Configure an API Data Protection Policy for Vera
The following sections describe how to configure an API Data Protection policy for Vera. To edit a section previously completed, click on the pencil icon beside the section title.
Application
To configure an API Data Protection policy:
In the Netskope UI, go to Policies > API Data Protection and under the SaaS tab, click New Policy.
In the Application section, select the app.
Note
If you select Google Drive as the application type, the administrator has an option to scan Content or Connected Apps/Plugins.
In the Instance section, select the app instance for the policy.
Click Next, and then go to the topic in this guide that matches the section you're configuring on the New API Data Protection Policy page.
Office 365 SharePoint Limitation
For Office 365 SharePoint application, when a policy is created on a parent site, it is not applied on the content in a sub-site under the parent site. If a policy has to be applied on sub-sites, you have to explicitly select in the policy.
Users
This section of the API Data Protection Policy page specifies the users and groups that can trigger a policy violation.
Select all sites, all users, a subset of users, user profiles, user groups, subset of domains, all team drives, or subset of team drives. You can search for and select specific users, user profiles, user groups, subset of domains, and subset of team drives. A list displays when you search for a subset of users (plus folders of users), user profiles, user groups, subset of domains, and subset of team drives. If you select All Users, User Profiles, User Groups, All Team Drives, or Subset of Domains (Google Drive app only), additional options are available to exclude users, user profiles, or team drives.
The Exclude Sites,Exclude Users, Exclude User Profiles, and Exclude Team Drives options are available for All Users, User Profiles, User Groups, All Team Drives, and Subset of Domains. The Exclude options excludes users’ files or files in user profiles from triggering a policy if the files are shared between the users in the exclusion list.
Note
It is important to note that the site(s) added to the exclusion list will be included for policy processing within a retroactive scan. This is a known issue and a fix is on the way soon.
Important
The exclude users feature checks the sharing attributes only. For example, if user x has shared a file with user y and z, then all three users need to be part of the exclude users list in order for the policy condition to trigger and skip processing the file any further for these three users. If you add user x only to the exclude users lists, then the exclude user condition for policy would not trigger. So it is imperative to add the owner and shared parties in the exclude users list.
The Subset of Domains, All Teams, and Subset of Team Drives options are applicable for Google Drive policy only. The Team Drive folders are populated after the Google Drive instance is created. The list of sub domains are available in the API Data Protection dashboard page of the UI.
For files owned by email aliases such as "IT Support", "HR Group" that do not follow the valid email address format, Netskope does not process such notifications from Google Drive API. As a result, Netskope does not trigger a violation nor display the same in the Skope IT page.
All Users, Subset of Users, User Profiles, User Groups, and Subset of Domains scan content in Google Drive's 'My Drive' folders. All Team Drives and Subset of Team Drives scan content in Google Drive's 'Team Drive' or 'Shared Drive' folders.
Note
Though the UI displays the Exclude User option on the API Data Protection policy wizard for GitHub, it is not supported.
User profiles must be added before they are listed here. To download a CSV file that contains your user profiles, go to Policies > Profiles > User, and then click New User Profile. Complete the steps in the Create User Profile wizard, and then select a user profile.
Note
To use the user groups option, you first need to install the Netskope Adapters Utility Tool. For more information, refer to Netskope Adapters.
For Salesforce, you see user names instead of email addresses when you select Subset of Users. You also have the option to include Structured and/or Unstructured data scans.
For Microsoft Office 365 SharePoint Sites, you can search for sites or a subset of sites instead of users.
For GitHub, you can search for any user, outside collaborators and user regions.
When finished, click Next.
Content
This section of the API Data Protection Policy page specifies files, objects, and messages that trigger a policy violation.
For AWS, select All File Types or Specific File Types to scan.
For Azure, select All File Types or Specific File Types to scan.
For Box, you can select one of the following options:
All Sharing Options: Scans all sharing options like private, public, shared internally, and shared externally.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like:
Private: A file not shared with anyone.
Public: A file that is shared or open to the public.
Shared internally: A file shared specifically with users within the same sub-domain of the organization. To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal or external collaborators that need to be detected for a policy violation to occur.
Note
The Shared Internally option will not trigger a policy if the file or folder has a public sharing link.
Shared externally: A file shared specifically with users outside the organization. You can select All External Domains, specific external domains, or exclude a specific domain by selecting the All External Domains Except option. If you select the All External Domains Except option, choose the domain to be excluded from a policy trigger. You can create a new domain by selecting the Create New option. To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal or external collaborators that need to be detected for a policy violation to occur.
Note
The Shared Externally option will not trigger a policy if the file or folder has a public sharing link.
