ThreatQ Plugin for Threat Exchange
This document explains how to configure the ThreatQ integration with the Threat Exchange module of the Netskope Cloud Exchange platform. This plugin only pulls the IoCs from the ThreatQ platform. This plugin does not support sharing of indicators with the ThreatQ platform.
Fetched indicator types | MD5, SHA256, URL |
Shared indicator types | None |
To complete this configuration, you need:
A Netskope tenant (or multiple, for example, production and development/test instances).
A Netskope Secure Web Gateway subscription for URL sharing.
A Threat prevention subscription for malicious file hash sharing.
A Netskope Cloud Exchange tenant with the Threat Exchange module already configured.
A ThreatQ instance.
Connectivity to the following host: https://10.50.1.21/login
Get your ThreatQ Client ID and Client Secret.
Configure the ThreatQ Plugin.
Validate the ThreatQ Plugin.
Log in in into the ThreatQ VM.
Run the following command to generate a Client ID and Client Secret.
sudo /var/www/api/artisan threatq:oauth2-client --name=Netskope
Copy the Client ID and Client Secret. These are needed to configure the ThreatQ plugin.
In Cloud Exchange, go to Settings > Plugins.
Search for and select the ThreatQ plugin box.
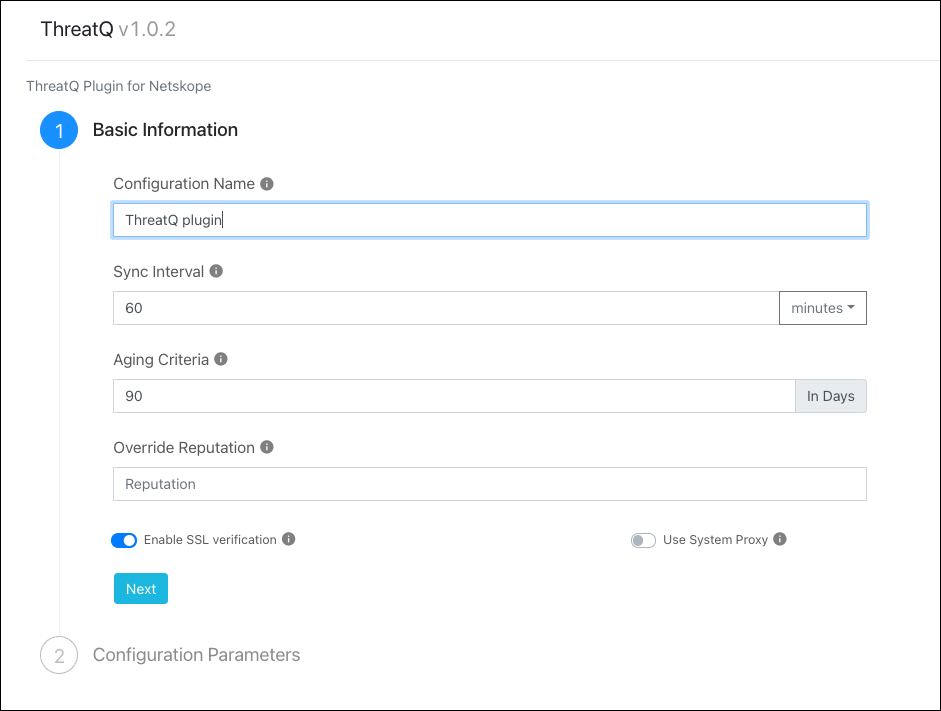
For Basic Information, enter these parameters:
Configuration Name: Unique name for the configuration.
Sync Interval: Leave the default.
Aging Criteria: Expiry time of the plugin in days. ( Default: 90 )
Override Reputation: Set a value to override the reputation of indicators received from this configuration.
Enable SSL Validation: Enables SSL Certificate validation.
Use System Proxy: Enable if proxy is required for communication.
Click Next.
