SAML Forward Proxy
This feature is a mode of Netskope's forward proxy. Enabling this feature allows you to deploy Netskope and continue your current SAML deployment for authentication. You can use Netskope as an authentication mode to integrate with an Identity Provider (IdP). You can configure multiple IdPs to authenticate users with different IdPs, based on criterion (such as, access methods, authentication domain, or network location) for SAML forward proxy authentication. Additionally, you can fine tune an IdP service with granular options (like network location, authentication domain) to be used only if specific conditions are matched.
Note
Multiple IdP is a Controlled General Availability (formerly known as Limited Availability) feature. Contact your Sales Representative or Support to enable this feature.
Multiple and Concurrent IdP
You can configure and concurrently enable multiple IdP services to authenticate users based on various criterion. The primary criteria, however, is the the access method. The supported access method include:
IPsec
GRE
Cloud Explicit Proxy
NS Client Enrollment
When enabled, the multiple IdP offers the following features:
Admin can enable multiple IdP services for different access methods.
Migrate an existing IdP from the older configuration set up to new set up and preserve existing configurations.
When there are more than one IdP for a particular access method, the first matched access method will be used.
If an IdP service is configured for ALL access methods with additional options for particular Network Location then only the requests from those network locations irrespective of the access method will use this IdP service.
Auth service domains need not be explicitly mentioned in the domain bypass.
Configuring Forward Proxy IdP Authentication
The SAML Forward Proxy must be configured with the Assertion Consumer Service (ACS) URL, IdP URL, and IdP Certificate by following this procedure.
Go to Settings > Security Cloud Platform > Forward Proxy > SAML. The SAML Entity ID and the SAML Access URL are listed here for your reference, along with a button to download the SAML certificate.
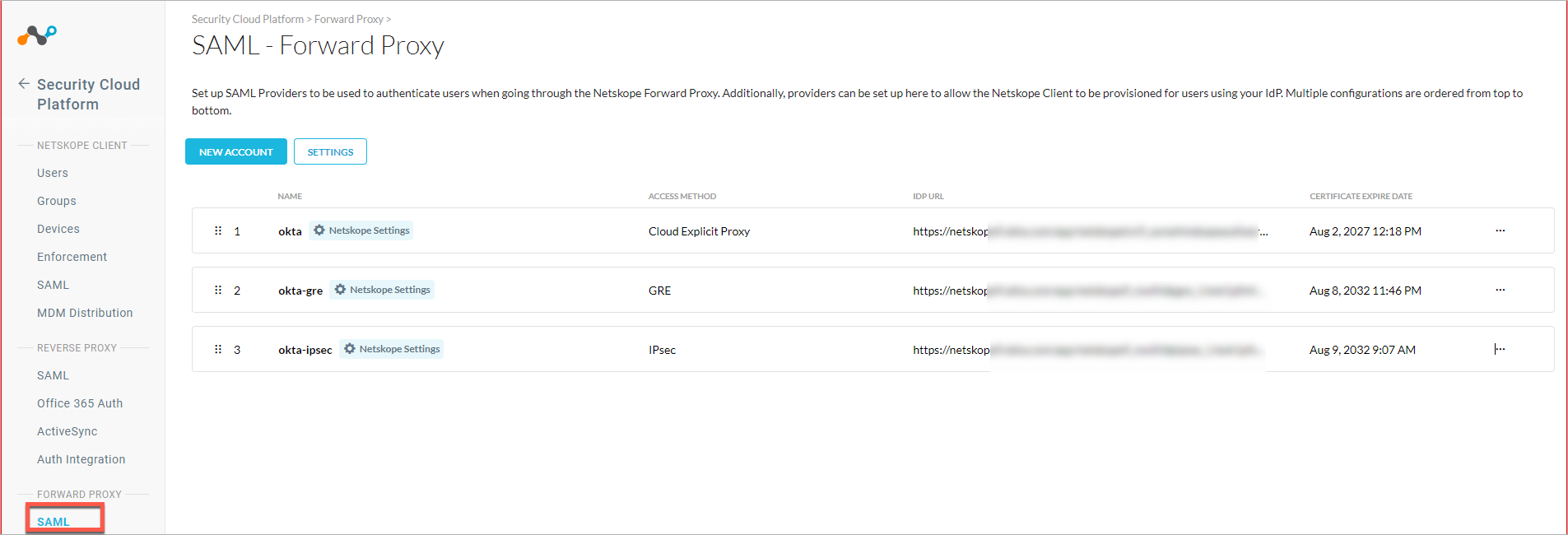
NAME: The name of the IdP service.
Access Method: The access method that will be used for authenticate users using this IdP service.
