Manage a Publisher
After deploying your publisher, use the following sections to make modifications to your Publishers.
Publisher Auto-updates provide a scalable means to update both the underlying operating system and the Publisher software. In high-availability Publisher deployments where two or more Publishers are assigned to an application, Netskope’s auto-update has implicit logic to stagger updates even if all Publishers are assigned to the same upgrade profile. This ensures that applications remain available during the upgrade.
You can get Publisher updates automatically, and also specify the version to be upgraded or downgraded for the Publishers. Options include the very latest Publisher, one of the two previous versions of the Publisher, or a Beta version.
For example, if the latest Publisher version is 101.0.0.1, Netskope will support Auto-Updates to version 101.0.0.1, 100.0.0.1, 99.0.0.1, or a Beta version. Updates for software defects and security vulnerabilities will only be introduced in the latest software version. So you should consider updating your Publishers to the latest version to take advantage of enhancements and security updates.
Important
This feature only supports Ubuntu-based Publishers and works with r97 or later Publishers.
The Publisher checks for a minimum disk space of 300 MB for System and Publisher upgrades. If the disk space verification fails, the Admin is notified through a message in the Admin UI and through email alerts, if notifications have been set up.
Auto-update use case factors include:
When Auto-Update is enabled for your tenant, all Publishers are included in a Default profile. The Default profile is disabled by default. When a default profile is enabled, all Publishers associated with this profile are enabled with the Auto-Update capability. Moving forward, all Publishers will be required to create or select an Update Profile upon creation.
You can perform a manual upgrade even if an Auto-Update profile is disabled.
Scheduled auto-updates will not occur when an Auto-Update profile is disabled.
An initiated upgrade process will continue if you disable the Auto-Update profile while the upgrade is in progress.
Before upgrading all Publishers, upgrade a test Publisher first, and then proceed to the other Publishers.
In enterprise environments, Netskope recommends the following:
Schedule Publisher updates during maintenance windows or non-peak hours for their location. You can have multiple Publisher Auto-Update profiles scoped to Publishers in different regions.
Enable Auto-update alerts for successful and failed Publisher Auto-Updates including the following:
Version update succeeded
Version update failed
Version update started but reconnection failed.
You can optionally also enable alerts for upgrades that start, and a 24-hour alert about when Auto-Updates will start.
Ensure that all Publishers check for N-2 releases at least monthly to ensure you stay within the Publisher Support Policy.
Ensure that at least one Publisher is available during the upgrade of other Publishers to provide administrative access should an upgrade fail. You can consider deploying dedicated Publishers for administrative functions to provide SSH access or via your virtualization solution’s interface.
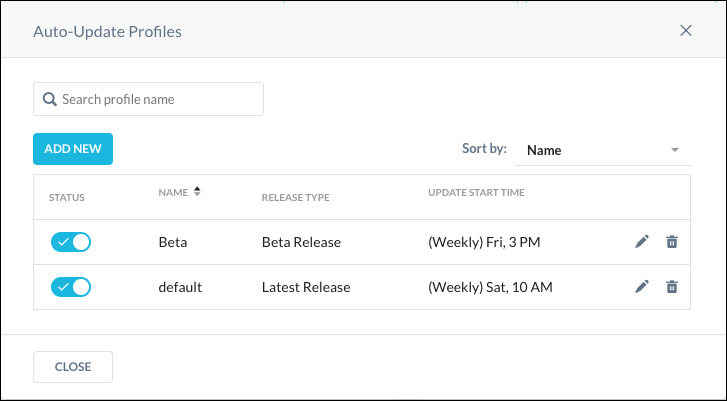
You can create, edit, or delete Auto-Update profiles, including the Default profile.
Go to Settings > Security Cloud Platform > Publishers and click Configure Auto-Update on the right side of the page.
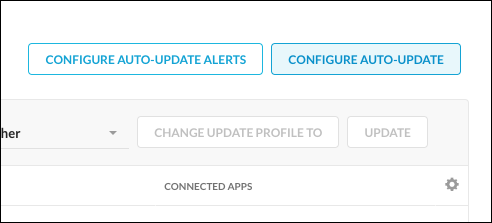
You can search for and sort existing profiles in the Auto-Updates Profiles dialog box, plus edit and delete profiles using the pencil and trash can icons. To create a new Auto-Update profile, click Add New.
Enter a profile name.
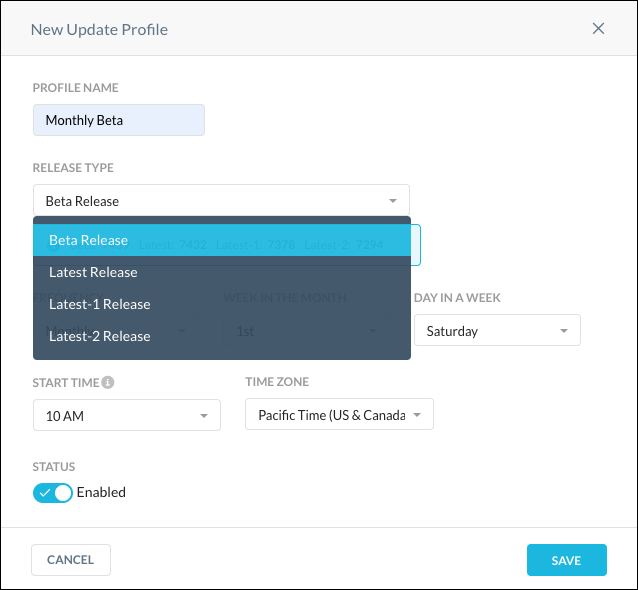
From the dropdown list, select Beta Release, Latest Release, or one of the previous versions of the latest release.
Tip
If you want to downgrade to a previous version, select the Latest-1 or Latest-2 version.
Specify a release frequency. For a Weekly update, specify the day of the week. For a Monthly update, specify the week and the day.
Select a time and a time zone to start the update. Publisher updates take around two hours to complete from the start time specified in the Update Profile.
When finished, click Save.
After Auto-Update profiles have been created, you can search for a profile, and also sort the profiles in the table in the Auto-Update Profile dialog box.
Auto-Update profiles can be applied to a single Publisher or multiple Publishers.
There are a couple of methods to modify an existing Auto-Update Profile, depending on whether you're modifying single Publishers or multiple Publishers.
For a single Publisher, select Edit from the Publisher side menu
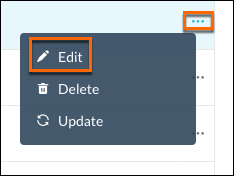 |
In the Edit Publisher dialog box, you can change the Update Profile for a Publisher by searching for and selecting a profile from the dropdown list.
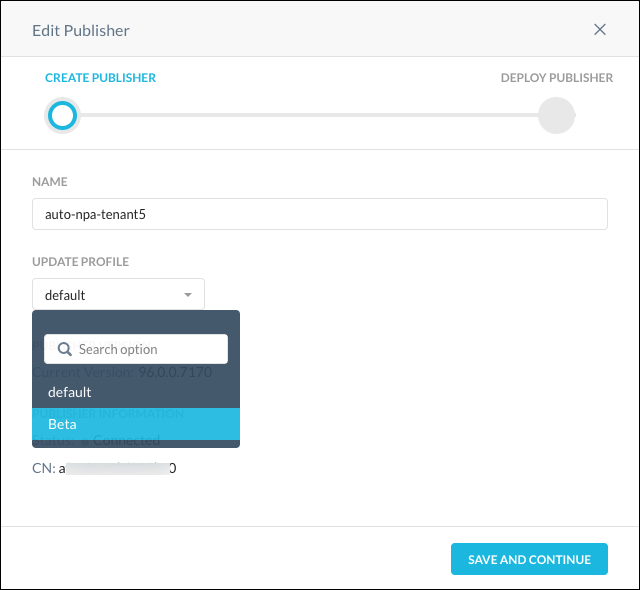 |
You can also delete and update a Publisher using the options on Publisher dropdown list. Click Update to immediately upgrade the Publisher to the Publisher version specified in the Update Profile.
