Next Steps
Review the default Real-Time Protection policies in your Netskope tenant.
The default policies in your Netskope configuration will cover the following:
Block undesirable sites (such as adult content and P2P) globally for all users.
Warn and require justification for access to unknown/miscellaneous content and newly registered domains.
Block known and suspected malicious domains and phishing Ensure all uploads/downloads are checked for malware.
See more:
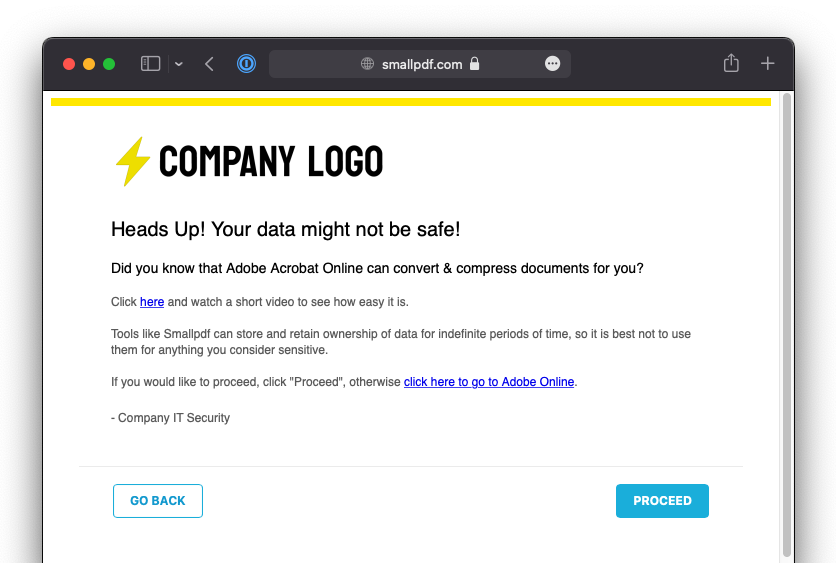
Create and Customize your User Notification Templates
The messages that appear to users when a block/coaching rule is hit can be customized under Policies > User Notification. Each policy can have a different template; allowing you to coach users on appropriate behaviors across a wide variety of scenarios.
 |
To learn more:
Establish Global Guardrails and Build Policies
Netskope recommends that you expand on the global block (included as a default policy) and add additional sites/categories that you may also want to block globally eg: Online Ads
You should also consider implementing a coaching policy with action "User Alert" that covers the applications and categories that you consider "non-business" related, but safe for employees to consume; eg: Streaming Media, and/or Gambling.
Access Control rules should take creation priority and you should start with the most simple rules first. Once you have baseline rules in place, slowly add rules of additional complexity; incorporating risk scores, instance awareness, and/or DLP rules.
To learn more:
Sanction your Business Applications
The Netskope Cloud Confidence Index™ (CCI) is a database of more than 54,000 cloud apps that Netskope has evaluated based on 48+ objective criteria adapted from Cloud Security Alliance Guidance. These criteria measure apps enterprise-readiness, taking into consideration an apps security, audit-ability, and business continuity.
Each app is assigned a score of 0-100, and based on that score, is placed into one of five Cloud Confidence Levels (CCL): Poor, Low, Medium, High, or Excellent. You can use the CCI score to make an app selection decision, as well as set policies based on level. For example, you can decide whether to let users share content in cloud storage apps rated Medium or below.
Access the CCI from the main panel of the Netskope Admin Console, lookup your key business applications (eg: Sharepoint, Teams, Slack, etc) and mark them as "sanctioned" (all apps are "unsanctioned" by default) - eg: Sharepoint, Teams, Dropbox, Zoom, Slack, etc. You can then leverage the "sanctioned" and "unsanctioned" tags in policy: For example, block upload to all high risk, unsanctioned, cloud storage applications.
To learn more:
Deploy to a Broader Subset of Users
Once your baseline policies are in place, you are ready to expand your rollout to additional users.
Deploy Netskope Publishers (NPA Customers Only)
If you are a Netskope Private Access (NPA) / ZTNA customer, you will need to deploy Netskope Publishers throughout your environment to facilitate access to your internal apps.
To learn more:
Establish IPsec/GRE Tunnels to Netskope to Secure Clientless Devices, Guest Wi-Fi, and Servers
The Netskope Client is only one of many methods to steer traffic to the Netskope Cloud.
Another common method used in conjunction with the Netskope Client is the establishment of IPsec or GRE tunnels from your internet egress points (including public cloud). This allows your security policies to be extended and applied to users and devices that can't run the Netskope Client: Guest Wi-Fi, Servers, and IoT/smart devices for example.
To learn more:
Deploy Netskope Cloud Exchange
Cloud Exchange (CE) is a platform (free for all Netskope customers) that facilitates the exchange of information between your various security and operations platforms; including threat intel, risk data, and logs.
To learn more:
Configure Administrator Single Sign-On
Currently, your Netskope Admin Console is authenticated using separately managed username and passwords. It is strongly recommended that you configure Single Sign-On for the Admin Console so that authentication is centrally controlled via your company's identity service.
To learn more: