Palo Alto Networks Panorama Plugin for Threat Exchange
This document explains how to configure the Palo Alto Networks Panorama integration with the Threat Exchange module of the Netskope Cloud Exchange platform. The Palo Alto Networks Panorama plugin retrieves information about domains, IP addresses, filehases (SHA256) from Wildfire logs, and URLs from URL-Filtering logs.
Pull | Yes |
Push | No |
To complete this configuration, you need:
A Netskope tenant (or multiple, for example, production and development/test instances).
A Netskope Cloud Exchange tenant with the Threat Exchange module already configured.
A Panorama Base URL and API Key.
Permissions needed for plugin. The API Key needs to have XML API permissions available to pull the indicators. Follow this document for the Panorama platform to give permission to your user.
Get your Panorama Base URL and API Key.
Configure the Panorama plugin
Validate the Panorama plugin.
Click play to watch a video.
Base URL
The URL of their Palo Alto Networks instance should be the Base URL for the configuration parameters.
For example:
https://<your-panorama-domain>
API Key
Get API Key by following the steps mentioned in this document.
In Cloud Exchange, go to Settings > Plugins.
Search for and select the Palo Alto Networks Panorama box to open the plugin creation page.
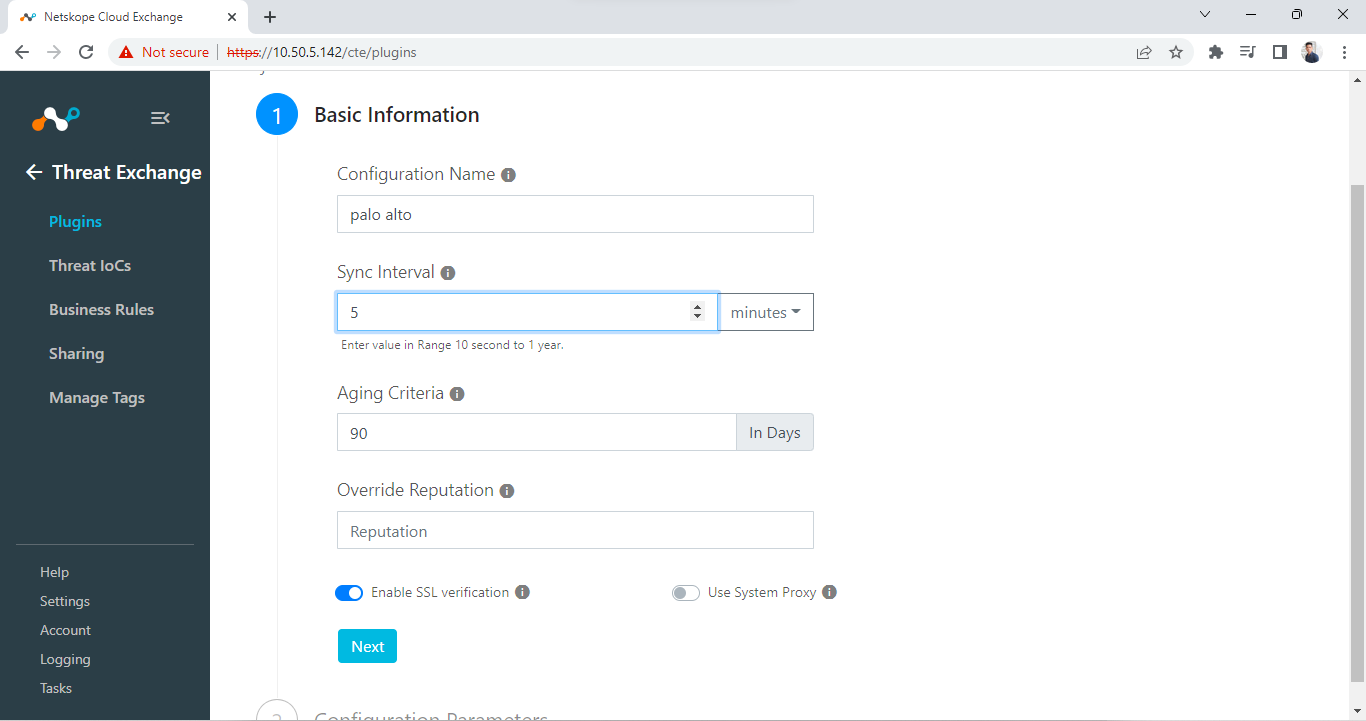
Enter these parameters:
Configuration Name: Unique name for the configuration.
