Enabling Dynamic Steering
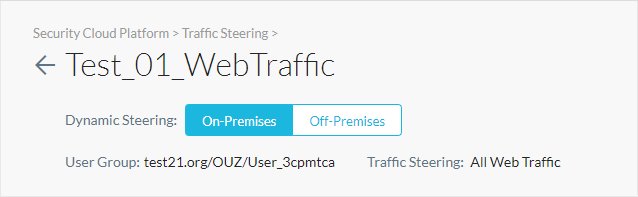
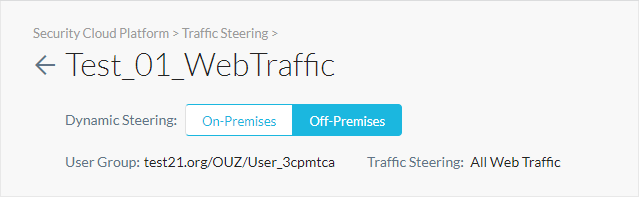
Dynamic steering enables location-based steering capabilities via on-premises or off-premises. Depending on the location, you can set up the steering configuration to steer or bypass configured traffic. When a managed device is detected to be on-premises, only cloud applications are steered and when the device is detected to be off-premises, all web traffic is steered. Dynamic steering also extends the capability to steer traffic from all or specific private applications.
For example, ACME Inc. uses a firewall in their on-prem network to manage web traffic, but they don't want to change this setup and use Netskope to steer cloud traffic. However, for off-prem users, they want to configure Netskope to steer both cloud and web traffic. In this situation, dynamic steering can detect user location and use appropriate steering modes.
Irrespective of the user location all exceptions types are supported. However, when using the Destination Location (with public IP address only) exception type, select the Treat like local IP address option. To learn more about exception types: Adding Exceptions.
About Dynamic Steering
The following are the supported steering modes when a managed device is on-premises or off-premises.
On-Premises Steering Modes
When the managed device is on-premises, you can set up the steering configuration to steer either web or cloud traffic:
Traffic Mode | Steering Exceptions |
|---|---|
Cloud (Default) | The Netskope cloud application exceptions are bypassed from the Netskope Cloud. If domain exceptions are part of a steered cloud application, they are bypassed by the Netskope cloud. If the domain exceptions aren't part of a steered cloud application, then the following behavior occurs:
|
Web | All exceptions are bypassed from the Netskope Cloud. Contact Netskope Support to enable this mode. |
Note
The steering bypasses are aggregated at the Netskope Proxy level, so if traffic is steered/sent to the Netskope Cloud when the Netskope Client is on-premises, the domain exceptions specified in off-premises steering configurations are allowed.
Off-Premises Steering Modes
When the managed device is off-premises, all web traffic is steered by the Netskope Client.
Traffic Mode | Steering Exceptions |
|---|---|
Web (Default) | All exceptions are bypassed locally by the Netskope Client. |
Netskope doesn't support Cloud mode for managed devices off-premises.
Note
The steering bypasses are aggregated at the Netskope Proxy level, so if traffic is steered/sent to the Netskope Cloud when the Netskope Client is off-premises, the domain exceptions specified in on-premises steering configurations are allowed.
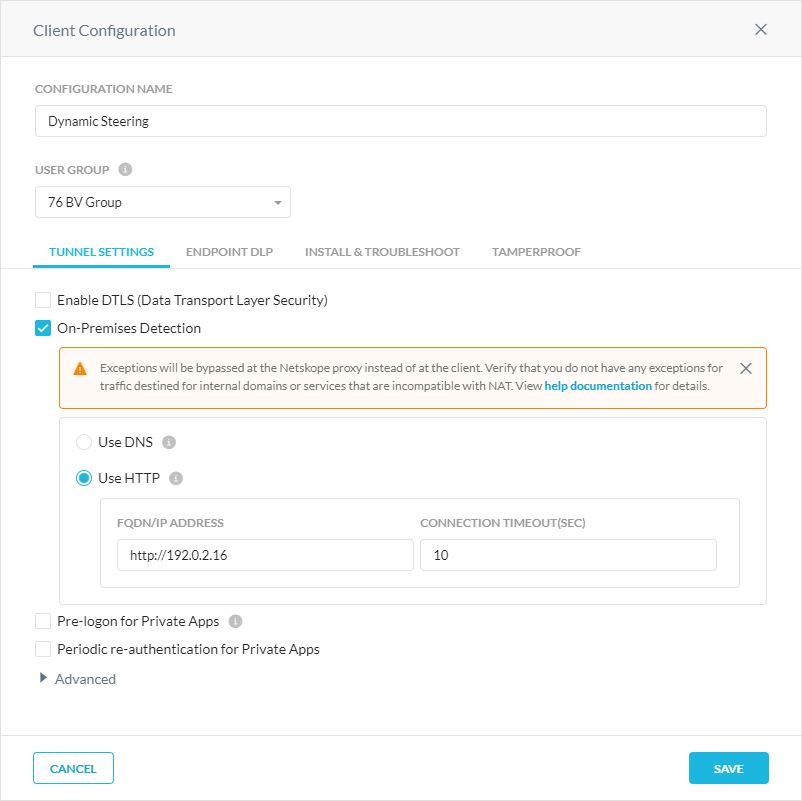
Enabling On-Premises Detection
Before enabling dynamic steering, you must enable on-premises detection for the Netskope Client. To learn more about on-prem detection: Tunnel Settings (Earlier Termed as Traffic Steering).