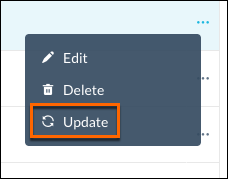 |
Click Configure Auto-Update to open the Auto-Updates Profile dialog box, which allows you to edit and delete a profile using the pencil and trash can icons.
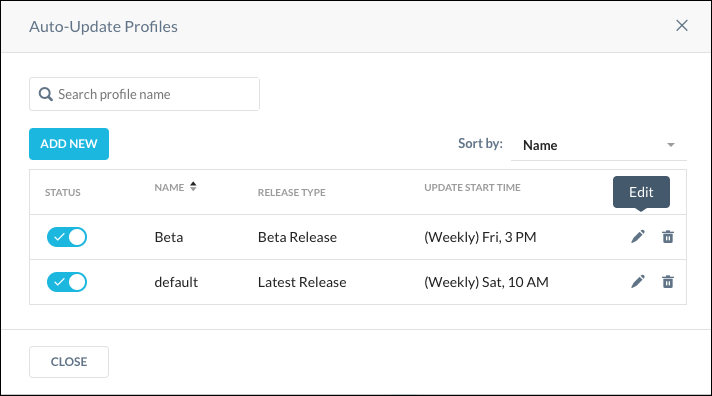 |
For multiple Publishers, select the Publishers (in the left column), and then click Update to immediately upgrade all the Publishers to the Publisher version specified in the Update Profile.
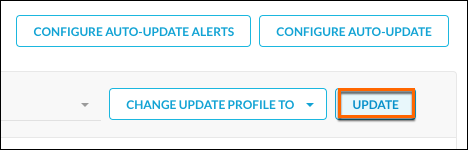 |
To change Auto-Update Profiles for multiple Publishers, click Change Update Profile To and select an Update profile from the dropdown list. Click Save and Continue and then Save.
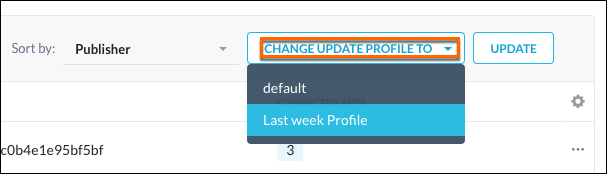 |
To receive notifications of when updates occur, for specific users, and the type of event that occurs, you can configure Auto-Update Alerts.
Click Configure Auto-update Alerts on the right side of the page.
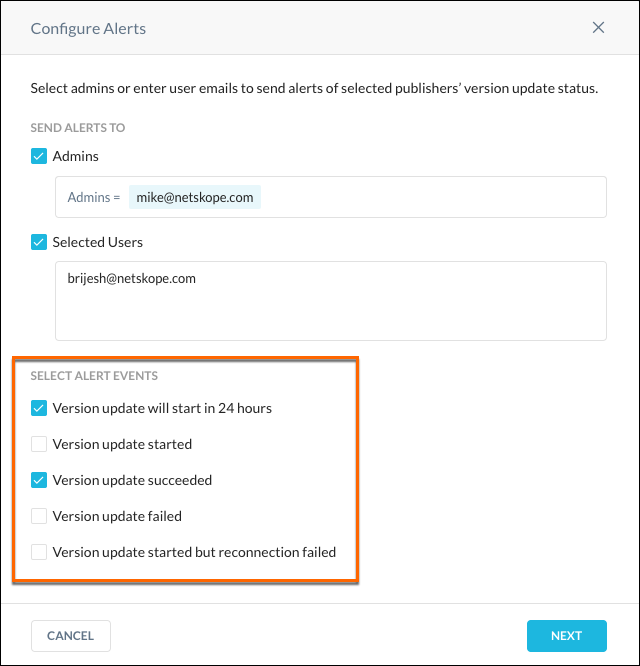
Specify who you want to receive notifications, and then the events that you want to know about.
Select the admins in the dropdown list; only users with Admin privileges for your tenant are shown in this list. To add Users, enter the user's email address, separated by commas if there is more than one.
Select the Alert types you want Admins and Users to receive via email:
Version updates will start in 24 hours: Profile-based. Publishers associated with a Profile are batched.
Version update started: Stitcher-based. Publishers associated with a stitcher are batched.
Version update succeeded: Batch-wise, they will be divided in to 3 batches (for example, if there are three versions specified). Publisher 1 in batch 1, Publishers 2 and 3 in batch 2, and Publishers 4 and 5 in batch 3. There will be three emails.
Version updated failed: Stitcher-based. For example, if there are seven Publishers, and batch 2 has three Publishers, out of the three Publishers in batch 2, two publishers are connected to Stitcher 1, and the remaining Publisher is connected to Stitcher 2. Upgrade failure notifications will result in two emails.
Version update started but reconnection failed: Profile-based. Failures are due to a timeout.
Click Next to save this configuration.
If an error occurs during an auto-update, refer to these troubleshooting recommendations.
Error | Recommendation |
|---|---|
Publisher auto-update failed while attempting to open the upgrade trigger file. | Check |
Publisher auto-update failed due to timeout. | Contact Netskope Support. |
Publisher reconnection failed due to timeout. | Contact Netskope Support. |
Publisher auto-update failed while upgrading Docker engine. | Check |
Publisher Host OS update failed. | Check |
Publisher Host OS update was stopped. Not enough disk space for the publisher Host OS update. | Check |
Publisher auto-update failed while downloading docker image. | Check network connectivity between the Publisher and |
Publisher software update was skipped. The new version and the existing version are the same. | Check the desired upgrade version. |
Publisher auto-update failed while attempting to stop the existing Publisher container. | Check |
Publisher auto-update failed while attempting to install the Publisher UI package. | Please check logs/publisher_wizard.log and the Docker log with the |
Publisher auto-update failed. | Check |
Publisher auto-update failed while launching the Publisher U.I | Collect the log bundle and contact Netskope Support. |
Publisher software update was stopped. Not enough disk space for the publisher software update. | Check |
This article explains how to configure an Ubuntu Host to enable Publisher's software updates via an Explicit Proxy. Note that this only applies to Publisher outbound traffic for OS and Docker updates. The Publisher tunnel itself does not support traversing explicit proxy and must be allowed to connect direct to the Netskope NPA stitcher IP space.
Configure the
http_proxyandhttps_proxyenvironment variables via/etc/environment. Here is an example used in a configuration to ensure*.goskope.comis excluded.169.254.0.0/16will also need to be excluded for AWS installations.sudo vi /etc/environment export http_proxy="http://10.1.10.1:3128/" export https_proxy="http://10.1.10.1:3128/" export no_proxy="localhost, 127.0.0.1, 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16, 169.254.0.0/16, *.goskope.com"
Next configure
docker-ceproxy settings, similar to the Ubuntu settings.sudo mkdir /etc/systemd/system/docker.service.d/ sudo vi /etc/systemd/system/docker.service.d/http-proxy.conf [Service] Environment="HTTP_PROXY=http://10.1.10.1:3128" Environment="HTTPS_PROXY=http://10.1.10.1:3128" sudo systemctl daemon-reload sudo systemctl restart docker
Log out and log in so the
/etc/environmentvariables are applied.In the Netskope UI, test the configuration by clicking Update on the Publisher page.