All File Types or Specific File Types to scan.
For Cisco Webex Teams, you can select one of the following options:
All Sharing Options: Scans all sharing options like private, shared internally, and shared externally.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like Private, Shared Internally, or Shared Externally.
For Shared Externally, you can select:
All Organizations
Internal Organization
External Organization
All External Domains Except..
Note
You can specify external domains to be excluded from exposure determination and policy enforcement.
For Dropbox, you can select one of the following options:
All Sharing Options: Scans all sharing options like private, public, shared internally, and shared externally.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like:
Private: A file not shared with anyone.
Public: A file that is shared or open to the public.
Shared internally: A file shared specifically with users within the same sub-domain of the organization. To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal or external collaborators that need to be detected for a policy violation to occur.
Note
The Shared Internally option will not trigger a policy if the file or folder has a public sharing link.
Shared externally: A file shared specifically with users outside the organization. You can select All External Domains, specific external domains, or exclude a specific domain by selecting the All External Domains Except option. If you select the All External Domains Except option, choose the domain to be excluded from a policy trigger. You can create a new domain by selecting the Create New option. To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal or external collaborators that need to be detected for a policy violation to occur.
Note
The Shared Externally option will not trigger a policy if the file or folder has a public sharing link.
All File Types or Specific File Types to scan.
For Workplace by Facebook, you can select one of the following options:
All Sharing Options: Scans internally and externally shared posts, comments, replies, chat messages, and attachments.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, internal and/or external.
Internal: Scans posts, comments, replies, chat messages, and attachments shared within the workplace organization.
Note
The Internal sharing option is not available for multi-company groups.
External: Scans posts, comments, replies, chat messages, and attachments shared outside the workplace organization like a multi-company group. For external sharing type, you can select all or specific external domains if they have been configured.
All File Types or Specific File Types to scan.
For Google Drive, you can select one of the following options:
FILES SHARING OPTIONS TO SCAN
All Sharing Options: Scans all sharing options like private, public, shared internally, shared externally, and enterprise shared.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like:
Private: A file not shared with anyone.
Note
This option is not available for Google Team Drive.
Public: A file that is shared or open to the public.
For public, you can select:
Public - Indexed and Unlisted: Any file that is shared publicly be it indexed or unlisted.
Public - Indexed Only: Any file that is shared publicly and searchable on Google search.
Public - Unlisted Only: Any file that is has a public sharing link but not listed on Google search.
Note
In Google Drive, files that are publicly shared may not be opened if the Google administrator has set the sharing setting to off in the Google admin console. This setting is located under Apps > Google Workspace > Drives and Docs > Sharing Settings > Sharing options > Sharing outside of <organization>. This discrepancy occurs because the Google API tags the file exposure as public, however the file has access restrictions due to the Sharing outside of <organization> option set to off.
Shared internally: A file shared specifically with users within the same sub-domain of the organization. To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal or external collaborators that need to be detected for a policy violation to occur.
Note
This option is not available for Google Team Drive.
Note
The Shared Internally option will not trigger a policy if the file or folder has a public sharing link.
Shared externally: A file shared specifically with users outside the organization. You can select All External Domains, specific external domains, or exclude a specific domain by selecting the All External Domains Except option. If you select the All External Domains Except option, choose the domain to be excluded from a policy trigger. You can create a new domain by selecting the Create New option. To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal or external collaborators that need to be detected for a policy violation to occur.
Note
The Shared Externally option will not trigger a policy if the file or folder has a public sharing link.
Enterprise Shared: Any file that is shared within the same organization but belongs to different sub-domain(s).
Anyone at Enterprise with the Link: Any file that is shared with any user within an organization but belonging to a different sub-domain(s) of an enterprise.
FILE TYPES TO SCAN
All File Types or Specific File Types to scan.
For Microsoft Office 365 OneDrive for BusinessSharePoint Sites, you can select one of the following options:
FILES SHARING OPTIONS TO SCAN
All Sharing Options: Scans all sharing options like private, public, shared externally, shared internally, cross-geo, enterprise shared, and shared with group(s).
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like:
Private: A file not shared with anyone.
Public: A file that is shared or open to the public.
Shared internally: A file shared specifically with users within the same sub-domain of the organization.
Note
If you share a file with an internal user who is in a different geo location, the file will be classified as 'Cross-geo' instead of 'Internal'.
Note
The Shared Internally option will not trigger a policy if the file or folder has a public sharing link.
Shared externally: A file shared specifically with users outside the organization. You can select All External Domains, specific external domains, or exclude a specific domain by selecting the All External Domains Except option. If you select the All External Domains Except option, choose the domain to be excluded from a policy trigger. You can create a new domain by selecting the Create New option.
