Netskope Adapters
The Netskope Adapters enable running various features that can integrate with your Active Directory and other directory servers to collect user and user activity information. This helps you collect analytics and enforce policies. To download the Netskope Adapter file, login to your Netskope tenant, go to Settings > Tools > Directory Tools and click the Download Tools button.
The Netskope Adapters provide three features: Directory Importer, AD Connector, and DNS Connector:
Directory Importer: Directory Importer connects to a domain controller (DC) and periodically fetches user and group information from the DC, and posts that info to your tenant instance in the Netskope cloud. if you are using the Netskope Client and Secure Forwarder you can utilize user and group membership information to send client invites and set up cloud app policies.
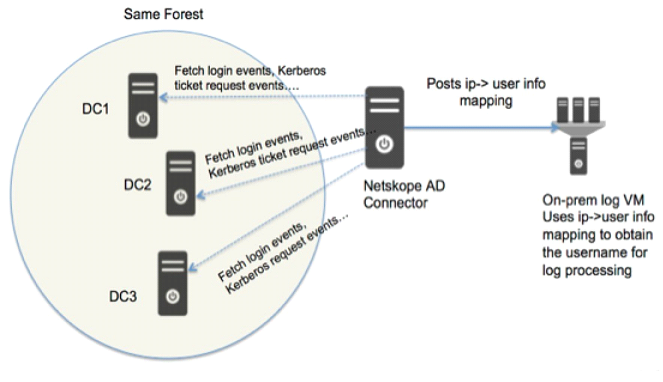
AD Connector: AD connector connects to the DC and periodically fetches user login events, extracts the User to IP mapping, and posts that info to Secure Forwarder. This provides user visibility for traffic going through Secure Forwarder.
DNS Connector: DNS Connector integrates with a DNS Server to populate the forwarding zones.
Depending on your need, the NSAdapters.msi file can install any or all of these three on a single machine. In addition, it installs a Configuration Utility UI that lets you configure the needed parameters to use different features.
Note
If you are using only the On-Premises Log Parser (OPLP) Virtual Appliance (VA), the only feature required to get user visibility is AD Connector.
Netskope Adapters provide the ability to integrate with your AD server to retrieve the IP to User mapping and use that information to provide user visibility for log processing.
Visibility into cloud app usage at a user level, not just at an IP address level, helps you align application usage with business unit requirements.
Prerequisites
Using the Netskope Adapters have these requirements:
The
NSAdapters.msifile from Setting > Tools > Directory Tools in the tenant UI.A 64-bit Windows machine running an OS noted in Supported Platforms.
The machine running Netskope Adapters needs to be part of the domain. It doesn’t need to run on the domain controller.
Ensure that Microsoft .NET Framework 4.6 or later (Supports TLS 1.2) is installed on this server: https://www.microsoft.com/en-us/download/details.aspx?id=48130
Create a new account (with Log on as a service rights for local machine) in the domain to be used for Netskope Adapters. It is recommended to create a dedicated service account / user (with admin rights) in the AD domain to use for the Netskope Adapters.
You must have local admin privileges to install the Netskope Adapters. You can log in with your own username to perform the installation if you're the local admin on the system. Directory Importer requires local admin privileges as well. Refer to Permissions for Directory Importer below for more details.
The user for whom Netskope Adapters are installed must be a member of the domain.
All the services will be installed under the provide username that has Log on as a service rights for the local machine.
Permissions Required for Directory Importer
If Directory Importer is used to fetch users from a non-Microsoft LDAP server, the user account specified during the Directory Importer installation should be an account in the local machine with admin privileges. The user account specified in the Directory Attributes dialog box (under under Other Directory Services) should be part of the Domain.
Directory Importer requires these permissions:
Account Privileges:
Installation Privileges
Operational Privileges
Local admin privileges - Username specified during installation can be different from the currently logged on user. Administrator can be logged in with a different username and perform the installation. In this case, both logged-on user and user specified during installation requires local admin privileges.
Service Account (with read/write access) - For reading and writing into config directory (default: c:\program files\netskope directory) and log files.
Non-admin user account - For general operation / execution of Directory Importer. Directory Importer will run as expected. The user must be an authenticated account of the Domain.
Requires port 443 connectivity to
addon-<tenant hostname>.goskope.com.Note
For deployments with release 46 and above, use the above domain name. For deployment with release 45 and lower, use
addon.goskope.com. For international deployments, use ~.eu.goskope.comor ~.de.goskope.com.
To test if the Directory Importer can run with the current user privileges, enter the following command at the command prompt.
dsquery user domainroot -name * -u <username> -p <password>
If the user has privileges, the command will execute without an error. Following is an representational example of a successful output , but the actual content or output may vary depending on your environment.
C:\Users>dsquery user domainroot -name * -u username1 -p 123456789 "CN=Administrator,CN=Users,DC=exampledomain,DC=local" "CN=Guest,CN=Users,DC=exampledomain,DC=local" "CN=Guest2,CN=Users,DC=exampledomain,DC=local" "CN=username1,OU=UserInfoDistOU1,DC=exampledomain,DC=local" "CN=username2,OU=UserInfoDistOU1,DC=exampledomain,DC=local" "CN=username3,OU=UserInfoDistOU2,DC=exampledomain,DC=local" "CN=user.exampleorg1.test,OU=exampleorg,DC=exampledomain,DC=local" "CN=user.exampleorg2.test,OU=exampleorg,DC=exampledomain,DC=local" "CN=user.exampleorg3.test,OU=exampleorg,DC=exampledomain,DC=local"
Permissions Required for AD Connector
AD Connector requires these permissions:
User should have appropriate privilege to read the AD security event logs.
User must be added to the built-in AD group Event Log Readers. The path to add is Start > Administrative Tools > Active Directory Users and Computers > Users > User > Properties > Member Of.
Ensure specific Windows Firewall rules are enabled. On the AD server, go to Start > Administrative Tools > Windows Firewall with Advance Security.
For the Inbound rules, enable the rules for Remote Event Log Management for the following options:
Remote Event Log Management (NP-In)
Remote Service Management (RPC)
Remote Service Management (RPC-EPMAP).
Optional for additional security, you also have a provision to allow incoming connections from only the IP of the remote machine that is designated to gather the event logs. You can enter this setting in the Rule Properties > Scope field.
Permissions Required for DNS Connector
DNS Connector requires these permissions:
User should have appropriate privilege to update the DNS records
User must be added to the DNS admins group so it can automatically add/delete/modify the DNS forwarding zones.
In addition to this, DNS connector requires additional preconfiguration steps. Refer to DNS Connector for details.
Supported Platforms
The Netskope NSAdapters work on these platforms:
Windows 10 64-bit
Windows 7 64-bit
Supported under special consideration. For more information, refer to Windows 7 EOL .
Windows 2008 R2 64-bit
Windows 2012 64-bit
Windows 2012 R2
Windows 2016
Windows Server 2019
Windows Server 2022