Please be aware that any additional software (not included with the Netskope provided package) that is installed on a Publisher instance will be sharing resources with the Publisher application. In addition, Netskope and 3rd-party domains and Publisher software processes may need to be whitelisted in the 3rd-party software.
Network security software that monitors each and every action on the Publisher instance may cause performance issues. You can install security software as long as doing so does not impact Publisher performance. It is your responsibility to ensure that enough resources are allocated for all the software applications running on a Publisher instance.
To troubleshoot issues, Netskope Support may request you to test/recreate without 3rd-party software to narrow down the root cause.
After assigning private apps to specific Publishers, you can change one or more Publishers simultaneously. The Private Apps page enables you to change private apps assignments in bulk. For example:
Change one or more publishers for private apps.
Quickly migrate existing private apps to a new publisher.
Disconnect private apps before deleting a publisher.
To change publishers for private apps:
Go to Settings > Security Cloud Platform > App Definition > Private Apps.
Select one or more private app check boxes and click Change Publishers.
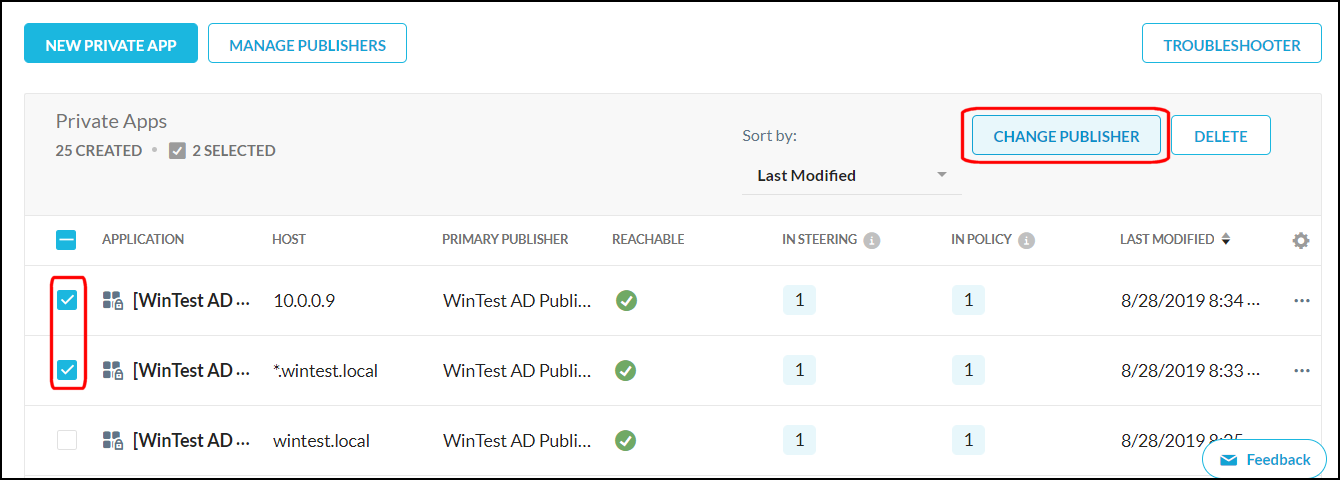
The selected private apps are shown in the Bulk Change Publisher dialog box. Click in the Publisher text field and select one or more publisher in the dropdown list, and then click Save.
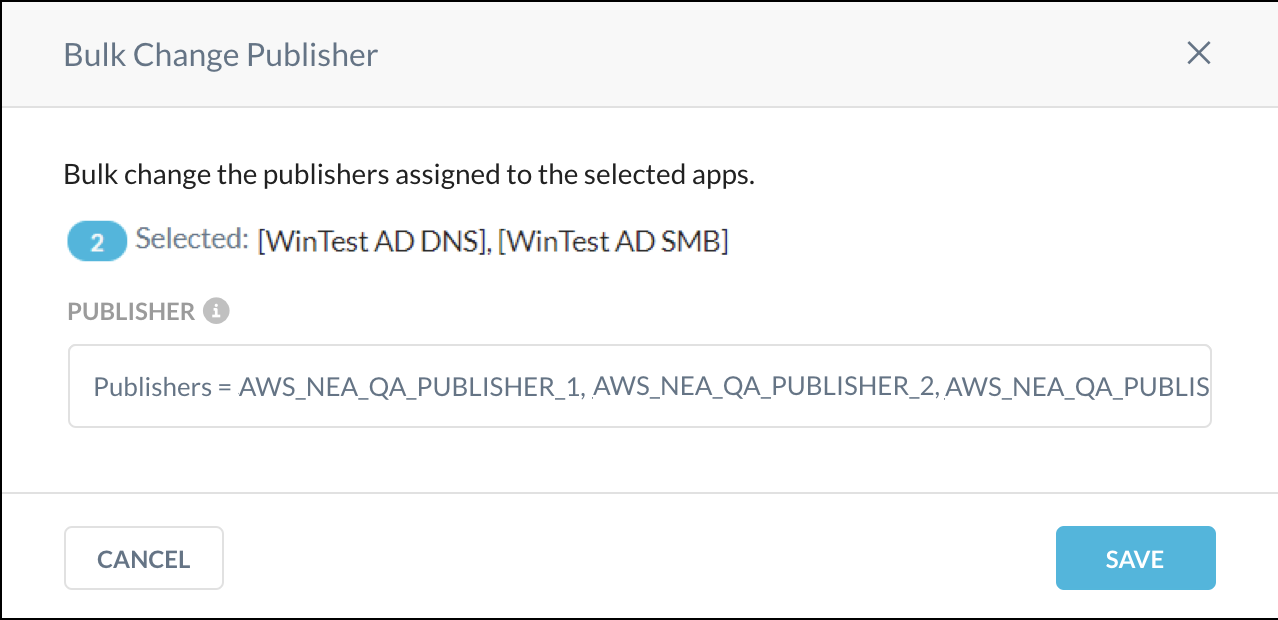
In addition to changing publishers for private apps, this page enables you to delete one or more private apps. Select one or more private app check boxes, and click Delete, and then click Delete again to confirm. If the private app being deleted is specified in a policy, a message box informs you of this factor and you'll need to remove it from the policy in order to delete the private app.
Starting with release 105 (end of May 2023), Netskope Private Access will stop supporting CentOS as the base OS for Publishers and only support Ubuntu-based Publishers.
Ubuntu provides an improved security posture from available CIS benchmarks for Linux distros, and Ubuntu also enables the Auto-Update capability for Publishers. Netskope recommends that you replace existing CentOS Publishers with Ubuntu Publishers using one of these methods.
You can generate a new token for an existing CentOS Publisher and use that to register a new Ubuntu Publisher. This will expire the previous registration for the existing CentOS Publisher and replace it with the Ubuntu Publisher. With this method, you do not have to update the App Definitions that reference the existing CentOS Publishers.
You can configure new Publishers, add them to the App definitions, and then remove the existing CentOS Publishers in the App Definition.
Ubuntu Publishers have feature parity with CentOS Publishers and do not have any capability limitations.
You can use a mix of CentOS and Ubuntu Publishers simultaneously for application access during this move to Ubuntu only support.
This topic explains how to enable SNMP v3 on a Publisher and edit the firewall to allow external monitoring.
Connect to a Publisher using SSH and log in.