Sync Interval: Leave Default.
Aging Criteria: Leave Default.
Override Reputation: Leave Default.
Enable SSL verification: Enable if SSL verification is required for communication.
Use System Proxy: Enable if the proxy is required for communication.
Click Next.
Enter your Panorama Base URL and API Key.
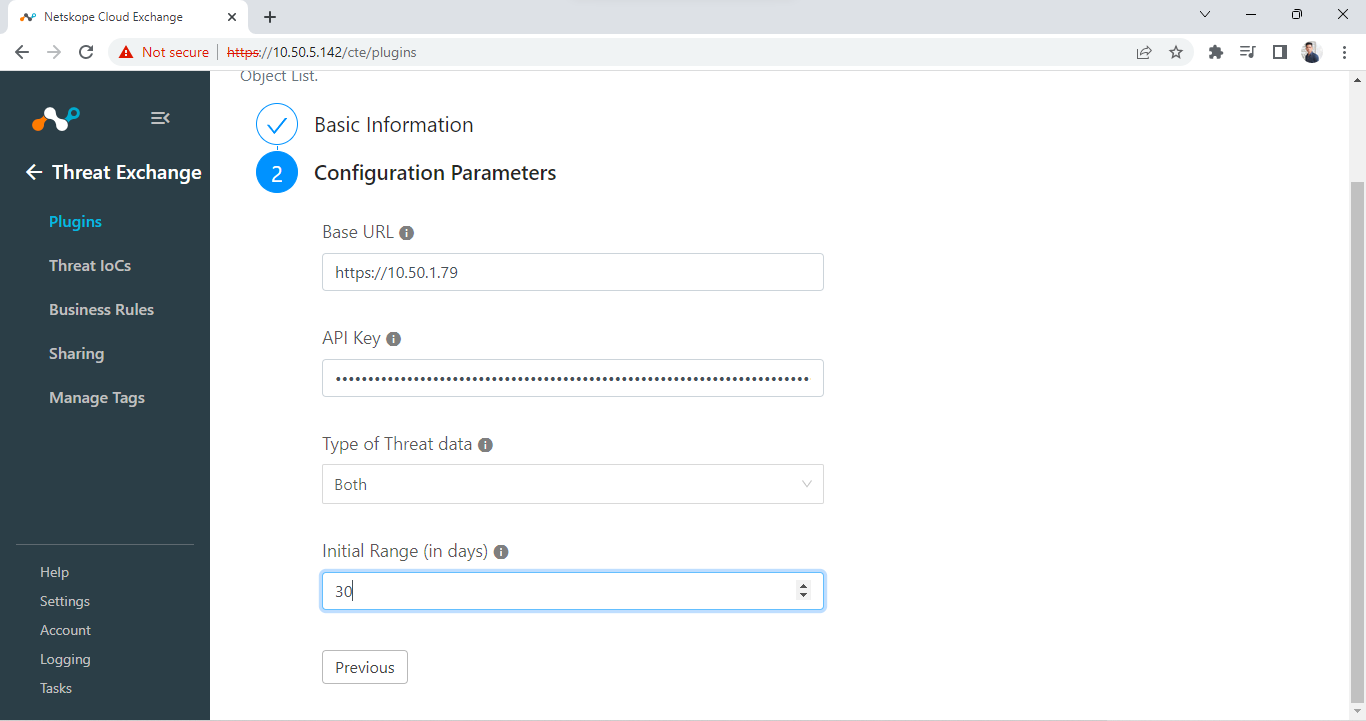
Select the Type of Threat Data. (Select Malware if you want to pull only file hashes or URL; if you want to pull only URLs, and select Both if you want to pull both.
Enter an Initial Range (how many days of indicators you want to pull initially.
Click Save.