Note
The Shared Externally option will not trigger a policy if the file or folder has a public sharing link.
Cross-geo: A file shared between geo locations in an Office 365 multi-geo environment.
Note
The cross-geo sharing exposure is available for centralized compliance administration with one instance for all geo-locations, and decentralized compliance administration with one instance per geo-location.
If you do not see the cross-geo file sharing option, ensure that the multi-geo capability is enabled on your Microsoft Office 365 account.
Enterprise Shared: A file shared with Office 365 preset groups. They are Everyone and/or Everyone except external users. In case of everyone, the file is shared within the Office 365 enterprise and external users. The file sharing exposure will be external. In case of everyone except external users, the file is shared within the Office 365 enterprise only. The file sharing exposure will be enterprise.
Shared with Group(s): A file shared directly with a specific named group. A shared group can be a combination of internal and external users. This list is fetched from your Microsoft Office 365 Admin Center's Groups > Active Groups. Only Microsoft 365, mail-enabled security, and security group types are supported.
Note
If you share a file with individual users in the selected group, API Data Protection will not count it as a match.
To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal, cross-geo, or external collaborators that need to be detected for a policy violation to occur. If you share a file with a Microsoft 365 group, API Data Protection can expand the group, identify the number of users and apply the threshold limit. However, there are a few important points to note:
API Data Protection does not support expansion of a distribution group.
API Data Protection does not support the expansion of a sub-group. If a Microsoft 365 group contains a sub-group (group within a group), API Data Protection does not expand the sub-group. The sub-group is considered as a single internal or external user.
Owner of a group does not get access to the files shared to the group, and hence API Data Protection does not count an owner as a member.
If a file is shared with two groups and user 'x' belongs to both the groups, API Data Protection counts this user only once.
Cross-geo users in any group will be treated as internal users. If a Microsoft 365 group contains a cross-geo user (user in another satellite location), API Data Protection treats such a user as an internal user during group expansion.
FILE TYPES TO SCAN
All File Types or Specific File Types to scan.
Microsoft Office 365 does not trigger events notification for sharing link activities. Netskope retrieves these via a polling mechanism after subsequent events. This may cause delays in processing shared links in OneDriveSharePoint.
For Salesforce, you can select one of the following options:
All Sharing Options: Scans all sharing options like private, public, and shared internally.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like Private, Public, and Shared Internally.
To set thresholds for when content sharing triggers a policy violation, select Advanced Options and enter the number of internal collaborators that need to be detected for a policy violation to occur.
All File Types or Specific File Types to scan.
For ServiceNow, click SELECT OBJECTS to select the ServiceNow tables to scan. Then, select the data type; Fields and/or Attachment. The following table lists the DLP supported fields:
ServiceNow Table | DLP Supported Fields |
|---|---|
Best Configuration Item | All fields* for which Netskope receives an API response from ServiceNow. |
Catalog Task | |
Change Phase | |
Change Request | |
Change Task | |
Feature Task | |
Group Approval | |
IMAC (Install Move And Change) | |
Incident | |
Incident Task | |
KB Submission | |
Knowledge | |
Problem | |
Problem Task | |
Release Phase | |
Request | |
Request Item | |
Task | |
Ticket | |
<custom table(s) created by the user> |
*It is observed that Netskope does not receive an API response from ServiceNow for Work notes and Additional comments fields. Due to this limitation, Netskope cannot perform DLP scan on these two fields.
Note
Netskope can perform DLP scan on files attached to the ServiceNow default and custom tables listed above.
For Slack, you can select one of the following options:
All Sharing Options: Scans all sharing options like private, public (files only), shared internally, and shared externally.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like Private, Public (files only), Shared Internally, or Shared Externally (All External Domains).
Under Content Type, select Messages and/or Files. If you select the Files option, you can select All File Types or Specific File Types to scan.
For Slack for Enterprise, you can select one of the following options:
All Sharing Options: Scans all sharing options like private, public (files only), shared internally, and shared externally.
Specific Sharing Options: With specific sharing options, you can choose all or specific sharing types, like Private, Public (files only), Shared Internally, or Shared Externally (All External Domains).
Under Content Type, select Messages and/or Files. If you select the Files option, you can select All File Types or Specific File Types to scan.
Support Folder-based Policies for Egnyte
In Egnyte, shared/team folders can be created by an administrator only. An administrator can add collaborators to folders. Folders are separated in two categories:
Team folder: Can be created by an administrator only.
Personal folder: Can be created by a user. This folder is the private folder of a user.