On the menu, select
6and exit to the CLI.Update all packages (recommended):
sudo apt-get update
Install SNMP.
sudo apt-get -y install snmpd libsnmp-dev
Configure the agentAddress in the
/etc/snmp/snmpd.conffile. Add this line to the file:disk / 10000
Stop the snmpd service so you can add a user.
sudo service snmpd stop
Add an SNMP v3 user.
sudo net-snmp-config --create-snmpv3-user -A <AuthPassword> -X <CryptoPassword> -a <MD5|SHA> -x <AES|DES> <user>
Restart the SNMPD service.
sudo service snmpd restart
Check that SNMPD is started.
sudo service snmpd status
Verify the firewall (ufw) is running.
sudo ufw status
Configure UFW to allow connections to SNMPD. The SNMP daemon will listen for connections on port 161.
sudo ufw allow in to any port 161 proto udp
Verify the SNMP service has been allowed by the firewall permanently and that UDP traffic on Port 161 is allowed.
sudo ufw status Status: active To Action From -- ------ ---- 161/udp ALLOW Anywhere 161/udp (v6) ALLOW Anywhere (v6)
The following sections provide information about monitoring Publishers. Go to Private Access Troubleshooting for troubleshooting information.
Thresholds to Monitor
CPU Utilization > 75%
Memory Utilization > 90%
Disk Space Left < 1GB
To Validate Resolution of the NPA Cloud
curl https://dns.google/resolve?name=stitcher.npa.goskope.com&type=A&edns_client_subnet=PublisherEgressIP
Nslookup stitcher.npa.netskope.com
Linux OS CLI Commands to Monitor Resources
top, cat /proc/meminfo, htop, sysstat, nload, iftop, nethog, bmon
SNMP OIDs to Monitor Resources
Available space on the disk: .1.3.6.1.4.1.2021.9.1.7.1
Used space on the disk: .1.3.6.1.4.1.2021.9.1.8.1
Percentage of space used on disk: .1.3.6.1.4.1.2021.9.1.9.1
Percentage of inodes used on disk: .1.3.6.1.4.1.2021.9.1.10.1
Path where the disk is mounted: .1.3.6.1.4.1.2021.9.1.2.1
Path of the device for the partition: .1.3.6.1.4.1.2021.9.1.3.1
Total size of the disk/partion (kBytes): .1.3.6.1.4.1.2021.9.1.6.1
Percentage of user CPU time: .1.3.6.1.4.1.2021.11.9.0
Raw user CPU time: .1.3.6.1.4.1.2021.11.50.0
Percentage of system CPU time: .1.3.6.1.4.1.2021.11.10.0
Raw system CPU time: .1.3.6.1.4.1.2021.11.52.0
Percentage of idle CPU time: .1.3.6.1.4.1.2021.11.11.0
Raw idle CPU time: .1.3.6.1.4.1.2021.11.53.0
Total RAM in machine: .1.3.6.1.4.1.2021.4.5.0
Total RAM used: .1.3.6.1.4.1.2021.4.6.0
Total RAM Free: .1.3.6.1.4.1.2021.4.11.0
Total bytes received on the interface: .1.3.6.1.2.1.2.2.1.10
Total bytes transmitted on the interface: .1.3.6.1.2.1.2.2.1.16
Connection Segment | Description | Example |
|---|---|---|
Registration Logs - Publisher | Logs to verify successful registration, or failed registration. | Logs to check: ~/logs/publisher_wizard.log Successful Registration: 2021/07/27 20:00:41 UTC Registering with your Netskope address: ns-6413.us-sv5.npa.goskope.com 2021/07/27 20:00:41 UTC Publisher certificate CN: 130dbd9d40e4ad35 2021/07/27 20:00:41 UTC Attempt 1 to register publisher. 2021/07/27 20:00:43 UTC Publisher registered successfully. Failed Registration: 2021/08/19 13:21:06 UTC Attempt 1 to register publisher. 2021/08/19 13:21:08 UTC Get https://ns-6413.us-sv5.npa.goskope.com/api/discovery: x509: certificate signed by unknown authority 2021/08/19 13:21:08 UTC Registration failed because a discovery call didn't succeed. Please generate a new token and try again. |
Publisher ⇔ Netskope connectivity logs | Logs to check: ~/logs/agent.txt Succesful tunnel connection: eventlog.cpp:115:logPublisherTunnelEvent():0x0 {"eventId": "NPACONNECTED", "publisherId": "130dbd9d40e4ad35", "stitcherIp": "163.116.135.6", "tenant": "ns-6413.us-sv5.npa.goskope.com"} Successful connection and certificate verification: sslhelper.cpp:80:verify_callback():0x0 Verified: /DC=io/DC=newedge/CN=New Edge Root CA Failed connection due to SSL error sslhelper.cpp:302:logSslError():0x0 SSL Error 5 error:00000005:lib(0):func(0):DH lib | |
Publisher⇔ Netskope HTTPS logs | Management Plane: openssl s_client -connect ns-{TENANTID}.{POPNAME}.npa.goskope.com:443 -servername ns-{TENANTID}.{POPNAME}.npa.goskope.com Data Plane: openssl s_client -connect stitcher.npa.goskope.com:443 -servername ns-{TENANTID}.{POPNAME}.npa.goskope.com | |
Publisher⇔ Application Connection Logs | Logs to check: ~/logs/agent.txt Application definition and reachability: reachability.cpp:109:parse():0x2484790 Added protocols login.microsoftonline.com:tcp:443-443; tcp:80-80; udp:443-443; udp:80-80; Application connection: tcpproxyhandler.cpp:35:TcpProxyHandler():0x2504cf0 Creating tcp connection to login.microsoftonline.com:443 | |
Client connects and disconnects | May follow Publisher disconnects and can be used to correlate issues: neconfig.cpp:121:setClientId():0x0 Set clientId l0ThzLYeZnqA neconfig.cpp:121:setClientId():0x0 Set clientId l0ThzLYeZnqA Indicates a graceful shut down and will not always be present if there’s an issue: L3ClientChannel.cpp:48:destroy():0x1292810 Cleaning up l3clientChannel |
Password policy for the Publisher are enabled for versions 101 or lower. The Publisher host user password may expire if not changed regularly. This article explains how to disable the password expiry. Versions 102 and above will have the password policy disabled, and you are now required to apply your corporate password policy to your Publishers.
If your AWS publisher was deployed from the Netskope prebuilt images (from AWS marketplace), the following instructions can help you to remove the password expiry. This approach is applicable for version 94+ Ubuntu Publishers.
The Ubuntu publisher built in with the AWS System Manager(SSM) agent. You can use SSM to log in to the Publisher EC2 instance and remove the password expiry.
Create an IAM role with the SSM permissions.
Create an IAM role.
Add permission policy AmazonSSMManagedInstanceCore into the IAM role.