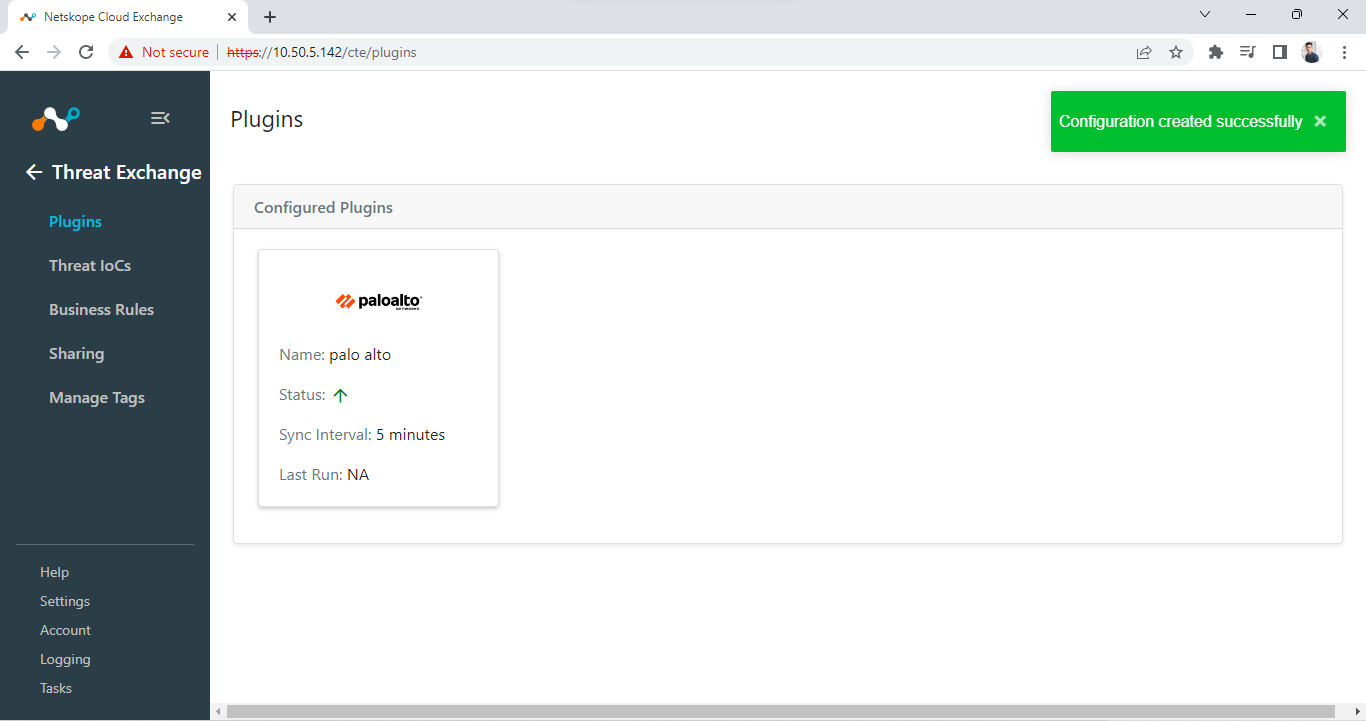
Now plugin is configured and you’ll see plugin configuration in Threat Exchange > Plugins.
In Cloud Exchange:
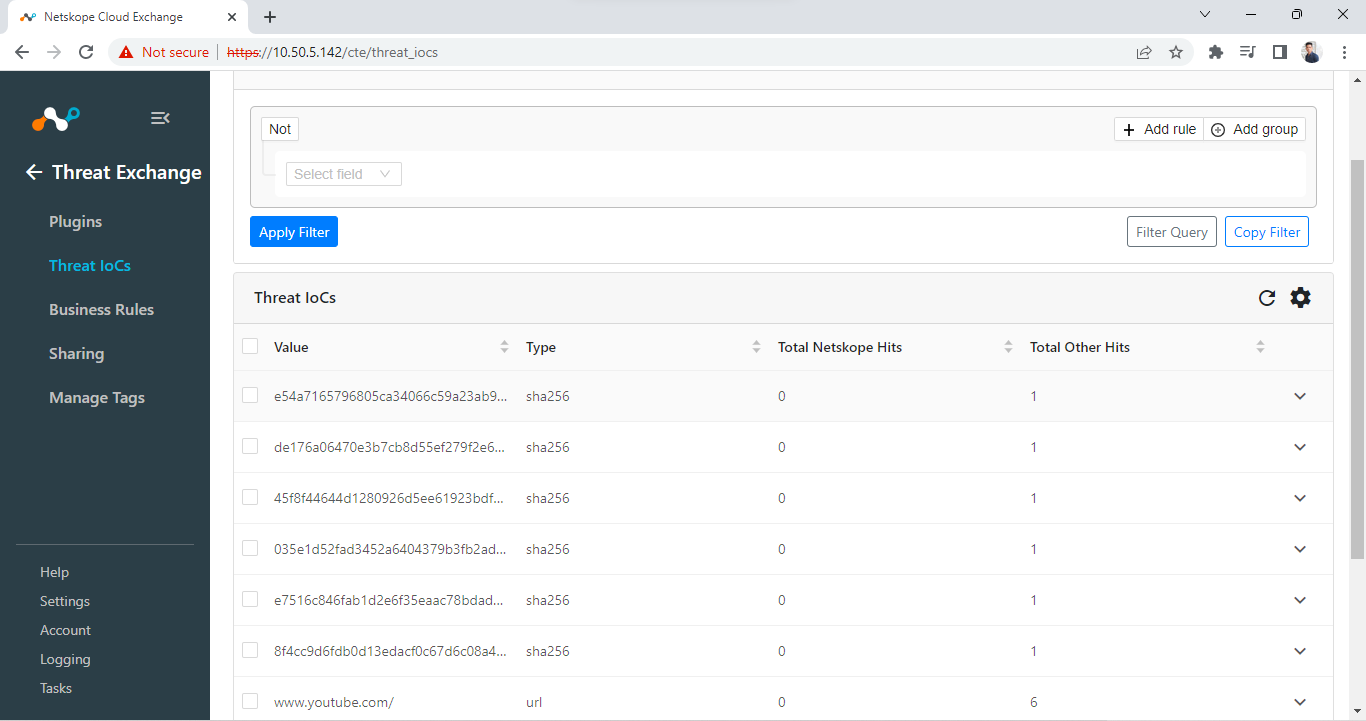
Go to Threat Exchange > Threat IoCs.