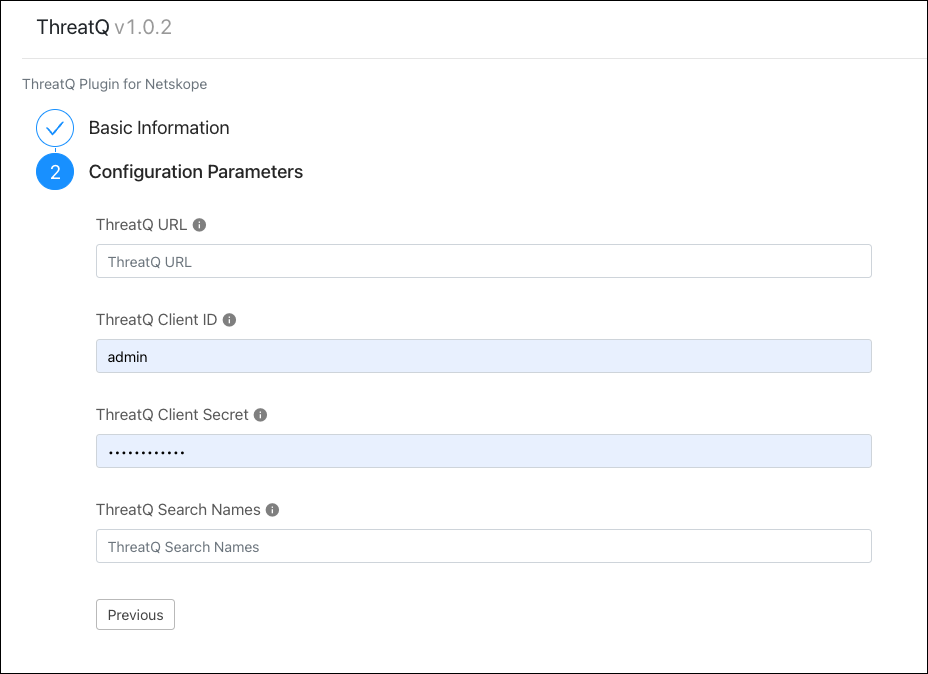
For Configuration Parameters, enter these values:
ThreatQ URL: This is the URL to the ThreatQ instance.
ThreatQ Client ID: This is the ThreatQ Oauth2 Client ID.
ThreatQ Client Secret: This is the ThreatQ Oauth2 Client Secret.
ThreatQ Search Names: These are the ThreatQ search names that contain the data to be imported. This should be a comma-separated list of search names, or a single search name.
Click Save.
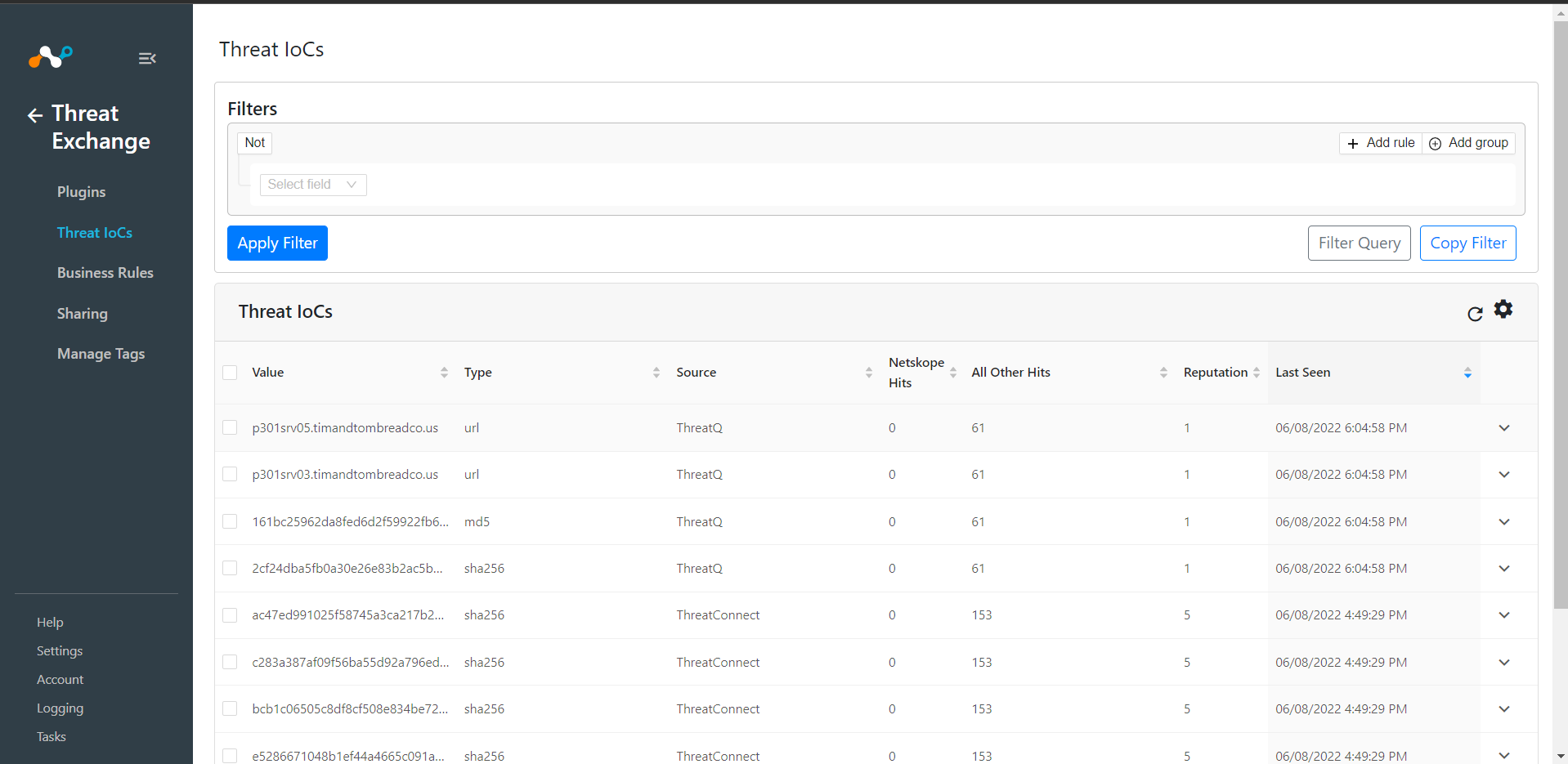
Based on the plugin configuration, indicators will be pulled from the ThreatQ platform. Go to Threat Exchange > Threat IoCs to view the received IoCs.