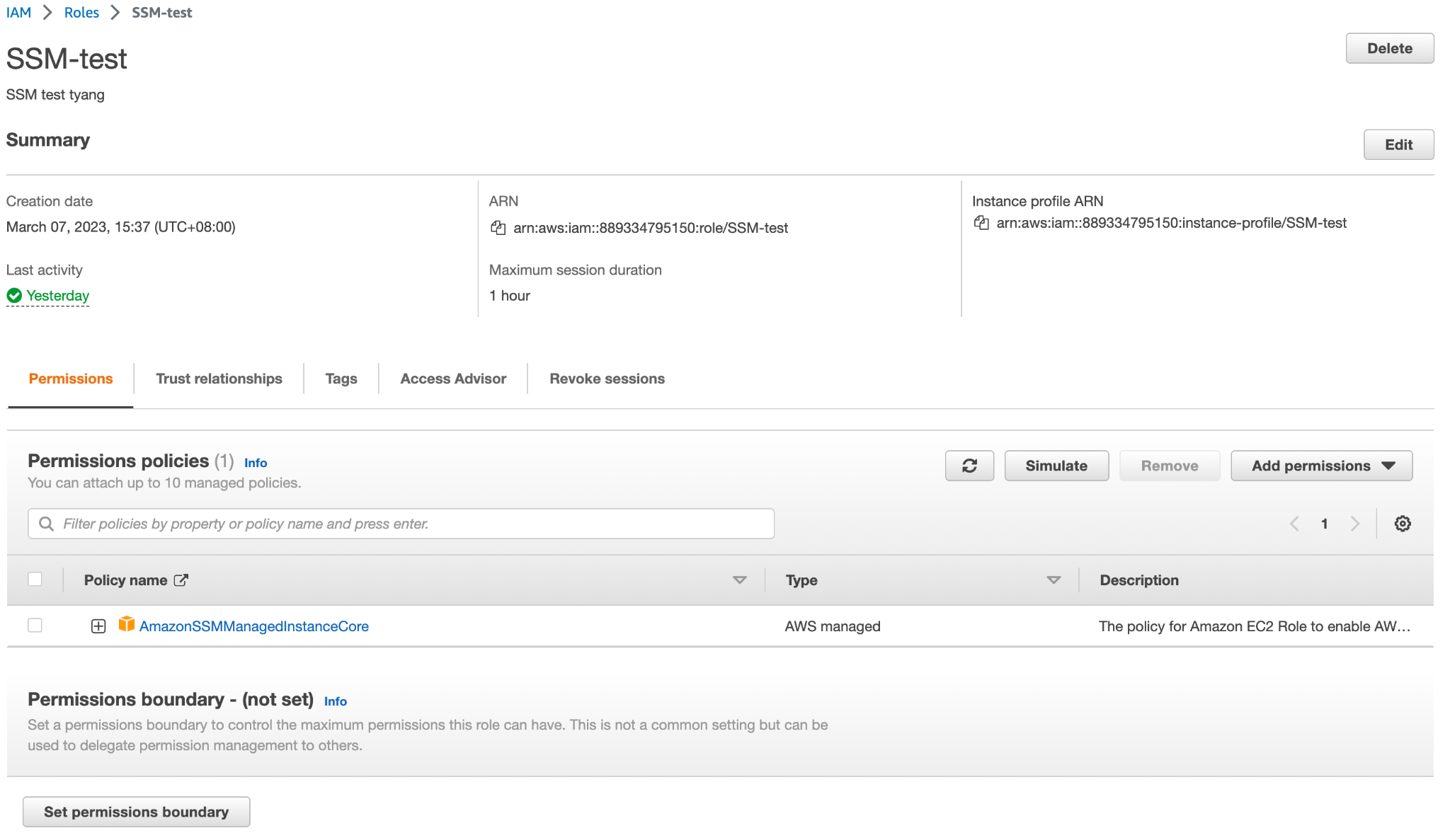
Attach the IAM role to the Publisher EC2 instance.
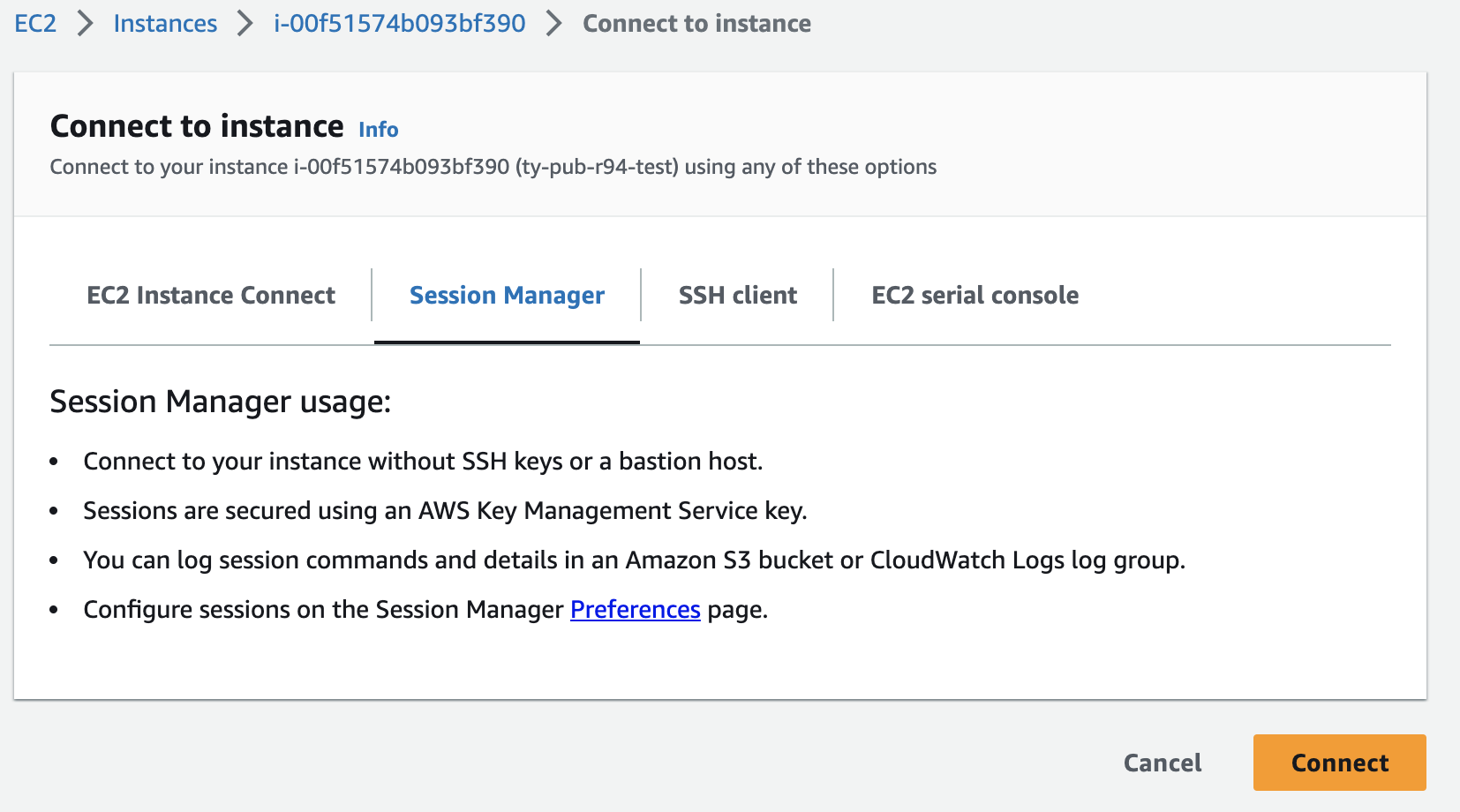
Connect with the Publisher EC2 instance via SSM.