To enable on-premises detection:
Go to Settings > Security Cloud Platform > Devices.
Click the Netskope Client configuration you want to enable on-premises detection for.
In the Tunnel Settings tab, select On-Premises Detection, and choose the location detection method:
Use DNS: Enter the endpoint domain and IP address. If the FQDN entered resolves to the provided IP Address, the device is considered to be on-premises. Ensure this is a valid DNS record that is resolvable only within your network.
Use HTTP: Enter
http://and then the endpoint FQDN or IP address as well as a connection timeout value. The default is 10 seconds, and the maximum is 60. The HTTP server must return a200 OKresponse code to determine if the device is on-premises. When a proxy server is available for Netskope Client, HTTP requests go to the proxy server from Netskope Client. To use this method, you must have Netskope Client release version 72.0.0 or higher.
Note
Don't use a .local hostname for the DNS check because the mDNS responder on Mac OSX might interfere with the resolution of .local hostnames.
Don't use hostnames or IP addresses that are defined for Netskope Private Access in DNS or HTTP checks because they cause flapping in the On-Premises check. Netskope recommends you use a separate domain name that does not overlap with NPA app definitions. You can configure a dedicated forward lookup or separate entry in your enterprise DNS for the on-prem detection.
Enabling Dynamic Steering for On- or Off-Premises Devices
To enable dynamic steering for on- or off-prem devices:
Go to Settings > Security Cloud Platform > Steering Configuration.
Click New Configuration, or click
 and Edit Configuration to choose one of the existing steering configurations you want to enable dynamic steering for.
and Edit Configuration to choose one of the existing steering configurations you want to enable dynamic steering for.In the Edit Configuration window, select Enable Dynamic Steering. You can optionally enable traffic steering for all or specific private applications or DNS traffic (if you have Cloud Firewall).
Note
If dynamic steering is not enabled for on-prem, then all exceptions configured for off-prem will be bypassed by the Netskope Cloud instead of locally when the managed device is on-prem.
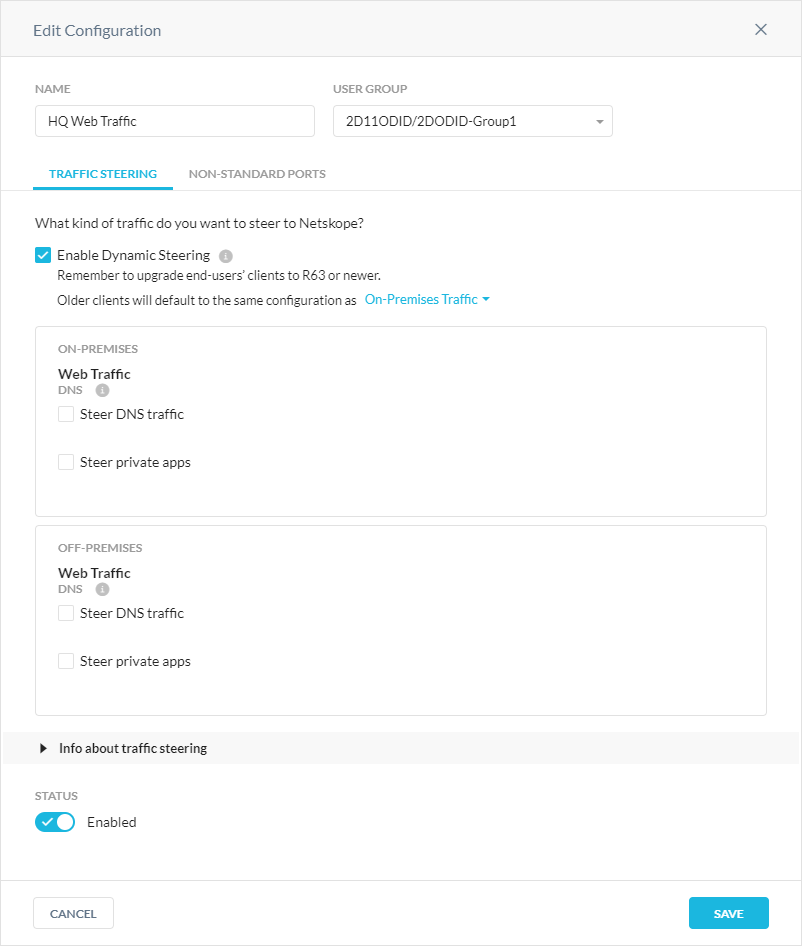
Click Save.
On the steering configuration page, select On-Premises or Off-Premises for the device location.