IDP URL: This is the URL used to redirect the user to IdP site for authentication.
Adding a New Forward Proxy IdP Service
To add a new IdP as an authentication service, do the following:
Go to Settings > Security Cloud Platform > Forward Proxy > SAML.
Click the NEW ACCOUNT button. In the New Account pop-up window, enter the following:
Name: Provide a name to identify the IdP service.
Access Method: Select the access method that will use this IdP service.
All - To use the IdP service for all access methods.
IPSec - Select this option to use the IdP service for IPsec access methods. For granular control, you can enable the IdP service for all tunnels or specific tunnels. To enable this IdP for a specific tunnel, select Specific tunnel from the list and then select the tunnel from the IPSec Tunnel list.
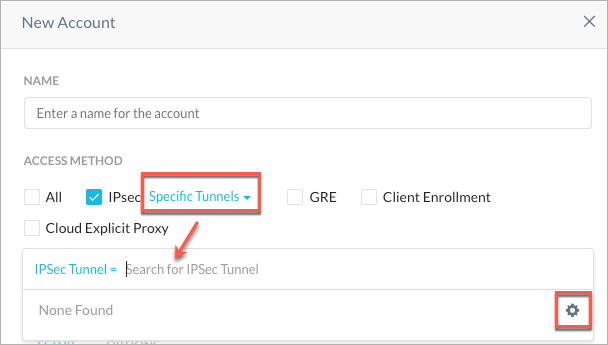
Note
If you have not configured an IPSec tunnel yet, click the gear icon to access the IPSec tunnel creation interface.
GRE - To use the IdP service for GRE access methods. For granular control, you can enable the IdP service for all tunnels or specific tunnels. To enable this IdP for a specific tunnel, select Specific tunnel and then select the tunnel from the GRE Tunnel list.
Client Enrollment - To use the IdP service for client enrollment workflow.
Cloud Explicit Proxy - To use the IdP service when the access method is via Netskope Proxy.
IdP Configuration - In the Setup tab, enter the following details to configure the IdP service.
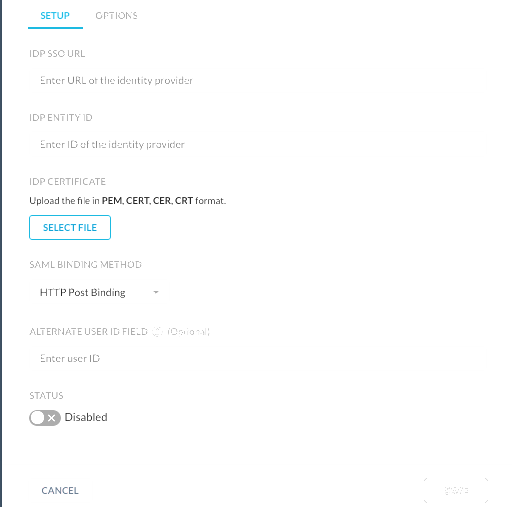
IDP SSO URL: This is the URL used to redirect the user to IdP site for authentication. Contact your third party Identity Provider and add the unique IdP login URL in this field.
IDP Entity ID: An entity ID is a globally unique name for a SAML entity, either an Identity Provider (IdP) or a Service Provider (SP).
IDP Certificate: Upload certificate of the third party IdP in this field. This is required by Netskope to validate the signature of the SAML assertion.
SAML Binding Method: Select between HTTP Post and HTTP Redirect as a method of communication method between IdP and tenant.
Alternate User Id Field - Netskope looks at the NameID field in the SAML assertion to get the user identity. If you would like to use another field for user identification, type the name of the SAML attribute in this field.
Select the Status toggle to enable or disable the IdP service.
Click Save.
Options tab. These are optional settings. In this tab you can specify granular controls to an IdP service so that the IdP is used only when a very specific criteria (like network location and authentication domain ) is matched.
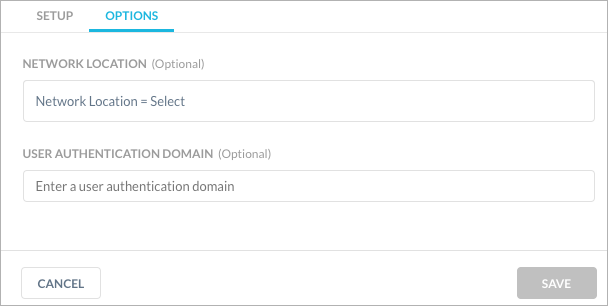
Network Location - Enter the list of network location that must be matched for the access method. For more information about Network Location see Network Location .
User Authentication Domain - Enter the user authentication domain that will matched along with the access method for the IdP service.