After you log in into the Publisher, use this following command to disable the password expiry.
sudo chage -m 0 -M 99999 ubuntu
Use the following to confirm the password expiry was disabled or not.
sudo chage -l ubuntu
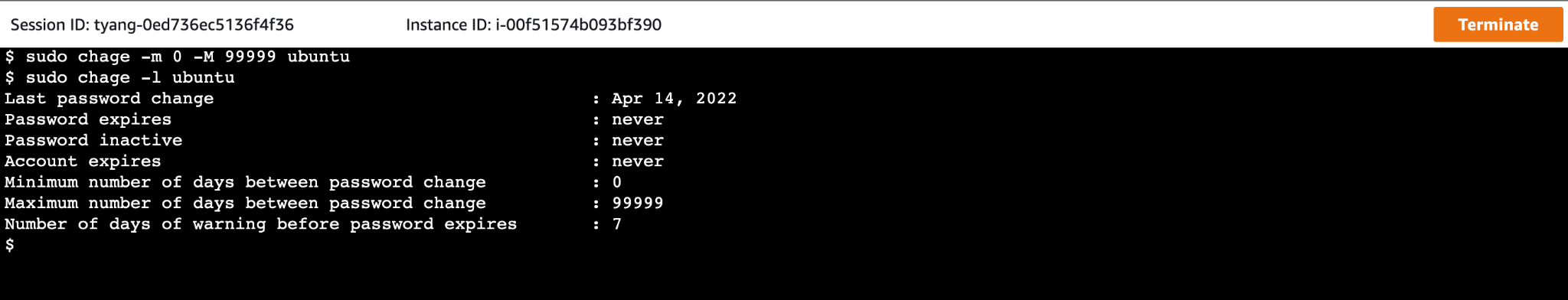
You should able to log in to the Publisher via SSH after disabling the password expiry.
If your Azure publisher was deployed from the Netskope prebuilt images (from Azure marketplace), the following instructions can help you to remove the password expiry. This approach is applicable for version 96+ Ubuntu Publishers.
You can use the built-in Reset password function in the Azure portal.
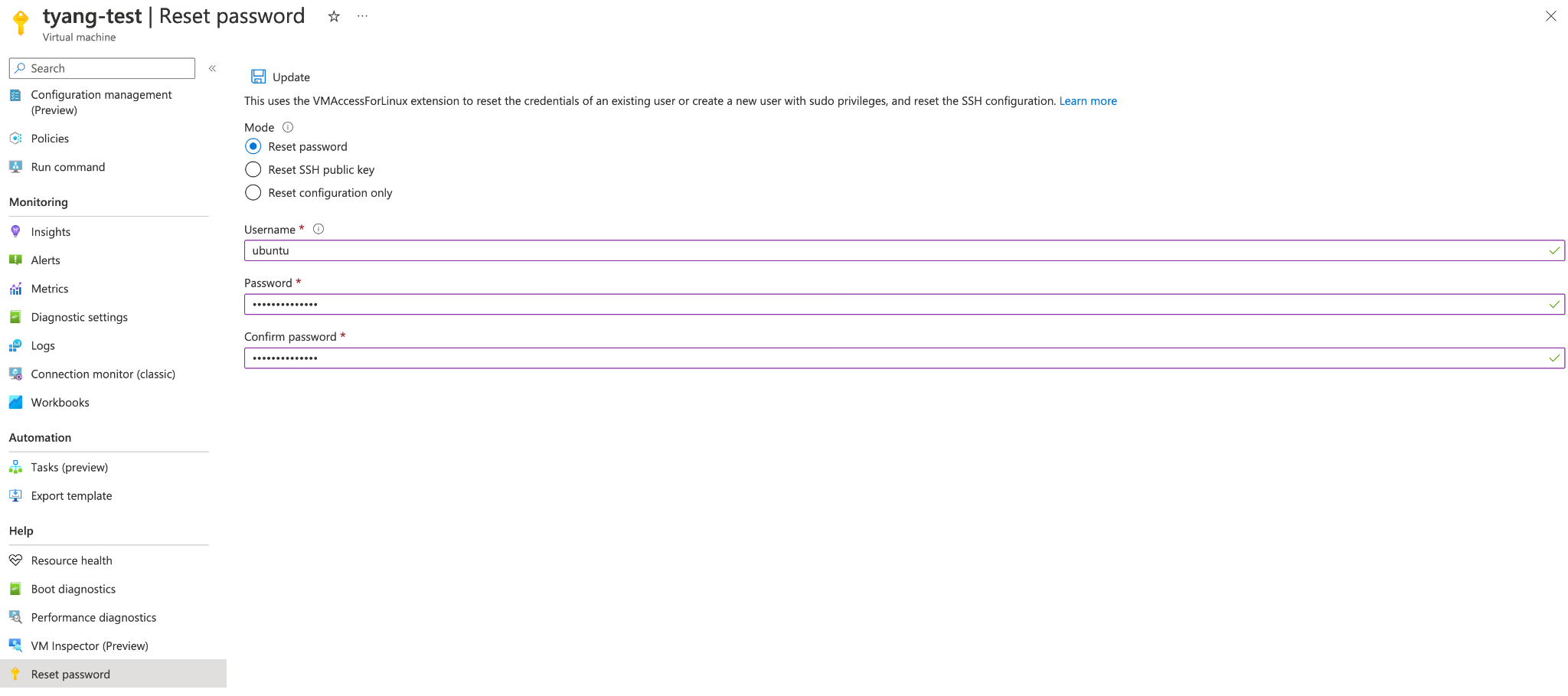
For Mode, select Reset Password, your username, and new password (twice) to reset your ubuntu password.
After resetting the password, you should be able to log in to the Publisher via SSH.
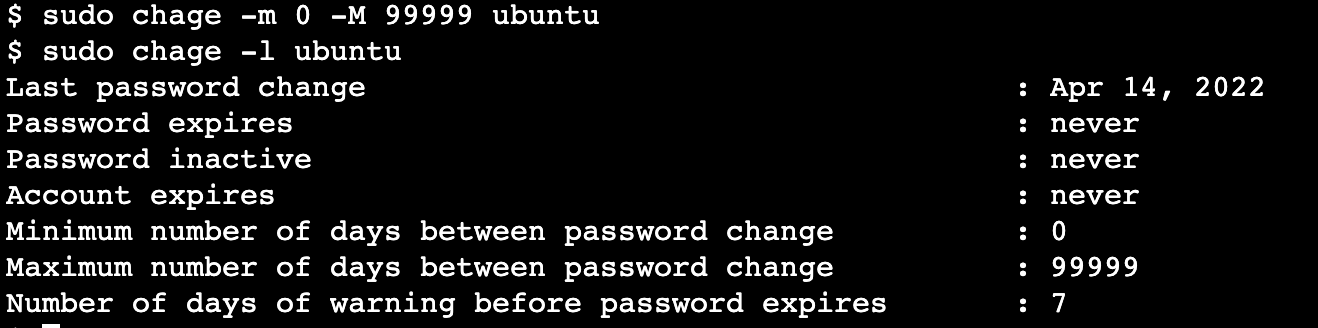
Disable the password expiry using this command.
sudo chage -m 0 -M 99999 ubuntu
Use this command to confirm if the password was disabled successfully or not.
sudo chage -l ubuntu
If your Azure publisher was deployed from the Netskope prebuilt OVA/VHDX images, use these steps to remove the password expiry. You should be able to boot into Single User Mode from Linux GRUB to remove the password expiry.
Reboot the VM.
Enter the GRUB menu by keeping pressing the shift key. If you are using Windows, you may need to disable the sticky key.
