Netskope SMTP Proxy
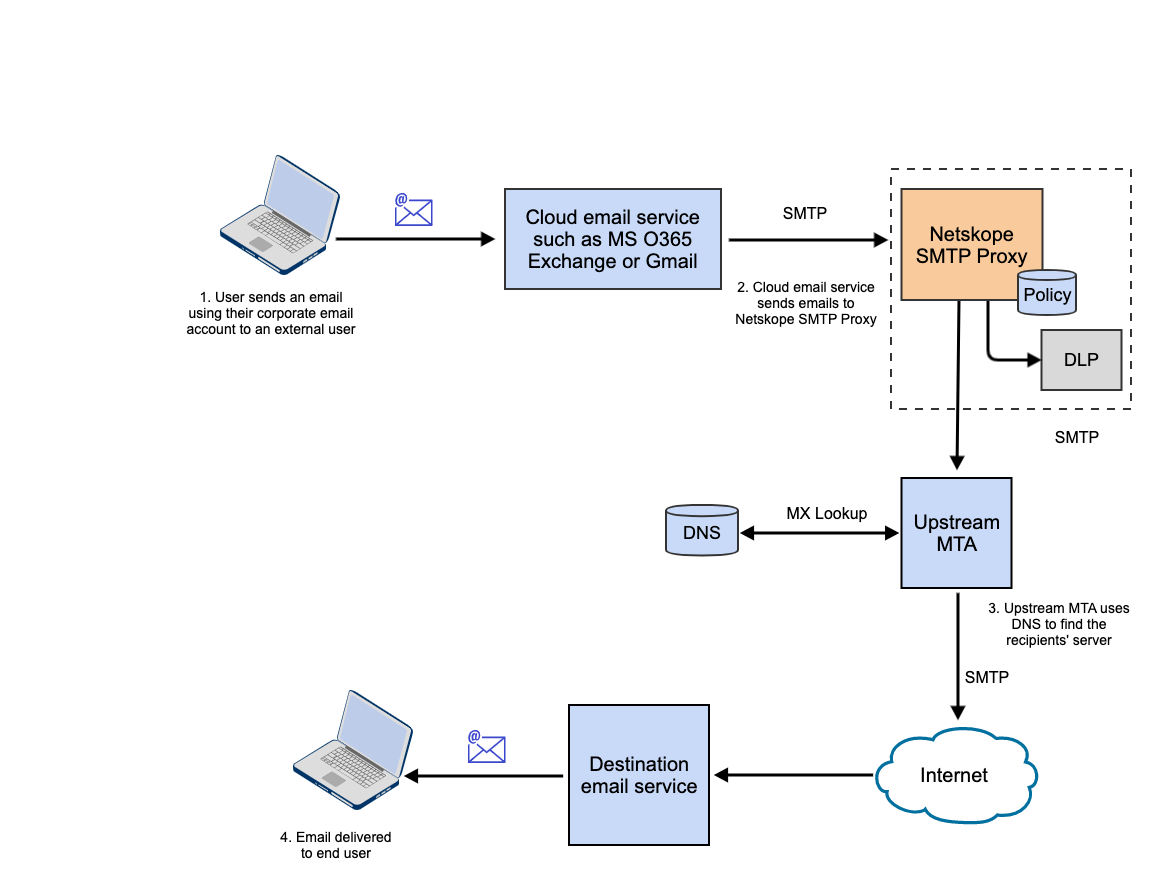
The Netskope SMTP Proxy can be used as a service to scan outgoing emails over SMTP for DLP violations. In this solution, an email initiated by the user is received by a cloud email service such as MS O365 Exchange or Gmail. The email is then passed through the Netskope SMTP Proxy integrated into your SMTP workflow. Netskope SMTP Proxy verifies the contents of the email against Real-time Protection policies and acts on DLP violations based on the policy configuration. The email is then passed on to an upstream MTA which looks up the DNS of the destination email service and sends the email to the recipient's server.
The following flow diagram provides an overview of the solution.
Prerequisites
Exchange must be working and connected to an upstream MTA like Mimecast or Proofpoint. If you are not using an upstream MTA in your environment, you can loopback traffic from Netskope to Exchange or Gmail. For more information see, Send traffic from Netskope back to Exchange or Send traffic from Netskope back to Gmail
Your SMTP setup must be using an upstream MTA that does not require authentication.
Limitations
Emails of any size can be forwarded to an MTA. Although, the DLP engine can only perform DLP checks on emails that are less than 32MB in size.
When creating a Netskope Real-time Protection policy, you can specify an SMTP header. Netskope SMTP Proxy adds this custom header to the email when the email content matches the policy definition.
If the custom header specified in the Netskope policy is the same as the standard header in the email, then Netskope SMTP Proxy replaces the value of the standard header with the value of the custom header.
For example, if the standard header in the email is
X-ns-Exchange-CrossTenant-Network-Message-Id : "1234ABC"and the custom header specified in your Netskope policy isX-NS-Exchange-CrossTenant-Network-Message-Id: "5678DEF"then, the value of the message ID in the standard header is replaced with the value of the message ID from the custom header. So, the final value of the header sent to the next hop MTA would be "5678DEF".Note
Netskope recommends that you use the naming convention
X-NETSKOPE-<custom-header-name>when specifying a custom header in the Netskope DLP policy.Netskope SMTP Proxy adds the header,
x-netskope-inspected: trueto every email. This header should also not be provided as a custom header in a policy action.Headers are case insensitive,
x-netskope-inspectedis the same asX-NETSKOPE-Inspected.
If a policy contains multiple DLP profiles, each with a custom SMTP header and more than one profile matches, then only the action from the first profile will apply. The result will be that only one custom header will be added.
In the Netskope UI under Settings > Security Cloud Platform > Configuration, none of the options on this page apply to the SMTP Proxy, including the Dynamic Trust Store.