Symantec Endpoint Protection
Symantec Endpoint Protection (SEP) is a client-server solution that ensures the protection of your endpoint devices from malicious attacks and threats.
This document contains the best practices required in Symantec Endpoint Protection and Netskope Client to ensure smooth interoperability.
Environment
This document was created using the following components:
Symantec Client Version: 14.0.MP1 build 2332 (14.0.2332.0100)
Netskope Client version: 92.1.0.943
OS: Windows 2016 Server Datacenter
Certain configurations in Symantec Endpoint Protection and Netskope tenant web UI can ensure that the processes or traffic from either of the applications are not blocked and directed to the Netskope Cloud.
Configurations In Symantec Endpoint Protection Manager
The Symantec Endpoint Protection includes a default firewall policy that contains a default set of rules. The firewall rules are the baseline that determines whether to allow or block the incoming and outgoing packets through the firewall.
To allow the Netskope Client to operate seamlessly, add a new firewall rule while creating a firewall policy in Symantec Endpoint Protection Manager and add the following executable files:
stAgentSvc.exe
StAgentUI.exe
nsdiag.exe
To add a new firewall rule:
Login to Symantec Endpoint Protection Manager.
Go to Policies > Firewall .
Open a Firewall Policy and click Rules depending on the Windows or mac settings.
On the Rules tab, click Add Rule.
On the Add Firewall Rule Wizard window, enter the rule name.
Click Next after you complete each action.
From the Select the Action for the Rule section, select Allow Connections.
From the Select the Rule Applications section, select Only the applications listed below and enter the following .exe files:
stAgentSvc.exe
StAgentUI.exe
nsdiag.exe
Fill out the options on each dialog box, and then select Submit.
You can view the newly created rule in Firewall Policy > Rules > Firewall Rules. To confirm that Netskope Client is not blocked, go to the endpoint machine and perform Update the Policy from the SEP manager.
Important
Select the checkbox in the Enabled column for the rule(s) on the Rules page.
Configurations In Netskope Client
Add exceptions (Certificate Pinned Application exception type) on the Netskope tenant WebUI to allow the SEP traffic to bypass Netskope and reach its destination. You must add exceptions to the Netskope Steering Configuration. To learn more, view Adding Exceptions.
To add Symantec Endpoint Protection as a Certificate Pinned Application on the Netskope UI:
Go to Settings > Security Cloud Platform > Steering Configuration and select a configuration.
On the configuration page, click EXCEPTIONS > NEW EXCEPTION > Certificate Pinned Applications.
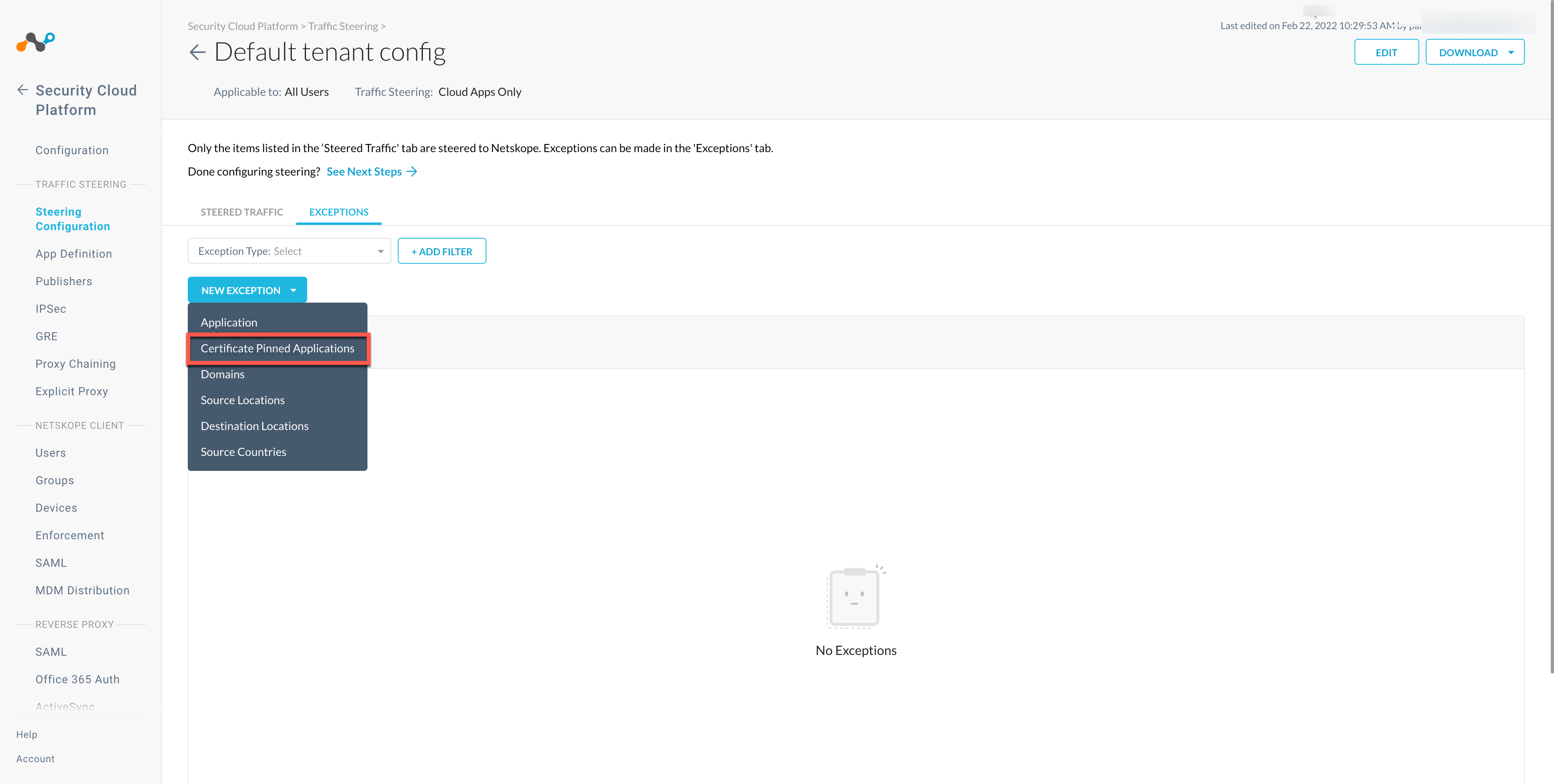
In the New Exception window, do the following:
From Certificate Pinned App, select the application. To add a new certificate pinned application in the New Certificate Pinned Application window, do the following:
Application Name: Enter the name of the application.