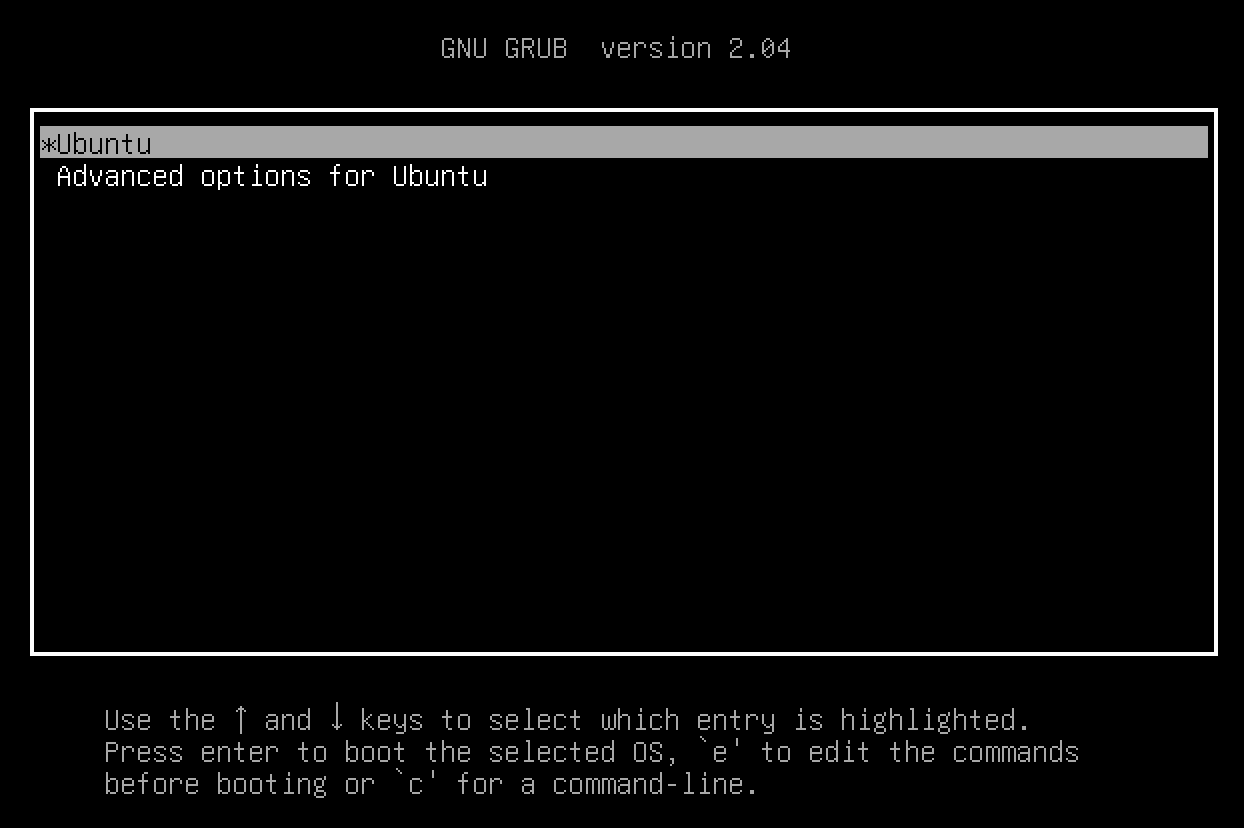
From the GRUB boot prompt, press the E button to edit the first boot option.
In the GRUB menu, find the kernel line starting with
linux /vmlinuzand addinit=/bin/bashat the end of the line.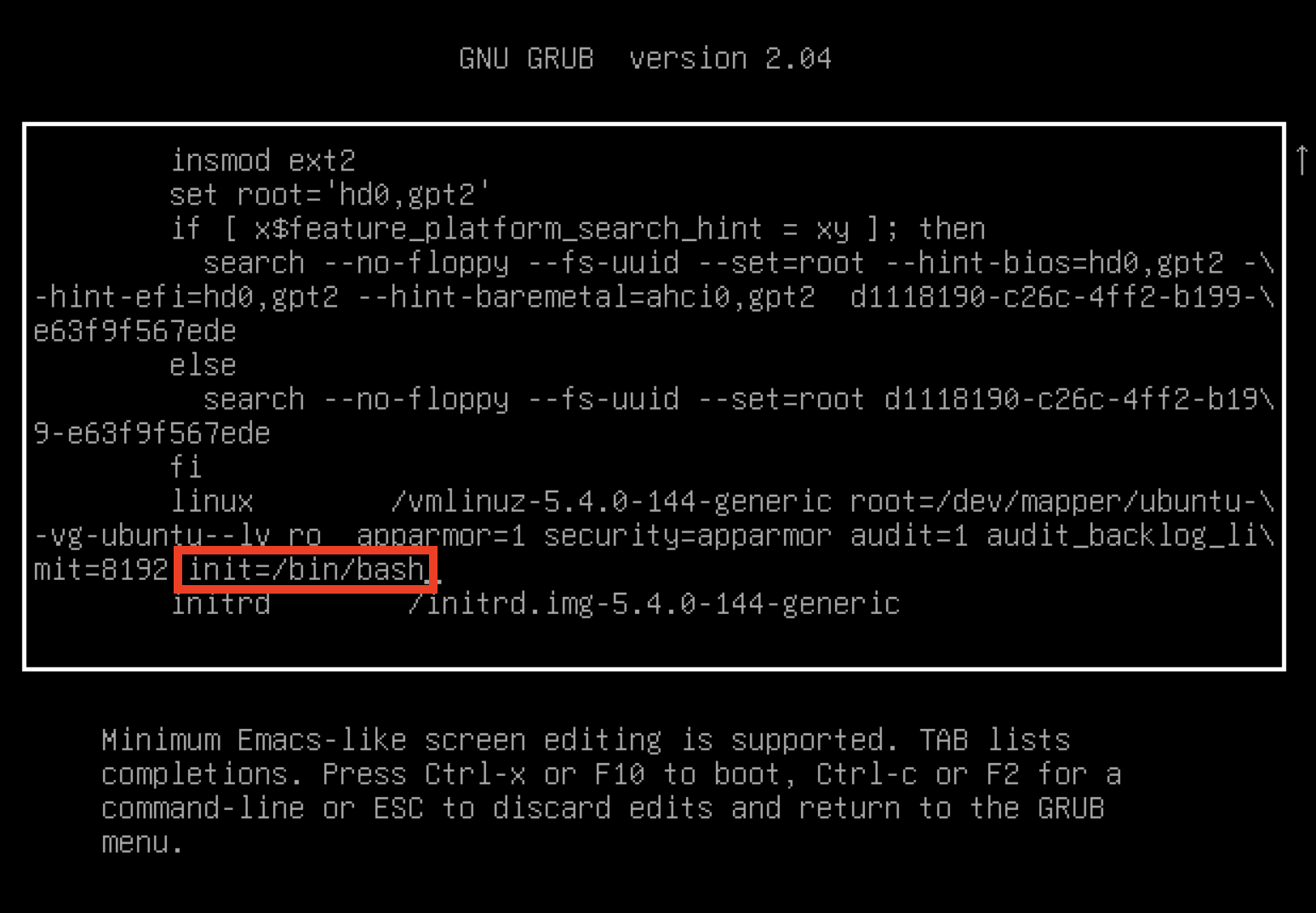
Press CTRL+X to save the changes and boot the server into single-user mode. Once booted. the server will boot into the root prompt.