With this feature, administrators can create policies to handle either team, personal folder, or both.
Note
In API Data Protection, shared folder (in Egnyte) is termed as team folder.
Following are the use cases for Egnyte:
A policy can be applied to all users, all folders, or select team or all personal folders.
A policy can be applied to a subset of users and all team folders or subset of folders. When you choose subset of folders, team folders and personal folders are shown separately. List of team folders have all the team folders irrespective of users selected; for personal folders, only the selected users' folders are shown.
A policy can be applied based on a matching folder name. You can enter a matching string. If the string matches with the folder name, the policy is triggered. For example, if a user has applied a policy on the folder name called Case, the policy will be triggered for all folders in the Egnyte app with the name Case. The policy will not be triggered for a folder name Case Sensitive.
Prior to release 48, folder selection was part of Users > Subset of Users policy workflow. In release 48, folder selection is separated out from users. Folders to Scan option is part of Content policy workflow. This option has the following choices:
All Folders: With this option, all folders irrespective of team or personal are scanned.
Select Folders: With this option, additional options are available; Team Folders and Personal Folders. You can select team, personal folders, or both for scanning.
Note
If you select All Users, User Profiles, or User Groups from the Users policy workflow, you can only select all personal folders. You cannot select subset of personal folders.
Match Folder Name In: With this option, you can enter a string matching the Egnyte app folder name. The string is matched with the folder name in either all folders, all team folders, or all personal folders. Based on a folder name match, the policy is triggered.
When finished, click Next, and then go to the topic in this guide that matches the section you're configuring on the New API Data Protection Policy page.
DLP
This section of the API Data Protection Policy page specifies the type of DLP profile that triggers a policy violation.
Note
API Data Protection now supports scanning files up to 128 MB for DLP and threat protection. The default file size is 32 MB. Contact Netskope support or your sales representative to configure a larger file size for your tenant. A few points to consider before enabling this enhancement:
With larger files, there may be an increased end to end latency for policy processing.
Plan for a increase in forensic/quarantine/legal hold data store size.
The encrypt policy action does not currently support larger than 32MB files. The action will therefore not work on files larger than 32MB.
To use a data loss prevention (DLP) profile, select DLP and click Select Profile. Search for a DLP profile or choose one from the list, which includes both predefined and custom profiles. After selecting a DLP profile, click Save.
When finished, click Next.
Note
Enabling DLP will evaluate files only. All structured data will be ignored for this policy. To evaluate all structured data, disable DLP.
Note
Microsoft does not provide any webhook notification for files uploaded through the files and wiki tab of Microsoft Teams. Due to this limitation, Netskope does not support DLP scanning for such file uploads. However, Netskope detects files sent as an attachment from a channel's chat window.
Note
Netskope does not scan emails in deleted/trash folder. Netskope will continue to scan emails in sent folder.
Action
This section of the API Data Protection policy page specifies the action to be taken when a policy violation occurs. The actions vary depending on the app chosen. For some apps, the only action is alert. Similarly, restrict access options vary depending on the app chosen.
Select the action you want to take from the drop-down list, like Alert, Block, Change Ownership, Restrict Access, Encrypt, Delete, Quarantine, Legal Hold, Restrict Sharing to View, Apply Azure RMS Template, Data Classification, Disable Print and Download, or IRM Protect.
Note
If you use the encrypt policy action, ensure that you have a Netskope real-time deployment i.e., a reverse or forward proxy. The Netskope real-time deployment is required to decrypt the file.
The Disable Print and Download action applies to Google users who have comment and view file permissions. Users with edit permissions on a file can continue to print and download the file.
Alert, Delete, Legal Hold, and Quarantine actions are available for Slack for Enterprise.
When an external user upload a file on a Slack Connect channel, Netskope cannot perform delete (write) action on the file. This is because the file belongs to another organization.
Once Netskope performs a delete action on a file, the Netskope tenant administrator may still have access to the deleted file from the Incidents > DLP page. This can happen if the Slack enterprise account has a retention policy to preserve the file. Though Netskope deletes the file from the Slack channel, the file may still be available to downloaded from the Netskope tenant. Please check your data retention policy with Slack support.
The alert action is available for ServiceNow.
In case of Workplace by Facebook, Delete action applies to posts/comments only.
The Data Classification option is disabled by default. To enable this option, contact Netskope Support. To know more about this option, refer to the Security Classification on Box section below.
For a list of supported actions per cloud app, refer to API Data Protection Policy Actions per Cloud App.
For some actions, like Restrict Access, you can select additional options from the adjacent drop-down list. For example, if you selected Specific Sharing Options and Shared Externally in the Content section, then the option to allowlist or blocklistan External Domain appears in the drop-down list.