Here you’ll see all the IoCs that are fetched from Palo Alto Networks Panorama.
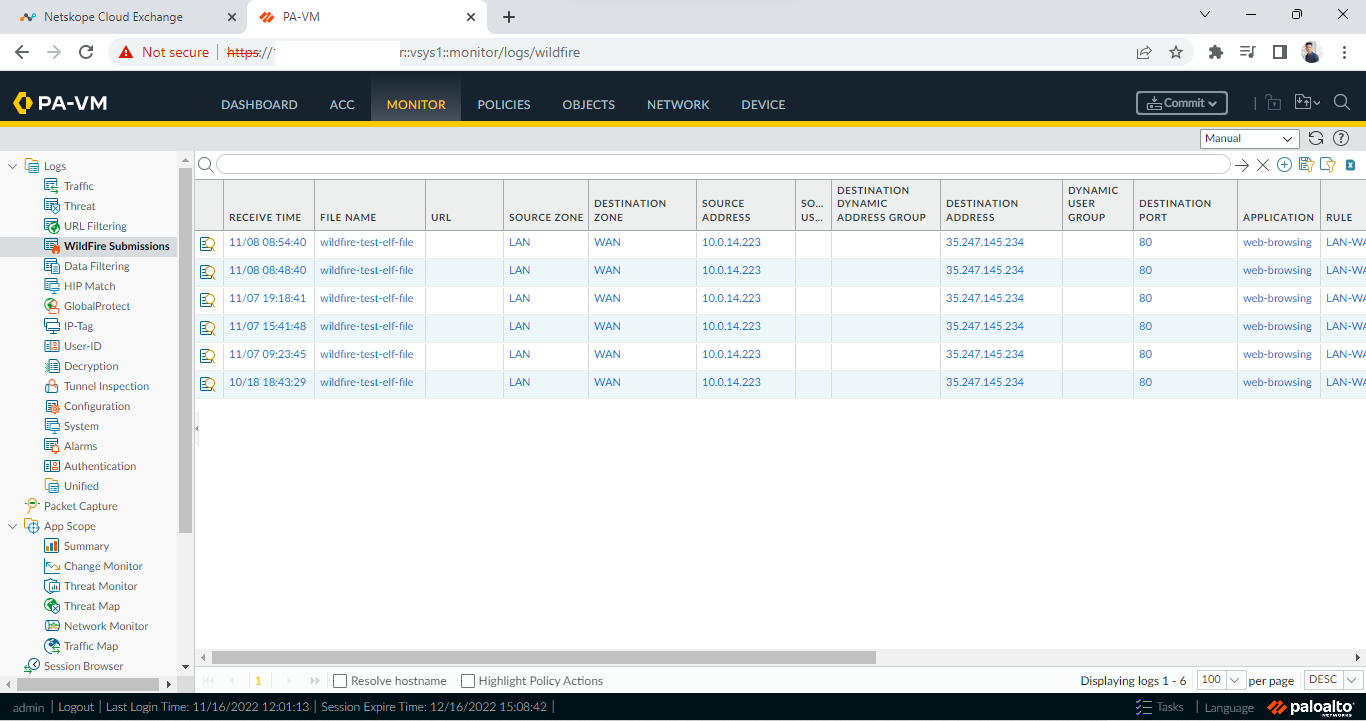
In Panorama:
Go to Monitor > Wildfire Submissions. File hashes are fetched from this page. So, if this logs appear here, then indicators will be pulled in Netskope CE.