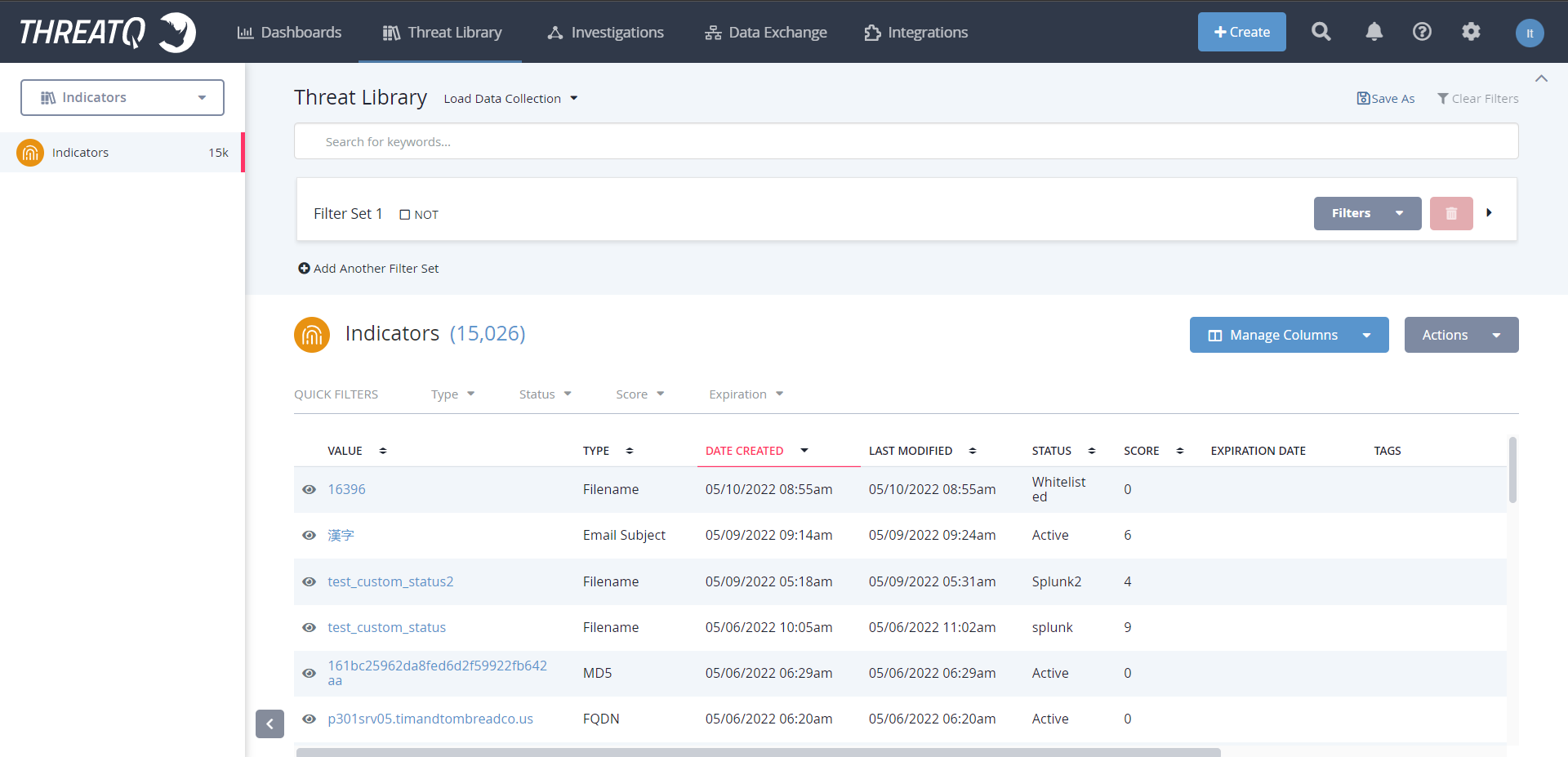
To verify IoCs in the ThreatQ Platform, go to ThreatLibrary > Indicators.