Note
For folders with 1000+ collaborators, Box does not send the list of collaborators to Netskope. Due to this, Netskope's API Data Protection rounds off the number of collaborators to zero. API Data Protection policy such as Restrict Access will not work for such folders. This is a limitation in the Box app.
For Microsoft Office 365 OneDrive for Business and SharePoint Sites apps, you can select the Restrict Access option from the adjacent drop-down list. The Restrict Access Levels are Owner, Internal Users, Remove Public Links, Remove Individual Users, and Remove Organization Wide Link.
Owner: Restrict file sharing access to the owner only.
Internal Users: Restrict file sharing access to internal users only. This action removes any external user who has access to the file and removes any public link on the file.
Remove Public Links: Remove public links from files/folder.
Remove Individual Users: Remove individual internal and external users from accessing files/folders. This option does not remove AD group email addresses like distribution lists.
Remove Organization Wide Link: Remove links from files/folders that are shared within the organization.
Note
In SharePoint, the Restrict Access to Owner action retains access to site owner(s) and site member(s). All other visitors and shared users/groups access are revoked.
Select the action as IRM Protect from the drop-down list and select Veraor MIP as the IRM vendor. If you select Microsoft Information Protection (MIP), you have to select an MIP Profile.
Note
Before you create an IRM policy, you should create a Vera or MIP instance. For more information, see IRM Integration with Vera or IRM Integration with Microsoft Information Protect.
If you do not see an MIP profile in the drop-down list, log in to your Microsoft 365 admin center, go to the compliance section. Under Information protection, ensure that the MIP label is published to 'all' groups or a group that contains the global administrator account.
Microsoft does not allow to create a policy with Remove Encryption action on MIP-encrypted files. The file types that are not allowed are Office 365 file extensions. Due to this limitation, in the Netskope UI, when you set up a policy to apply an MIP label, the policy will not trigger on such Office 365 file types. This is because Netskope cannot replace a label from an MIP-encrypted file with any other label. This issue is not observed in Adobe PDF and .jpeg, .png, and .tiff image file types.
Select the available action and click Next.
For Quarantine, select an existing quarantine profile from the list, or create a new one. Click New Quarantine Profile from the drop-down list to create a new quarantine profile for this policy. A DLP profile must be selected in section to use Quarantine. In Create Quarantine Profile wizard, complete the Settings, Customize, and Set Profile pages. When finished, click Create Quarantine Profile. When finished, click Next.
Important
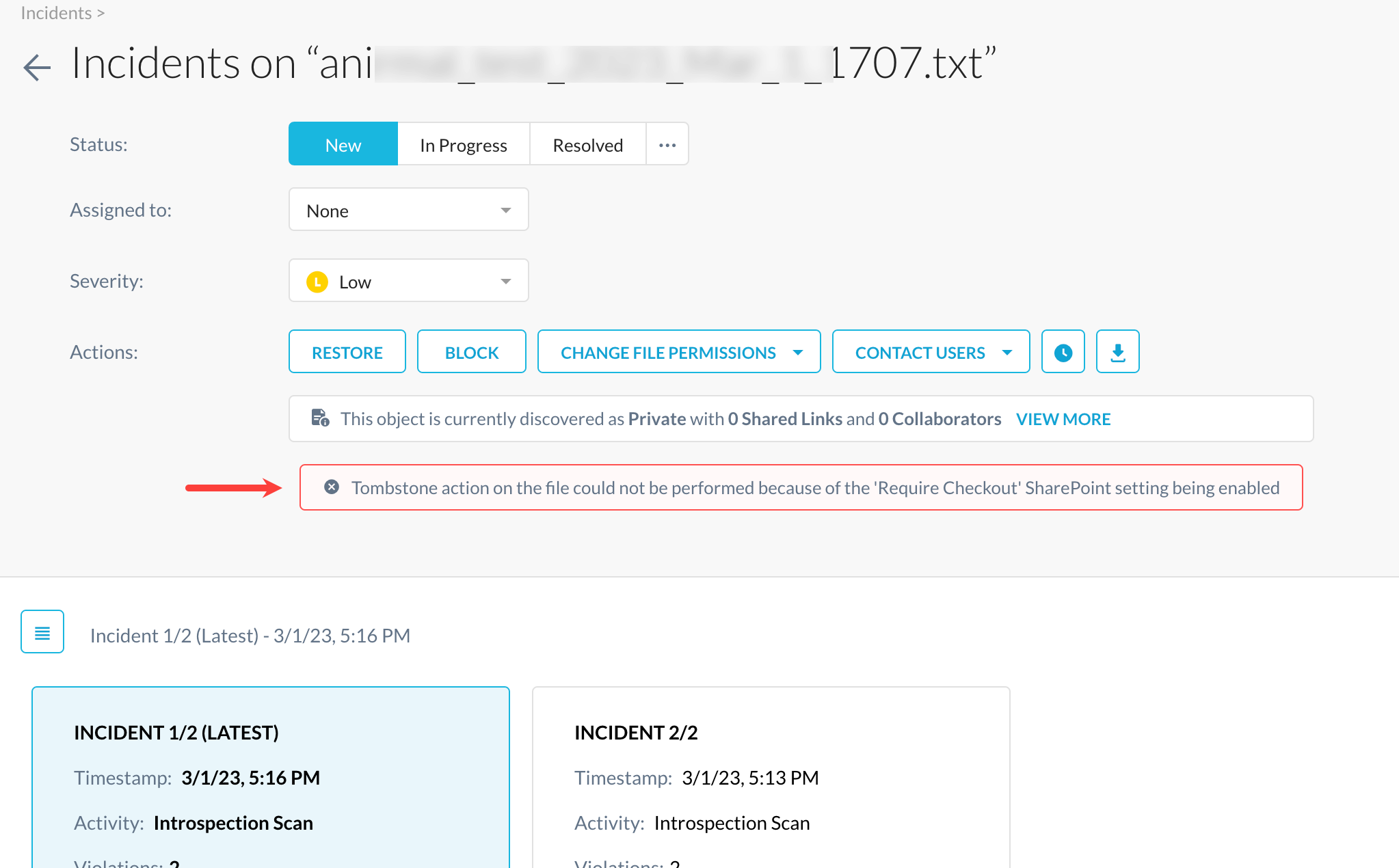
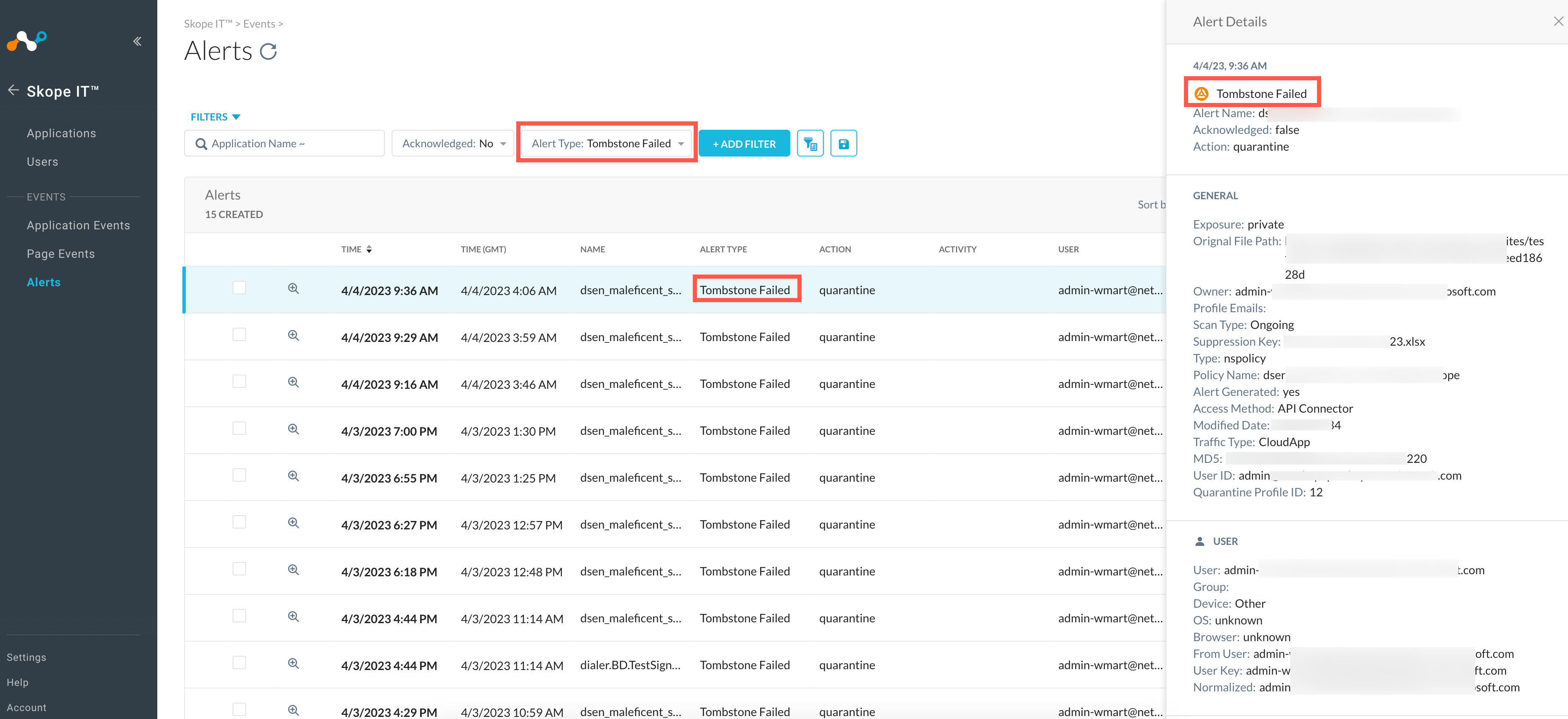
Latest update on Microsoft Office 365 SharePoint's Require check out of files - If this setting is enabled on a SharePoint site, Netskope API Data Protection can quarantine the file but fails to overwrite the original file with a tombstone file. To gracefully handle this kind of a scenario, API Data Protection now provides administrators to identify such files within Incidents and Alerts UI pages. Following two changes are added in the Netskope tenant UI:
Under Incidents > DLP, when you click an incident, the UI displays a new tombstone failure message.
Under Skope IT > EVENTS > Alerts, a new alert type Tombstone Failed is introduced for quarantine action.
Note
Encrypted files sent to the quarantine folder are limited to 20 MB in size.
When an external user upload a file on a Slack Connect channel, Netskope cannot perform quarantine action on the file. This is because the file belongs to another organization.
To trigger an email notification, you will need to set up a couple of things:
Under Notification, select Send to custodian and to users in profile.
Under Policies > PROFILES > Quarantine, create a new profile or edit an existing profile. Under NOTIFICATION EMAILS, the email notification will be sent to this email address.
For Legal Hold, choose an existing profile from the drop-down list or click Create New. The CREATE LEGAL HOLD PROFILE wizard opens. For more information, refer to the Legal Hold section of Profiles. When files are placed in legal hold, emails are sent to the custodian and the users who created the files. When finished, click Next.
Security Classification on Box
Security classification on Box is a feature that enables customers to classify files based on their confidentiality and enforce security policies associated with that confidentiality level. This helps organizations protect sensitive information and encourage smarter user behavior when handling that content.
API Data Protection helps in automating the content classification for organizations. The feature leverages Netskope's DLP engine to identify sensitive data and classify the user's content automatically. Netskope introduces a new policy action called Data Classification. Like any other policy action, a user can set up the data classification, to classify sensitive files. There are three file classification options: confidential, internal only, and unrestricted. You can drill further down and set priority for the file classification. There are three priority options: P0, P1, and P2. Priorities can be set in order of importance with P0 being the highest priority followed by P1 and P2. This option is disabled by default as it requires API Data Protection to make additional API calls to Box for each file classification. To enable this feature, there are two steps:
Make sure you enable the file classification feature on your Box account. Refer to this article to enable this feature on Box: https://community.box.com/t5/Using-Box-Governance-Features/Using-Security-Classifications-with-Box-Governance/ta-p/21276.
Once activated on your Box account, contact Netskope Support to enable on your Netskope tenant.
File Collaboration on Box
To improve collaboration, Box supports inviting collaborators to edit individual files. Previously, users needed to be invited to the file's parent folder to edit a single file. There is a new invite/add collaborators option at the file level. Once invited, the collaborator has editor or viewer permission. All enterprise and folder-level settings related to collaboration are inherited to file-level collaboration.
If a file has an internal collaborator, Box tags the file as internally shared. Similarly, if a file has external collaborators i.e., a user outside the Box enterprise, Box tags the file as externally shared. Netskope calculates the file exposure based on the file and parent-level collaboration.
Impact on Restrict Access Policy Action
If the administrator applies the restrict access policy action, Netskope removes the folder and file-level collaborators.
Impact on Restrict Sharing to View Policy Action
If the administrator applies the restrict sharing to view policy action, Netskope restricts the access level of a collaborator of the file and the collaborator inherited from the parent folder to view only.
Restrict Access to Domain and User Profiles
Up until release 47, allowlist and blocklist domain profiles under Restrict Access were linked to the domain profiles under Content > File Sharing Options to Scan policy workflow. These two are independent of each other. An administrator access based on domain profiles. In addition, administrators can now allow (allowlist) or deny (blocklist) certain users (user profile) from accessing files and folders.