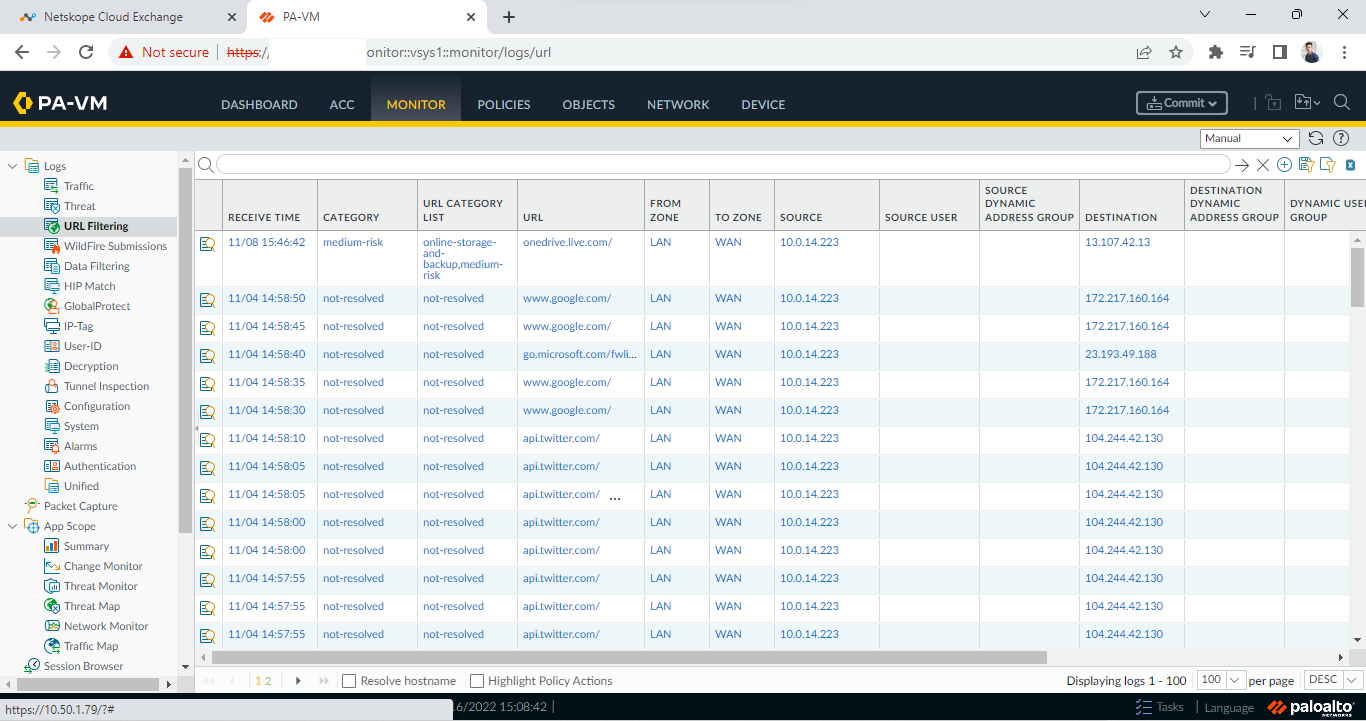
Go to Monitor > URL Filtering. File hashes are fetched from this page. So, if logs are available in this page, then it will be fetched as an indicator in Netskope CE.
First seen time and Last seen time will be converted automatically according to local time zone of the device.
We only support pulling 100k indicators as of now, which takes around 2 and a half hours to pull and then a few more hours to store in CE. If the indicators to be pulled is greater than 100k you might start to see some performance issues in CE, like indicators taking too long to be fetched, CE taking time to respond, etc. This issue will be fixed in the next release of CE.