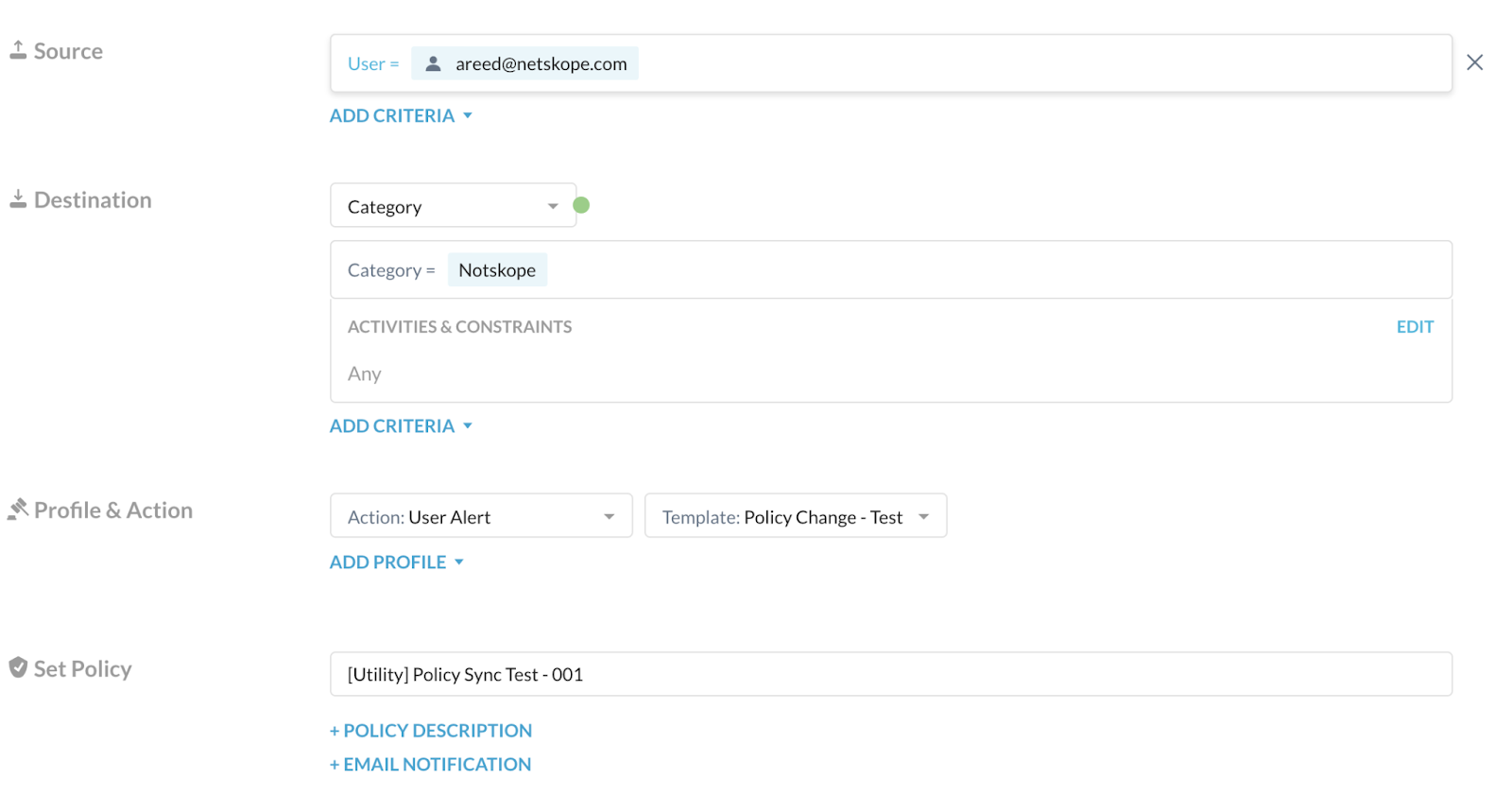
Source: Click X on the right to change scope to Any.
Destination: Choose Category, and select the custom category that contains the websites you want users to proceed with caution. Ensure the Activities & Constraints is Any.
Profile & Action: Choose the following.
Action: Choose User Alert.
Template: Choose a predefined or custom template that alerts the users but allows them to proceed.
Set Policy: Enter a name for the policy.
To learn more about any of these fields: Real-time Protection Policies.
Click Save and then Apply Changes.
Recommended Utility Policy #2
DNS over HTTPS is not a supported protocol for Netskope steering (CASB/NGSWG/NPA) and can be compromised by malicious actors. Therefore, Netskope recommends configuring a policy to steer and block this traffic.