Before restricting access to a domain or user profile, you need to create the profile from the Policies > Profiles page. Once the profile is created, they get listed as part of the Restrict Access action. Restrict Access is available as part of the Action policy workflow. You must select Restrict to select Allowlist Domains, Blocklist Domains, Allowlist User , or Blocklist User from the Restrict Access Level drop-down list. Based on the choice, the Domain Profile or User Profile dropdown list is displayed.
Note
In Contents > File Sharing Options to Scan, if you select Specific Sharing Options > Private, the Restrict Access option is not available under Actions.
Azure RMS Template
Go to Policies > API Data Protection and under the SaaS tab, click New Policy.
Configure the policy workflow till DLP.
In the Action section, select Apply Azure RMS Template from the Action drop-down list and RMS template from the Azure RMS Template drop-down list.
Note
In Azure, if a template is created with scope, RMS super user should be part of the scope, if not, the RMS template will not populate under the Azure RMS Template drop-down list.
Click Next and then go to the topic in this guide that matches the section you're configuring on the API Data Protection policy page.
Egnyte Policy Action
Admin and power users can use a link to share one or more files users. When you share a file link in Egnyte, the recipient receives containing the URL of the file. Clicking the URL downloads the file. need not be an Egnyte user. If a user belongs to a blocklist user profile, Netskope removes the shared link for all users irrespective user/domain profile. A couple of used cases to be noted:
If a user has shared a file with a.com, followed by b.com domain users at a time difference, restrict access to blocklista.com domain denies access to a.com domain users only. B.com domain users can continue to access the file.
If a user has shared a file with a.com and b.com domain users at the same time using a single URL, restrict access to blocklista.com domain denies access to both a.com and b.com domain users. Netskope changes the exposure of the file to private.
Google Drive Connected Apps/Plugins
If you select Google Drive application to scan Connected Apps/Plugins, only two actions are available: Alert and Revoke.
Alert: If the policy is triggered, based on the policy definition, an alert will be generated.
Revoke: If the policy is triggered, based on the policy definition, the selected Google app/plugin will be revoked.
Note
Apps that are revoked can be reinstalled by the user. However, if the policy is active, the apps will be revoked again.
If the policy to revoke an app applies to a user A, user B can continue to install the app.
After revoking, the app is visible in the Google Drive account. But on running the app, the user has to grant access again.
SharePoint Restrict Access to Owner Behavior
In SharePoint, a site owner is the owner of the files and folders of the site. This is the default behavior. In the following scenarios the owner of the site becomes the owner of the uploaded file by default:
The site is owned by an administrator and other groups.
The site is shared with select users.
A folder or file is uploaded on the site by one of the site member users.
When there is an access restriction to an owner of such a file, users are restricted to access from the shared list apart from the author of the file and the owner(s) of the site.
Notification
This section of the API Data Protection Policy page specifies who and when to notify users about a policy violation.
With Slack for Enterprise, you can send notifications to an owner or user through direct messaging using a Netskope bot.
Select None if you do not wish to send any notification.
Select the Notify once every option to specify how often to notify recipients and who to notify. Click on the adjacent toggle to specify a interval, or choose to Notify after each event.
To send multiple notifications, select the recipients to notify, and then choose the email template you want to use and enter the email address of the recipient(s). To create custom email templates for each recipient, enable the checkbox for the recipient types, and then select Create New from the drop-down list. Enter the needed info in the Create Email Notification Template window, and then select components to include in the email. When finished, click Save.
Note
The Create New email template is not available for GitHub.
Optionally, you can enter your email address so the recipients know who set up this policy.
For Notify once every and Notify after each event, there are more options:
Send to custodian and to users in profile.
Owner: Sends email notification to the creator of the message or file.
Admin: Sends email notification to the admin email that was specified as part of the instance setup.
Collaborators: Sends email notification to all users that are part of the channel to which the message/file was posted.
Select Users: Sends email notification to selected users who's email addresses are added in the edit box.
Note
For Slack for Enterprise, when you select Notify after each event, options for sending a notification through the app appear under a Notify by section.
Note
For Cisco Webex Teams, when you select Notify after each event, options for sending a notification through the app appear under a Notify by section.
Note
With GitHub, if an administrator needs to be notified by email, you have to explicitly use the Select Users - Email Template option and specify the email address.
When finished, click Next.
Set Policy
This section of the API Data Protection Policy page specifies the name of the policy and allows you to add a description if desired.
Enter the name of the policy.
Optionally, you can enter a short description of the policy.
When finished, click Save, followed by Apply Changes. The policy that you just created will scan the files and folders specified based on your selections, and the action chosen occurs when there is a policy violation.