Platform: Select the operating system where the application is managed.
Definition: Provide the processes and .exe(s) list that you want to bypass. To learn more about the .exe(s) excluded, view Exclusion List.
From Custom App Domains, add the URLs that you want to exclude. To learn more about the exclusions for the Symantec Endpoint Protection Manager, view Allow URLs.
From Actions, select Bypass for all operating systems that you want to allow directly to the destination.
Click ADD.
Netskope Client Functions
Refer to the list of validated use cases that you can use to verify Client operations.
Symantec Endpoint Protection Functions
To verify if Symantec Endpoint Protection functions smoothly:
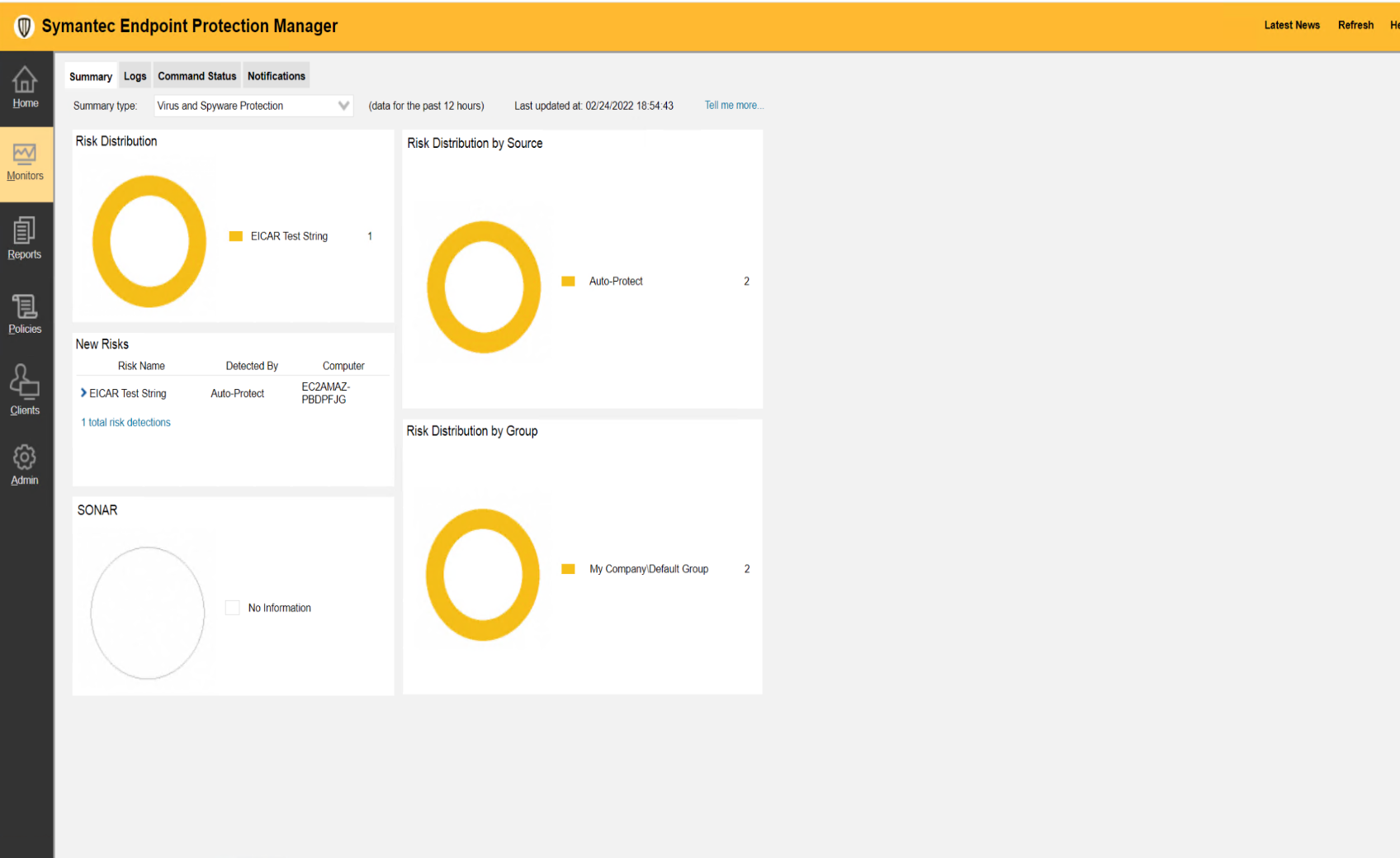
Ensure that an infected file is detected by Symantec Endpoint Protection (optional).
View the alert on the Symantec Endpoint Protection Manager console