Go to Policies > Real-time Protection.
Click New Policy and then Cloud App Access.
On the Real-time Protection Policy page:
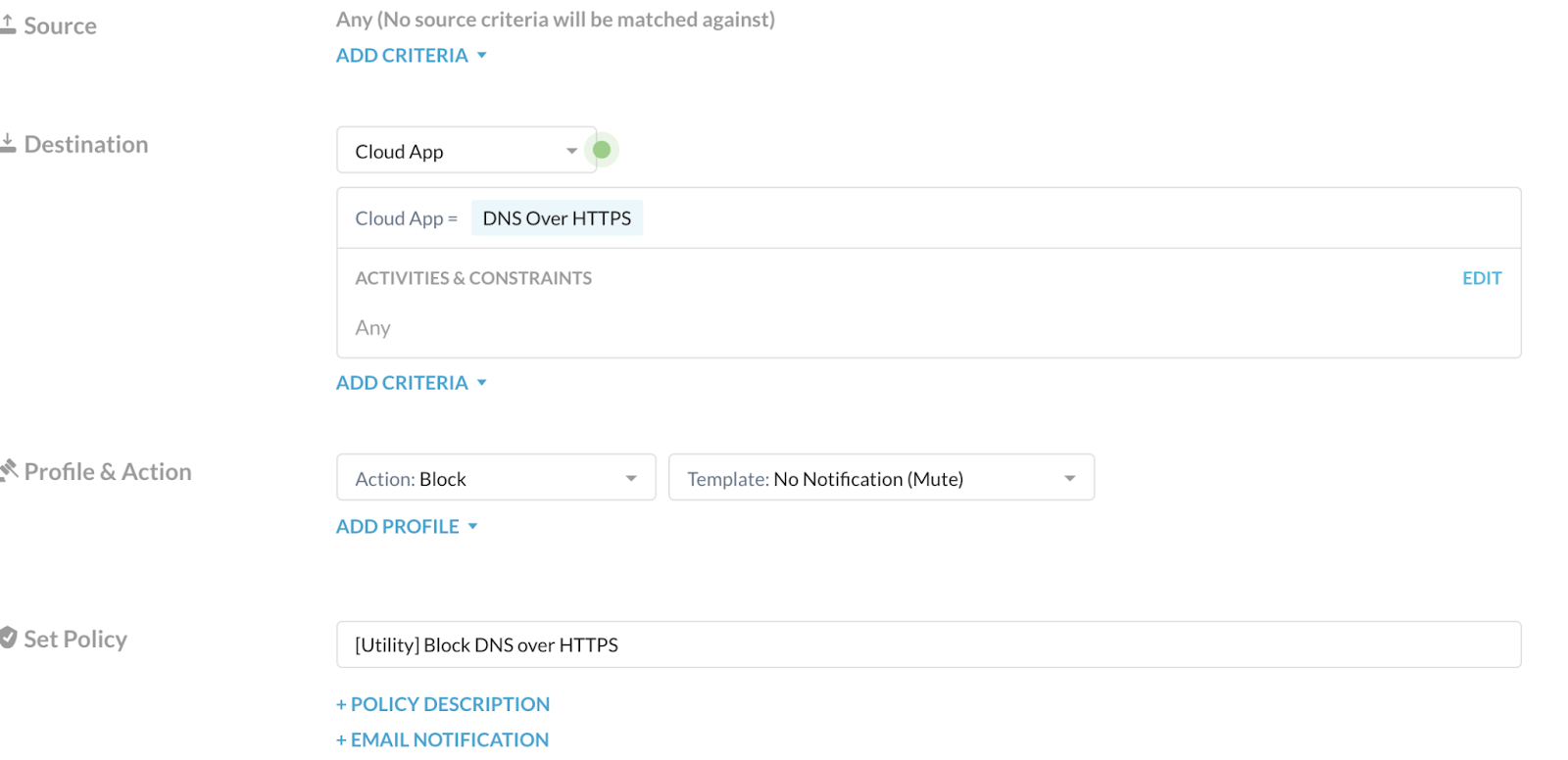
Source: Click X on the right to change scope to Any.
Destination: Ensure it's Cloud App, and select DNS over HTTPS. Ensure the Activities & Constraints is Any.
Profile & Action: Choose the following.
Action: Choose Block.
Template: Choose a custom template that doesn't send a notification and blocks silently.
Set Policy: Enter a name for the policy.
To learn more about any of these fields: Real-time Protection Policies.
Click Save and then Apply Changes.
 |