UEBA for Amazon Web Services
Note
This is a beta feature. Contact your Netskope sales representative to enable it on your tenant.
Netskope Public Cloud Security enables you to configure your Amazon Web Services (AWS) accounts with CloudTrail logs for behavior analytics. The following workflow diagram provides a visual representation of the steps required to configure your AWS accounts for UEBA.
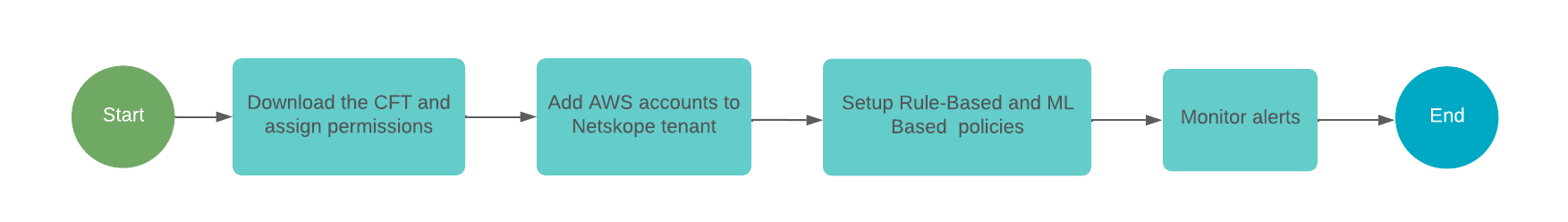
The setup uses a Cloud Formation Template (CFT), aws-instance-setup.yml that is customized with permissions required for Netskope to create an IAM cross-account role. The role provides Netskope access to create a CloudTrail stack called NetskopeCloudTrailStack in one of the regions of the AWS account added to the Netskope tenant. This stack subscribes the AWS account to Netskope's notification receiver to receive CloudTrail logs generated from management and data events in your AWS accounts.
To learn more, see "What happens in the process?" section in Step 2/2: Configure AWS Permissions for UEBA.
Netskope Public Cloud Security enables you to simultaneously configure multiple AWS accounts in a single region. To learn more: Enabling UEBA for AWS CloudTrail .