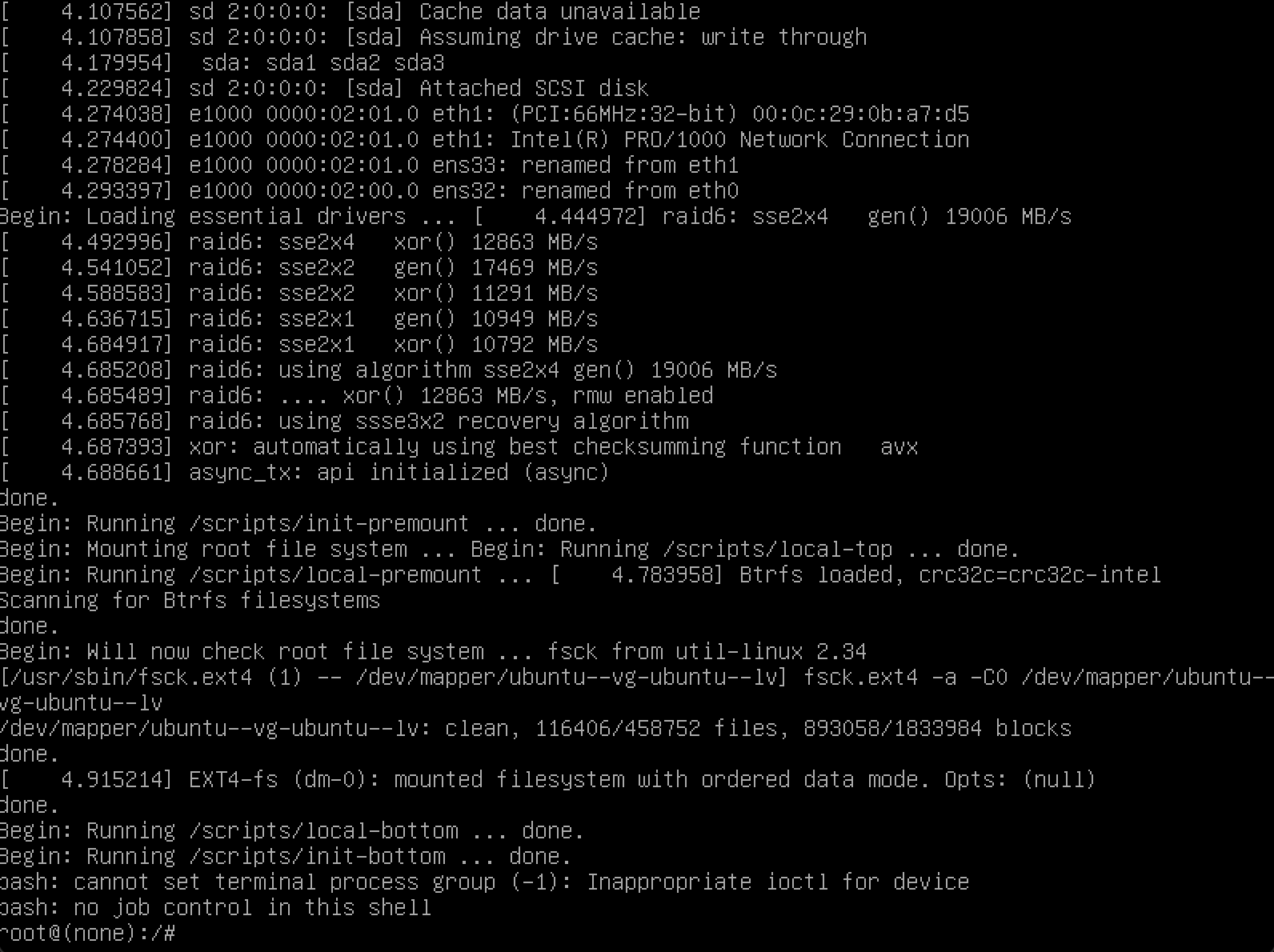
Type in the command
mount -o remount,rw /to mount the file system.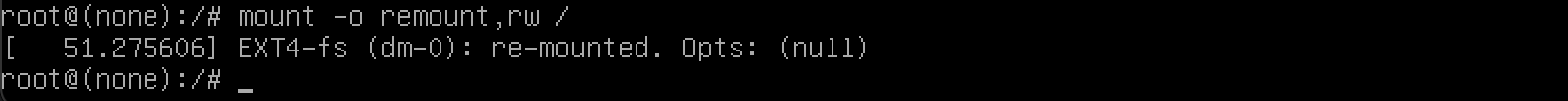
Use
chage -m 0 -M 99999 ubuntuto disable the password expiry, and usechage -l ubuntuto confirm if the password was disabled successfully or not.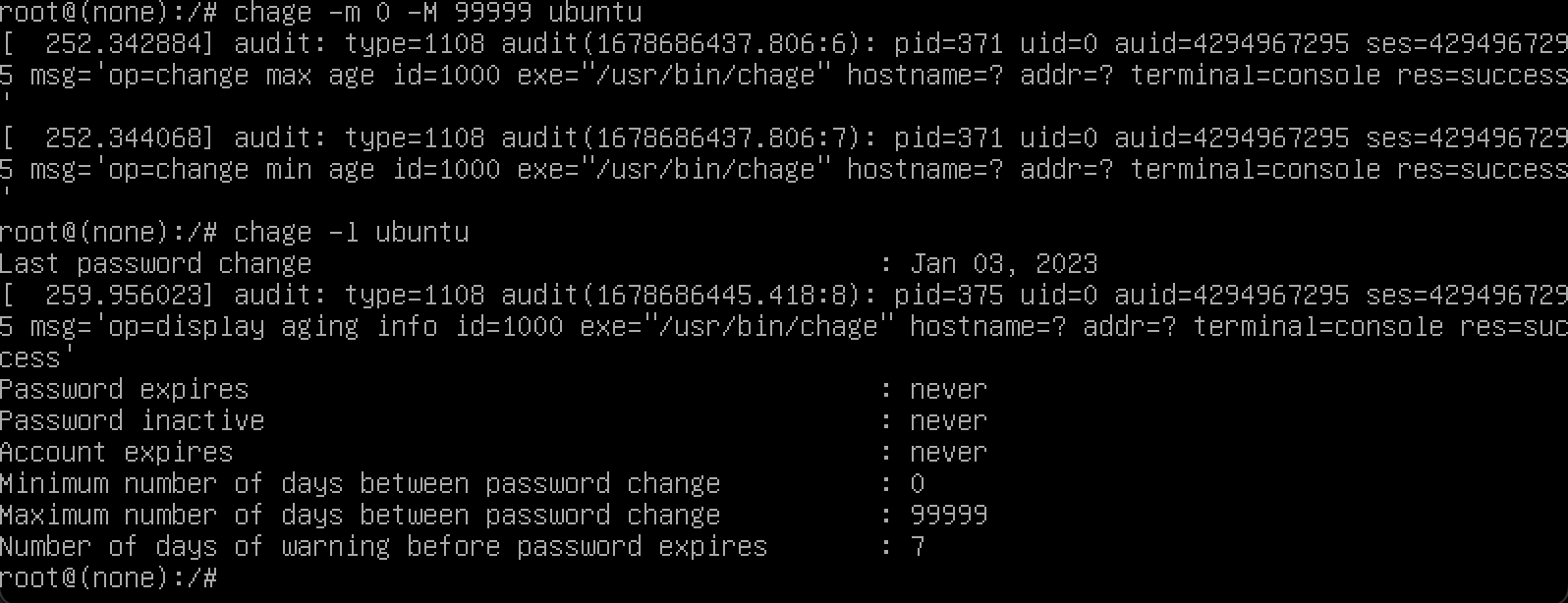
Reboot the system. Use
reboot -fto reboot the VM.You will see the GRUB menu again. Press enter on the first item or wait 30 seconds, the boot process will continue. And you should be able to log in into your VM again with your password.